What Is a Digital Signature & How Does It Help Your Organization?
Digital signatures are at the heart of secure online communications. They not only validate that you’re really you (i.e., not an imposter), but digital signatures also offer assurance that the data you’re providing is authentic and hasn’t been altered
Think back to the last time you downloaded software from your favorite website. Were you able to download and install the software without triggering any unknown publisher warning messages? This likely means that the publisher essentially stamped their application with a digital signature before releasing it. What this communicates is that the software publisher:
- Cares about the security and integrity of their products, and
- Aims to provide users’ operating systems and browsers with a way to differentiate their legitimate products from counterfeits.
But what if you received unnerving warning messages telling you that the software can’t be trusted or that Windows couldn’t verify the publisher? This indicates that the publisher didn’t apply a valid digital signature to their product. And not digitally signing your software is a big red flag from a security standpoint.
But what is a digital signature in terms of security? It’s time to explore what a digital signature is and why using this type of verification method is crucial to your organization’s defenses and reputation.
Let’s hash it out.
What Is a Digital Signature? A Look at This Type of Electronic Signature
A digital signature, also called a public key signature, is a digital identifier that you can apply to files, email communications, websites, and other digital assets to prove their authenticity. It’s a special type of electronic signature that uses cryptography to show that your data is legitimate and hasn’t been messed with. (All digital signatures are electronic signatures, but not all electronic signatures are digital ones — it’s like how all types of ice cream are desserts but not all desserts are ice cream.)
Before the internet, people had to be in the same physical location to verify one another’s identities and exchange secure communications. Now, you can use a digital signature to verify that you’re really you and that the file or site you created is authentic without having to meet the other party face to face. For example, I could share a digitally signed file with a friend in Australia and they’d be able to verify that I created it without actually being here next to me to observe my actions.
PKI Is What Makes Digital Signatures Possible
Digital signatures rely on public key infrastructure (PKI) — a system that uses two separate but related keys to secure data via encryption — and digital certificates. PKI is the foundation of security on the internet; it’s all about providing a way to remotely authenticate parties and prove that the integrity of their data hasn’t been compromised so the parties can communicate securely.
Are digital signatures 100% foolproof? Of course not — no technology is. In this case, their effectiveness depends on the strength of the cryptographic algorithms used and your ability to secure your digital certificates’ private keys. (If you don’t secure your keys and they fall into the wrong hands, then bad guys can use them to sign counterfeit software and raise all kinds of hell.)
But while digital signatures aren’t perfect, they’re a great solution in an age when virtually instantaneous remote communications are the norm.
What Do Digital Signatures Do? It’s All About Creating and Fostering Trust
In a nutshell, digital signatures facilitate both of the following:
- Authentication — This is all about showing that the digital asset in question is legitimate and came from you. It helps users know that you’re not some shyster cybercriminal who created something malicious while impersonating a legitimate person or company.
- Non-Repudiation — Basically, this means that you can show that you, and only you, signed something. This way, no one (including you) can come back later and say that it was signed by someone else.
A digital signature irrefutably ties you or your organization’s digital identity to your digital certificate and key. A digital certificate, such as an SSL/TLS certificate, is a data file that contains information about you and/or your company and the entity (i.e., a publicly trusted certificate authority [CA]) that issued the certificate to you.
Why does it matter who issued the certificate? Every publicly trusted digital certificate is issued by a third-party CA (think DigiCert, Sectigo, etc.). This is an entity that has to meet strict industry standards in order to have the authority to issue certificates that are trusted by browsers and operating systems. When a CA issues a certificate to you or your company, they use their good name and reputation to vouch for you and help you establish trust.
Using a Digital Signature Is Like Hiring a Notary Public…
In some ways, applying a digital signature is similar to having a public notary. When signing important documents, you typically are required to have the notary witness the signing, verify your identity, and add their stamp to affirm the authenticity of your signature. This is because a notary public has been given the authority to sign and attest to the signing of documents in an official capacity.
Likewise, a certificate authority acts similarly, essentially affirming that:
- You are who you claim to be, and
- You’re truly the one who signed the item in question.
Much like how a notary needs to check your government-issued ID card to verify your identity, certificate authorities also validate you or your business by checking official government records and other trusted third-party resources. Once the CA verifies this information, they’ll issue you a certificate from a trusted root.
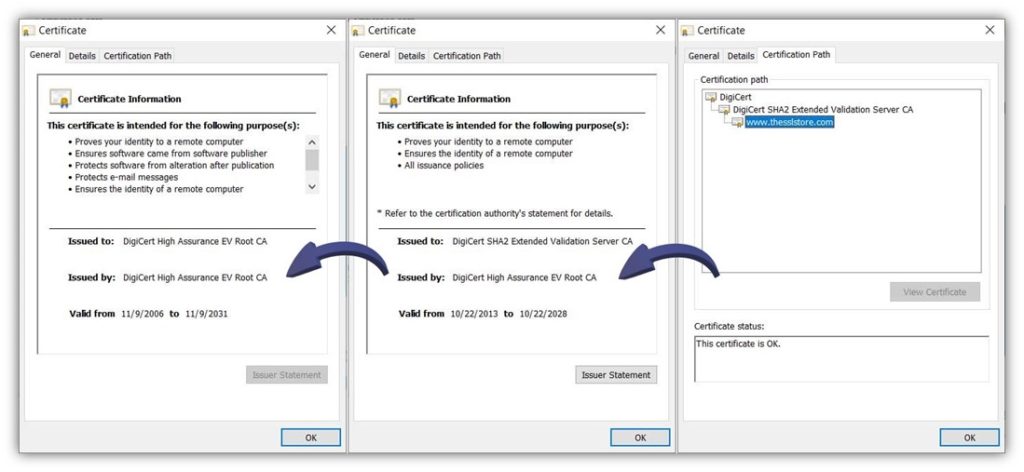
Digital Signatures Rely on the Issuing CA’s Chain of Trust
A trusted root, or root CA, is part of a critical element of public key cryptography called a “chain of trust.” Basically, this is a line of digital certificates, and each certificate contains information from the previous certificate that was used to sign it. In a traditional chain of trust:
- The certificate you install on your website is issued and digitally signed by an intermediate CA.
- The certificate of the intermediate CA’s certificate that issued the leaf certificate is issued and digitally signed by a root CA.
- The root CA’s certificate is digitally signed by the root CA, which is stored offline in a highly secure location.
Here’s a quick look at the chain of trust for The SSL Store’s SSL/TLS certificate:
Why Digital Signatures Matter to Your Organization
When you add digital identity to your data, it’s shared with others. You’re letting those parties know that your data is authentic and hasn’t been messed with since you signed it. But that’s not the only way that integrating digital signatures into your organization’s cyber defenses can help you.
Adding digital signatures to your emails, documents, software, and digital communications also:
- Mitigates phishing attacks and data exposure risks. If your employees know that they should expect only digitally signed emails from colleagues, this can prevent phishing scams from being successful. This, by extension, aids in mitigating the risk of your sensitive data and systems being exposed.
- Increases your organization’s digital security. Since some PKI certificates (such as SSL/TLS, email signing certificates, and device certificates) also have the additional benefit of enabling encryption, it’ll make your communications and data more secure. Which leads us to our next point…
- Aids your compliance efforts. Many regulations require the use of secure communications and connections to protect data in transit. Digital signatures improve the security of communications by helping you ensure that you’re connecting to a legitimate party on the other end.
- Helps you reduce costs. Whether it’s preventing data breaches or avoiding non-compliance issues, using digital signatures can help you reduce or mitigate various costs, including breach mitigation-related costs and non-compliance fines and penalties.
5 Ways You’re (Probably) Already Using Digital Signatures Within Your Organization
You now know what a digital signature is and what it does. But where can you find these digital identifiers in use? Virtually everywhere, if you know what to look for! Digital signatures are commonly used to secure files and data for organizations in the following industries for organizations across virtually all sectors, including banking, government, healthcare, and sales.
Here are a few examples of common digital signature uses:
1. Create Secure Website Connections
Look at the top of your browser at the web address bar. See the little security padlock icon in your web browser? This means that your website is secured via the HTTPS protocol.
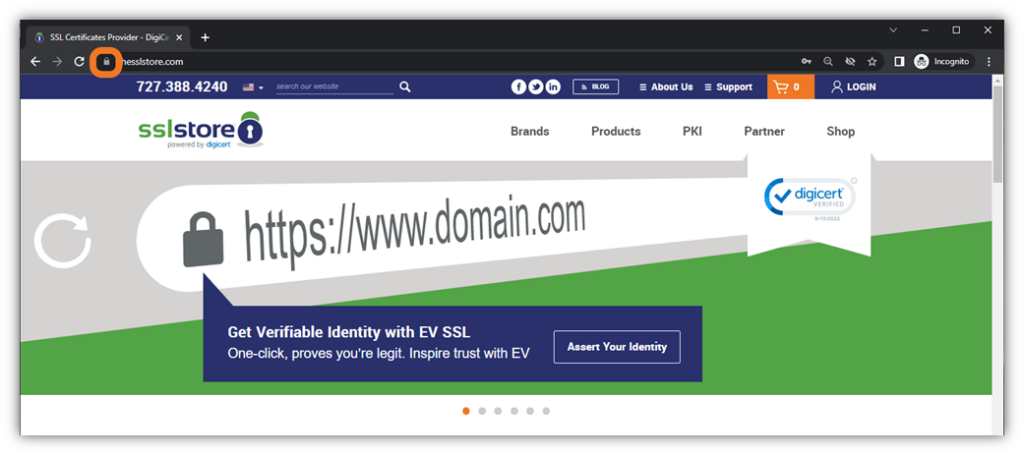
Image caption: A screenshot of TheSSLStore.com’s home page with the security padlock icon highlighted.
When you initially connected to our website (TheSSLStore.com), our web server sent your browser an SSL/TLS certificate. This certificate contains a wealth of verifiable identifying information about our domain and company. It also includes the digital signature of the publicly trusted certificate authority that issued the certificate to us. Your browser verifies this digital signature as part of the SSL/TLS handshake process that creates a secure, encrypted communication channel.
To enable HTTPS on your website, purchase and install an SSL/TLS certificate on your web server.
2. Authenticate Your Email Communications
When you add a digital signature to your outbound emails, it offers your recipients assurance that the emails are legitimate and came from your email client. It’ll look something like the image below (which was captured in Microsoft Outlook).
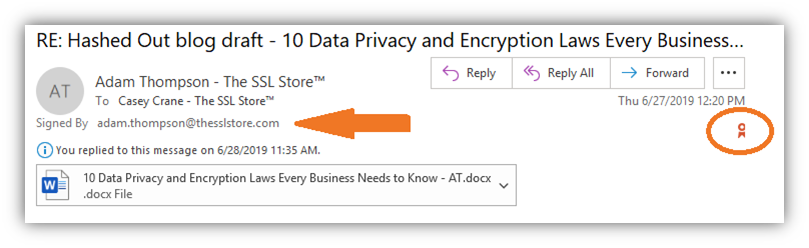
If you want to prove your emails are authentic and haven’t been tampered with, you can digitally sign your message and all attachments. Simply add an email signing certificate to your email client (such as Outlook) and have at it. Once you do this and enable the digital signing feature, it makes the little verification ribbon appear in your outbound emails.
You can also add an optional timestamp, which shows the precise date and time when your email was signed and verified. (This is always a good idea, as far as we’re concerned!)
3. Offer Assurance of Your Digital Files’ Authenticity
Creating fraudulent Office documents isn’t rocket science — virtually anyone can do it. So, if you want to ensure that no one tampers with your PDF and Microsoft Office files, you can do so by attaching your digital signature. This is akin to giving your files an official stamp of authenticity, much like the notary stamp we mentioned earlier.
Here’s a quick example of how it looks when you use a document signing certificate to sign your Adobe PDF files:
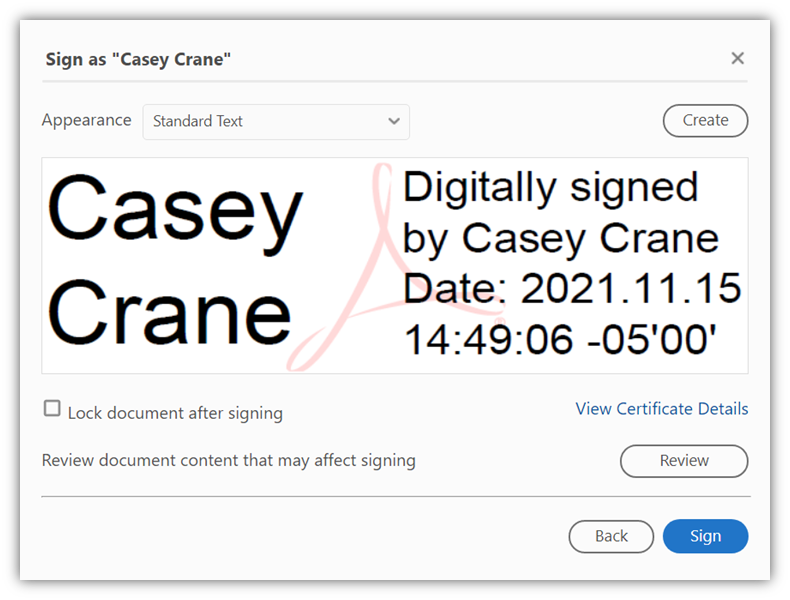
As you can see, the digital signature provides the signer’s name, date, and time of when the digital signature was applied. Furthermore, you can click on Certificate Details to view additional information, including:
- Who issued the certificate,
- When it was issued, and
- Whether the certificate has been revoked.
Note that this digital signature is different from a basic typed signature (which can be easily faked). To start adding digital signatures to your files, you’ll need to first get a document signing certificate. After that, you’ll need to install it in your device or client’s trust store.
4. Ensure the Authenticity of Your Software, Code, and Containers
The same concept applies to your code and executables. If you want to provide assurance that your software is legitimate and isn’t counterfeit, digitally sign your executables using a standard code signing certificate. This will enable your verified organization information to display in the warning windows instead of the dreaded “Unknown” publisher message.
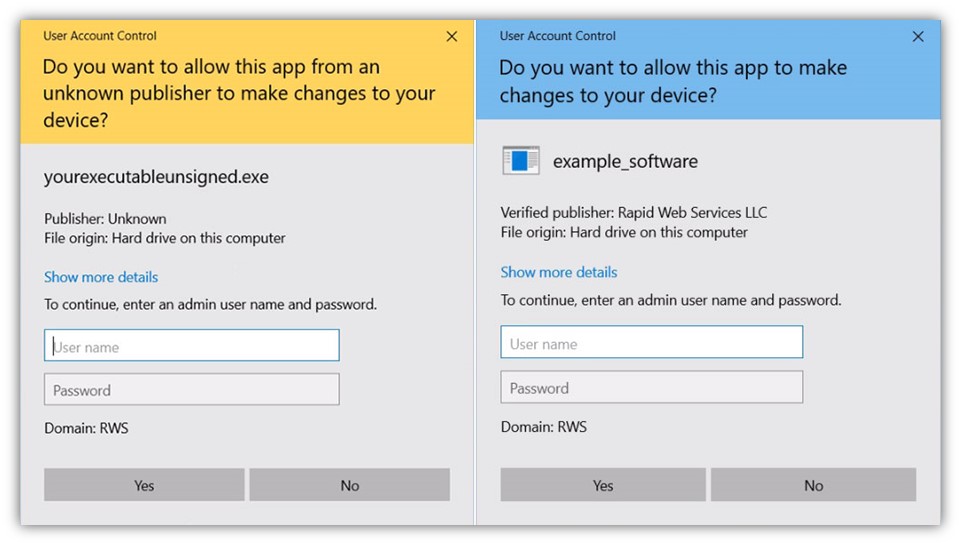
But if you want to take your digital identity to another level, use an extended validation (EV) code signing certificate. Doing this ensures your software will automatically be trusted by browsers and operating systems and won’t trigger the Microsoft Defender SmartScreen warnings like the one above.
5. Establish Digital Identities for Your Network’s Connected Devices
For all you IoT lovers out there, this one is for you. Digital signatures are a great way to add verifiable digital identity to your smart technologies. If you’ve got remote monitoring devices deployed in the field, you need a way to verify that it’s your legitimate devices that are connecting to your network.
Using digital certificates for these devices enables you to harness the power of digital signatures (and public key cryptography as a whole) to keep your network and device data as secure as possible.
How Digital Signatures Work
We already wrote a comprehensive article on how digital signatures work, so we’re not going to dive into all of that again here. Here’s the quick overview of how using a digital signature works using an example of signing an executable:
- A publisher applies a hash function (a type of cryptographic function) to their software application.
- They then take the resulting hash value (i.e., a fixed-length string of special characters) and use a code signing certificate’s private key to encrypt it. This creates a digital signature.
- Next, they take the digitally signed file and upload it to their website, along with the corresponding public key.
- When a user downloads the software, they can then use that public key to decrypt the file.
- The user then can compare the provided hash value against one their system generates using provided values. (The hash value information will be provided in the file’s Properties section under Digital Signatures, as shown in the screenshots below.)
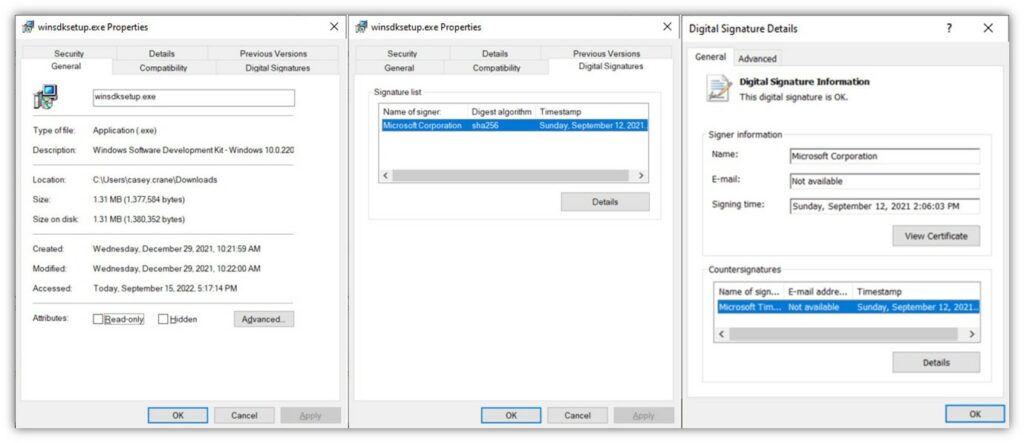
If the publisher-provided and generated hash values match, it means that the software is authentic and hasn’t been tampered with since the publisher signed it. If they don’t, it means that it’s been altered somehow and shouldn’t be trusted.
Final Thoughts on Digital Signatures in Cyber Security
As you’ve learned, digital signatures have a place in virtually every organization. Digital signatures are all about establishing trust by providing users with a way to verify the authenticity of a product and its creator. Without them, you have no verifiable means to prove whether your software is legitimate or was created by an imposter.
Whether you’re a mortgage broker, software publisher, or managed service provider (MSP), these cryptographic tools can make a world of difference in increasing the security of your products, services, and organization.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown