Public Key Signature: What It Is & Why It’s Everywhere
PKI digital signatures can be found virtually everywhere — from digitally signed emails and software to secure websites. We’ll break down what a PKI signature is and how it helps protect your data’s integrity

Remember when you were a kid and your parents told you that if you put your mind to it, you can do or be anything you want? Well, on the internet, that is kind of true. You can pretty much make your own truth about yourself — you could be a teenager, an adult, or a company’s CEO. Without a way to prove your claims are legitimate, no one will be any the wiser.
Cybercriminals know this and love to take advantage of it. That’s why we have all the issues that we do today relating to phishing other sorts of predatory cyber attack techniques. Before the internet, you had to meet up with someone face to face to securely exchange information or send coded, encrypted messages.
But now that people are communicating and doing business with others across the world instantaneously, face-to-face meetups are no longer feasible in most cases. So, to protect yourself and your customers, you need to have a way to prove your identity online and help people know that your emails, files, and software are legitimate and haven’t been faked. This is where PKI signatures come into play.
But what is a public key signature? How is a digital signature different from other electronic signatures? And where can you find PKI digital signatures in action?
Let’s hash it out.
What Is a Public Key Signature? A Simple PKI Digital Signature Definition & Analogy
Before we can dive head-first into the nitty-gritty of public key signatures, it would be smart to at least briefly recap what a digital signature is as well as the role it plays in public key infrastructure (PKI). After all, you can’t run the play if you don’t know the rules.
A PKI signature is a form of verifiable digital identity that helps you prove you (or something you create) is real. In a way, it’s kind of like a fingerprint because it’s something that uniquely identifies you. However, it’s more than “just” identity. A digital signature is a way for your organization to affirm its legitimacy through the use of a digital certificate (such as a code signing certificate) and a cryptographic key.
In a nutshell, using a PKI digital signature enables you to attach your verifiable identity to software, code, emails, and other digital communications so people know they’re not fake. This helps you:
- Prove your identity so you can do things that require authorized access (authentication)
- Assert your organization’s digital identity so people know you’re you and not an imposter (non-repudiation) using the signature and other tools (such as timestamping), and
- Protect and prove the authenticity of your messages, files, connections and data (data integrity).
If that all seems a bit complicated, let’s break this down with more of a simple analogy…
A Public Key Signature (PKI Digital Signature) Is the Wax Seal of Internet Communications

A PKI signature is the modern equivalent of a wax seal that people historically would use to secure sensitive communications. Before the internet or the invention of the telephone, people would either meet up in person or communicate remotely via written letters. Of course, without digital communications, these messages would have to be delivered by hand — via train, boat, or horseback riders — which means that these messages could be intercepted on their way to their intended recipients.
Say, you want to send a sensitive message to a friend. You’d want to have a way to let them know that you signed it and that the message hasn’t been tampered with in any way. Years ago, you’d use a wax seal to achieve this. This process would entail:
- Melting some wax,
- Pouring it on the envelope, pressing your personal seal (i.e., stamp) into the wax, and
- Giving the wax time to harden.
When your friend receives your message, they’ll see that the wax seal intact. This unbroken wax seal indicates that your message is legitimate in two crucial ways:
- The crest proves your identity because you should be the only one with that stamp. Sealing the message with your individual crest lets the recipient know that you’re the one who sealed the message.
- The unbroken wax seal means no one altered the message in transit. This lets your friend know that the message’s integrity has been protected and that no one altered it since you sent it.
In much the same way, communications on the internet also need to have these same types of protections. While they’re not being sent by horseback, digital communications pass through a lot of “hands” as they transmit across the internet in the form of servers, routers, and other intermediates until they reach the right destination. This means that cybercriminals would have many opportunities to alter or manipulate your information in transit if there wasn’t a way for the recipient to verify the message’s integrity.
Here’s a great video from Computerphile that helps to explain PKI digital signatures in another way:
PKI Digital Signature vs Electronic Signature
People often mistakenly conflate PKI digital signatures and electronic signatures as being the same, but that’s not quite true. Yes, a digital signature is a type of electronic signature, but not all electronic signatures are digital signatures. It’s kind of like how all iPhones are smartphones but not all smartphones are iPhones. Sure, they both are a way to say you’re someone on the internet, but only one of them (*cough*PKI signature*cough*) can actually help you prove your identity because it’s more than just an online signature that can be altered.
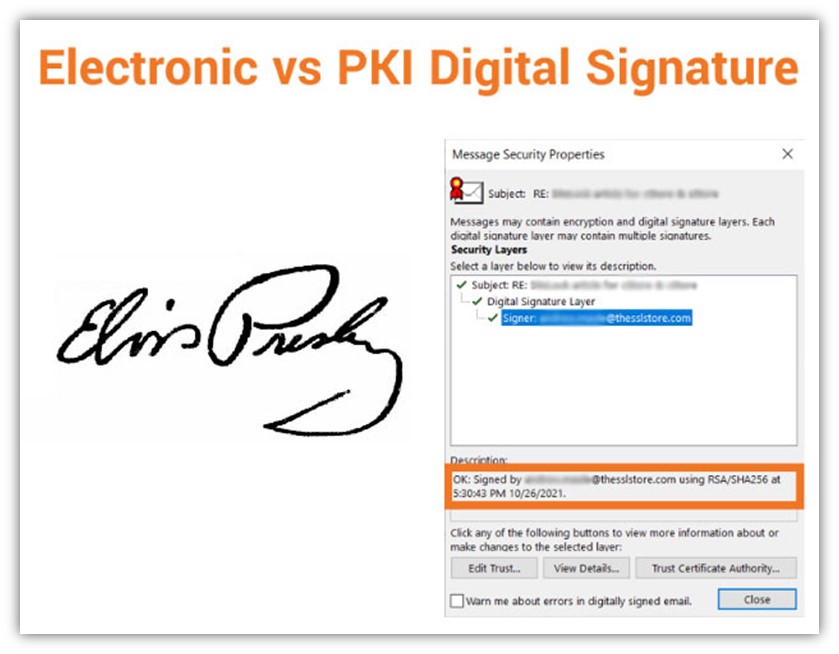
It’s kind of like getting an autograph of your favorite athlete — like, say, quarterback Tom Brady. (Sorry, Pats fans, Tom is ours now! #TampaBayBucs) Sure, you could just walk up to Tom at a bar and ask him to sign something. But without having some way to authenticate that his signature is real — like, say, an official certificate of authenticity — then someone could argue that anyone could have signed his name.
Or, for all they know, you really could have gotten Tom to autograph one item. But what would stop you from sitting at home on the weekends, using his signature as an example so that you can forge his autograph on a bunch of Buccaneer’s team gear that you want to sell? Well, nothing, unless your prospective buyers had a way to verify the autograph’s legitimacy.
This is kind of like the difference between an electronic signature and a digital signature:
- An electronic signature is signing your name in an electronic format. Instead of putting a physical ink-writing pen to paper, you’re signing your name using electronic means.
- A PKI digital signature is like a certificate of authenticity. In this way, a public key signature is a way for you to sign something so that others can verify:
- You, as the legitimate person or organization representative, actually signed the email, file, or software, and
- The item you signed hasn’t been modified or tampered with since you signed it.
Two Cryptographic Processes Are Integral to the Digital Signing Process
To really get at the heart of understanding public key signatures, you need to know about two cryptographic processes that play pivotal roles in their creation: encryption and hashing.
Encryption
This cryptographic process takes a mathematical algorithm and applies it to plaintext (readable) data to “scramble” it into an unreadable state. It can use:
- a single key to encrypt data and decrypt data (symmetric encryption), or it can use
- two separate keys (asymmetric encryption) to do the same.
As you can see, there are some key differences (excuse the pun) between asymmetric and symmetric encryption. Regardless of those differences, the process is, essentially, reversible (using the decryption key), which means that encryption is a two-way function.
In digital signatures, encryption is used to specifically encrypt the hash data to create the digital signature. (It doesn’t encrypt the file or email you want to digitally sign — it only encrypts the hash value.)
Hashing
Hashing is a cryptographic function that also applies a mathematical algorithm to data and files. However, its purpose is different than an encryption algorithm — a hashing algorithm takes data of any length and maps it to an output (hash value) of a specific length. For example, you can take a single sentence or an entire book, apply a hash function to it, and the result will be an output (hash value) of the same length.
Because the process isn’t reversible, there’s not a key that reverts or maps the hash value back to the original input. This means that hashing is a one-way cryptographic function. (You know… because hashing only works in one direction.)
5 Uses for a Public Key Signature
In truth, digital signatures can be found all across the internet. For example, you can use digital signatures in the following applications:
1. Enabling HTTPS on Websites
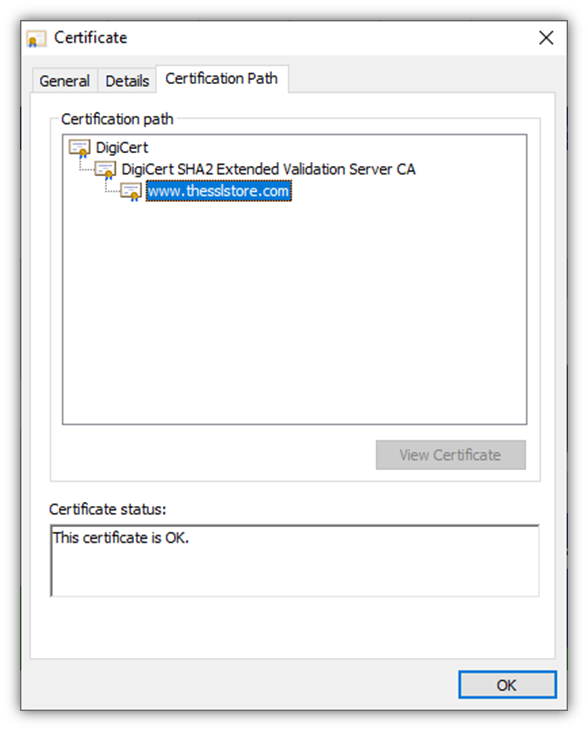
A website security certificate, or what’s known as an SSL/TLS certificate, is one of the most central components of security on the internet. Installing this certificate on your server enables you to secure your website using the secure HTTPS protocol. Enabling HTTPS means that whenever customers connect to your website, their individual connections (and any data they share during their session) will be secured using encryption. This is what makes that nifty little padlock icon appear in your browser.
A digital signature is a part of what’s known as the TLS handshake (or what some people still call the SSL handshake). We won’t get into all of the specifics here, but the first part of the handshake involves the website’s server and user’s browser exchanging information (including the server’s SSL/TLS certificate and digital signatures) via an asymmetric encrypted connection. Using a digital signature helps the server prove that it’s the legitimate server for the website you’re trying to visit.
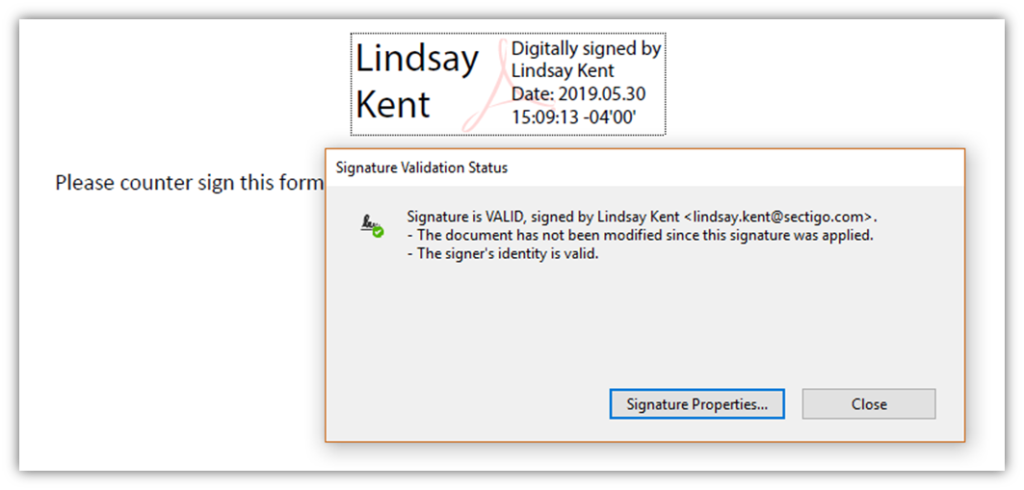
2. Signing Digital Documents to Prove Their Legitimacy
A document signing certificate enables you to apply your digital signature to many types of documents, including Microsoft Office documents and PDFs (depending on the specific certificate you use). Here’s a quick example of what a digital signature looks like:
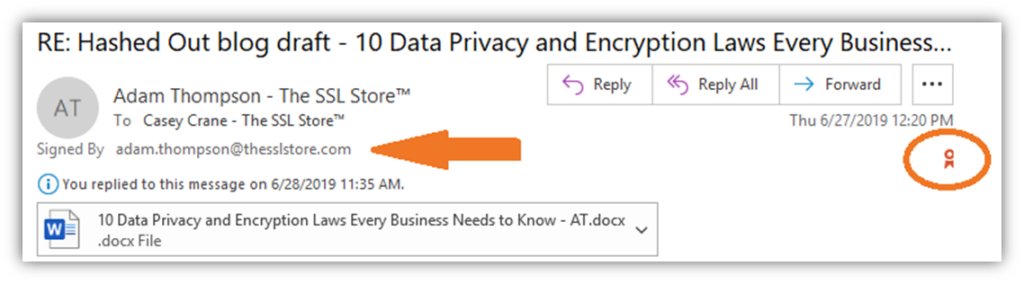
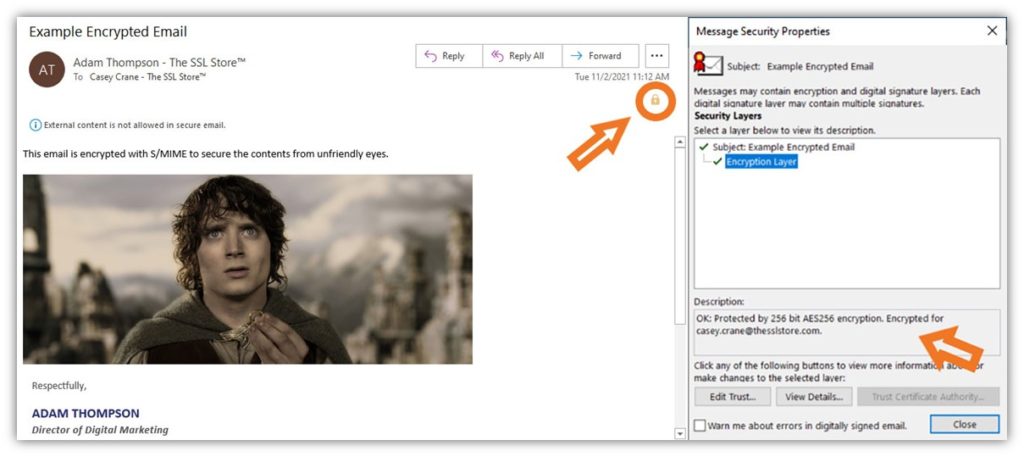
3. Providing Extra Security to Sensitive Emails
Using an email signing certificate (i.e., an S/MIME certificate) allows you to apply your digital signature to your emails. This provides identity assurance and protects the integrity of your communications.
Note: For extra security, you can also use this certificate to send encrypted emails (to users who also use email signing certificates). This provides secure, end-to-end encryption that protects your data both while it’s bouncing between servers and routers and sitting on your recipient’s email server.
4. Securing Your Software and SaaS Supply Chain
Using a code signing certificate helps you to protect your supply chain. It also offers assurance to users who download your software that your software is both legitimate and unmodified.
When you sign your certificates using a code signing certificate, you’ll display your verified company organization information (as shown in the screenshot on the right):
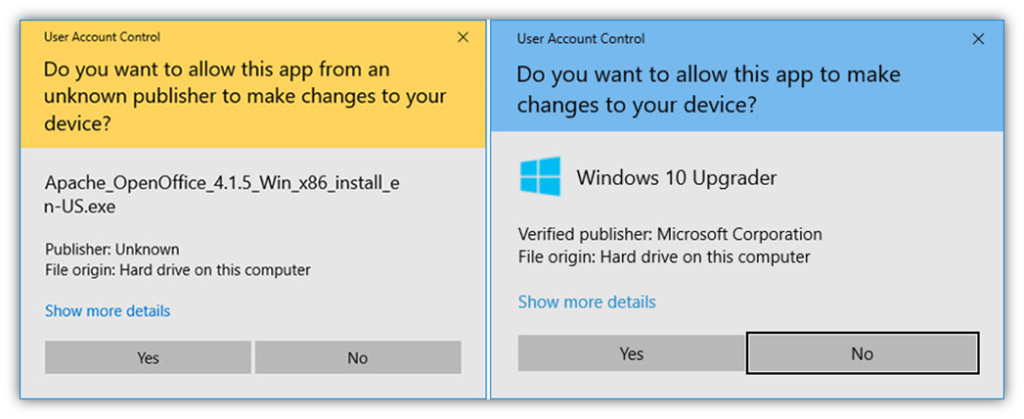
Of course, unsigned (and software signed using standard code signing certificates) can also trigger Windows SmartScreen warning messages as well — the difference would be that digitally signed software would display the verified publisher information instead of “Unknown publisher.”
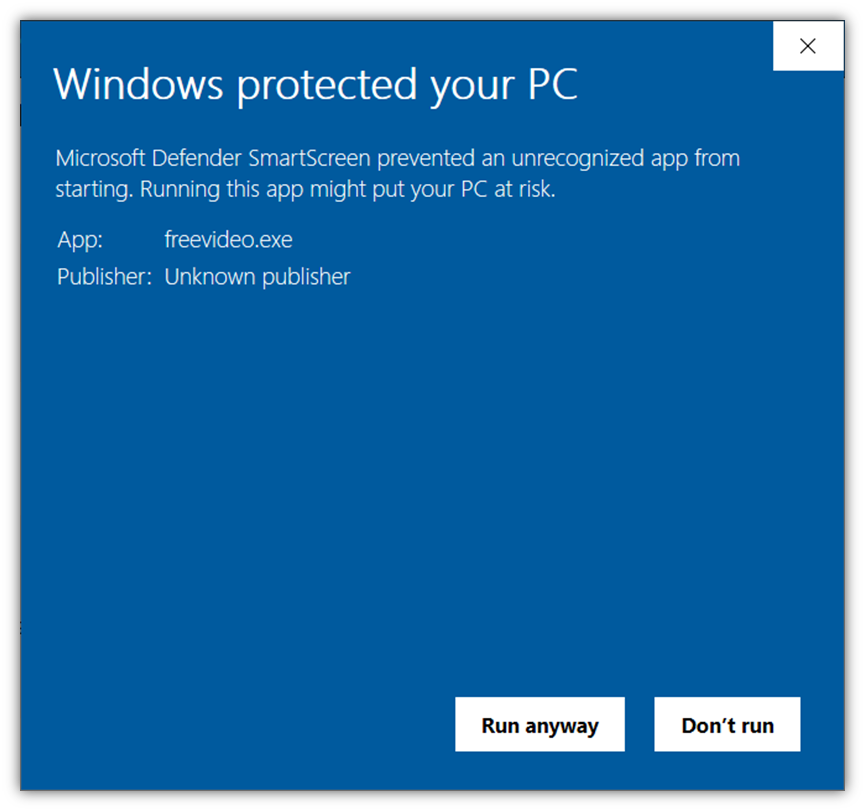
To avoid displaying Windows SmartScreen messages, be sure to sign your software, code, and other executables using an extended validation code signing certificate. Using this PKI digital signature ensures Microsoft and its browsers automatically trust your software.
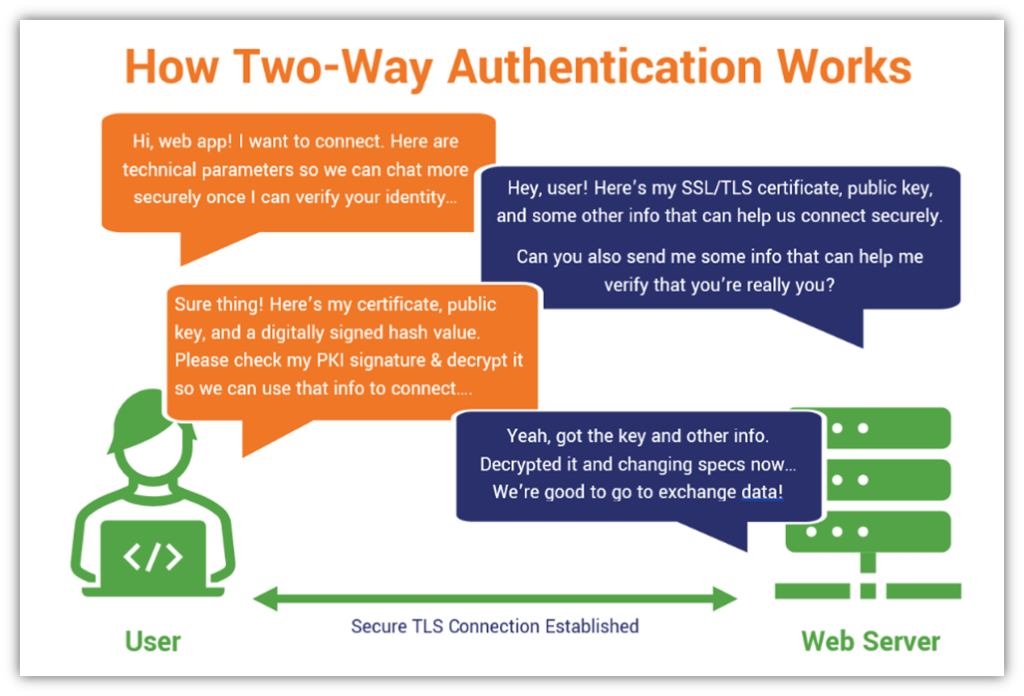
5. Enabling Secure, Two-Way Authentication (Mutual Authentication)
Remember the SSL/TLS handshake that we mentioned earlier? Well, in two-way authentication, or what’s known as mutual authentication, both the server and the client prove their identities to one another. This means that in addition to the server providing its information to the client, the client must do the same by providing information to the server.
This information includes a generated hash value, digital client certificate, and cryptographic public key. The client generates the hash using data it exchanges with the server and encrypts the fixed length string using its private key (which is mathematically related to the public key it shares).
Here’s a basic overview of how this process works:
Why Using a Public Key Signature Matters to Your Business & Customers
Public key signatures are essential in an internet-oriented world. As more companies are moving to the cloud and relying on this public network to conduct business and provide services, the roles of identity and integrity in security become more important.
Of course, we’ve talked about the reasons why it’s so important at length in a previous article. Be sure to check out our article on why you should use digital signatures to sign everything. But we’ll quickly summarize the key reasons here for you about why digital signatures matter:
- Attaches your identity to your software or communications. The best way to help users know whether your software or communications are legitimate is by giving them a way to verify your identity.
- Helps you protect your supply chain. If you’re a software developer or publisher, one of the worst things that can happen is it someone uses your supply chain to attack customers while impersonating you. By signing your software or other executables, you’re providing a way for users to verify whether your code is legitimate or if it’s been altered after it was signed.
- Protects your organization’s reputation. If you have a verifiable way to prove that you’re authentic and your products or files are trustworthy, prospective customers are more likely to want to do business with you.
Wrapping Up Public Key Signatures (TL;DR)
Thanks to all of you who’ve stuck through this article to get to this point. For those of you who’ve decided to skip to the end for the “too long; didn’t read” portion of our article, welcome. We know your time is precious, so here’s a quick overview of what we’ve covered in this article so you can skim and head out on your way.
- A digital signature is the modern wax seal for sensitive communications.
- Organizations use digital signatures to assert their identity and ensure the integrity of their communications, files, software, and connections. Simply put, PKI signatures:
- Identifies you as you (and not an imposter).
- Provides verification techniques to help prove that the message came from you (i.e., not someone else).
- Protects the integrity of your communications and data so recipients know it’s legitimate (not fake).
- Public key signatures are a type of electronic signature (but that doesn’t mean all electronic signatures are digital signatures).
- PKI digital signatures rely on public key infrastructure and cryptographic components like certificates and keys.
All of this is to say that this cryptographic technique is all about helping companies prove their authenticity and giving users a way to verify that files, software, and other information haven’t been manipulated or altered since they were digitally signed.
Stay tuned next week for a related article that will break down how digital signatures work.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown