Symmetric Encryption 101: Definition, How It Works & When It’s Used
Symmetric key encryption is part of virtually everything you do online. We’ll break down everything you need to know about what it is and how and where you’re using it…
Although you may not realize it, symmetric encryption is in use just about everywhere you look. It’s part of what makes it possible to do everything from secure online banking to ordering your groceries for delivery.
But what is symmetric key encryption? If you peek “under the hood,” how does symmetric encryption work? And what role does it play in your daily life online?
Let’s hash it out.
Editor’s Note: This article is the first in a series of articles on symmetric encryption. Be sure to check out the related articles below:
- Asymmetric vs Symmetric Encryption: Definitions & Differences
- Symmetric Encryption Algorithms: Live Long & Encrypt
- Block Cipher vs Stream Cipher: What They Are & How They Work
What Is Symmetric Encryption & What Does It Do? A Definition & Explanation
To put this in the simplest terms possible, symmetric encryption is a type of encryption that uses the same key to encrypt and decrypt data. Both the sender and the recipient have identical copies of the key, which they keep secret and don’t share with anyone. This differs from asymmetric encryption, which uses two keys — a public key (that anyone can access) to encrypt information and a private key to decrypt information.
Just in case it’s helpful, let’s do a quick review of how encryption works in general:
- The sender uses an encryption key (usually a string of letters and numbers) to encrypt their message.
- The encrypted message, called ciphertext, looks like scrambled letters and can’t be read by anyone along the way.
- The recipient uses a decryption key to transform the ciphertext back into readable text.
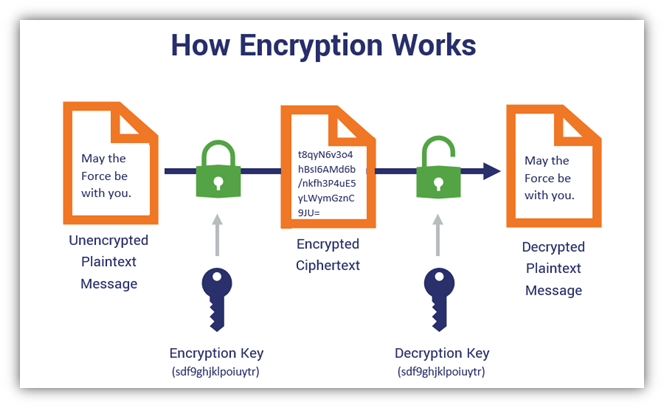
In the example above, we used the same key for encryption and decryption, which means this is symmetric encryption.
Only these two parties (sender and recipient) can read and access the data. This is why it’s also sometimes called secret key encryption, secret key cryptography, private key cryptography, symmetric cryptography and symmetric key encryption.

Having only one key to serve both the encryption and decryption functions simplifies the encryption process. After all, you’re applying one key to turn plaintext, readable information into unreadable gibberish (ciphertext) and vice versa. One of the advantages of using symmetric encryption is that it provides data privacy and confidentiality without the extra complexity of multiple keys.
Symmetric key encryption does work on its own, for certain use cases. For example, it’s useful for encrypting databases and files, where you’re not exchanging data publicly between parties. But as with any technical process, there are other advantages and disadvantages of using symmetric key encryption, such as key distribution and management issues, and we’ll talk about those a little later. But for now, let’s talk about the history of symmetric encryption.
Symmetric Key Encryption Isn’t a New Concept
While symmetric key encryption in the sense of encoding digital data through the use of computers is relatively new (it’s been around since the mid-1900s), the concept behind isn’t. Symmetric cryptography itself is a process that’s thought to have been created thousands of years ago.
An early example of symmetric encryption — and probably the best-known symmetric cipher — is attributed to the Roman General Julius Caesar. This particular cipher is aptly known as the Caesar Cipher (more on that in a couple of minutes). However, there have been other types of symmetric ciphers that have existed throughout history, including everything from the Vigenère Cipher — which dates back to the 1500s — to the modern AES algorithm (more on that later).
Symmetric key encryption is a way for you to encrypt a message so that only you and your intended recipient can read it. It’s one type of data encryption, but it’s not the only one. There’s also another type of encryption that’s close in name but is different in terms of what it does: asymmetric encryption. We mentioned it earlier, but just know that asymmetric encryption is what makes it possible to authenticate and exchange symmetric keys via public channels (such as the internet).
However, we aren’t going to hash out all of the specifics of asymmetric encryption here. That’s a topic for another time. In the meantime, though, we invite you to check out this article on the differences between asymmetric vs symmetric encryption to learn more about the topic.
So, for now, let’s stay the course and continue our journey of exploring the world of symmetric encryption.
How Does Symmetric Encryption Work?
It’s time to take a closer look at the symmetric encryption process. To understand how symmetric cryptography works, you need to know what the components are that are involved in the process:
- Your original message that you wish to encrypt (plaintext data).
- A symmetric key encryption algorithm (we’ll touch on the different types of algorithms a bit later).
- An identical secret key that only you and your intended recipient have that encrypts and decrypts the data.
- The encrypted message that no one can read (cipher text).
The way that symmetric encryption works is by encrypting and decrypting data through the use of identical keys. The data, once encrypted into ciphertext, can’t be read or otherwise understood by anyone who doesn’t have the key. This means that you and the party you’re communicating with both need to have an identical copy of the key to communicate securely.
To better understand how symmetric encryption works and how all of these components work together, let’s consider a basic type of symmetric encryption known as the Caesar cipher.
How a Basic Shift Cipher (Substitution Cipher) Works
An easy way to think of this is to think of this encryption process is through the use of a Caesar cipher, or what’s known as a substitution or shift cipher. This was a method by which Caesar was able to secretly communicate with his generals without anyone being able to read the messages (even if the message carriers were intercepted).
In this case, a cipher, also known as an algorithm, is a number or sequence of steps that you’d use to convert plain text information into unreadable ciphertext. With a basic shift cipher, you can encrypt and decrypt a message simply by shifting the message along the alphabet a set number of spaces.

Imagine writing out the entire alphabet in a single long line. And when you use the shift cipher, you’d shift any given letter X number of spaces. So, if you were to shift the letter “G” by nine spaces, it would become “P.” The letter “O” would become “X.” This means that the message “Good morning, sunshine,” for example, then becomes “Pxxm vxawrwp bdwbqrwn” when you shift each letter nine spaces to the right.
So, the key in a Caesar cipher is the secret value that only you and your recipient know, which tells you how many letters to shift.
Nowadays, however, we’re not passing paper messages back and forth. Today’s information exchanges take place through virtual channels via computers, websites, and the internet in general. And while the internet makes things incredibly convenient, banking online or paying for a rideshare over the internet doesn’t come without its risks.
The Role of Symmetric Key Encryption in Website Security
Symmetric key encryption is part of the public key infrastructure (PKI) ecosystem, which makes it possible to communicate securely across the insecure internet by converting plain text (readable) data into unrecognizable ciphertext. In fact, you’re using PKI-based technologies and processes right now as part of your connection to TheSSLStore.com to read this article.
See that padlock in your browser’s URL bar? It means that our website has a website security certificate (SSL/TLS certificate) installed and you’re using a secure, encrypted connection to send data. This is what helps to make it possible to connect to our website using the secure HTTPS protocol instead of the insecure HTTP one.
What this also means is that your browser (client) has already gone through the process of:
- Authenticating our website’s server,
- Negotiating with the server on the encryption algorithms to use, and
- Generating symmetric session keys.
The way that HTTPS works is that we use asymmetric encryption to first authenticate the website server and to exchange symmetric session keys. This is part of a process known as the TLS handshake — of which there are three versions (TLS 1.0, TLS 1.2 and TLS 1.3). After that, we use symmetric encryption for the actual bulk of the data encryption that takes place during your session.
In general, the TLS handshake:
- Enables our web server to authenticate itself to your browser (web client),
- Establishes parameters to use for secure communication (such deciding which encryption algorithm to use),
- Determines which key exchange protocol to use, and
- Generates a session key that only the two communicating parties know using that algorithm and other public and private variables.
The reason for the change to symmetric encryption is that it’s faster and less resource-intensive than asymmetric encryption when you’re encrypting massive quantities of data. This is particularly important for enterprises who encrypt data at scale. (Think of banks and large companies.)
We won’t get into all of the specifics of the handshake here — you’ll find a deep dive on that topic in our article on the TLS handshake. But let’s explore a few of the encryption algorithms that fall under the symmetric encryption umbrella.
Symmetric Encryption Algorithms
Symmetric algorithms are broken down into two main types: stream and block ciphers. Block ciphers encrypt data in chunks (blocks), whereas stream ciphers encrypt data one bit at a time. So, what are some of the most commonly used or well-known symmetric algorithms?
- Data Encryption Standard (DES) — DES is a type of block cipher that encrypts data in 64-bit blocks and using a single key that is one of three sizes (64-bit, 128-bit and 192-bit keys). However, one of every 8 bits is a parity bit, meaning that a single-length key that’s 64 bits is really like using a 56-bit key. Although DES is one of the earliest symmetric encryption algorithms, it’s viewed as insecure and has been deprecated.
- Triple Data Encryption Standard (TDEA/3DES) — Unlike DES, triple DES can use two or three keys, which enables this algorithm to use multiple rounds of encryption (or, more accurate, a round of encryption, round of decryption, and another round of encryption). While 3DES is more secure than its DES predecessor, it’s not as secure as its successor, AES.
- Advanced Encryption Standard (AES) — This encryption algorithm is what you’ll most commonly find is use across the internet. The advanced encryption standard is more secure and efficient than DES and 3DES with key options that are 128 bits, 192 bits and 256 bits. However, while it’s also a type of block cipher, it operates differently than DES and 3DES because it’s based on a substitution-permutation network instead of the Feistel cipher.
Of course, we’re going to cover these three symmetric key algorithms — along with the differences between block and stream ciphers — in the coming weeks in additional articles. But for now, let’s move on to discussing the “secret” in secret key encryption.
For Symmetric Encryption to Work, the Key Must Stay Secret…

For symmetric encryption to work, however, it means that you and your intended recipient both must know the key and keep it secret. Otherwise, if someone else knows the key, then they can decrypt your data and read it, which makes the entire encryption process pointless. That’s why it’s vital to keep the secret key secret and away from prying eyes to limit the number of people who have the key.
As such, you should never store secret or private keys in any internet-facing environment. This is true for both asymmetric encryption private keys as well as symmetric keys. You need to keep those keys hidden somewhere where no one is going to be able to find, access, or steal them. Basically, protect those keys like you would a lifetime paid subscription that someone gave you to your favorite gaming service — ‘cause I know that no one’s getting their hands on that.
But the tricky part with symmetric encryption is that there’s an assumption that you and your recipient both already have identical copies of the key. But what do you do if you and your recipient have never met, and if you don’t already have those identical keys?
Remote Key Distribution: How to Share a Key Securely to Facilitate Symmetric Encryption
Let’s say that you want to share secret messages with your friend, Erica, who’s in another country but she doesn’t have a key to decrypt said messages. This means you’d need to get a shared key to her so that she can securely decrypt the message.
To do this, you’d have to send the secret key across the internet — which you know is anything but secure. After all, your internet connection gets bounced through potentially dozens of different touchpoints in its journey. This means that any Tom, Dick or Harry — any cybercriminal, government, or anyone else you don’t want reading your messages — could intercept the key en route and decrypt your messages with ease, and you’d be none the wiser. This is known as a man-in-the-middle attack (MitM).
So, sending data (especially keys) across the internet isn’t a good idea, which means we need to look at an alternative method. This is where asymmetric tactics — such as asymmetric key exchange (i.e. key generation) methods like RSA and Diffie-Hellman — come into play.
The Role of Key Exchange Protocols
Earlier, we touched on the fact that symmetric encryption algorithms aren’t the only algorithms out there that PKI depends upon. There are also asymmetric algorithms and asymmetric key exchange protocols. So, if you’re trying to communicate securely with your friend Erica using symmetric key cryptography, you’ll use asymmetric encryption tactics to generate and share a secure key that only you and Erica will know.
Historically, symmetric encryption is paired with either RSA or Diffie-Hellman asymmetric algorithms (i.e., key exchange protocols) for the key exchange/generation process. However, these two algorithms have separate roles.
RSA vs Diffie-Hellman Key Exchanges
The RSA encryption algorithm, which stands for Rivest-Shamir-Adleman (the surnames of the three people who created it), is an authentication and key exchange mechanism that’s commonly used in the TLS 1.2 handshake process. In an RSA key exchange, public key encryption facilitates the exchange of a pre-master secret and a randomly generate number from the client that, together, generate a shared session key.
With the Diffie-Hellman key exchange, the server and client instead mutually agree upon a value that’s used for the session key. (More on that shortly.)
However, the use of RSA for key exchanges is frowned upon (although some systems are still using it) due to vulnerabilities that were discovered by cryptologist Daniel Bleichenbacher. In fact, the RSA key exchange cipher suites (and non-ephemeral Diffie-Hellman groups) were deprecated with the rollout of TLS 1.3 in an effort to mandate perfect forward secrecy (which uses an ephemeral key). So, RSA key exchange was replaced by the exclusive use of ephemeral Diffie-Hellman key exchanges.
The Diffie-Hellman key exchange algorithm is a public key distribution system that uses modular arithmetic to come to an agreed upon secret number (session key). So, as you can see, calling Diffie-Hellman an “encryption” algorithm is actually misleading because it can’t be used to encrypt or decrypt anything. And it’s not so much a key “exchange” as it is a key generation process. Yes, there are variables exchanged, but you’re still actually creating the key based on those exchanges.
Diffie-Hellman uses the exchange of public variables (numbers) to generate a shared solution known as a session key. This secret session key is what you’d use to exchange data in a secure channel that’s protected by symmetric encryption.
Check out this great video to see how the Diffie-Hellman key exchange process works using colors:
How Secure Are Symmetric Keys?
The strength of any cryptographic key depends on a few specific considerations.
- The length of the key,
- The randomness (entropy) of how it was generated, and
- How long it takes to reverse it to figure out is individual components.
Now, you may be wondering whether a cybercriminal could just reverse the process to guess the variables to calculate the numbers that were used. It’s possible, but the reality of that happening is so remote that it’s not practical. I say that because even though cybercriminals understand how these calculations work, it’s incredibly difficult to reverse the process to find out the secret number you or your recipient used to generate your matching session keys.
It goes back to the concept that was discussed in the video that shows the uses of mixing of specific colors to create a shared value. While it’s easy to combine colors to create the shared value, it’s virtually impossible to deconstruct those values to figure out exactly which shades of the colors were used to create them.
Furthermore, since the numbers that are used in these calculations are massive, it would take way longer than any cybercriminal would have during a session to figure them out. Even with the most current supercomputers, an attacker would have to spend hundreds — if not thousands of years — trying to figure out the individual numbers you both used. I don’t know about you, but we mortals don’t have that much time to spend on such tasks.
So, now that we know what symmetric encryption is and how it works, how is it used in the real world?
Examples of Where You’re Already Using Symmetric Encryption
Symmetric encryption is useful in many cases and has implementation opportunities across various industries. For example, symmetric encryption is useful for encrypting banking-related data as well as data storage.
Banking
Ever heard of PCI DSS? The Payment Card Industry Data Security Standards is a set of 12 requirements that businesses or organizations that accept credit card payments must adhere to. Symmetric encryption is a key component of PCI compliance, as it directly correlates to requirement No. 3, which focuses on protecting at-rest cardholder data.
This different from requirement No. 4, which focuses on protecting in-transit data. That’s all about using asymmetric encryption (basically, the SSL/TLS and HTTPS we were talking about earlier).
Data At Rest
Data at rest refers to the state of your data while it’s sitting on a server or a device. It’s not in transit, meaning that it’s not being sent across a network or the internet. So, consider the example of a private ledger or a diary. You write either highly valuable or sensitive information in it that you don’t want anyone other people to read. So, while you’re not sending it anywhere, it doesn’t mean that you want someone else to be able to read its contents should they manage to get their hands on it. At rest data encryption is what prevents that type of exposure from happening.
Wondering what products or services you use that incorporate symmetric encryption into their platforms or tools? Here’s just a handful of such services:
- CodeGuard — CodeGuard is a website backup tool that uses AES-256 encryption to secure your backups.
- Google Suite — Many of Google’s G Suite services use at-rest data encryption (in addition to in-transit encryption via HTTPS) to secure your data.
- Microsoft Azure — Azure Encryption uses symmetric encryption to encrypt and decrypt lots quantities of data quickly.
- SalesForce — The SaleForce Platform uses AES-256 encryption to secure data at rest.
HTTPS and Website Security
We already touched on this earlier. Remember how we talked about how symmetric encryption is a part of the HTTPS process? This is where asymmetric encryption is used to facilitate a key exchange between two parties, and then identical symmetric session keys are what’s used to actually process the encryption for the session.
So, this means that symmetric encryption is an integral component of website security.
Final Thoughts on Symmetric Key Encryption
Okay, we’ve reached the finish line. Needless to say, breaking down what symmetric key cryptography is and how symmetric encryption works is a lot to take in. I hope this article has provided you with insights that will help you better understand the process and its role in cybersecurity.
One quick note: This blog post is the first in a group of articles that we’re going to publish in the coming weeks that break down various aspects of symmetric encryption. So, be sure to keep an eye out and check back for those upcoming articles on Hashed Out as well.
Although symmetric cryptography is an old method of encryption, it still holds an invaluable place in our digital world.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown