Symmetric Encryption Algorithms: Live Long & Encrypt
Much like tribbles in Star Trek, symmetric encryption is everywhere. We’ll explore symmetric key algorithms and take you to places no non-IT person has gone before
Symmetric encryption algorithms are the underlying processes that make secure communications possible. If you were to put it into Star Trek-related terms, symmetric algorithms are the warp drive for your starship’s propulsion system. They’re integral to information security and are what help your business move forward with data encryption securely and at faster-than-light speeds.
(Yes, I know, I’m really flying my nerd flag high today. While fascinating, symmetric key algorithms aren’t exactly “light” or easy reading — so I’ve got to have some fun when writing. Damn it, Jim, I’m a cybersecurity writer, not a cryptographer.)
Make sure to refresh your coffee (or earl grey tea, if that’s more your speed). We’re about to take a deep dive into exploring what symmetric encryption algorithms are, why they’re important, and what the most common symmetric encryption algorithm types are.
Make it so.
Let’s hash it out.
Editor’s Note: This article is the first in a series of articles on symmetric encryption. Be sure to check out the related articles below:
- Symmetric Encryption 101: Definition, How It Works & When It’s Used
- Asymmetric vs Symmetric Encryption: Definitions & Differences
- Block Cipher vs Stream Cipher: What They Are & How They Work
What Is a Symmetric Algorithm and How Does It Work?
Symmetric algorithms are the cryptographic functions that are central to symmetric key encryption. They’re a set of instructions or steps that computers follow to perform specific tasks relating to encrypting and decrypting data.
Feel like you need a universal translator? Okay, let’s break this down a bit more.
Symmetric encryption algorithms are used (combined with an encryption key) to do two main things:
- Encrypt. Convert readable text (plaintext) into unreadable, encrypted text (ciphertext).
- Decrypt. Convert the ciphertext back to plaintext.
Symmetric encryption algorithms use the same encryption key for both encryption and decryption. (Unlike asymmetric encryption algorithms, which use two different keys.)
Encryption algorithms, in general, are based in mathematics and can range from very simple to very complex processes depending on their design. In the case of symmetric encryption algorithms, they’re paired with a single key to convert readable (plaintext) data into unintelligible gibberish (ciphertext). They then use the same key to then decrypt the ciphertext back into plaintext. And all of this is done in a way that ensures data confidentiality and privacy. Pretty cool, huh?
Symmetric encryption algorithms are actually known by a few different names:
- Symmetric key algorithms,
- Symmetric ciphers,
- Secret key algorithms, and
- Bulk ciphers. (We’ll talk more about bulk ciphers a little later.)
In general, the purpose or goal of encryption is to make it so that only someone with the key can decrypt and read the secret message. In case you need a quick reminder of how symmetric encryption works, here’s a quick overview:

In this graphic above, moving from left to right, you’ll see that you start with the plaintext, readable data. Once the symmetric encryption algorithm and key are applied to that data, it becomes unreadable ciphertext. The way to decrypt that message to decipher its meaning is to use a decryption key. In the case of symmetric encryption, the decryption key is identical to the key that was used to encrypt the data. Basically, you use the same key twice.
What Do Symmetric Encryption Algorithms Actually Do?
In a nutshell, a symmetric algorithm is a set of instructions in cryptography that use one key to encrypt and decrypt data. These encryption algorithms and keys are lightweight in the sense that they’re designed for speed in processing large blocks or streams of data. (This is why symmetric encryption algorithms are known as bulk ciphers.)
Asymmetric key algorithms and keys, on the other hand, are resource eaters. The keys are massive and are expensive to use at scale. What I mean is that they suck up a lot of your CPU processing resources and time, battery power, and bandwidth to execute.
Remember how we described symmetric algorithms as being a key component of your warp drive? Let’s continue with that analogy. So, if you were to think about what asymmetric encryption algorithms are, they’d be like the equivalent of the thrusters in the propulsion system. Sure, they’ll get you there eventually, but they’re not suitable for rapid encryption at scale.
However, they’re great for encrypting smaller batches of data in public channels. And asymmetric key exchanges (which we’ll talk more about shortly) are a great way to distribute keys in those insecure public channels.
This is why people often turn to symmetric encryption for encoding large amounts of data.
What Determines the Strength of a Symmetric Encryption Algorithm?
As you’ll soon discover, not all symmetric algorithms are created equally. They vary in terms of strength — but what exactly is does strength mean in cryptography? The short answer is that cryptographic strength is all about how hard it is for a hacker to break the encryption to gain access to the data. The longer answer, of course, may vary depending on the type of algorithm you evaluate. But, in general, cryptographic strength typically boils down to a few key traits:
- The length, randomness, and unpredictability of the symmetric key,
- The algorithm’s ability to withstand or be resistant to known attacks, and
- A lack of back doors or other intentional vulnerabilities.
Symmetric encryption can be a bit of a balancing act because you need algorithms and keys that are computationally hard yet practical enough to use with acceptable performance. You also need to ensure that you secure those keys to keep any data encrypted by those algorithms secure.
Symmetric Encryption Algorithms Can’t Stand On Their Own in Public Channels
While symmetric encryption algorithms might sound like the most logical tools for all types of online data encryption, it’s not quite that simple. Much like the ever-logical Spock and the charismatic Captain Kirk, symmetric encryption also has weaknesses — especially when used on their own in public channels. These weaknesses come in the form of key distribution and key management issues:
- You need a secure connection to distribute symmetric keys, and
- Trying to keep up with everyone who has a copy of the key could be a pain if you gave it out to a lot of people.
When using symmetric encryption, ideally, you and the person you’re communicating with sort out your secret key ahead of time (prior to using it for any data exchanges). This means that in order to share a symmetric key securely with someone, you’d need to meet up with them in person to give it to them. But what if you’re across the country from the other party? Or, worse, what if you’re on the other side of the world from them?
While this wouldn’t be an issue in the Star Trek universe, where you could simply transport from one place to another within seconds, this isn’t feasible in our 21st century transporterless world. Here, people are exchanging information with web servers worldwide every moment of every day. This means that people can’t meet up ahead of time to hand out or receive keys. So, we have to rely on other means to securely exchange keys with other parties.
This is where asymmetric algorithms — or, more specifically, key exchange protocols — come into play. Asymmetric key exchanges make it possible to exchange symmetric keys in otherwise insecure public channels. What you may or may not realize is that you’re actually using this combination of symmetric and asymmetric encryption techniques right now.
Asymmetric Techniques Make Secure Symmetric Encryption Possible Over the Internet
Let’s consider your connection to our website as an example. See that padlock icon in your browser? It means you’re connected to a secure website.
So, when you initially connected to TheSSLstore.com, your browser had to perform a process with our server that’s known as a TLS handshake. This handshake is a way for the server to prove to your browser that it’s legitimate and isn’t an imposter. (You know, ‘cause cybercriminals love to pretend to be other people to trick people in connecting with them. They’re kind of like Romulans in that way — always engaging in subterfuge.) The handshake process uses asymmetric encryption and asymmetric key exchange processes to do this.
- The asymmetric encryption process verifies the digital signatures.
- The asymmetric key exchange process encrypts the pre-master secret that your browser and the web server will use to create a symmetric session key.
Of course, there are a few versions of the handshake — TLS 1.0, TLS 1.2, TLS 1.3 — and there specific differences in how they work. (For example, the Internet Engineering Task Force [IETF] pushes for the strict use of forward-secrecy-only ciphers in TLS 1.3 — but that’s a topic for another time.) Just know that only the TLS 1.2 handshake should be the minimum used. As of October 2020, Qualys SSL Labs reports that 99% of sites support the TLS 1.2 protocol and 39.8% support the TLS 1.3 protocol.
We won’t get into the specifics of how the TLS handshake works here, but know that it involves the use of cipher suites. These groups of ciphers are what help to make it possible to establish a secure, HTTPS connection by determining which of each of the following to use:
- A protocol (TLS)
- An asymmetric key exchange algorithm (such as Diffie-Hellman)
- A bulk encryption cipher
- A digital signature
- A hash function (such as SHA2-2)
- A message authentication code (MAC) function
You can read more about the process in this explainer blog on how the TLS handshake works. But for now, let’s stay with the topic at hand of symmetric encryption algorithms.
The Two Types of Symmetric Algorithms (Ciphers)
During the symmetric encryption that takes place when you connect securely to a website, you’re using a bulk cipher to make that happen. There are two subcategories of bulk ciphers: block ciphers and stream ciphers.
Block Ciphers
In this type of cipher, plaintext data breaks down into fixed-length groups of bits known as blocks (which are typically connected via a process known as chaining). Each block then gets encrypted as a unit, which makes this process a bit slow. And if there’s not enough data to completely fill a block, “padding” (typically an agreed upon number of 0s) is then used to ensure that the blocks meet the fixed-length requirements.
The ideal block cipher has a massive key length that isn’t practical, so many modern ciphers have to scale back key sizes to make them usable. But just as a quick note: Unlike with asymmetric encryption, symmetric encryption key sizes don’t determine the size of the data blocks.
The majority of modern symmetric encryption algorithms fall within the block cipher camp, and these types of ciphers have broader usage and application opportunities. So, we’re mainly going to focus on them here. But if you’re wondering what the most popular or common stream ciphers are, don’t worry, we’ve got you covered.
Stream Ciphers
With this type of cipher, it encrypts plaintext data one bit at a time. As such, data gets processed in a stream rather than in chunks like in block ciphers. This makes the process less resource-intensive and faster to achieve.
Now, we’re not going to get into all of the specifics of block ciphers and stream ciphers — that’s a whole other topic. But the good news is that we’ve already written an article that covers block ciphers vs stream ciphers. So, be sure to check that one out for a more in-depth look at what they are and how they work.
Okay, now this is where things start to get exciting (or more complicated, depending on your perspective). With shared key encryption, there are several well-known symmetric key algorithms to know. Let’s break them all down to understand what they are and how they work.
Symmetric Algorithm List: The 3 Most Common Symmetric Algorithm Types
For this section, we’ve put together a symmetric algorithm list that will help us navigate the most common symmetric ciphers. We’ll start with one of the oldest and work our way up to the “latest and greatest” — meaning, the algorithm that we typically use today for modern symmetric encryption.
1. Data Encryption Standard (DES)
First up on our list is the data encryption standard. DES, also known as DEA (short for data encryption algorithm), is one of the earliest symmetric encryption algorithms that’s since been deprecated. It’s based on the Feistel Cipher (much like many other varieties of block ciphers) and was actually deemed one of the first symmetric algorithms to be adopted as a Federal Information Processing Standard (FIPS) in 1976.
DES dates back to the early 1970s when its original form (“Lucifer”) was developed by IBM cryptographer Horst Feistel. IBM reports that the encryption method was originally created at the behest of Lloyds Bank of the United Kingdom. The National Bureau of Standards (now known as the National Institute of Standards, or NIST for short) ended up seeking proposals for a commercial application for encryption, and IBM submitted a variation of it. It was even desired for use by the National Security Agency (NSA) to protect their data.
This type of symmetric encryption maps inputs of a specific length to outputs of a specific length. As such, it operates on 64-bit blocks — meaning that it could encrypt data in groups of up to 64 blocks simultaneously — and has a key size of 56 bits. There are also 8 additional parity bits to the key, which serve as a way to check for data transmission errors. However, it’s important to note that parity bits aren’t something you’d ever use for encryption.
This size key is actually very small by today’s standards, which makes it highly susceptible to brute force attacks. Also, the key and block lengths differ from the original Lucifer key and block lengths, both of which were reduced from 128 bits.
To learn more about how DES encryption and Feistel Networks work, check out this great video from Coursera and Stanford University.
The Data Encryption Standard (DES) document (FIPS PUB 46-3) was officially withdrawn on May 19, 2005, along with the documents FIPS 74 and FIPS 81. The National institute of Standards and Technology’s Secretary of Commerce published the following in the Federal Register:
“These FIPS are withdrawn because FIPS 46-3, DES, no longer provides the security that is needed to protect Federal government information. FIPS 74 and 81 are associated standards that provide for the implementation and operation of the DES.”
DES encryption was succeeded by triple data encryption algorithm (TDEA) for some applications, although not all. However, DES was primarily superseded as a recommendation by the advanced encryption standard, or what’s known as AES encryption, in 2000. This is what we most commonly use today for symmetric encryption.
Now, let’s explore those two other types of symmetric encryption algorithms.
2. Triple Data Encryption Algorithm (TDEA)
The triple data encryption algorithm, which was created in the late 1990s, is a bit tricky as it actually goes by several abbreviations: TDEA, TDES, and 3DES. But as you can probably guess from its name, 3DES is based on the concept of DES but with a twist.
Unlike its predecessor, TDEA uses multiple separate keys to encrypt data — one variation of TDEA uses two keys and the other variation uses three keys (hence the “triple” in its name). The stronger of the two is the one that uses three keys.
Here’s an illustration of how the three-key TDEA process works:
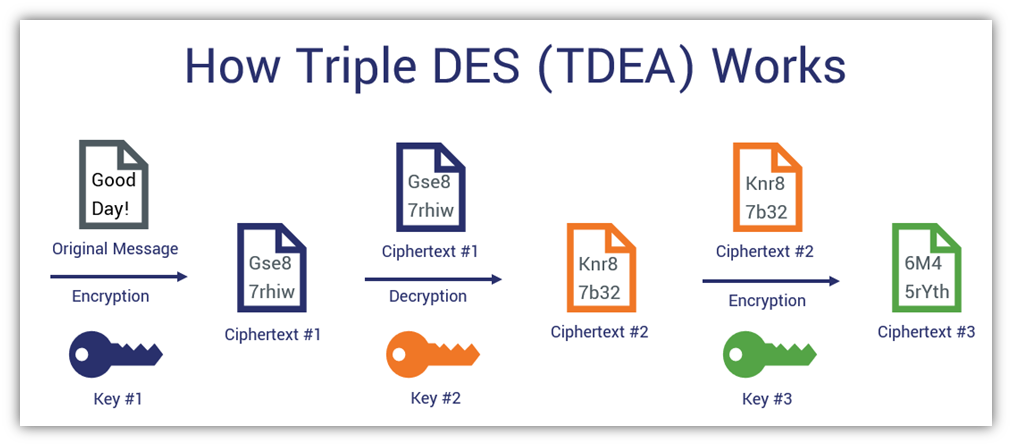
The use of multiple keys makes processing data slow and increases the computational overhead, which is why organizations often skipped over 3DES and moved straight on to using AES.
TDEA operates using a decent 168-bit key size. However, like DES, 3DES also operates on small 64-bit blocks. Its small block size made it susceptible to the sweet32 vulnerability (CVE-2016-2183 and CVE-2016-6329), or what’s known as the sweet32 birthday attack. This exploit takes advantage of a vulnerability that enables unintended parties to access portions of DES/TDEA-encrypted data.
The TDEA symmetric key encryption algorithm is set to deprecate in terms of being useful for cryptographic protection in 2023. However, in the meantime, NIST SP 800-76 Rev. 2 specifies that 3DES can be used by federal government organizations to protect sensitive unclassified data so long as it’s used “within the context of a total security program.” Such a program would include:
- Good information security practices,
- Strong physical security procedures, and
- Computer network or system access controls.
3. Advanced Encryption Standard (AES)
AES is the most common type of symmetric encryption algorithm that we use today. In fact, even the NSA uses AES encryption to help secure its sensitive data.
AES is a variant of the Rijndael family of symmetric encryption algorithms. Unlike its DES or TDEA counterparts, it’s based on a substitution-permutation network. So, it uses this as its foundation in lieu of the Feistel cipher. You’ll find the advanced encryption standard in use for everything from SSL/TLS encryption to wireless and processor security. It’s fast, secure, and doesn’t noticeably increase your processing overhead (at least, when you use the right key).
AES operates on block sizes of 128 bits, regardless of the key size used, and performs encryption operations in multiple rounds.
There’s a total of four AES encryption sub-processes:
- AddRoundKey
- SubBytes
- ShiftRows
- MixColumns
The rounds, which are performed on the plaintext data, uses substitutions from a lookup table. So, one of the rounds looks akin to this:
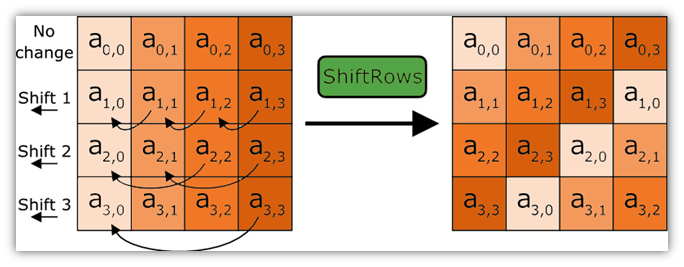
AES, which became the new FIPS-approved encryption standard after replacing DES and superseding 3DES, has a maximum key size of up to 256 bits. This is about 4.5 times larger than a DES key. Any larger, and it wouldn’t be practical for at-scale applications. Now, the size of the key determines how many rounds of operations will execute — for example, a 128-bit key will have 10 rounds, whereas a 256-bit key will have 14.
Of course, AES encryption is incredibly strong. So, any attempts to crack AES via brute force using modern computer technology is “futile,” as a certain collective of cybernetic individuals love to say. Even Lt. Commander Data would likely struggle with such a computational effort. I say that because even quantum computers aren’t expected to have as big of an effect on symmetric encryption algorithm as it will on, say, modern asymmetric encryption methods. (Symmetric encryption methods would require larger keys to be quantum resistant, whereas public key methods will no longer be secure — period.)
For a more in depth look at the advanced encryption standard, be sure to check out our other article on the topic. There, you’ll get a highly technical look at how AES works.
Of Course, These Aren’t the Only Three Symmetric Algorithms In Use…
There are plenty of other types of symmetric encryption algorithms that are useful for different purposes and cryptographic functions. Just to give you a quick taste, the list of some of these algorithms include:
- International Data Encryption Algorithm (IDEA, a 64-bit cipher with a 128-bit key),
- Blowfish (a 64-bit cipher with keys up to 448 bits),
- Twofish (a 128-bit cipher with keys up to 256 bits),
- Multiple Rivest Ciphers (including RC2, RC4, RC5, RC6),
- KASUMI (a cipher that uses a 128-bit key,
- SALSA20, and
- CHACHA20.
Of course, there are other ciphers, too — but we’re not going to include them all here. But this at least gives you some examples of what’s out there as far as AES algorithms are concerned.
Where You’ll Find Symmetric Algorithms At Work
Symmetric encryption algorithms, when used on their own, are best suited for encrypting data at rest or in non-public channels. I say that because they’re often found protecting at-rest data in various situations, including databases, online services, and banking-related transactions. (The latter is because the Payment Card Industry Data Security Standards, or PCI DSS for short, requires it.)
However, those aren’t the only places they’re useful. Oh, no — you’ll also find symmetric algorithms in use across the internet. When you use them in conjunction with asymmetric encryption for key exchange — such as when you connect to a secure website — then symmetric encryption comes into play with services such as:
- Website data exchanges
- Google’s G Suite of online services
- CodeGuard website backup tool
- SalesForce platform
What We Hashed Out on Symmetric Encryption Algorithms (TL;DR)
Didn’t feel like diving into all of the technical mumbo-jumbo? (Or didn’t feel like reading through my nerdy Star Trek comparisons of symmetric encryption algorithms?) No worries. Here are a few of the main takeaways from this article on symmetric key algorithms:
- Encryption algorithms are basically step-by-step directions for performing cryptographic functions (such as encryption, decryption, hashing, etc.). Algorithms come in asymmetric and symmetric varieties. In the first, one key encrypts data and another decrypts data. In the latter, one key performs both the encryption and decryption functions.
- Symmetric algorithms are efficient processes that are designed for encrypting data in secure, non-public-facing channels.
- A process known as a TLS handshake makes it possible for you to use a form of symmetric encryption in public channels.
- There are many different types of symmetric key algorithms that have been used in recent years. Three of the most common include DES, TDEA/3DES, and AES.
Be sure to stay tuned for our next chapter in this blog series on symmetric encryption in the coming weeks. And until next time… live long and proper.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown