Google Chrome Adds Support for a Hybrid Post-Quantum Cryptographic Algorithm
If you’ve been waiting to put quantum-resistant encryption to work to protect your organization’s infrastructure and data, then your wait is over. Chrome rolled out a quantum hybrid key agreement mechanism in its latest release (version 116) on Aug. 15.
On Aug. 10, the Chromium Project announced in a blog post by Devon O’Brien its adoption of a hybrid cryptographic algorithm (X25519Kyber768) for Chrome and Google Servers. The goal is to help organizations globally secure their data against future quantum computing-based threats while ensuring security against today’s cryptographic threats.
In December 2022, the U.S. Congress passed legislation encouraging federal agencies to adopt quantum-resistant cryptography. Some quantum computing (QC) algorithms are already being used by companies like Amazon Web Services (AWS), Cloudflare, and IBM. While widespread adoption of quantum computers will be great when used by well-intentioned people, it also poses a significant threat should that technology fall into the wrong hands.
From an organizational security perspective, Google’s move represents the first real opportunity for users to use post quantum cryptography (PQC) for HTTPS. But what does this mean for your business and the security of your customers and users, whose data you’re entrusted to protect?
Let’s hash it out.
Overview: Google Chrome 116 Adds Support for Its First Public Post Quantum Algorithm
Google is testing new PQC algorithms as part of its multi-year goal of preparing for the PQC future. Starting officially with Chrome version 116, the browser has added support for a quantum-resistant algorithm called X25519Kyber768.
As Google explains, the algorithm is a “hybrid mechanism” that “combines the output of two cryptographic algorithms to create the session key used to encrypt the bulk of the TLS connection.” The two algorithms used are X25519 (an elliptic curve algorithm already in use) and Kyber-768 (a winner of the NIST PQC competition).
Google ran a test several years ago where they rolled out another quantum computing hybrid algorithm, CECPQ1, to a limited group of Chrome Canary (the experimental version of Chrome) users, but this is the first algorithm rolled out for general use.
PQC Is Now Available for Both Clients and Servers
We’ve been talking about post-quantum encryption for a while, and this is the first algorithm to be supported by commonly used clients (browsers) and servers.
Alongside Google Chrome’s support:
- Google announced that they are also rolling out support for X25519Kyber768 to Google Servers.
- Cloudflare previously announced they had added support for Kyber on “all websites and APIs served through Cloudflare.”
Of course, we don’t want to overstate what’s happened here — this is just one algorithm being supported by one client and a couple of server providers. There are many other steps needed to migrate the internet to post-quantum cryptography (quantum-resistant digital signatures, for example), but this is a very tangible milestone in the journey.
If you want to know more details about quantum cryptography, what the changes are regarding the hybrid algorithm, and why it’s a smart move, then keep reading. But first, we want to address how to check what cryptographic security measures you’re currently using and how to enable them in Chrome.
How to Tell If You Have the PQC Hybrid Algorithm Enabled in Chrome
Want to see if your version of Chrome is set to enable post-quantum security? You can do this easily using the Cloudflare Research PQC Key Agreement checker tool:
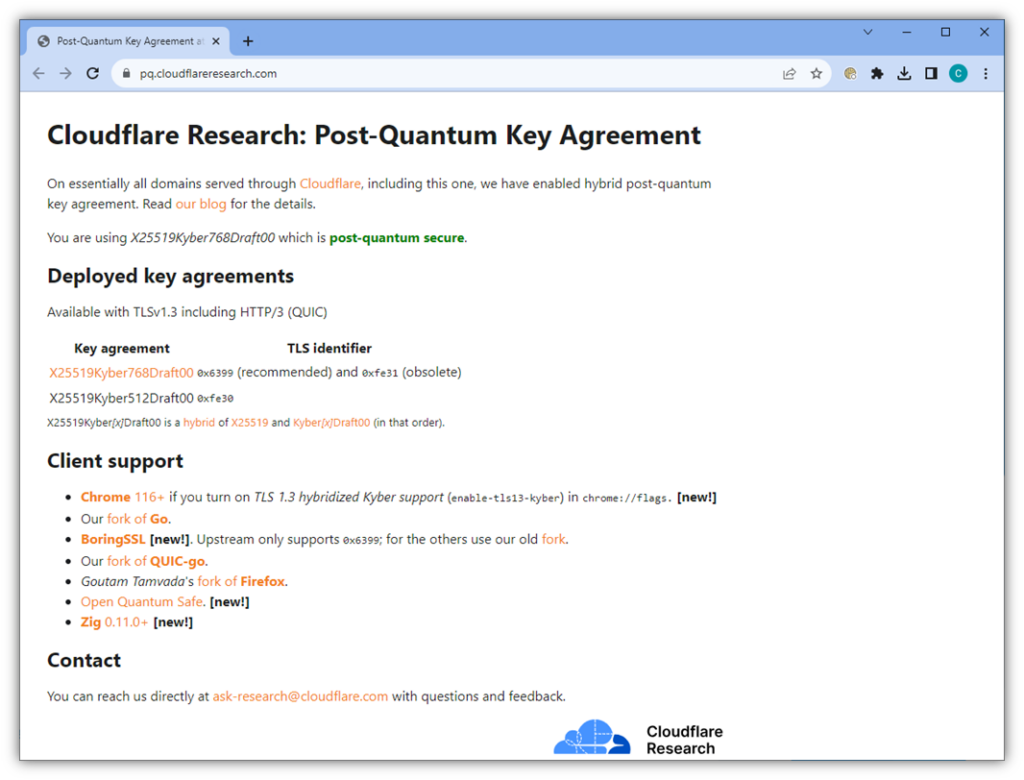
Otherwise, you can check to see which encryption algorithms Chrome is using for a specific website connection in Chrome’s Developer’s Tools.
To access this screen, click on Chrome’s menu (the three stacked dots in the top-right corner of your browser window. Then navigate to More Tools > Developer Tools and select the Security tab):
Here’s an example of what Chrome displays if the client and/or server don’t have Kyber enabled (we’re using TheSSLstore.com as an example):
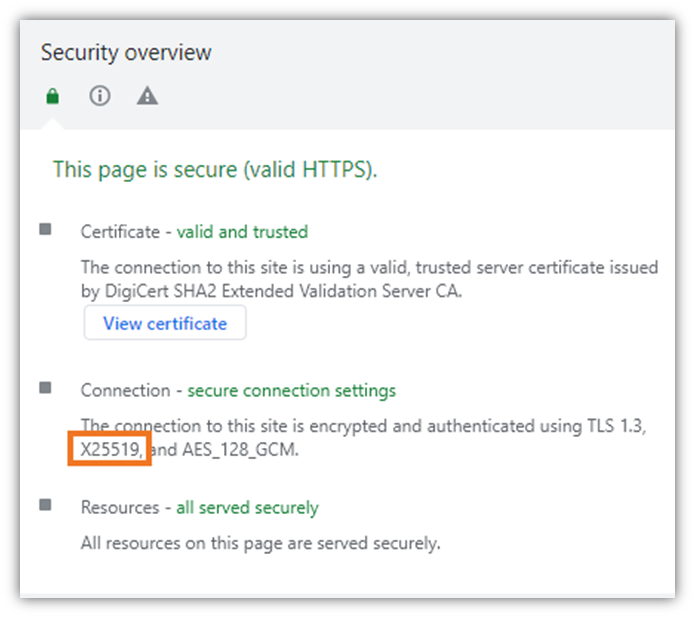
This tells me that The SSL Store is using the X25519 key agreement algorithm and has TLS 1.3 enabled. But what if you want to go ahead and enable X25519Kyber768 instead?
It’s time to explore how to enable this hybrid quantum-resistant algorithm in Chrome.
How to Enable Client Support of Kyber in Google Chrome 116
NOTE: The following directions also work in Google Chrome 115 as well (behind a flag).
Open your browser and type the following in the web address bar: chrome://flags.
This will open a new window titled “Experiments,” where you can choose to enable or disable experimental features. In the top search bar, start typing TLS 1.3 hybridized Kyber support and you should see the search result pop up right away.
If your browser is set to Default, change it to Enabled instead:
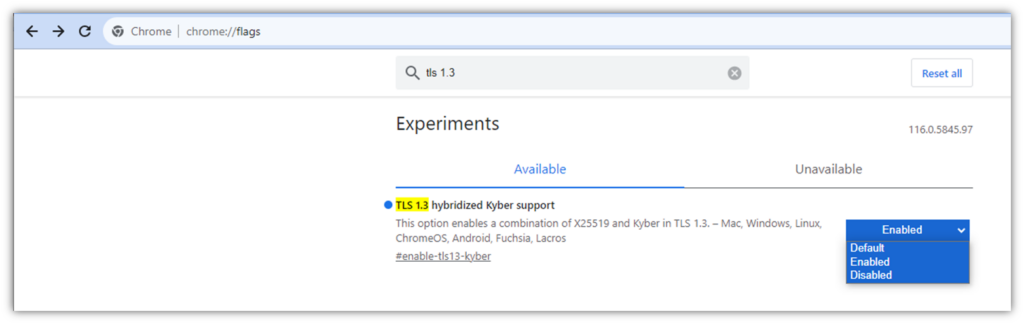
Chrome will then inform you that the change will take place once you relaunch the browser. (Don’t worry, it’ll be quick and will re-load all of your existing tabs right away.)
Here’s what it looks like when Kyber is enabled:
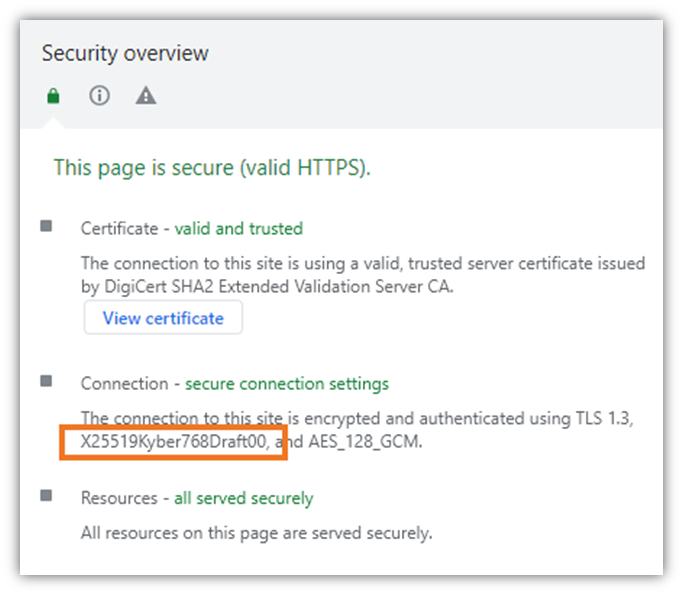
Let’s Go Back to the Basics: What Is Quantum Cryptography?
Just in case quantum computers aren’t something you’re very familiar with, let’s quickly review what they are and how they work. Quantum computers are supercomputers that currently exist only in laboratory environments and use a quantum mechanics principle called superposition to process information differently from classical (modern) computers.
Now, we sense that your eyes are probably starting to glaze over, so let’s simplify this a bit:
- Modern computers process bits (1s or 0s) individually. A traditional computer views bits (values of 1 or 0) of data in one of two states. As such, it processes each bit of data independently as either a 1 or 0. This requires higher computing costs and slower processing speeds.
- Quantum computers process them differently, using quantum bits (called “qubits”), which can represent 1s and 0s simultaneously. A quantum computer views each bit of data as existing in both states simultaneously (i.e., it can be both a 1 and 0 at the same time). This change in approach exponentially increases processing power and shrinks processing times.
Here’s a nifty graphic animated illustration from Natasha Hanacek/NIST that illustrates this concept in a simple way:

The concept of quantum computing has been around since the 1970s, but concerns about what this new technology would mean for data security really gained traction in the 80s and early 90s. It was then that mathematician Peter Shor shared his groundbreaking algorithm and the first quantum computer was created.
(NOTE: If you want to dive into the nitty-gritty of superposition and how quantum computers process data, check out notes from Schor’s Fall 2022 lecture notes.)
To combat the significantly faster processing speeds of quantum computers, cyber security experts need to have new tools in their toolbox. This is where quantum-resistant cryptographic algorithms and key agreement functions come into play.
Enter X25519Kyber768, a Hybrid Key Agreement Algorithm
Although the header of this section looks like something akin to a math problem you had to solve in high school math classes, I can promise that this is something very different. X25519Kyber768 is a combination of two post-quantum cryptography (PQC) key-related security mechanisms:
- X25519 — This is a modern key agreement algorithm we use today that’s based on elliptic curve cryptography (ECC). A key agreement function enables two parties to agree upon a shared secret that they can use to communicate securely in an open connection. This key is generated using points on a specific type of elliptic curve (Curve25519).
- Kyber-768 — Kyber is one of the finalist post-quantum public-key key encapsulation method (KEM) and encryption schemes selected by the National Institute of Standards and Technology (NIST). It’s a way to protect data confidentiality and offer authentication in place of cryptographic signatures that require less computational power. Kyber-786 is roughly the equivalent of AES-192 in terms of the data security (i.e., encryption) it offers.
Key encapsulation methods (KEMs) involve the use of two algorithms: encapsulation and decapsulation. So, let’s take a moment to consider what this will look like.
- Essentially, a client will create a new symmetric secret (i.e., a X25519 key) for a session to encrypt data and convert it into ciphertext.
- Before it can be used, the symmetric secret will be encapsulated (“encap” for short) with the server’s public key using the Kyber-768 KEM encapsulation algorithm. (Think of it like placing the key inside a box and locking it; doing this protects the key in transit by providing an additional layer of security.)
- When the server receives the message, it uses its corresponding private key with a decapsulation algorithm (“decap”) to decrypt the shared key data.
Here’s a quick look at how this process works:
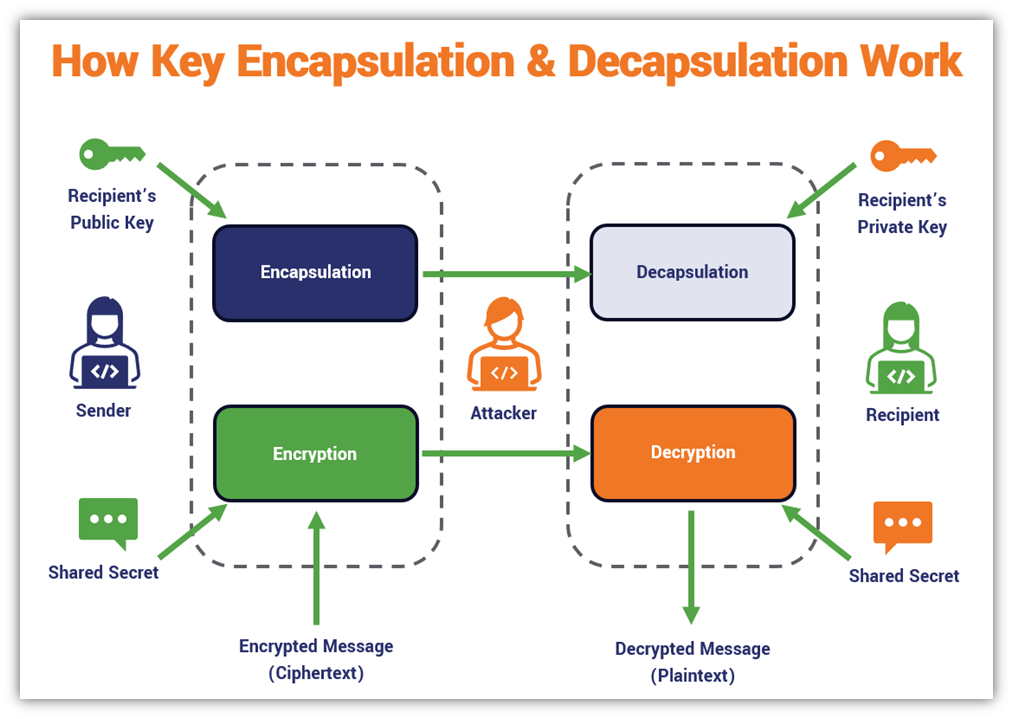
Although Kyber is still in draft form and won’t be standardized until 2024, early implementations like what Google is doing are thought to promote greater interoperability as more companies add support for PQC.
Why Using a Hybrid Approach Is Good for Data Security Now and in the Future
It boils down to securing data against both the attacks we face today and the quantum computing attacks we’ll face tomorrow (or, more realistically, years from now). This ensures that the connection will still be secure even if one of the key agreement methods is broken.
Devon O’Brien, Technical Program Manager at Chrome Security, explained more about this in his Chromium blog post: “Hybrid mechanisms such as X25519Kyber768 provide the flexibility to deploy and test new quantum-resistant algorithms while ensuring that connections are still protected by an existing secure algorithm.”
But why is all of this necessary? O’Brien says it has to do with cryptanalysis attacks known as “Harvest Now, Decrypt Later” (HNDL) attacks. In these attacks, the bad guy stores a bunch of your company’s encrypted data now, so they can decrypt it years down the road when more powerful quantum technology becomes available.
Regardless of whether the bad actor is a cybercriminal acting on their own or a nation-state actor with an even darker agenda, it’s easy to see the cause for concern regarding HNDL attacks.
A 2022 Deloitte survey shows that more than 50% of organizations’ respondents believe they’re at risk of HNDL attacks; another 29% indicate that they don’t know.
Some Types of Data Have Longer Lifespans Than Others
Just think about it. Although your credit card and login credentials may be inconvenient to change, they have short lifespans because attackers know that your account info can be changed relatively quickly when things go wrong. But some types of personal data (highlighted below) have significantly longer lifespans because they’re exceptionally harder (if not impossible) to change — e.g., your name, social security number, date of birth, etc.
Now, let’s think about this in terms of your organization. If you’re like most organizations, you’ve got a treasure trove of data that you’re responsible for protecting:
- Employees’ personally identifiable information (PII),
- Customers’ PII and account-related information,
- Trade secrets (e.g., Coca-Cola’s recipe or KFC’s chicken spices mix), and
- National secrets (e.g., identities of spies or blueprints for nuclear weapons)
Now, imagine that information falling into the wrong hands. The idea of HNDL attacks is similar to how pirates buried their gold so they could return for it later. If an attacker steals your sensitive data and it’s not secured with a hybrid PQC algorithm, all they have to do is sit on it until the time when quantum technology becomes available. Then they’ll be able to use that technology to carry out identity theft and a wealth of other attacks.
This is where implementing PQC hybrid algorithms within your organization’s IT environment sooner rather than later can help.
Google Implements PQC to Protect Data Now Against Future Decryption Attacks
“[…] any encrypted messages sent today could be stored until those computers are eventually built,” Matthew Green, a Johns Hopkins cryptography professor told The Register in an email. “By adding post-quantum encryption to today’s connections, that threat is eliminated.”
So, how exactly does using quantum-resistant cryptography help in the scenario? In modern SSL/TLS connections, we rely on public key encryption to enable clients and servers to agree upon a shared (symmetric) session key they can use to communicate securely for the rest of the session. But there are a few problems here:
- Public key cryptography relies on ciphers like RSA that use large prime numbers, which can be factored and broken (a la Shor’s algorithm).
- While symmetric ciphers are thought to be secure, the methods we rely on now to generate symmetric keys aren’t considered safe against PQC.
Google aims to replace the industry’s existing symmetric key agreement methods with quantum-resistant session keys. The thought process here is that by securing the connections organizations and businesses use now to transmit sensitive information using those PQC keys, even once quantum computers are available, attackers won’t be able to decrypt data they previously harvested.
Let’s Wrap This Up
Although quantum cryptography has been around for several decades, it still represents both a technological marvel and secret threat that looms on the horizon. Although we don’t know a specific date, experts agree that it is coming… it’s just a matter of when, not if. So, it’s good to Google and several other tech industry leaders are taking steps to help organizations start the process.
Google’s move to integrate this hybrid PQC algorithm into its browser and servers is great because it provides an opportunity to protect data now against modern attacks while preparing for the quantum-related threats still to come. Instead of kicking the can down the road to deal with “later,” adopting a hybrid PQC approach now helps you kill two birds with one stone.
Quantum computing isn’t something to freak out about now. However, now is the time to start preparing for its eventual arrival.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)





 (3 votes, average: 4.67 out of 5, rated)
(3 votes, average: 4.67 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown