Google Chrome to Join Apple’s Safari in One Year Certificate Validity
One year validity for SSL/TLS certificates has been a hot topic of conversation within the CA/B Forum for years — Google’s latest announcement goes to show that shorter validity is absolutely happening
It’s no secret, Google has been championing shorter certificate validity within the CA/Browser Forum (CA/B Forum) for years. At the end of last week, a well-known voice within the forum posted on Twitter that the tech giant will be making the switch to a one year validity period of 398 days for SSL/TLS certificates starting Sept. 1. This might sound like a big move, but it doesn’t actually change anything because it was already happening.
Although their past efforts to push one year validity had previously failed, Google is ultimately getting what they want after Apple announced in February that they were leading the charge on this one. That made for a nice early birthday present for Google. But hey, it’s all for the greater good of security, right?
So, what does this actually mean to you as a website owner or administrator? Or as a certificate reseller?
Let’s hash it out.
For Most People, Google’s Move to One Year Validity Doesn’t Really Change Anything
On June 11, Dean Coclin, chair emeritus of the CA/B Forum, broke the news on Twitter that Google will be following Apple’s lead in limiting public SSL/TLS certificates starting Sept. 1:
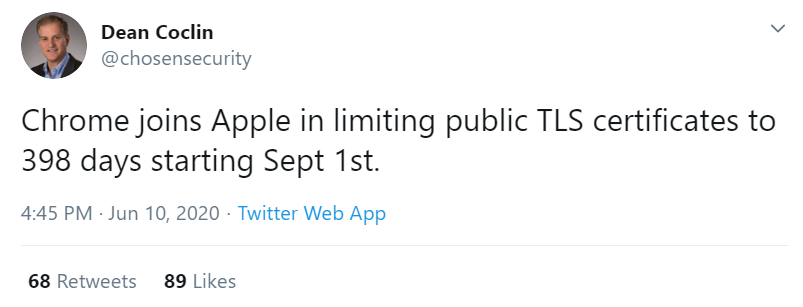
Technically, we’re still waiting to read the minutes from the meeting. (They haven’t been posted yet because the meeting minutes have to be approved at the next meeting on June 18.)
The idea behind the move to one year validity is that certificates with shorter lifespans have to be issued more frequently, to make them more secure. And this is great, we’re all for more secure certificates. But on a granular level, what does this move by Google really mean to a website administrator/owner or an SSL/TLS certificate reseller?
In reality, not much. Despite how it may seem, not a lot has really changed for site admins.
The reason we say that is that Google’s announcement is more of a formality than anything else. Basically, when we broke the news about Apple’s hushed announcement of their move to one year certificate validity back in February, we shared that their browser would only support certificates with shortened validity periods starting Sept. 1. We knew this move would instigate the other browsers to do the same, and it would force the world’s certificate authorities to start issuing certificates to comply. It was only a matter of time before everyone would have to fall in line.
And considering that Google Chrome and Safari are the world’s two leading web browsers in terms of market share, it’s no surprise that the other browsers will simply follow suit.
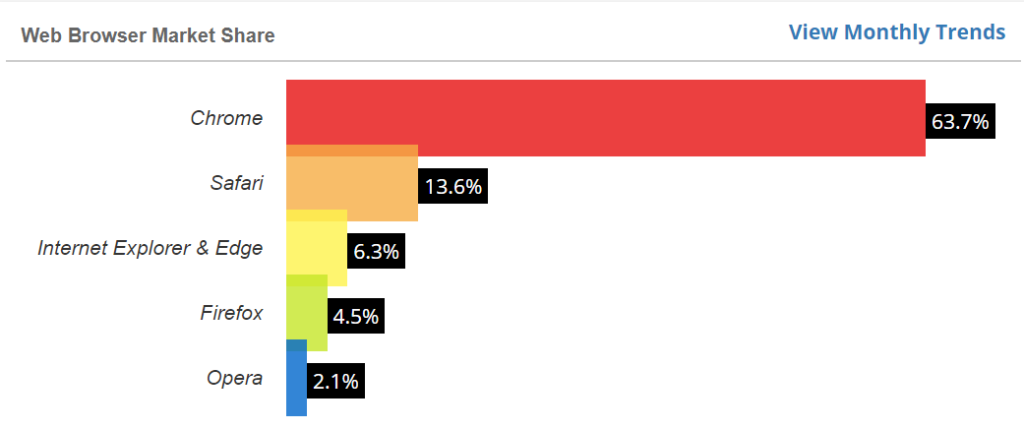
This means that regardless of whether Google chose to make an announcement, the industry was already moving to one year validity by Sept. 1 at the latest.
So, If “Not Much Has Changed,” Why Are We Even Talking About This?
Well, even if nothing has truly changed from a 30,000-foot perspective, it’s still worth mentioning that Google is making the change official. (We also like to keep our readers in the loop about the changes that go on within the industry, so there’s that, too.) But this change doesn’t mean that life is going to suck for the people who handle certificates — let’s rehash how this move to one year validity will affect your organization.
How One Year Validity Affects Site Admins
Going from two year certificate validity to one year means that your certificate lifecycle is, essentially, cut in half. This means that there will be double the chance to miss an expiration and that you’ll need to prioritize security more than ever.
But it’s not all bad. As a website admin, this may mean that you’ll have more interaction with the site owner. This can serve as a touch point opportunity — you know, where you can gently remind the customer of your value or even sell them something new. Either way, it’s win-win opportunity for you.
If you’re both the site admin and owner, then this change means that you’ll simply have a little more busywork in terms of certificate management. The plus side, though, is that you’ll have greater confidence that you’re more secure because:
- Your certificate keys are rotated more frequently
- Your certificates have the most recent information
- You don’t have to worry as much about things like hash algorithms being deprecated mid-lifecycle (and you not knowing it), resulting in your certificates no longer being valid
This also serves as an important reminder for our site admins: If you’re someone who wants to continue taking advantage of certificates with two-year certificate validity, you’d best get a move-on. Buy your certificates now so that, barring any revocations, they’ll be trusted by both Safari and Chrome for the next two years. Essentially, they’ll be grandfathered in come Sept. 1. But if you choose to wait to purchase your certificates until on or after Sept. 1, then you’re going to be limited to one-year validity.
SSL ‘Subcription’ Packages Offer Up to 5 Year Coverage
Of course, even after Sept. 1, you can still buy coverage for 1-, 2-, 3-, 4- or 5-year certificates through multi-year subscription plans. Commercial certificate authorities (CAs) like Sectigo and DigitCert are rolling out these plans prior to Sept. 1 to enable their customers to continue taking advantage of multi-year discounts. Basically, the more years you buy per certificate, the lower the cost will be per year. This saves you more money in the long run. However, the difference will be that you’ll have to re-issue your certificates each year. Sorry, there’s just no way around it.
Now’s a Great Time to Implement Certificate Automation
If you’re worried that managing hundreds or potentially thousands of certificates is going to be an issue for your organization, you have good reason. But there’s a silver lining: There are certificate lifecycle automation tools that you can use to keep everything straight regarding certificate issuance, expirations, revocations, and renewals.
How One Year Validity Affects Certificate Providers
Basically, the message here to resellers is to just keep doing what you’re doing in terms of selling two year certs. That is, until Aug. 31 — after that, any certificates that you sell (starting Sept. 1) will need to be re-issued annually by your customers.
So, be sure to communicate the upcoming one year validity change to your customers so they can take advantage of the two year certs while they still have the chance. Otherwise, after Sept. 1, be sure to remind all of your customers of the one year expiration so that they can reissue their certificates before they expire (and you can avoid a bunch of angry phone calls or emails).
Basically, be proactive and helpful. Providing the best service to your customers also entails keeping them informed about the changes going on within the industry with regard to the browsers.
Final Thoughts
Google’s latest announcement, although it sounds major, it’s just one more step toward the inevitability of one year validation for SSL/TLS certificates. And since Apple cleared the way for them to do it with their ask-for-forgiveness-instead-of-permission approach, Google has clear passage to do what they’ve longed to do for several years. The only change is that they’ve now put their official stamp on it. Starting Sept. 1, 2020, public SSL/TLS certificates will only be issued with a one year validity period from all of the major certificate authorities.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown