PKI Management: Private Key & Certificate Lifecycle Management Best Practices
Keyfactor’s 2021 Executive Survey shows that 96% of IT security execs view PKI management as critical to zero-trust architecture. Here are five PKI certificate and key management best practices your company can implement now
PKI management, or the management of your organization’s public key infrastructure and its components, is integral to your organization’s IT and data security. This process involves proactively managing the digital certificates and cryptographic keys that make public key encryption possible. This cryptographic framework of processes and technologies is the backbone of internet security.
Having clear visibility and control of your certificate and key lifecycles is at the heart of PKI management. It’s the difference between knowing that you’ve taken all the necessary steps to ensure your sensitive data is secure versus leaving it at risk of falling into the wrong hands. And there are certain PKI management best practices and approaches every organization should implement to secure their cryptographic keys and certificates.
But what does it mean to manage your PKI certificate and key lifecycles? And what are the PKI certificate and key management best practices you should follow to ensure your PKI management processes are up to snuff?
Let’s hash it out.
What Is PKI Management?
PKI management is a combination of processes, technologies, and policies that allow you to control PKI components’ lifecycles (i.e., digital certificates and public-private key pairs.) In a nutshell, the goal of PKI management is to:
- Ensure sensitive data remains securely encrypted by avoiding encryption vulnerabilities or decryption key disclosures to unauthorized parties.
- Avoid downtime caused by certificate expirations or related issues.
PKI lifecycle management relates to everything from how these cryptographic assets are created, stored, and distributed to how they’re used, destroyed, or revoked. PKI management is all about managing everything relating to certificate and key lifecycles and their functions, including:
- Requesting and generating new digital certificates,
- Generating and activating cryptographic keypairs for those certificates,
- Distributing and using the digital certificates,
- Securely storing and backing up your cryptographic keys,
- Monitoring and reporting all certificate and their corresponding keys,
- Renewing existing valid certificates,
- Re-issuing expired certificates,
- Revoking compromised certificates and keys,
- Recovering keys (in specific circumstances), and
- Securely destroying keys.
Managing your PKI lifecycle applies to both private and public CA environments — which we’ll speak more to in a little bit — as well as hybrid environments. And regardless of whether you choose to host your CA environment in-house or rely on a third-party managed PKI service provider, someone is going to have to ensure that your public key infrastructure and its components are properly managed.
Implementing certificate and key management best practices is an important part of PKI management. Following PKI management best practices:
- Gives you total visibility of your PKI environment and all of its components.
- Helps you ensure your organization’s public key encryption systems are operating correctly.
- Enables you to ensure your PKI systems meet standards and regulatory requirements (and respond quickly to changes).
- Ensures all privileged users are informed about who is responsible for what.
- Helps you stay ahead of certificate expirations and respond quickly to revocations.
- Frees you up from important but monotonous tasks to focus on other critical functions.
How Public and Private PKI Factor Into PKI Management
Now, it’s important to note that there are differences when it comes to managing and using private and public certification authorities, or what’s more commonly known as certificate authorities or CAs. (Sometimes, people also refer to these environments as private PKI and public PKI). In part, it’s because public PKI and private PKI serve different purposes — public CA certificates are for public-facing environments, whereas private CA certificates and keys are intended for internal (non-public) environments only. As such, one is publicly trusted automatically while the other is not.
- Public PKI digital certificates. A publicly trusted CA issues public PKI certificates from their trusted roots. This provides a verifiable, universal certificate chain that browsers, operating systems, and many major applications trust automatically. This so-called “chain of trust” is what makes messages like this display in your browser:
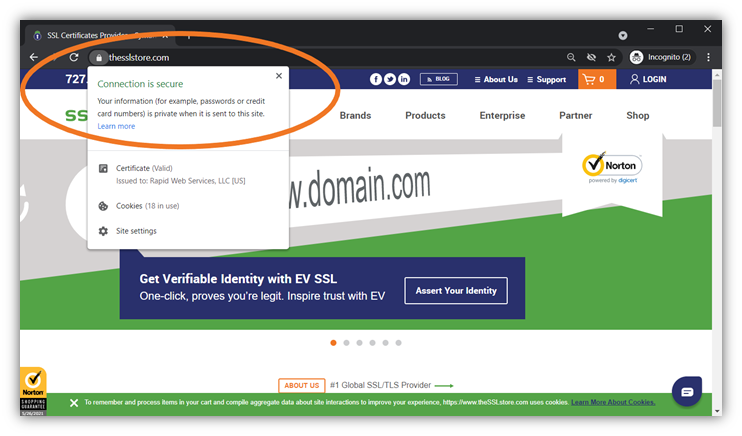
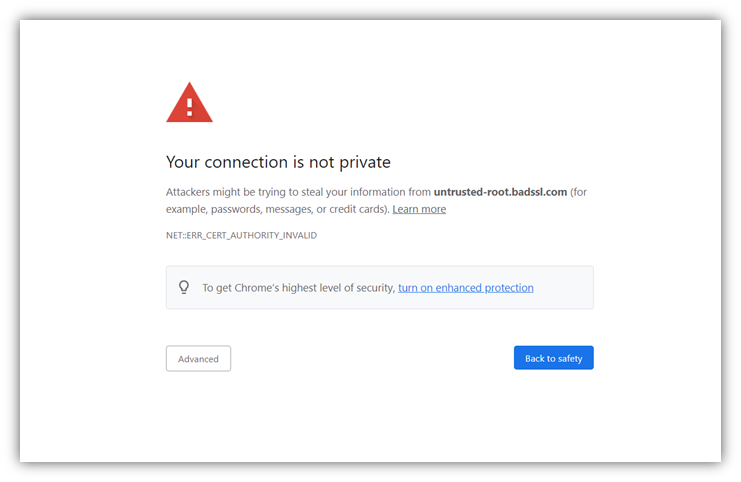
- Private PKI digital certificates. These certificates are issued by a private CA (i.e., a CA you own and control) rather than a publicly trusted third-party CA. They’re required to secure devices without a public IP address/hostname/identity such as IoT devices. However, they aren’t trusted by browsers or other external parties without you first having to distribute your private root to them manually. If you accidentally use a private PKI certificate on a public-facing site, you’ll get a warning like this:
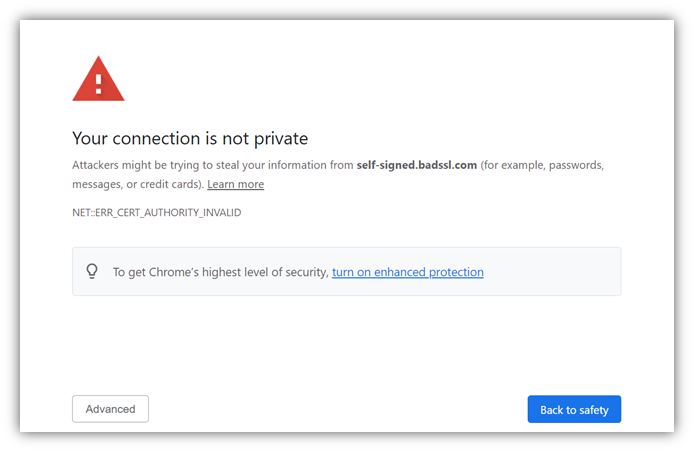
The good news is that you don’t have to choose one versus the other. Many companies opt to use a hybrid public-private PKI approach that allows them the benefits of using public CA certificates in external environments and private CA certificates for internal ones.
This may leave you wondering how companies deploy private CAs. There are a few ways to go about this. Some companies:
- Host and manage their private CA internally.
- Use a third-party service provider to host either or both their private PKI and public CA certificates.
- Implement a hybrid model if you want to take on some PKI management responsibilities but not all of them.
There are pros and cons to each deployment method. Often, the determining factors for companies often boil down to one of the following:
- Deployment and management costs,
- How much internal control they wish to retain,
- Availability of resources (time, people, and finances), and
- Knowledge and/or skills of their employees.
Effective PKI Management Is Especially Critical If You Run Your Own CA
It’s no secret that private PKI offers a lot of advantages. But it’s important also to recognize that managing private PKI requires significantly more management-related tasks than public PKI — it’s not just about managing certificates alone. It’s a more complicated, time-consuming and costly endeavor.
Here’s a nice way to sum up the difference between managing public and private PKIs nicely: it’s the difference between maintaining a fleet of vehicles versus maintaining a fleet of vehicles and the manufacturing plant where they’re built.
Deciding whether public PKI may (or may not) be a good option for your organization often comes down to the size of your organization and the resources you have at your disposal. When you build a private CA from the ground up, there’s a lot that goes into it. Some of the additional things you’ll have to handle when operating private PKI include:
- Purchasing, setting up, and managing the necessary software tools and IT infrastructure.
- Creating, implementing, and adhering to relevant certificate policies and procedures that outline and ensure appropriate creation, management, and usage. (This includes certificate templates.)
- Continually monitoring and managing the lifecycles of all your digital certificates and their respective cryptographic keys.
- Securely storing your cryptographic keys (typically via hardware security modules, or HSMs).
- Managing access in terms of who can request, authorize, issue, and manage digital certificates and access your certificate management platform.
- Having the skilled and knowledgeable personnel who can set up and manage your intermediate and root CAs.
- Working with registration authorities (RAs) and managing CRL and OCSP processes.
If this list doesn’t scare you, or you have the resources to handle these functions and want to run your own CA, then wunderbar. It sounds like private PKI is right up your alley.
Of course, you can have all the benefits of a private CA without doing all of this tedious stuff yourself by using managed PKI. A little later in this article, we’ll share some private PKI management best practices that you’ll find helpful.
Why PKI Lifecycle Management of Certificates and Keys Matters
Why is all of this necessary? Suppose you don’t properly manage your keys and certificates or are not using the right tools for the right environments (think using private PKI certificates in public-facing environments). In that case, you’ll run into issues — everything from service outages that affect your customers to security and compliance issues that affect you in many areas.
Let’s consider what happens when you use expired, revoked, or misconfigured SSL/TLS certificates on public websites. Users’ web browsers will display ugly warning messages like these:
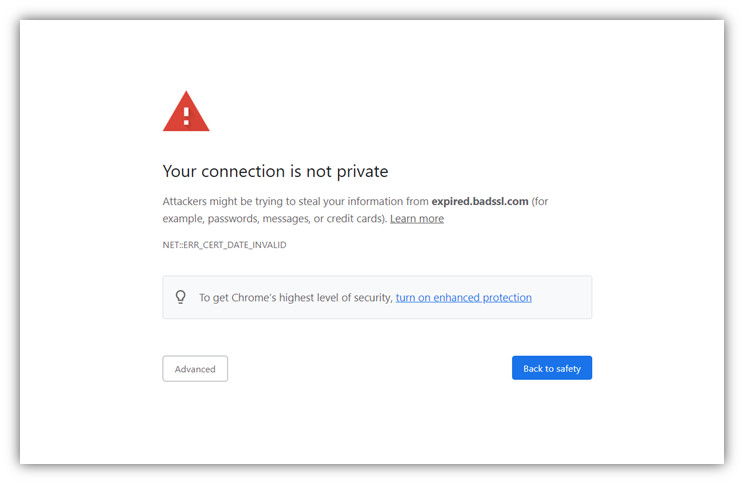
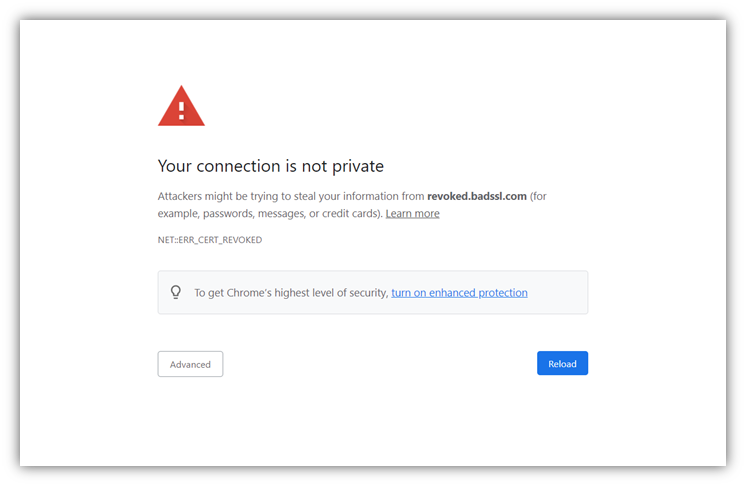
When it comes to managing your certificate and keys, you can’t just focus on one and neglect the other. Digital certificates and keys go together like chocolate and peanut butter. (If you’re not a fan of that combination, too bad — I’m rolling with it.) Or, to put it another way, the relationship between cryptographic keypairs and PKI certificates is like a line from Frank Sinatra’s 1956 classic Love and Marriage: “…. you can’t have one without the other.”
Basically, a digital certificate without a secure cryptographic key is useless, and a key doesn’t do you much good if you don’t have a valid certificate to use it.
But digital certificates, like everything good in life, don’t last forever. Each cert is issued with a finite lifespan and will expire after a set amount of time. (In some rare cases, certificates may get revoked before their expiration dates.) This is why you must stay on top of your certificates’ individual validity dates. Otherwise, using expired certificates leads to:
- Data and IT security issues (if your certificate expires, someone could take advantage of the situation)
- Service disruptions (clients and operating systems don’t recognize expired certificates),
- Non-compliance with data privacy and security requirements (which can lead to penalties and fines),
- Higher costs (due to incident response-related functions), and
- Reputational harm and lost business (why should someone trust you if you can’t be bothered to follow industry best practices?).
Likewise, the security of your cryptographic keys is also essential to your organization’s public key encryption capabilities. If you don’t securely manage your keys, they may wind up in the wrong hands. And if your keys get compromised, the digital certificates that rely on them will be as useful to your security as wearing just a swimsuit in Antarctica would be to your health. Translation: your data becomes easily compromised.
All of this brings us around to the main focus of this article — covering the PKI management best practices for your certificates and private keys.
5 PKI Certificate & Private Key Management Best Practices
NIST covers many PKI management best practices in their key management and TLS server certificate management resources (we’ll link you to all of those shortly). We’ll go over several key points that will give you a better understanding of how to manage your PKI certificates and private keys effectively.
1. Create Visibility: Keep Close Tabs on Your Certificates and Private Keys
Having clear visibility of all the certificates and keys on your network is a must for effective PKI lifecycle management. Part of this entails maintaining a current and accurate inventory of your cryptographic assets. Some of the information you should track includes:
- Who is responsible for managing certificates and private keys.
- Which certificates and keys are deployed and where.
- How each certificate or key is used (i.e., knowing its applications).
- Who owns (is authorized to use) each certificate and its corresponding private key.
- Who attempts to use those keys (log both successful and failed attempts).
- When each certificate was issued and is set to expire.
- Which CA issued or signed each certificate.
- Key sizes and algorithm types (so you can identify any weak or deprecated algorithms).
It’s important to note that public CA-issued SSL/TLS certificates only have one-year validity (a maximum of 397-398 days, to be more specific). That’s because in 2020, Google and Mozilla decided to that their browsers would no longer trust website certificates with longer lifespans. In August 2020, the CA/Browser Forum (CA/B Forum) updated their baseline requirement to indicate as much. However, this change doesn’t affect private certificates because private CAs aren’t subject to CA/B Forum rules or requirements.
2. Create Accountability: Decide & Document Who Will Handle Specific Responsibilities
Don’t wait until the last minute — or, worse, wait until something goes wrong — to define your PKI management responsibilities. Part of this process involves determining whether you want to handle everything internally or if you want to outsource some of those responsibilities to a vendor. And if you decide you want to handle at least some functions internally, then you’ll need to define who is responsible for what and clearly document that information.
Outlining these roles and responsibilities is a key component of establishing a strong certificate and key management program within your organization.
3. Have a Strategy: Clearly Define & Enforce Your PKI Management Policies
Remember how we mentioned earlier that PKI management is a policy-driven process? We didn’t mean that lightly. Defining and enforcing clear PKI management policies is critical to your IT and data security. It’s also another core component of developing a strong certificate and key management program or framework.
Your key management and certificate management policies should:
- Define who is responsible for which tasks (particularly relating to requesting, issuing or managing your certificates and keys).
- Clearly define identity management and access control-related authorization requirements and processes.
- Help you implement an organization-wide PKI management strategy.
- Delineate what processes should be followed for various functions (for example, certificate or key generation). This will help you avoid misconfiguration issues that can cause issues down the road.
- Specify any technical requirements, restrictions and obligations.
- Detail which third-party CAs can (or shouldn’t) be used for certificate requests.
- Specify which governing standards your organization should adhere to (such as NIST or FIPs for federal agencies). This will help you to avoid non-compliance issues and have more successful audits.
- Keep you compliant with data security and privacy regulations (such as PCI DSS, HIPAA, GDPR, CCPA, etc.).
- Account for any organization-specific requirements.
4. Secure Your Private Keys: Use Secure Storage Technologies & Processes
The security of your cryptographic certificates depends on how well you protect your keys. There are several ways to store your keys, and which method you choose depends on whether you want to store them securely yourself or rely on a third party to store them for you (this process is known as key escrow). These methods include:
- Key stores (OS and Browsers),
- Key vaults (tools like Active Directory or related third-party services),
- Cryptographic tokens (detachable drives),
- Hardware security modules (HSMs),
Many businesses opt to use hardware security modules (HSMs) to store their keys securely. (Heck, many key escrow providers use HSMs to store their customers’ keys, too!) Like security tokens, HSMs are typically physical pieces of hardware that you’ll want to store in a safe on-prem location. But unlike tokens, which are mainly built for end-user usage, HSMs are generally more secure and are built to support a wider range of applications and PKI management automation tools.
Regardless of which method(s) you choose, such as a key management service, the main takeaway here is to keep your keys secure. If even one key winds up in the wrong hands, it can spell disaster for your business and customers who rely on your services.
5. Simplify PKI Management: Use a Centralized Management, Monitoring & Reporting Tool
Sure, you always have the option of going the manual route when it comes to PKI management. But in addition to being an incredibly inefficient approach, it’s also a dangerous one. Manually managing keys and certificates for a small business is challenging; trying to do so at scale is damned near impossible.
What if someone neglects to add one or more certificates or keys to the spreadsheet? What if someone leaves your organization and doesn’t tell you that a bunch of certs they were managing are now about to expire? Employees are people, and we’re all prone to making mistakes sometimes. As such, it’s not uncommon for certificates and keys to become lost or forgotten.
Keyfactor’s State of Machine Identity Management 2021 report indicates that more than half of their survey respondents say their companies have no clue how many public or private PKI certs and keys they have. As you can imagine, these situations create vulnerabilities that cybercriminals can capitalize on to gain access to your organization’s IT and data storage systems.
This is where a PKI certificate management tool is a game-changer. Of course, the specific functionalities vary from one platform to the next, but a good certificate manager is a useful tool that:
- Simplifies managing your certificate and private key lifecycles through a single, integrative dashboard.
- Gives you total visibility of the assets on your network, which enables you to maintain a current inventory of your organization’s digital certificates and keys. (It’s virtually impossible to manage assets effectively when you don’t know they exist.)
- Enables you to assign and delegate responsibilities and achieve greater accountability amongst your employees.
- Improves your organization’s PKI management efficiency and reporting capabilities.
- Offers automation, which relieves you of monotonous, repetitive tasks so you can focus on bigger priorities.
Some examples of great certificate management platforms include:
- DigiCert CertCentral Enterprise,
- Sectigo Certificate Manager,
- Keyfactor Command,
- ManageEngine Key Manager Plus,
- Venafi Trust Protection Platform, and
- AppViewX Cert+.
For a more in-depth look at specific PKI management-related processes and recommendations, check out the following NIST publications:
- Securing Web Transactions: TLS Server Certificate Management (SP 1800-16),
- Recommendation for Key Management: Part 1 — General (SP 800-57 part 1, revision 5),
- Recommendation for Key Management: Part 2 — Best Practices for Key Management Organizations (SP 800-57 part 2, revision 1), and
- Recommendation for Key Management: Part 3 — Application-Specific Key Management Guidance (SP 800-57, revision).
Final Takeaways
Hopefully, you’ve found this overview of PKI management best practices helpful! The security and success of your organization depend on how well you manage your PKI environment. Be sure to keep an eye out in the weeks to come as we continue to explore more articles on PKI, secure key storage, certificate management, CAs, and other related topics.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown