Cryptographic Keys 101: What They Are & How They Secure Data
Compromised cryptographic keys have a devastating effect on any organization — just ask the major Android device manufacturers whose keys were used to distribute malware. Here’s what to know about cryptographic keys, how they work, and how to keep yours secure.
Encryption secures everything from the credit card transactions you use to buy items online to the health information you share with your doctor. It’s an intricate system that relies on cryptographic keys to help keep that information secure.
But what are cryptographic keys, and how do we use them? We’ll explore the roles of cryptographic keys in modern communications and what you can do to secure them.
Let’s hash it out.
What we’re hashing out…
- Compromised cryptographic keys have a devastating effect on any organization — just ask the major Android device manufacturers whose keys were used to distribute malware. Here’s what to know about cryptographic keys, how they work, and how to keep yours secure.
- What Is a Cryptographic Key? A 90-Second Overview of Cryptographic Keys
- Cryptographic Keys Are Lumped Into Two General Categories: Symmetric and Asymmetric
- Large Keys Are More Secure (But Less Scalable) Than Smaller Ones
- Encryption Is Only Secure If Your Keys Are Secure
- A Look at What Cryptographic Keys Do
- 5 Examples of Cryptographic Key Applications Within an Organization
- Let’s Wrap Things Up With a Few Final Takeaways
What Is a Cryptographic Key? A 90-Second Overview of Cryptographic Keys
A cryptographic key is a string of characters (often random or mathematically generated) that’s paired with a cryptographic algorithm to secure data. Algorithms are mathematical formulas that carry out multiple important cryptographic functions. Two of the most common functions involving cryptographic keys are data encryption and decryption:
- Encryption uses a cryptographic key to scramble plaintext (readable) data into unreadable gibberish (called ciphertext). This protects the data’s confidentiality from prying eyes.
- Decryption enables a person with the correct cryptographic key to recalculate the original data from the gibberish ciphertext. This way, they — and only they — can read the message.
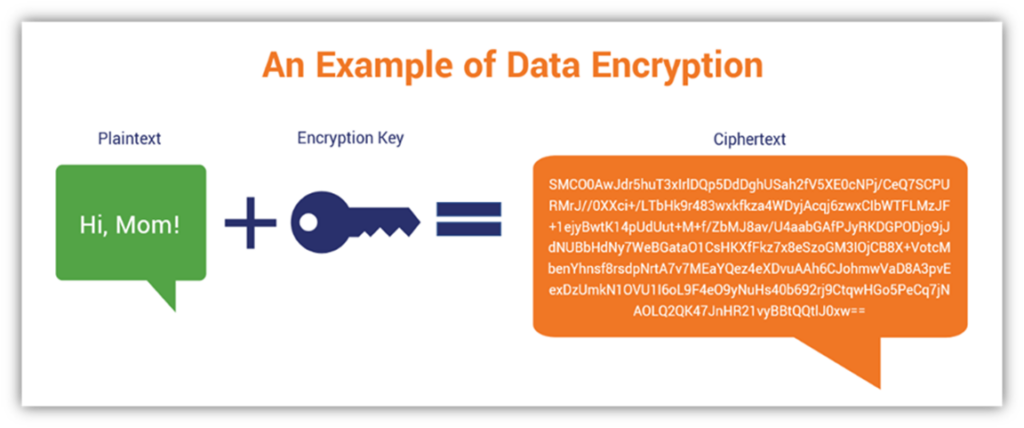
When a secret cryptographic key gets exposed or compromised, it means that whatever it’s used to secure is now at risk of compromise.
Throughout nearly the last nearly 4,000 years of human history, there’ve been many instances of using cryptographic keys to communicate secret information. This includes everything from ancient Egyptian tomb inscriptions to activities associated with the United Kingdom’s Government Communications Headquarters (GCHQ) after World War I. One of the best-known (and simplest) examples of cryptographic key applications is the Caesar Shift Cipher. This basic substitution cipher “shifts” the alphabet by a set number of spaces (e.g., A becomes D, and N becomes P). In this case, the “key” would be knowing how many spaces to shift to decrypt the message.
A common example of encryption can be seen when you log in to your favorite website. If you see the secure padlock icon (pictured below), it means that you’re accessing a site that’s secured with public key cryptography using SSL/TLS. (We’ll speak more about that later in the article.)
NOTE: This trusted little padlock icon will be going away in Google Chrome, starting with Chrome 117 that’s estimated to launch in September 2023, according to a recent update by the Google Chrome Security Team. Instead, the browser will display a “tune” icon that users can click on for information.
Cryptographic Keys Are Lumped Into Two General Categories: Symmetric and Asymmetric
Different methods of cryptography involve the use of one or two cryptographic keys. Let’s explore them both before we dive into their uses.
Symmetric Keys = A Single Private Key That Decrypts and Decrypts Data
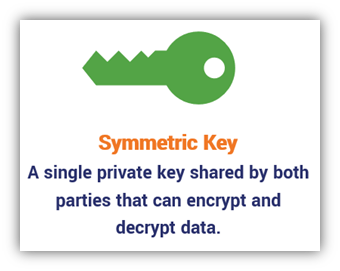
Symmetric encryption uses a single key, known as a symmetric key. Both the sender and the recipient need to have a copy of the key to encrypt and decrypt data. As such, this private key has to be kept secret so that no unintended third parties could use it to decrypt their secret messages. When you encrypt and decrypt data using a single key, it’s known as symmetric encryption, symmetric cryptography, or private key cryptography.
Imagine you’ve just completed a home renovation, a project that included replacing all of your interior and exterior doors with door locks you bought at a local hardware store. As such, each door you install would have its own separate lock, requiring a separate key to open it. (This would be a bit closer to asymmetric encryption because each key would only fit its corresponding lock — but we’ll dive more into that in just a few moments.)
However, using a symmetric key is like re-keying all of your home’s door locks so that a single key can open them. This is great for convenience because you only need one key, but it also means you have to go to great lengths to keep that key safe. Otherwise, everything inside your home will be compromised if someone gets their hands on that key.
One of the tricky aspects of symmetric keys is that they require the two communicating parties to meet up in a secure way so they each have a copy of the key. (Think of those stereotypical clandestine spy meetups you see in movies or read in books.) This isn’t too bad if you’re in the same geographic area as the other party. But what if you need to share sensitive information now but don’t have the time to meet to exchange keys? Or, what happens when you’re trying to communicate securely with someone who’s located in another state, country, or side of the world? You’ll be plumb out of luck.

Within the last century, the rise of digital communications changed the landscape of communications. Now, you can be using a phone in the United States and communicate nearly instantaneously with someone regardless of their geographic location. You can enter your information in a web form and send it instantaneously across the internet to someone on the other side of the world.
However, there’s a drawback: If you’re sending that data in plaintext, it isn’t secure and can be intercepted by nosy or malicious third parties.
To avoid this security risk, you and the person you’re communicating with need a way to securely communicate using encryption. But this would require exchanging your symmetric key, right? Yes. And this is where public key cryptography comes into play…
Asymmetric Keys = Separate Keys to Encrypt & Decrypt Data (And Enable Authentication)
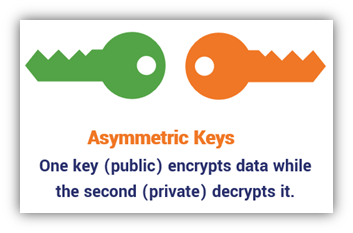
In modern cryptography, another type of cryptographic key is an asymmetric key—a pair of two different but related keys. A public key is publicly known and doesn’t have to be kept secret. It’s linked to a private key, which is kept secret.
Asymmetric cryptographic keys (asymmetric = not identical) are generated in mathematically related pairs containing one public key and one private key. In public key encryption:
- The public key, which is available to virtually everyone, is used to encrypt the data.
- The private key, which must be protected and kept secret, is used to decrypt the ciphertext.
A common analogy you’ll see online that’s used to describe the role of separate keys in asymmetric encryption is a mailbox where you have one key to deposit items (public key) and a separate key to remove them (private key).
Using these two cryptographic keys enables two parties to create a secure, encrypted connection. Think of when you connect to a website. The server and client use asymmetric keys to securely exchange information that’s used to establish symmetric session keys. These symmetric keys, which require fewer resources to compute, make data exchanges faster at scale.

To learn more about how public-private key pairs work in various cryptographic uses, check out our other article that looks at the topic more in depth.
But why bother switching to symmetric encryption at all? Can’t you just use asymmetric keys the whole time? Technically, yes, you could use asymmetric encryption alone to communicate securely on open channels. However, the resources required to make this happen for popular websites would be too costly to do when dealing with thousands or millions of connections. This is why we use asymmetric keys to exchange symmetric key-encrypted sessions to promote scalability.
Check out this recent comparative cost analysis of asymmetric and symmetric applications by researchers at the Institute of Electrical and Electronic Engineers (IEEE). Spoiler alert: Their research shows a “58% saving in global energy costs of public key-based applications” through symmetric key system adoptions.
A Quick Comparison of Symmetric and Asymmetric Keys
| Symmetric Keys | Asymmetric Keys | |
| What It Is | A single secret that must be protected and not shared. | Two keys — one that’s shared publicly (public key) and one that’s kept secret (private key). |
| What It Does | Encrypts and decrypts data for storage and/or in secure channels. | Used for encryption, description, and authentication, usually over insecure channels like the internet. |
| Key Sizes (Using AES and RSA Keys as Examples) | AES key sizes are smaller in size (256 bits is the most common size). These keys are calculated in various ways with varying levels of entropy, such as by using a random number generator (RNG). | RSA key sizes are larger keys (1024 bits, 2048 bits, 3072 bits, 7680 bits, 15360 bits, etc.) that are calculated using massive prime numbers. |
| Uses and Applications | Encrypt at-rest data on servers and internal digital storage applications. | Encrypt in-transit data in open (insecure) channels. |
| Processing Speeds | Faster to process than asymmetric encryption keys because symmetric keys are smaller. | Slower than symmetric encryption keys because they are larger. |
| Where You’ll Find It | Stored on authorized devices and internal (non-public) servers | Asymmetric public keys are integrated with digital certificates or sent with digitally signed and encrypted emails, documents, and software. The private keys are stored securely. |
Cryptographic Keys Also Can Be Identified By Their Uses and Applications
Sometimes, cryptographic keys are referred to with regard to the roles they play in cryptographic processes. We won’t get into all of them because they vary depending on the type of cryptographic processes you’re performing, but here’s a quick overview of several examples:
- Session keys — These keys are used to encrypt data during individual sessions (e.g., connections to a website or web app).
- HMAC keys — These keys are used to create the digital signatures used in hash-based message authentication codes.
- Data encryption keys (DEKs) — These keys enable you to encrypt data at rest on your server. DEKs also can be master keys.
- Key encryption keys (KEKs) — These keys, also called key wrapping keys, are used to encrypt other cryptographic keys that perform at-rest and in-transit data encryption. This means they can be symmetric or asymmetric, depending on the task.
- Traffic encryption keys (TEKs) — These cryptographic keys are used to encrypt data in transit against man-in-the-middle attacks and other interception methods.
- Master keys— The meaning of a “master key” differs depending on its usage. It’s also called a key-derivation key because it’s used in part to calculate other keys using key-derivation methods.
Large Keys Are More Secure (But Less Scalable) Than Smaller Ones
Generally speaking, the bigger the key, the more secure it is. For example, a 256-bit AES symmetric key is stronger than a 128-bit symmetric key, and a 3078-bit RSA asymmetric key is more secure than a 2048-bit asymmetric key. Larger keys help thwart brute force attackers who try to guess your key because it would be virtually impossible to guess all possible combinations using modern computer resources.
Let’s quickly compare public and private keys. We’ve used the RSA key generator tool from devglan.com to generate a 2048-bit RSA key pair for this example.
Public key:
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAnfyxkfwlj+QmitT4lVxrQLHAuJLRl2oIvy+J3I1cuWbyJWXfcmwzc99HRPL6qvfT3IdkJphxok1KZZf6r38v5HpUacSbLyHfi3s0JjclM09HvzuqWqHe1BJhP14RTIaa2ZVcZZvnFOm91U7VSR3lVFVOBFcfJYGTlvIVtXo57KYKYdwsZmiMlNZ3Zr8BX9gqY/Vl7sgjm9tJhBlpDFHCA0/v1jFlsYgddbOXl8ar7Dhp6VyOFG7ifahjmb7rUjzBvIVm7BG7Ds3IFkNvJAXVzfqqW/Zvru73X0AYOGwE5KWbjYN04JwErNI+2JDpk8d6gJrxb/MT6xXjEBuwc/s1mQIDAQAB
Private key:
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCd/LGR/CWP5CaK1PiVXGtAscC4ktGXagi/L4ncjVy5ZvIlZd9ybDNz30dE8vqq99Pch2QmmHGiTUpll/qvfy/kelRpxJsvId+LezQmNyUzT0e/O6paod7UEmE/XhFMhprZlVxlm+cU6b3VTtVJHeVUVU4EVx8lgZOW8hW1ejnspgph3CxmaIyU1ndmvwFf2Cpj9WXuyCOb20mEGWkMUcIDT+/WMWWxiB11s5eXxqvsOGnpXI4UbuJ9qGOZvutSPMG8hWbsEbsOzcgWQ28kBdXN+qpb9m+u7vdfQBg4bATkpZuNg3TgnASs0j7YkOmTx3qAmvFv8xPrFeMQG7Bz+zWZAgMBAAECggEADz17G6wJK5JErYvR1watSfZbsvJmyYZvBZJeaCoy0ae+oCDtpyoM5JabV2lhCPETPOjKnnaCL7fo/1fj1N4eDppGXlWa6rcHy3q9ExqqugJh1264BjorNqX3P5ehb5JkiazA1wRtDDVoHJWYOY9qufHorr6AwKt5Q0xjD7iUseFDN1jsnAQcbl1kifTcc9lbkSv9+zyBmzVQCSVifITe39YmBBCtGJWbC2+aCs2shcO7XOZrDjYABqlYRP7O1XXo0dJYnvat9EnLMTRwQZZwCXhavn+Iyrt2Odd3Vil3w5jSdIOiXivq2C9suZ5c8HIiAepm1Fvu7evo2OfUxTu9CQKBgQDtGN0wn5LUrcI0AO/FNNUobG+wYr7u4QnuucbwP+j9aF7Eo6LrPdgZw4o4DwMTP/rOC/2lNy4RyhQ6Y8CZ7ehxmZLTkCPeGaKRyzm6Z2fq0x3fielqIH9L3SeIgDnTwTxjJ9/Jq5UOvFsj5a1u6+6W9Z0iqDDVGAb+aWa+ic85iwKBgQCqlTL6mtRni1P2pfm8la3p+SjurJKwFaXlLbd6QphptYud8ox81JnCDeTMXUkXHcYwNRarxkqGKqe43j2oHj7XEmEGJUqOXG/9uUa2CBGVIy2b0EIEFnvw8Tj9T13EFi+3p48ksg9C33Jzv9Kcebjhb3B0h6rJuRu9LXEXSaKJ6wKBgQCkCVXPNDgECQuZqyQ4TmtDgnJrmIX9A5k5nzKyOaVa3YDjj0tCchE3EgBo9InuIY/GSql8SwcGq8b+9tDkLqNpJRVeZhVKrnW5ZN9VxgExiErcw6/ICx/HPwUA/aYEiWbcO1QrVRjVjx+HYHpziawSqW/D8JWIeQ0tq4K4ROQoLQKBgE8DFL3ngYMEkjuo3WhwnEHH2yHSZY+SN2lUJ6xFtHsiUC0078XSY/XyoYvXmcdPT0F9FaczDcnfcBi9OCnq+Ih+Rtql40bVojoP26TtT9eYl8OYTzu9fmM4GIGchX4SGMAkqLUClPcQsN7UdyVrbCtfhuMzA/Sz/Rk/NybmQJdJAoGAOR1qIyDpjal8YE/SeK+pI5ZAosADIW3zSPNrGxSbX8kqtdqTDODtP0JgXWfBuB7B2OM6SiV4AID0y/XRGmmyCD3tom7P/s3HnwUt5LxUhVgQ0Ufcw4IkfScNHVTfXBgu1aVN7eLPQMmfM+Inh7z4Gdcbf/xW2KyOdBFcI7Y8ZKE=
Big difference.
If you compare a symmetric key with an asymmetric key, then you might be surprised to learn that key sizes aren’t equal in terms of their security strength. For example, a 256-bit AES symmetric key is more secure than a 3072-bit RSA asymmetric key. In its “Recommendation for Key Management: Part 1,” the National Institute of Standards and Technology (NIST) lists an AES 256-bit key as being roughly equivalent to a 15360-bit RSA key. Furthermore, since asymmetric encryption requires the use of two keys, it’s slower than symmetric encryption, which only requires one.
Encryption Is Only Secure If Your Keys Are Secure
The security offered by your cryptographic secrets depends on how well you manage and secure them. A lost or stolen key doesn’t do you any good because it’s at risk of compromise. Once a key is compromised, the security of anything it’s been used to secure is at risk. That’s bad news for you and great news for cybercriminals.
You can protect your cryptographic keys using a key management system and by following key management best practices. We’ll speak a little more about that later. But first, let’s look at what cryptographic keys do; then, we’ll explore a few of the most common ways they may be used within your organization.
A Look at What Cryptographic Keys Do
Cryptographic keys are critical elements of public key infrastructure and play important roles in several crucial cryptographic functions:
- Encryption and decryption — We’ve already talked about this, but to recap, encryption is a method of scrambling plaintext data into ciphertext. Depending on the type of encryption used (asymmetric vs symmetric encryption), a cryptographic key is used to encrypt, decrypt, or encrypt and decrypt data.
- Authentication — This verifies that an entity (i.e., a person, client, or device) is who they say they are using public key cryptography. Basically, it’s a way to ensure that someone is authentic and isn’t an imposter because only the authorized user should have access to the private key. (This differs from symmetric keys, which both parties share.)
- Digital Signatures — A digital signature is a value that proves something (e.g., software, code, documents, or emails) hasn’t been modified or tampered with since it was digitally signed. A cryptographic function (hashing) and a cryptographic key are applied to the data to generate the signature. As such, it also helps provide non-repudiation, meaning that someone who sends something to you later can’t deny sending it. It’s akin to signing a document with a notary present: you can’t later refute signing it because they witnessed you doing so.
5 Examples of Cryptographic Key Applications Within an Organization
Not sure if you’re currently using any cryptographic keys within your IT environment? Here are several examples of how your organization or others are likely already using them:
1. Protect In-Transit Data Against Interception Attacks
By enabling HTTPS on your website, you’re securing your data in transit by using transport layer security. You can do this by installing an SSL/TLS certificate on your web server. Using an SSL/TLS certificate on your website ensures that your site users’ data will transmit via secure, encrypted connections.
These connections protect the data in transit. This stops man-in-the-middle attackers who want to intercept, read, modify, or steal your customers’ sensitive data as it transmits between their clients and your server.

For added security, enable the support of TLS 1.2 as a minimum on your server. Furthermore, you can use HTTP strict transport security (HSTS) as another layer of security to prevent downgrade attacks (i.e., prevent cybercriminals from forcing a website to downgrade from HTTPS to HTTP).
2. Secure At-Rest Data on Your Hard Drives and Servers
Encryption isn’t just for securing data in transit (i.e., public key encryption uses). Rather, encryption is also commonly used to secure at-rest data as well. This includes virtually any type of data stored digitally on a computer system. For example, this includes computers, database servers, cloud storage, and messages on your email server.
To encrypt data at rest, you’ll often use a symmetric cryptographic key because it’s fast and requires fewer resources than a pair of asymmetric keys.
But data encryption and decryption aren’t the only tricks up a cryptographic key’s sleeve (so to speak). These digital secrets also have other uses…
3. Authenticate Clients, Users, and Devices on Secure and Open Networks
Digital identity authentication in digital communications is crucial to data security. It’s what validates that you’re really you because a trusted authority has vetted your digital identity.
But what if you want to verify whether a user who is trying to access your protected resources is legitimate? Traditionally, this would involve the user entering their username and password. However, login credentials are easily compromised through phishing scams and malware, it means that it’s no longer a viable way to know that someone is authentic.
An alternative is to use digital certificates to verify your digital identity via public key cryptography:
- A client authentication certificate verifies your identity when accessing a secure web app, virtual private network (VPN), or other protected resources. This can be a certificate you install on your computer or mobile device.
- A device certificate (also known as a PKI device certificate) enables a covered autonomous device to authenticate to your network and transmit data securely. For example, this type of certificate is often used to authenticate IoT devices in healthcare facilities, airports, and manufacturing plants.
In each of these cases, the cryptographic key associated with the certificate proves your digital identity because only you should have access to it. As such, once authenticated, you can access resources you’re authorized to see and use.
4. Exchange Digitally Signed and/or Encrypted Emails
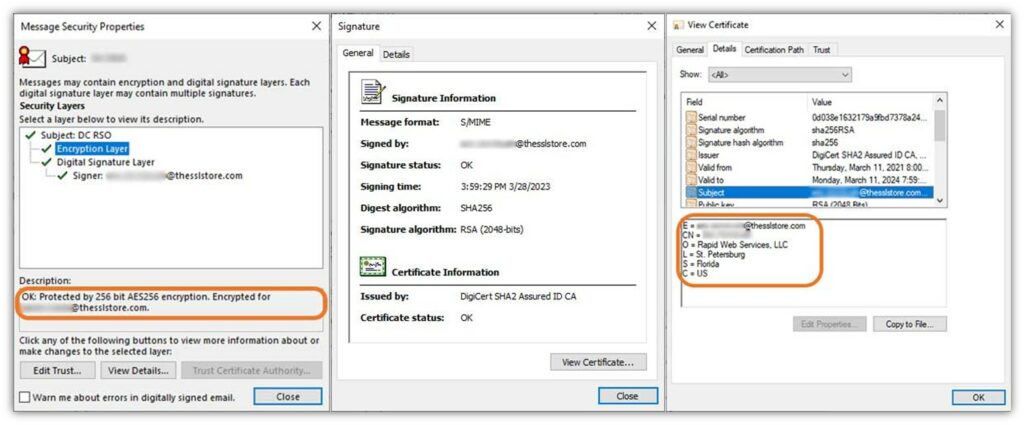
Email security is another important area where organizations rely on cryptographic keys. When you digitally sign an email, you apply a hash function to the email contents and your private key to the resulting hash value.
When an email is digitally signed, the recipient knows:
- the email is authentic because it came from you (i.e., your public key decrypts the hash value)
- the hash value the recipient’s email client calculates matches the one you sent.
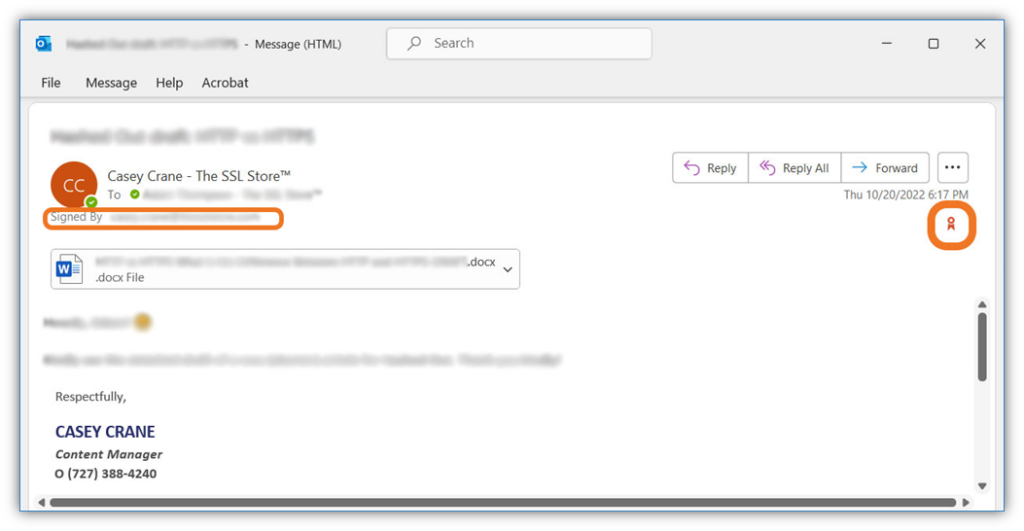
Now, let’s say you want to add another layer of security when sending sensitive or confidential data. You can do this using email encryption. Both the email signing and encryption processes involve the use of S/MIME certificates (i.e., email signing certificates). So, as long as you and your email recipient use email signing certificates and you’ve exchanged public keys, then y’all can exchange secure, encrypted emails. This is particularly important for compliance when sending protected customer, financial, or patient health-related data.
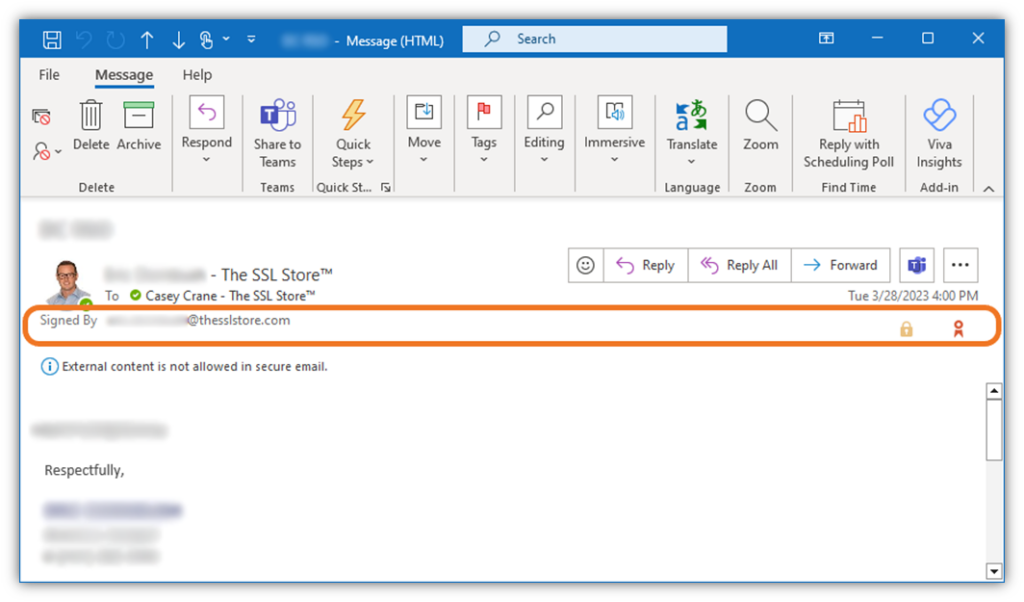
5. Digitally Sign Code, Software, and Updates Before Release
Digitally signing your software enables you to show customers and software users that your product is not only authentic but hasn’t been tampered with since it was signed. This is important for software developers, publishers, and service providers that maintain customers’ systems.
You can use a code signing certificate to attach a digital signature to your code. This involves applying a cryptographic hash function to your code and using your private cryptographic key to digitally sign the resulting hash value. When someone downloads your software, their browser or operating system will check to see if the hash value matches. When it does, it’ll display your verified organization information.
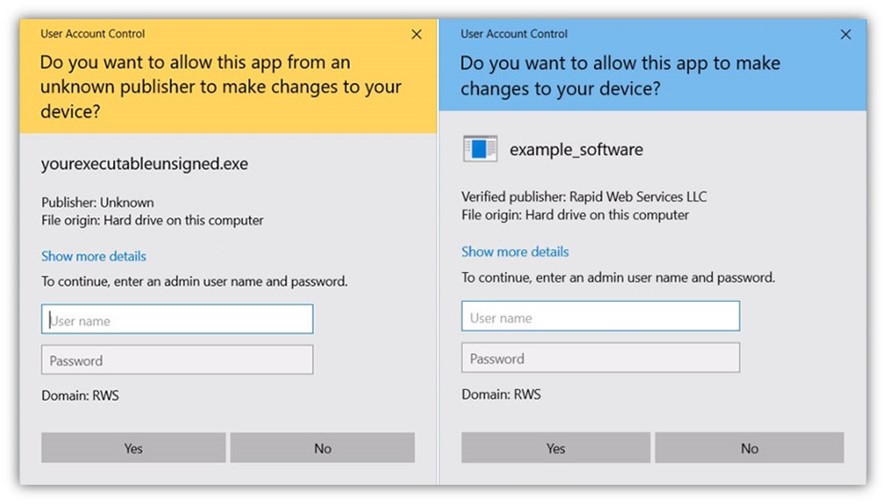
If you decide to take your identity a step further, you can use an extended validation code signing certificate. Signing your software with that digital certificate ensures your software is automatically trusted by Windows operating systems and the Edge browser. As a result, it won’t display Windows Defender SmartScreen warnings like this:
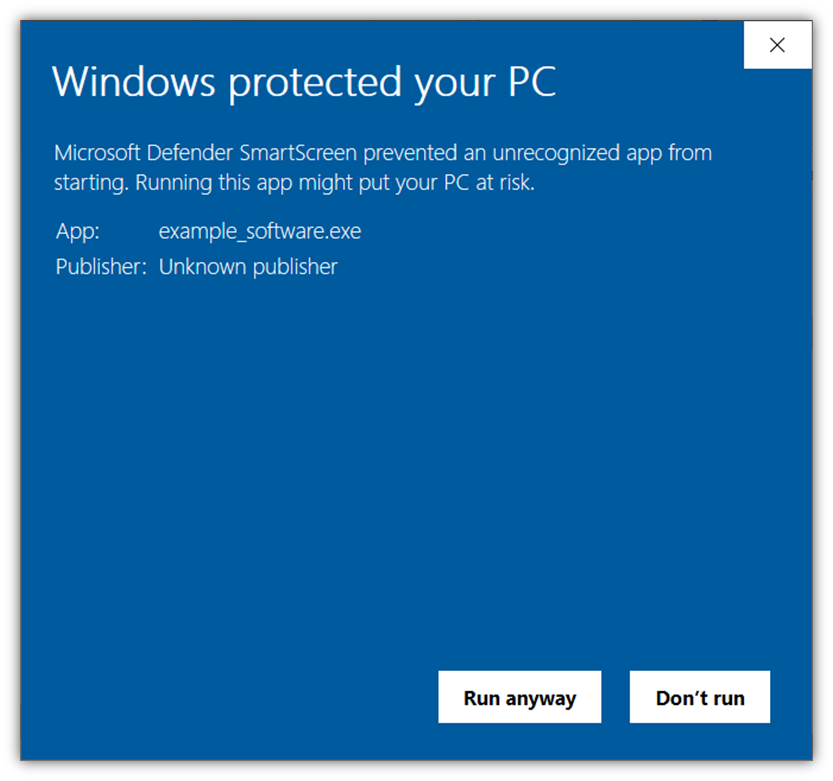
Let’s Wrap Things Up With a Few Final Takeaways
Hopefully, we’ve driven home the point that cryptographic keys are crucial to the security of digital assets and data. But much like other precious things in life, they must be protected through all means possible.
Want Your Keys to Work? Store Them Securely
Storing your cryptographic keys securely isn’t optional; it’s actually a requirement of many industry and regional regulations. And unless you like the idea of forking over thousands or millions of dollars in noncompliance penalties, legal fees, and lawsuit settlements due to data breaches, then we suggest you pay attention.
Historically, only extended validation (EV) code signing certificates came pre-installed on a hardware security token. Now, all organization validation (OV) code signing certificates will also be delivered via secure tokens by default.
You also can use hardware security modules (HSMs) to protect your other cryptographic secrets. These on-prem appliances and cloud-based storage mechanisms provide a way for your authorized users to use your cryptographic keys without having direct access.
Familiarize Yourself With Key Management Best Practices
We’re not going to dive into the specifics of key management best practices here because we’ve already done that in previous articles. To learn more, check out our key and certificate management, check out the following resources:
- 12 Enterprise Encryption Key Management Best Practices
- 14 SSH Key Management Best Practices You Need to Know
- PKI Management: Private Key & Certificate Lifecycle Management Best Practices






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown