What Is a Key Management Service? Key Management Services Explained
A lost or stolen cryptographic key can devastate a company — that’s why many companies choose to use key management services to protect and secure their organization’s sensitive assets
When you’re out and about, there’s virtually no worse feeling than reaching into your pocket or purse and discovering that your keys are missing. The realization hits you like a ton of bricks, and you’re left asking two important questions: where did you leave them? And what happens if someone untrustworthy finds your keys before you do?
Your keys are your literal method of access to important places in your life — your home, office, and your car. Keys keep bad guys out yet enable you access to everything you hold dear. Needless to say, you don’t want them winding up in the wrong hands! The same can be said about your organization’s cryptographic keys. These sensitive keys do everything from secure your website and email communications to authenticate users and devices on your network. Therefore, you need to keep them safe from compromise and do everything you can to mitigate risks.
Keyfactor and the Ponemon Institute research shows that organizations report having an average of 88,750 digital keys and certificates within their IT environments. And to make matters worse, 74% of respondents indicate they don’t actually know how many keys actually exist or where to find them! As you can imagine, this level of oversight can cause irreparable harm if you’re one of these businesses. Having a key management service in place can be a lifesaver (or, more accurately, a job saver).
This article will explore what a key management service is and why it’s a crucial investment for your organization.
Let’s hash it out.
What Is a Key Management Service? A KMS Definition
A key management service (KMS) is a system for securely storing, managing, and backing up cryptographic keys. Of course, the specific types of keys that each KMS supports vary from one platform to another. Most key management services typically allow you to manage one or more of the following secrets:
- SSL certificate private keys
- SSH key pairs
- API keys
- Code signing private keys
- Document signing private keys
- Database encryption keys
Key management services are designed to help you avoid a key being lost or stolen (which could result in a data breach, downtime, or data loss). Features vary a bit between different solutions, but most key management services include at least these capabilities:
- Web-based interface for managing your cryptographic keys.
- Secure storage and backup of private keys (typically on a hardware security module, or HSM — we’ll speak more to that in a bit).
- APIs and/or plugins to integrate the KMS with your servers, software, and systems.
KMS vs KMS vs KMasS
Key management services, key management systems and key management-as-a-service (KMaaS) are three terms that often refer to the same thing. While there are some technical differences, these terms are often used interchangeably to refer to systems (usually cloud based) for managing cryptographic keys.
(Remember how we’ve mentioned before in our articles that companies use the terms SSL and TLS interchangeably even though they’re technically different? Yeah, that same line of thinking applies here.)
What Does a Key Management Service Do?
A KMS is a form of secrets management that helps you manage keys and their meta data. It can deploy on-prem or in the cloud (depending on your chosen platform and vendor). The goal of using one of these systems is to help you keep all of your cryptographic keys as secure as possible. It does this in several ways (depending on which KMS you use):
- Creating secure keys that protect your data. A great KMS enables you to generate keys that have sufficient entropy (randomness). Every key is a string of hexadecimal characters — the more random the order, the harder it is to crack.
- Giving you visibility to view and monitor keys. A KMS is a tool that enables you to discover any key within your environment — even those not created in the KMS. If you know what keys you have and where they’re deployed, then you’ll be able to properly manage them. (No more rogue keys!)
- Allowing you to set permissions. Effective key management entails knowing who has access to which keys and why they’re using them.
- Helping you securely store your keys. Secure key storage is a critical component of virtually every KMS, which is why many of these systems use hardware security modules (HSMs) — more on that shortly. If you don’t store your keys securely, they could become lost or stolen, which can result in data compromise.
- Enabling you to use keys without needing direct access to them. Some key management services enable you to use your keys to digitally sign data without requiring access to the plaintext keys.
- Providing you with a way to back up and archive keys. Rather than trying to handle key backups and escrows one a one-by-one basis, you can automate the process.
- Allowing you to automatically rotate SSH keys. Some key management systems offer automation. This means you can automatically rotate your SSH keys for increased security on web servers.
- Enabling you to import existing keys. Some key management services enable you to bring your own keys (BYOK) by importing them from your computers, servers, devices, and/or on-prem HSM to their cloud environment.
The National Institute of Standards and Technology says that while keys can be managed manually, some circumstances may require the use of an automated system (i.e., key management system).
Protecting Your Keys Is Essential to PKI Security
Practicing good key management is integral to the security and usefulness of your organization’s public key infrastructure. PKI is, basically, the backbone of online security. PKI relies on cryptographic tools known as digital certificates and keys, which allow you to do everything from verifying your identity during logins to protecting your customers’ data in transit as it leaves their browser and transmits to your web server.
As such, cryptographic keys exist throughout your network and larger IT environment. They often operate in the background, unseen by your customers by offering them security all the same. These tools help you facilitate secure authentication and data encryption.
Of course, we’re not going to go into all of the technical details of PKI here as the topic is a bit of a rabbit hole and will take us off-track from the topic at hand. So, be sure to check out these two articles to learn more about what PKI is and how PKI works.
Effective Key Management Matters More Than Encryption
Wait, what? We’re a company that lives and breathes everything encryption — why are we saying that something’s more important? Well, if you don’t properly manage your keys, then using those keys to encrypt your data won’t do you any good.
Encrypting data with compromised keys is a pointless endeavor — bad guys can just use the compromised asset to decrypt your data. Using a compromised key for encryption is the equivalent of using a lightweight puzzle box to secure your most valuable possession. Sure, someone might try to go to the trouble of trying to crack the code to open the box. But the savvy criminal will simply break the box to gain access to its contents more quickly.
What’s the Difference Between a KMS and an HSM?
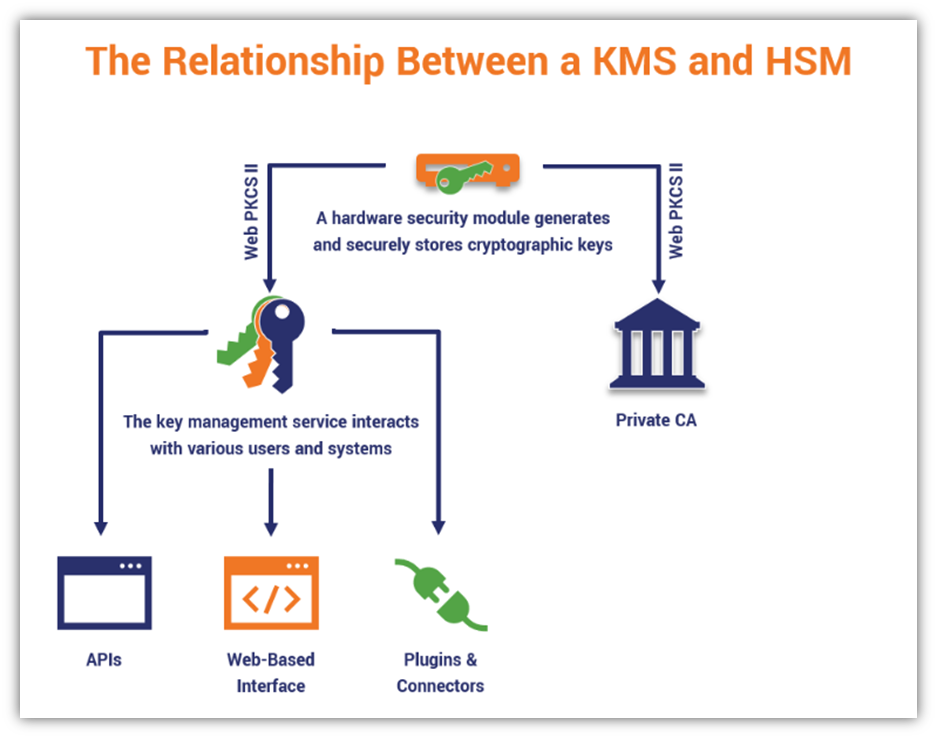
People often confuse HSMs with key management services. And while they’re related, they’re still separate in terms of their individual functionalities. Here’s a quick summary of the differences between a KMS and an HSM:
Hardware Security Modules
A hardware security module is typically a physical piece of hardware that handles key storage and cryptographic functions at scale. (There are some cloud HSMs available as well but the term HSM typically refers to the physical devices.) An HSM is a secure environment that allows you to handle key lifecycle management operations and offload many cryptographic operations as well. (This way, you’re not overburdening your servers and other systems.)
HSMs can be stored as online or offline devices (depending on how you choose to use them). For example, public certificate authorities use offline HSMs to store their root CAs to keep them as secure as possible. But some companies use online HSMs to store their private PKI’s intermediate CA keys.
HSM devices typically are offered with one of several Federal Information Processing Standards (FIPS) certified ratings from level 1 to level 4 (with 4 being the highest). The HSMs that many key management systems rely on are typically rated at FIPS 140-2 level 2 or better.
Key Management Systems
A key management system is typically a cloud-based tool for securing, generating and managing keys. This system enables users to handle everything relating to managing key lifecycles. This is a good option for organizations that don’t require an on-prem HSM device or don’t want to deal with having to protect it within their environment.
However, it’s important to note that many key management services use HSMs on their backends to provide secure storage and backups. They also typically enable you to carry out limited cryptographic operations as well. For example, some key management systems will allow you to use the keys inside the KMS to perform data signing and other related functions.
6 Reasons Why Using a Key Management Service Can Benefit Your Business
Now we know both meanings of “KMS” and how HSMs play a role in key management, it’s time to explore several reasons why a key management service matters to your business.
1. Using a Key Management System Helps You Achieve and Maintain Compliance
Compliance is essential. Whether your business falls in the healthcare sector or you’re an ecommerce business that accepts online credit card payments, remaining compliant with regulations and laws is non-negotiable — you have to do it if you want to keep your doors open.
But compliance isn’t a one-and-done kind of thing; it requires ongoing efforts, audits, and other security processes to prove you’re doing what you’re supposed to do in terms of securing sensitive data. A crucial part of this is keeping your keys secure.
Let’s emphasize this point for the people who might be skimming this article: cryptographic keys are only useful if you keep them safe. This means preventing unauthorized users from accessing or using them. If someone gets their hands on your private keys (digitally speaking, of course), they can gain access to whatever those keys can touch.
Needless to say, regulators and customers won’t be happy for reasons we’ll discuss in section five. But in the meantime, let’s continue to explore how key management services help your organization and protect your customers’ data.
2. Implementing a KMS Keeps Your Data and Systems Secure
We’re pretty sure we don’t need to explain why it’s important to secure your data. If you’re like most organizations, the fact of the matter is that you have cryptographic keys in use across all of your IT environments, including:
- Virtual environments and testing servers,
- Email servers, file servers and databases,
- Website and web apps, and
- Private and public clouds.
As such, a key management service can help you secure your files and communications both while they’re in transit and at rest.
3. Relying on a Key Management System Helps You Prevent Unauthorized Access
Another benefit of effective key management is that it helps you ensure that only the right people have access to secure resources. KMS tools typically enable you to define permissions for how and where keys are used. If someone doesn’t have the right key, they can’t use an authentication certificate to verify their identity or decrypt encrypted information.
Properly managing your keys is integral to digital identity and secure device and user authentication — both of which help you keep data secure from prying eyes.
4. Ensuring You Always Have Access to Your Server & Data
Effective key management helps you avoid the hassle, frustration, and other issues that stem from losing cryptographic keys. Imagine the following scenario: You have a great developer working for your company. They create a server, which they use a single SSH key pair to access. But what happens when they leave the company a few weeks later and your access to that server disappears with them? Nothing good, we can tell you.
Depending on the specific situation, this could spell disaster for your business. Losing even a single SSH key to a server means that you might not be able to access the server again in the future. Simply put, there aren’t locksmiths for SSH keys. So, you need to ensure that you have key management processes, policies and technologies in place to prevent this type of situation from occurring.
5. Adopting a KMS as Part of Your Key Management Strategy Increases Efficiency
Implementing a key management service can help you streamline your organization’s key management tasks. Rather than having to dedicate part of your IT team to handle everything relating to key lifecycle management tasks — generating, deploying, using, managing, and destroying keys — you can free up these personnel assets to focus on other critical functions.
6. Implementing a Key Management Service Helps You Mitigate Costs
Manually managing your keys can be a nightmare. It costs loads of money in terms of time, IT resource investments, and employing knowledgeable and skilled personnel. This can run up a high tab in no time.
Furthermore, manually managing your keys is a poor key management practice because it can result in one or more keys falling by the wayside and increase your attack surface as a shadow IT asset. As you can imagine, this can result in a litany of direct and indirect costs:
- Non-compliance fines and penalties,
- Harm to your brand and reputation,
- Damaged customer relationships,
- Lost revenue and future sales opportunities,
- Costs associated with responding to and recovering from a data breach,
- Costs associated with informing customers about any security incidents your mitigation strategy,
- Other financial consequences such as lawsuits and settlements.
Final Takeaways on the Importance of Key Management Services
Alright, you’ve stuck with us this long. Now, it’s time to drive home the biggest point of all. Whether you’re looking to use a key management tool to manage your keys in-house or you opt to work with a key management service provider, the important thing is to ensure you’re properly managing your cryptographic key lifecycles.
Poor key management reflects negatively on your brand and results in far-reaching financial damages. As such, it’s important that you take the time now to assess your organization’s existing key management practices and tools to ensure you have your ducks in a row. Here are a few related resources that we think you’ll find beneficial:
- PKI Management: Private Key & Certificate Lifecycle Best Practices
- 14 SSH Key Management Best Practices You Need to Know
- 12 Enterprise Encryption Key Management Best Practices
- NIST Key Management resources page






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown