Creating Your Own Certificate Authority Server
We Take a Look at the Various Options You Have for Creating Your Own Certificate Authority Server and the Pros and Cons of Each
When it comes to securing your sites and/or devices with SSL/TLS certificates, you have two basic courses of action to choose from – either pay a certificate authority (CA), such as DigiCert or Sectigo, to sign and issue them, or you can go ahead with creating your own certificate authority server and generate the certificates yourself. What’s the best way to go? It all depends on your specific situation and needs.
If you want to proceed with creating your own certificate authority server, you’ll have to choose between the two primary ways of doing so – you can build your own completely from scratch or you can go with a managed PKI solution from a third-party vendor. So, what are their pros and cons of each? How will they impact your business? And what are the most common platforms to choose from?
Let’s hash it out.
Why Run Your Own Certificate Authority Server?
So, how do you know if creating your own private CA is the way to go? If your site is public facing – let’s say it’s an ecommerce site, for example – then you’ll most likely want to use a public CA for your certificate. These certificates are signed by an established root certificate whose keys are included with all the major web browsers and operating systems. That way, your site’s certificate will be automatically trusted out-of-the-box by your visitor’s machines, and they won’t be met with any warnings like the one below:
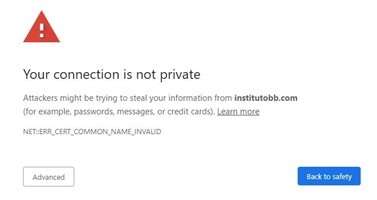
On the other hand, if you’re an organization that has its own internal systems and devices that are private to the rest of the outside world, then creating your own private CA can offer many advantages. You won’t have to purchase certificates for every single device and site – which can get quite pricey very quickly.
A private CA is also ideal for authentication on virtual private networks (VPN), internal wi-fi networks, and other services that use multi-factor authentication. Private certificates work great in those situations – you’ll issue and install them yourself and won’t have to worry about trust warnings because external users won’t be attempting to use the certificates. Only internal users that have already installed your trusted root certificate on their machine should be using them.
With your own private CA, you’ll have full control over things like:
- The server hardware
- Root & intermediate certificates
- Revocation mechanisms (CRL & OCSP)
- Policies
- Interface for issuing/managing certificates
- Integrations with systems
Creating your own certificate authority server also has security benefits for certain situations. Private certificates can be issued with a common name that is not an email address or public hostname/IP. So, for example, if you want to install a device certificate on an IoT device using public SSL, your only option would be to assign an email address to that device. That’s not very practical and adds an unnecessary degree of complexity to manage.
A private CA also gives you full control over issuance and revocation. You know that nobody can get a certificate from your CA unless you let them. If you secured your IoT network using public SSL instead, then people outside your organization could get certificates issued by the same CA and might be able to use them to join your network (depending on how you set it up). With private certificates, you’re the only one that can grant access (and you can revoke it at any time, as well).
Building Your Own Internal CA vs Managed Private CA
Setting up your own private CA from scratch gives you the highest level of customization and control, but there are also trade-offs you’ll have to consider. Theoretically, setting up your own private CA isn’t all that hard to do. However, doing it properly and comprehensively – dotting all the I’s and crossing all the t’s – takes a significant amount of time and expertise. It’s a resource-intensive project and the question of whether or not it’s the better choice than going with a managed third-party solution must be analyzed on an organization-specific basis.
The vast majority of companies aren’t inherently set up to build an effective, enterprise-wide PKI solution. Significant additional investment is usually needed in terms of staff and technical resources because organizations have other higher priority goals that they are focused on – developing new products, improving manufacturing capabilities, supporting their sales force, etc. When deciding which way to go, you’ll want to have a solid understanding of the pros and cons of each option so you can make an informed, intelligent decision that’s best for your organization.
Personnel
When considering the costs of building your own certificate authority server from scratch, personnel is often overlooked. First off, you’ll most likely need additional staff with PKI experience to build and manage the private CA. Not only that, but your existing engineering/IT team’s time is also required. They have other responsibilities pertaining to security and infrastructure, maintaining email servers, wireless systems, audits, penetration testing, and so on. Chances are they don’t have free time to create a private CA, and instead it will pull them off other high-priority work.
Scalability
Scalability is another challenge that faces those building their own private CA. Organizations tend to craft their CA based on present-day needs, then eventually find that what they came up with won’t be enough for their future needs. For instance, a company sets up their internal CA to issue certificates to devices so that they can be authenticated into their wi-fi network. Then, six months later they realize they need certificates for all their internal servers and want them automatically issued via an API. Suddenly, the scope of the project has expanded into creating an API, requiring even more resources than originally thought. Without in-house PKI expertise, it’s difficult to accurately predict what the finished product ultimately needs to be.
The challenge of scalability is an area where managed solutions usually have the edge. Predicting the future is never easy, but it’s even more difficult if PKI isn’t your organization’s expertise (and for most companies, it isn’t). It’s one of the reasons that a managed PKI solution can be the way to go, since commercial CAs have much better perspectives – their past experience helps them better prepare and scale for the next few years and beyond.
Cost
When it comes to figuring out the dollar cost of your internal CA, that number will depend greatly on the scope and your needs. We’d recommend breaking down the cost considerations by category and then analyzing each. Regardless of the specifics of your organization, you’ll need to budget for the following if you’re creating your CA from scratch:
- Hardware, software, and licenses
- PKI personnel
- Staff training
- Certificate policies and practices
- Audits
- Vulnerability testing
The biggest reason that companies tend to shy away from hosted solutions and decide to build their own CA is due to misconceptions regarding the costs of the hosted CA solution. For most organizations, their prior experience with commercial CA’s was related to buying SSL certificates for their websites. Therefore, the assumption is made that privately issued certificates will have a similar cost on a per-certificate basis as their publicly trusted SSL certificates. However, issuing a private certificate through a managed CA is almost always a fraction of the cost of the publicly trusted one issued by a commercial CA.
Overall, the managed CA solution has a lower total cost of ownership and drastically less up-front capital investment requirements. And if you’re going the DIY route, there’s more risk involved because anything that’s missing will be on you and you alone to take care of. Remember to think long term and have a thorough understanding of all the potential costs before taking the plunge.
Capabilities
Capability is another area where there are misconceptions about managed CA’s. Organizations think that they will have limited options and won’t be able to do the same things with a hosted CA that they can with a homegrown private CA. Take automated certificate issuance, for example. Most hosted CA platforms have APIs and other tools that allow for automated certificate management, meaning your company won’t need to develop them.
Basically, it comes down to how many development resources you have available. If you already have the talent and infrastructure available to say, build your own API, then going that route will give you the most robust and customizable tools possible.
If you don’t? With a managed CA, you’re getting a hosted solution that’s pre-configured to give you everything you need out of the box. The downside is that there’s less flexibility and customization versus doing it from scratch. That being said, the options available should be sufficient for the vast majority of customers.
Hosted solutions also allow your engineering and IT teams to remain focused on your company’s highest priority projects. They aren’t designing the private CA – that work has already been done by the vendor – and the resources required for administering the hosted CA are a fraction of what it takes to build it from scratch.
Flexibility
Finally, there is a belief that hosted CA solutions limits flexibility and confines users to specific certificate profiles. However, you won’t necessarily be limited to certificate profiles that are approved by the CA/B Forum. Many vendors are willing to create custom certificate profiles to meet your needs. DigiCert, for instance, can provide non-SSL certificate profiles that don’t even necessarily have to be X.509 type. If you have specialized requirements, it’s definitely worth reaching out to vendors to see what they have to offer – odds are you won’t be disappointed.
Managed CAs can also offer improved device support depending on the situation. As we’ll talk about shortly, Microsoft CA is the most popular platform for creating your own CA. While it offers some automation via Active Directory, you’re out of luck for any non-Windows servers or devices you may be using. Managed CAs usually include a PKI manager that that will work with all your devices. Therefore, a managed CA can potentially be the best option not only for new CA deployments, but for supplementing an existing Microsoft CA instance, as well.
Popular Platforms for Creating Your Own Certificate Authority Server
If you’ve decided that creating your own certificate authority server from scratch is the best option for your organization, then your next step will be to decide on the platform you want to use. Two of the most widely used tools are Microsoft CA and OpenSSL.
The most common platform for private CAs is Microsoft CA. It is part of the Windows Server OS. Note that it isn’t enabled by default but must be installed by selecting Certificate Services in the “additional Windows components” section of Add/Remove Programs. Microsoft CA integrates with Active Directory, so if you already have that set up in your organization, then that will make things easier when configuring Microsoft CA. Once you’re finished, you’ll then be able to issue certificates to your domain-connected devices via group policies. You can read about how to get started with Microsoft CA with this tutorial.
The downside of Microsoft CA is that deploying it is not a trivial task. While the basic setup steps are pretty straightforward, doing it right will take a significant amount of time. You’ll want to have a dedicated team that’s experienced in PKI to handle the implementation and then manage it afterwards. So, while technically Microsoft CA is free (as we mentioned, it’s included in Microsoft Server), don’t forget to consider the costs of the additional personnel and hardware.
OpenSSL has the benefit of being free and open source. It’s a cryptographic library that incudes command-line tools for generating and managing digital certificates, which you can configure to serve as a certificate authority. You can generate private keys, create CSRs, install certificates, and view certificate information. This tutorial can help you learn the basics of OpenSSL and get started with generating and installing your own private certificates.
Managed Solutions for Creating Your Own Certificate Server
Now let’s take a look at some of the most popular managed solutions for creating your own certificate server. Sectigo and DigiCert both have their own platforms for creating and managing your private CA.
DigiCert® Trust Lifecycle Manager
DigiCert’s option is called the DigiCert® Trust Lifecycle Manager, and is designed for scalability and streamlined management. There’s a number of deployment options, including:
- Public cloud
- Private cloud
- Hybrid
- Air-gapped
- In-country and on-premises
- DigiCert hosted
It allows for Active Directory integration and autoenrollment and is capable of quickly issuing large numbers of certificates across your enterprise. It also includes pre-configured certificate profiles for things like VPNs, wi-fi networks, REST API, Adobe, and Microsoft. You’re also able to manage all your certificate types from a single dashboard, including issuance, installation, and revocation.
Sectigo Private PKI
Secito Private PKI is similar to DigiCert®’s Trust Lifecycle Manager in that it’s a managed platform that gives you the power to issue private certificates of all types without having to deploy and manage your own separate server. Like other managed CA solutions, Sectigo Private PKI requires significantly less resources than building your own CA from scratch. It enables users to issue, install, renew, and revoke certificates via a proven and scalable infrastructure.
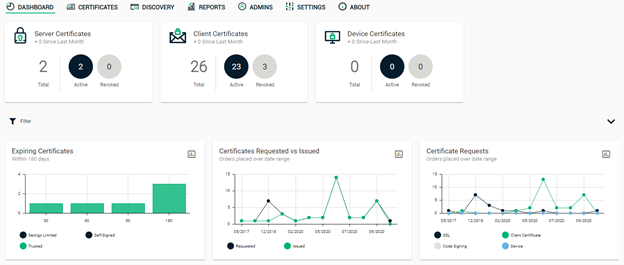
Sectigo Private PKI also works with any existing internal CAs you already have setup and running. For example, if you already have a Microsoft CA deployment, then Sectigo Private PKI can integrate and augment it. The two main benefits are that it lets you issue certificates to non-Microsoft devices and applications, and it provides a powerful management platform that is more robust and easier-to-use than the out-of-the-box Microsoft CA.
In addition to that, you’re getting:
- Backups with secure storage
- Comprehensive security policies
- A secure facility for your private CA’s hardware
- A central repository of keys
- A 2nd redundant system in case of an emergency
- Audits to verify compliance
All these tasks are critical to a successful private CA and would otherwise cost upwards of hundreds of thousands of dollars total to do on your own, not to mention the time and staff requirements that would also be needed.
Hosted or Internal?
As we’ve seen, there are benefits to both routes. If your organization has a clear idea of what it needs and has the budget and resources to accomplish it, then creating your own certificate authority server from scratch gives you the highest degree of customization and control. For most companies, however, PKI isn’t a primary focus nor a core competency. Because of the degree of expertise, time, and money required, hosted CA solutions are usually the best bet. And thanks to the evolved state of most of the private PKI platforms available, you won’t be making significant sacrifices in terms of features and capabilities once you get your managed private CA up and running.






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown