Your Security Certificate Has Expired: Here’s How to Fix It (3 Steps)
Elon Musk recently shared that an expired security certificate for a ground station caused a glitch that knocked SpaceX’s Starlink services offline. Here’s what to do when your organization is in a similar situation.
No one likes realizing that a security certificate expired but is still being used within your organization’s IT environment. Expired certificates result in service outages, unencrypted connections, and ugly “Insecure Connection” warning messages displaying. As you can imagine, all of these things can play havoc on your organization’s reputation and relationships with customers. (None of these things aid your efforts in creating digital trust.)
Unfortunately, with digital certificates having increasingly short lifespans, certificate expirations are bound to happen more frequently for companies that don’t adhere to the industry’s certificate lifecycle management best practices. Research from Keyfactor and the Ponemon Institute’s 2023 State of Machine Identity Management report shows that more than three-quarters (77%) of surveyed organizations experienced at least two “significant” outages stemming from certificate expirations in the previous 24 months. 55% indicate that the outages cause “severe disruptions to customer-facing services.”
We’ve previously written about what happens when your SSL certificate expires and why SSL certificates expire. But what do you do once you realize a security certificate has expired? And why do you need to mitigate the situation ASAP?
We’ll quickly walk you through how to renew a security certificate that expired and share how you can prevent this situation from happening again.
Let’s hash it out.
3 Steps to Take After Your Security Certificate Has Expired
Data from the Keyfactor/Ponemon Institute report shows that certificate outages can cause acute pain in very critical areas of your organization:
- 55% of survey respondents indicate that the outages caused “severe disruptions to customer-facing services.”
- 50% indicate that these security events caused “major disruption to internal users or a subset of customers.”
Of course, most companies (ours included) often preach about the importance of renewing your digital certificate before it expires. And it’s true — you absolutely should renew your certificates before the clock strikes 12, Cinderella. And every publicly trusted certificate’s issuing certificate authority (CA) also sends renewal reminders to give you warnings ahead of time. But we get it — stuff happens, and when you’re manually managing your public key infrastructure (PKI), things are bound to fall through the cracks when you rely on calendar reminders and have to set up individual alerts manually for everything.
But what do you do if, for some reason, the task of renewing a certificate has gotten pushed to the back burner too many times and the security certificate has officially expired?
1. Identify Where the Expired Certificate Is in Use Within Your IT Ecosystem
Before you can replace the offending certificate, you need to know where it’s located and all of the systems connected to it. This is where having full visibility of the certificates within your network and overarching IT environment really comes in handy.
PKI visibility entails knowing what certificates you have and when they’ll expire, who (or what) they’re assigned to, where they’re located, what they’re used for, and who is responsible for managing them. Yeah, that’s a whole lot of tracking. Thankfully, there are some tools and services that can help you out with PKI monitoring and certificate management.
Here’s a quick example of what customers see when you have an expired SSL/TLS certificate:
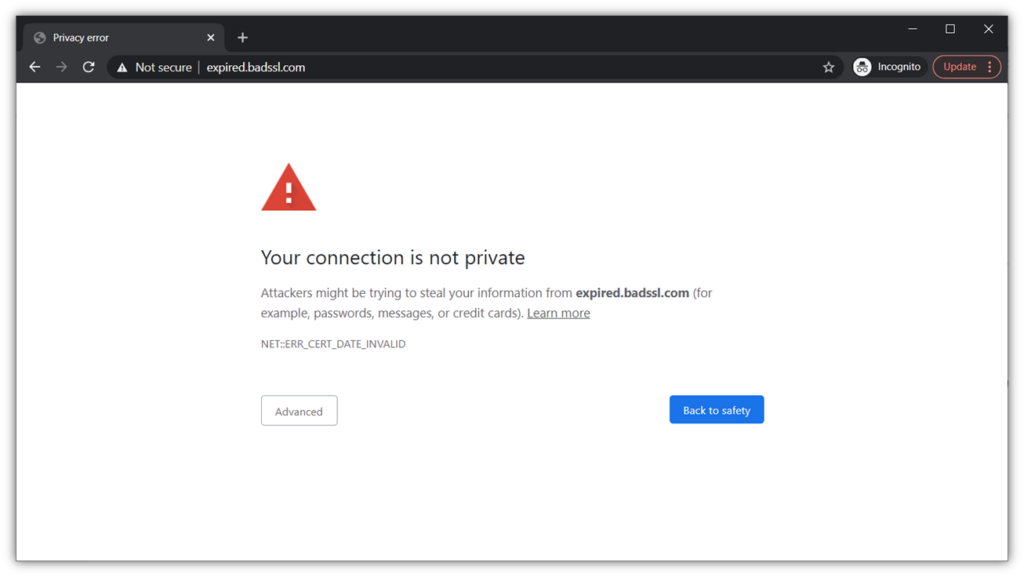
Let’s say, for the sake of this article, you know which certificate has expired and where to find it. Once you have this information, you can move on to the next step.
2. Renew the Expired Certificate ASAP
Using an expired SSL/TLS certificate is a lot like serving spoiled milk: it doesn’t do you any good to keep around, nobody likes it, and it can negatively impact their experience and perception of your organization (i.e., give you a bad reputation). DigiCert reports that four in five (84%) of consumers might abandon your business altogether and go with a competitor if they lose trust in your organization.
Simply said, expired certificates typically have a negative impact on your brand’s image and may even make customers decide against doing business with you again. It’s for these reasons (and more) that you must quickly divest yourself of this certificate and put a valid one in place right away.
Renewing an expired SSL/TLS certificate is like buying a new digital certificate. Depending on the certificate authority you use, you may (or may not) have to undergo the full validation process to get your certificate renewed.
DigiCert solves this problem with pre-validation and instant issuance. With DigiCert, domain and organization validation approvals are good for 12 months, so you can reuse them to issue as many certificates as you need without having to re-do validation steps every time. Basically, you can issue virtually unlimited digital certificates for your organization and domain throughout the active validation period.
Since life isn’t perfect and the trains don’t always run on schedule, DigiCert allows you to resubmit your organization validation at any time. So, you can refresh your organization validation ahead of any certificate expiry to avoid getting caught waiting for validation processes when time matters most.
If you find yourself in a pickle where your certificate has expired and you forgot to re-validate your organization ahead of time, reach out to the certificate provider to see whether your case can be expedited.
3. Install Your New Digital Certificate
You’ll have to take the lead on this part since we don’t know which type(s) of server(s) you’re running and systems you’re using. As a result, we’re not going to go into the nitty-gritty here because, frankly, the way you install your certificate often varies from one platform to the next.
Check out our resource page on installation instructions for SSL/TLS certificates on different platforms to help you with the process. You can also use an SSL/TLS Certificate Installation Service to do it for you if you want to spend your time on other critical tasks.
Why Dealing With an Expired Certificate ASAP Is Crucial
We’ve already touched on this throughout the article, but let’s quickly recap for those who didn’t stop to read everything. (TL;DR, anyone?) Simply put, an expired digital certificate is no joke. It can cause a litany of issues, including service outages and downtime, data security issues, and insecure connections, and cause harm to your brand and reputation with customers.
How to Avoid Repeating This Issue in the Future
Alright, your security certificate expired; it’s done and over with. Now, it’s time to take steps that will help prevent history from repeating itself. There are a couple of ways you can do this…
Implement Certificate Management Best Practices
Managing your certificate lifecycle is a critical aspect of public key infrastructure (and cyber security as a whole). If you don’t carefully manage your certificates and keys, then it’s only a matter of time before the proverbial crap hits the fan.
A comprehensive approach to certificate management isn’t something we can cover in this article. However, we do have several helpful resources that can provide guidance on what to do and things to avoid:
- Certificate Management Best Practices Checklist (eBook)
- PKI Management: Private Key and Certificate Lifecycle Management Best Practices (blog post)
- Let’s Talk About Some Common PKI Certificate Management Mistakes (blog post)
Use Automation to Manage Your Certificate Lifecycle
Automation can be a godsend when you’re managing hundreds or even thousands of digital certificates and keys with varying expiration dates. Trying to go at it alone with just manual spreadsheets to aid you is a nightmare for everyone involved.
Don’t do it to your customers or team — bring automation into the fold to help you manage your PKI assets at scale.
There are few ways you can use automation to manage your certificate lifecycle, depending on your organization’s size and which certificate management platform you choose. As with most every product in life, different companies offer different solutions. Some support ACME agents (more on that in a moment) while others support network “sensors” that rely on API calls.
Let’s explore a couple of ways you can manage your certificate lifecycles.
Use an Agent Provided By Your Certificate Management Platform
This provides end-to-end fully supported automation within your CLM platform. This entails installing a local agent on your servers or other systems.
Use Agentless Automation in Your Certificate Management Platform
Simplify your certificate deployment and related task management with agentless automation — no human interaction is necessary. Typically used for load balancers, firewalls, and similar use cases, your CLM platform will securely log in via SSH, API, or similar credentials to complete the installation automatically. This remote approach doesn’t require having an agent installed on every system.
Use a Certificate Management Protocol Such as ACME
The automated certificate management environment (ACME) protocol is an open-source, industry-standard protocol that facilitates automation for PKI digital certificates’ validation and issuance procedures. Your software/platform may have built-in support for ACME, and there are also many open-source agents available you can install.
Offer Automation to Web Hosting Customers with AutoInstall SSL
What if you’re an IT hosting or service provider that wants to automate SSL/TLS for your customers? You can make getting and installing SSL/TLS certificates a breeze with AutoInstall SSL. This plugin automates many integral processes relating to generating certificate signing requests, validating domains, and installing certificates. This plugin is available for cPanel, DirectAdmin, and Plesk.
Let’s Wrap This Up
You came here to discover what to do when you discover an expired security certificate on your network. Hopefully, this guide on how to renew a security certificate that expired was helpful and answered many of your questions. If you have additional insights or questions about how to fix expired certificate issues, be sure to leave us a comment below.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown