Expired SSL Certificate Knocks Pokemon Go Offline
Managing multiple SSL certificates can prove challenging.
Pokemon Go, the popular augmented reality mobile phone game, was offline briefly on Monday, January 22nd as a result of an expired SSL certificate.
It seems like we get about one of these stories per month, if you’ll remember the UK Conservative Party was just in the news for a similar gaffe.
And it might be tempting to slam Pokemon Go’s creator, Niantic, but given the scale of their digital infrastructure, these kinds of mistakes are a bit more common than you might realize. Here’s a screenshot of the expired certificate, courtesy of GameRant.
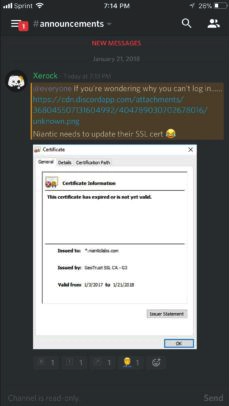
While the damage was minimal, with Niantic’s massive player base only being without access for about half an hour, the mistake will likely become just another chapter in a game that has dealt with its share of bugs, server issues and missing or delayed features.
But let’s not pile on to Niantic too much. Again, a game with a global reach such as Pokemon Go, that is available on multiple platforms, is going to require a digital infrastructure of equally impressive proportions.
While we prefer to keep a barrier between our parent company and the activities of Hashed Out, I can say with certainty that one of the biggest challenges The SSL Store’s enterprise clientele face is certificate visibility. That’s why almost every scaled Enterprise security solution that’s offered comes with a certificate discovery feature that helps to find and identify every active digital certificate you have deployed.
Oftentimes larger companies have ordered certificates in multiple batches from multiple certificate authorities and given the size and scale of the operation, sometimes things fall through the cracks.
That was likely the case here. We reached out to Niantic and as of publication had yet to receive any comment back. We will update this story if we hear from them.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown