What Is a CAA Record? Your Guide to Certificate Authority Authorization
Not all certificate authorities are created equally — some are more trustworthy than others. But did you know that there’s a way to control which CAs can issue certificates for your domain? Here’s everything to know about DNS CAA records…
Let’s say, for some reason, that you don’t like or trust a particular certificate authority (CA). Maybe they’re untrustworthy because they’ve had of a bunch of certificate mis-issuances or revocation issues in the past. Or, perhaps, they’ve just sent you one too many annoying sales emails in the past and you want to stick it to ‘em. On the other hand, maybe you want to just use one or two CAs to make certificate management easier (that’s a good idea, btw). Whatever the reason, there’s a way to lock down your domain and specify which CAs issue can issue certificates on your behalf: You can create something that’s known as CAA record.
This is what’s known as setting certificate authority authorization, or CAA for short.
Some of our customers or resellers ask us, “what’s CAA?” or “how do I create a CAA record?” We could tell you that it means “certificate authority authorization” and say that it involves generating a DNS record before calling it a day. But that won’t really help you and, as you now likely know by now, that’s not really our style at Hashed Out. (Especially since there are several reasons why organizations may want to use CAA for their domains and different ways to create CAA record for their domains.)
With this in mind, we’re rolling up our sleeves to dive deep into the topic of certificate authority authorization. We’ll cover what CAA DNS records are, why they’re so important, and how you can create one for your domain. We’ll also discuss what issues can arise with certificate authority authorization. But first, what is a CAA and how does it help you to secure your domain?
Let’s hash it out.
What we’re hashing out…
- Not all certificate authorities are created equally — some are more trustworthy than others. But did you know that there’s a way to control which CAs can issue certificates for your domain? Here’s everything to know about DNS CAA records…
- CAA Meaning: What Is a Certificate Authority Authorization?
- What Is a CAA DNS Record (CAA Resource Record)?
- How to Add, Edit, or Create a CAA Record
- How CAA Works & the Role Certificate Authority Authorization Plays in Cert Issuance
- Why You May Want to Consider Creating a CAA DNS Record for Your Domain
- Need to Generate a CAA DNS Record? Look No Further
- Final Thoughts on Certificate Authority Authorization and DNS CAA Records
![]() CAA Meaning: What Is a Certificate Authority Authorization?
CAA Meaning: What Is a Certificate Authority Authorization?
Certificate authority authorization is a domain name system (DNS) security measure that helps you to increase control of your brand identity. More specifically, certificate authority authorization is a DNS record that lets you specify which certificate authorities are allowed to issue SSL/TLS certificates for your domain. (SSL/TLS digital certificates, which are also known as website security certificates, add identity and encryption to connections between clients and your web server.)
A CAA record looks like this:

In this example, only DigiCert and Sectigo are authorized to issue certificates for this domain. Note: CAA records aren’t a suggestion or a request — certificate authorities are required to obey them. If they don’t, they can be distrusted. But we’ll get more into the technical details/specifics in just a little bit. (Patience, young padawan.)
As stated in the current Internet Engineering Task Force (IETF) proposed standard (RFC 8659):
The Certification Authority Authorization (CAA) DNS Resource Record allows a DNS domain name holder to specify one or more Certification Authorities (CAs) authorized to issue certificates for that domain name. CAA Resource Records allow a public CA to implement additional controls to reduce the risk of unintended certificate mis-issue.”
As the domain name holder, you can also specify whether your chosen CA (or CAs, if multiple) can issue wildcard or non-wildcard certificates. So, in a way, having a CAA is kind of like having authorization to see an in-network doctor through your insurance here in the U.S.: It specifies the physician(s) you can see and which covered services they are authorized to provide.
How Certificate Authority Authorization Came to Be (and What Issues It Presents)
Certificate authority authorization first became an IETF proposed standard in RFC 6844 in October 2010, according to the IETF’s DataTracker tool. In 2017, the CA/Browser Forum (CA/B Forum) voted to pass Ballot 187, a measure that makes checking CAA records mandatory for CAs to do before issuing an SSL/TLS certificate. According to the CA/B Forum ballot:
The intent of this motion is to make it mandatory for CAs to check CAA records at issuance time for all certificates issued (except in a few special cases), and to prevent issuance if a CAA record is found which does not permit issuance by that CA. This therefore allows domain owners to set an issuance policy which will be respected by all publicly-trusted CAs, and allows them to mitigate the problem that the public CA trust system is only as strong as its weakest CA.”
However, RFC 6844 wasn’t perfect; it had some issues that needed to be addressed. According to Timothy Hollebeek, DigiCert’s CA/B Forum representative:
The original RFC specified a search algorithm for CAA that improperly handled CNAME and DNAME CAA records, preventing some organizations that should have been able to obtain certificates from receiving them. In addition, there were a number of errors in the specification of how CAA records should be formatted, as well as a lack of information about what to do if a CAA record exists but does not contain a record listing authorized CAs.”
This is what led to the current proposed standard, RFC 8659, which we mentioned a little earlier. Many of the technical issues relating to CAA record checking are addressed in this new version of the proposed standard.
Now that we know what CAA is and its history, let’s get to talking about CAA records themselves.
What Is a CAA DNS Record (CAA Resource Record)?
A CAA record — or what’s also known as a DNS CAA record, CAA DNS record, CAA record, CAA certificate, or DNS CAA — is a type of public policy for your domain name system. It’s a way for you as a domain owner to make it known to everyone which certificate authorities can issue SSL/TLS certificates for your domain. This record gives public certificate authorities a place to look to identify whether they’re eligible to issue a certificate for your domain.
The domain name system itself is the naming system that makes the internet easy to use. It’s like a translator that converts a domain name into an IP address that the server can use to retrieve the right website. So, when you want to pull up a specific website in your browser, the DNS system makes it so that you can type in the website domain instead of having to remember the full IPv4 or IPv6 numerical IP address.
For example, you can type in thesslstore.com to get to our website instead of having to remember the IP address 104.22.3.46.
But just how many websites actually use CAA records? Qualys reports in its July 8, 2020 data that 10,581 websites — or (7.6% of the sites they surveyed — support certificate authority authorization. Considering that Qualys reported 8,329 CAA-supporting sites (or 6% of surveyed sites) as of July 3, 2019, you can see that certificate authority authorization is slowly gaining traction.
What Does a DNS CAA Record Look Like?
You remember earlier when I said we were going to get dirty? Yeah, it’s time to roll up those sleeves — we’re getting into the nitty-gritty of CAA records.
If you want to see what a real DNS CAA record looks like for a little more clarity, check out the DNS Lookup tool on dnschecker.org. Here, we’ve pulled up the CAA record for the certificate authority DigiCert:
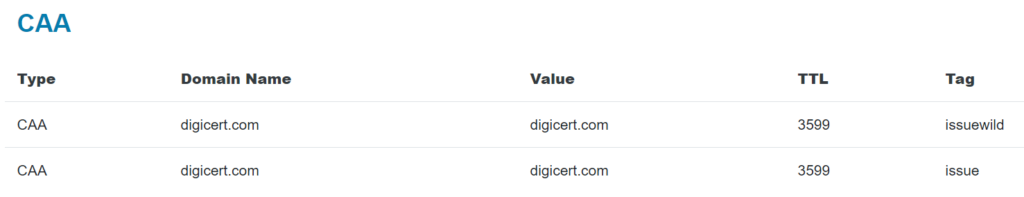
As you now know, a CAA certificate record is basically a set of instructions that tell CAs what they are or are not authorized to do in terms of issuing all or specific types of certificates. However, what you may not know is that CAA records are formatted differently depending on which DNS files they’re being added to.
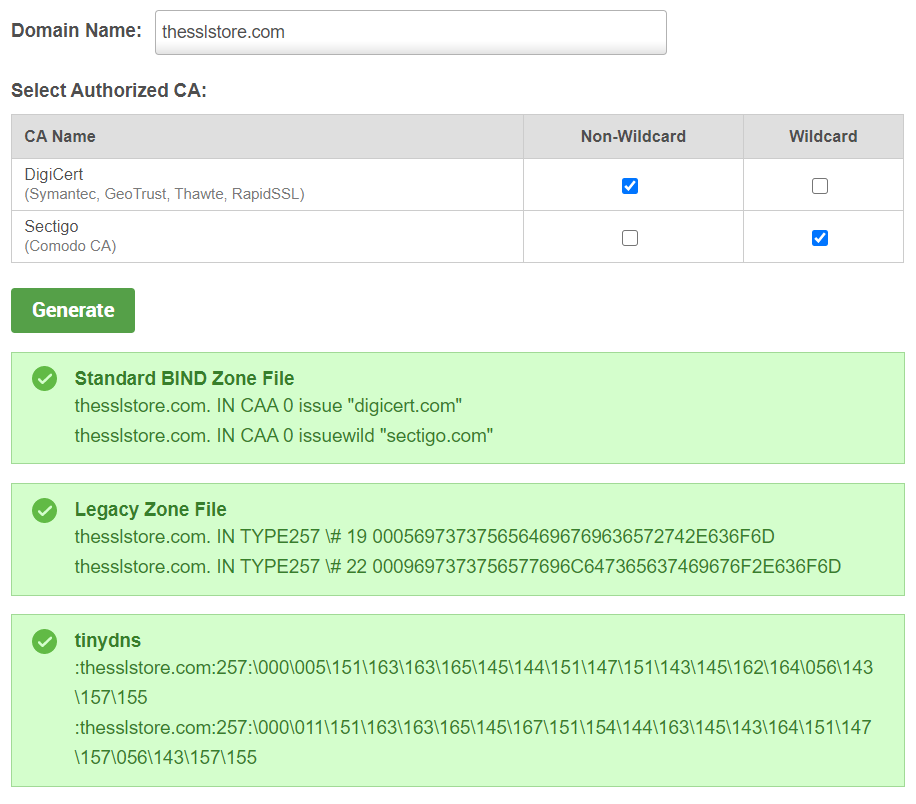
For example, the syntax for a standard BIND zone file will be different from that of a legacy zone file. Which version you may have to use will vary depending on your DNS product. For example:
- IETF RFC 6844 specifies the format for standard BIND files.
- IETF RFC 3597 specifies the format of resource records (RRs) for legacy BIND files.
Here are some examples of how CAA records can look for these different files:
Now, you might be thinking: “Ugh, do I really need to know all of this to create a CAA record?” In most cases, no. That’s because, if you’re like most people, you use your domain registrar’s DNS servers rather than running one of your own. When you use third-party DNS servers, you can just use their systems or your control panel to create CAA DNS records.
We’ll actually show you how to do that in cPanel a little later. But first, we still have a few more things to cover.
What Goes Into a CAA Record
For the purpose of this article, we’re going to focus on the CAA record canonical presentation format as it’s outlined in RFC 8659 (since it obsoletes RFC 6844):
CAA <flags> <tag> <value>Remember seeing something like this a little earlier? We’re going to break down what each part of it means.

As you can see in this example above, a DNS CAA record has surprisingly pretty basic setup … so long as you know what the different parts of it are, that is. Otherwise, it can be a bit confusing.
DNS CAA records include the following components:
- Flags — A flag, as outlined in RFC 6844, can be one of two specific states: 1 (critical) or 0 (non-critical) with 0 as the default. However, much like with the tags, a CA can create their own custom flags as well to give specific directions for issuance.
- The 1 flag tells the CA that it can’t use the CAA record in the zone if it doesn’t understand the property. Basically, it tells it that it can’t proceed further with trying to issue the certificate and should send an email notifying the domain owner about the CAA record check failure.
- The 0 flag tells the CA that it can use any CAA record info in the zone regardless of whether it understand the property. If it doesn’t understand this CAA record, it can skip over it and use another in the DNS zone file.
- Tags — A tag specifies which actions an authorized CA can take in terms of issuing SSL/TLS certificates. The three tags that are outlined in RFC 6844 are issue, issuewild, and iodef. However, it’s important to note that CAs can also specify their own custom tags to provide directions for the cert issuance process.
- The issue tag authorizes a specific CA to issue non-wildcard certificates for the domain and any of its subdomains. However, this tag can also be used to restrict any CAs from issuing non-wildcard certificates for those same subdomains (a little more on that momentarily).
- The issuewild tag authorizes a specific CA to issue wildcard certificates for the domain.
- The iodef tag (what stands for “incident object description exchange format”) provides info about invalid certificate requests. Basically, this gives you (as the domain owner), the ability to receive an email whenever a certificate request fails a CAA check. This way, you can stay abreast of CAA-related issues and fix the error that causes the failure.
- Values — A value (typically listed between double quotation marks) is the domain of the CA that has the authority to issue certificates for the domain in question. If the value is a semicolon (;), it means that no CA has the authority to issue a certificate for that domain.
- TTL — A TTL field, which stands for “time to live,” refers to the period of time (seconds) that a server should keep your CAA record in its cache.
Yeah, that was a lot to take in. Take a deep breath and grab some more coffee ‘cause we’re not done yet. Now it’s time to put all of this together.
Examples of DNS CAA Records
Let’s say, for example, that we want a CAA DNS record for TheSSLStore.com that specifies that only DigiCert and Sectigo can issue non-wildcard certificates for the TheSSLstore.com. The CAA record would look something like this:
thesslstore.com. CAA 0 issue “digicert.com”
thesslstore.com. CAA 0 issue “sectigo.com”Now, if we want to ensure that only Sectigo can issue wildcards and only DigiCert can issue other SSL/TLS certificates, the CAA DNS record would look something like this:
thesslstore.com. CAA 0 issue “digicert.com”
thesslstore.com. CAA 0 issuewild “sectigo.com”Now, to set IODEF properties for your CAA record, the syntax should look something like this:
thesslstore.com. CAA 0 issue “digicert.com”
thesslstore.com. CAA 0 iodef “mailto:email@thesslstore.com”
thesslstore.com. CAA 0 iodef “http://iodef.thesslstore.com”Okay, now that we know what CAA records are and how they look, let’s jump into how you can put them to use for your website.
How to Add, Edit, or Create a CAA Record
There are multiple ways that you can add, edit, or create a CAA certificate record for your domain or subdomain. For example, if you have your own DNS server and want to add or edit your CAA record directly in the DNS BIND file, you’ll want to:
- Use Notepad to open your domain’s DNS file. This avoids inadvertently adding any code that other word processing programs like Microsoft Word.
- Add or update the DNS CAA record information to that file. This is where you add or alter the information (tags, values, flags, etc.) like what you see above.
- Save the zone file in Notepad and close out of it.
That’s it!
But what if you want to create a CAA record using your control panel or your domain registrar’s DNS? No worries, you can do that easily. We’ve put together direction for cPanel (below). For your third-party domain registrar, though, you’ll have to go through them directly.
How to Add a CAA Record in cPanel
If you wish to create a certificate authority authorization record within cPanel, you can do that as well by doing the following:
1. Log into your cPanel account.
2. Scroll down to the Domains section and select Zone Editor.
3. Find the domain you wish to create a CAA record for and select Manage.
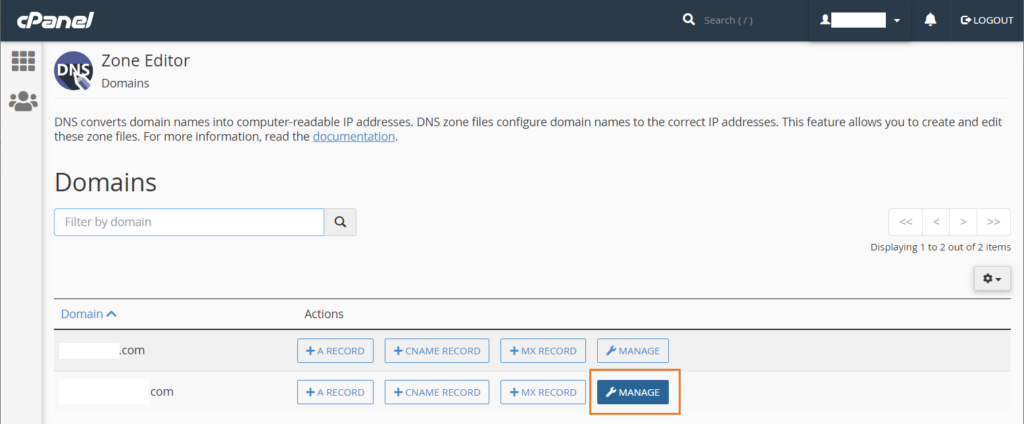
4. In the Zone Editor, look for a blue button labeled Add Record and click the down arrow. From the drop-down list, select Add “CAA” Record.
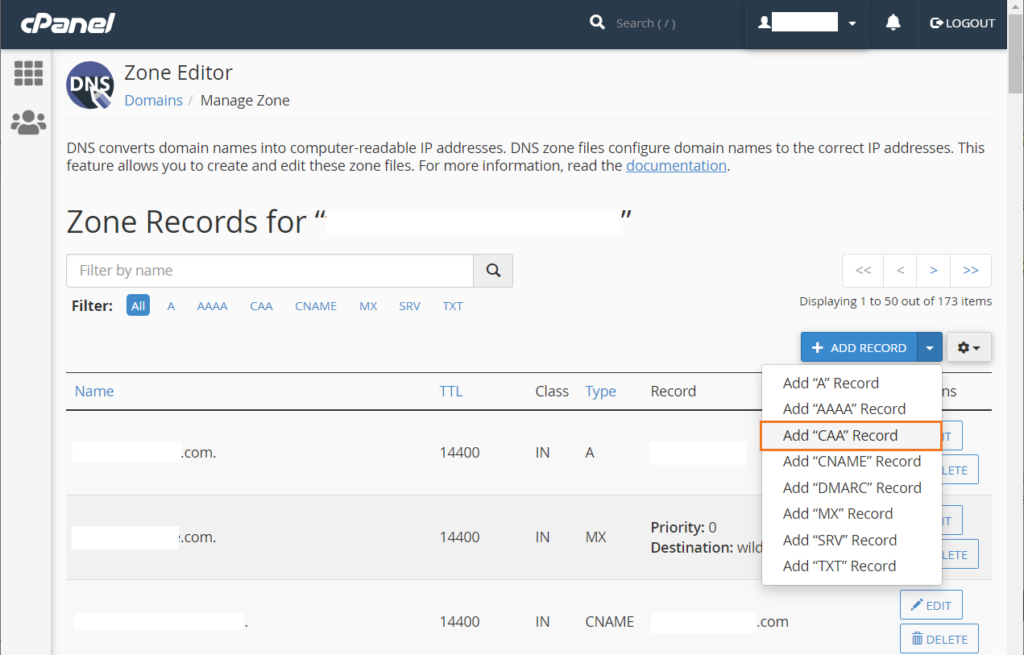
5. In the Zone Editor menu for that specific domain, select the right option or fill in the missing info for the form’s required fields. This includes:
- The name of the website (the domain or sub-domain you wish to add a CAA record for).
- The record type (CAA).
- The flag (0 or 1).
- The tag (issue, wildissue, iodef).
- The value (the domain of the CA that you’re giving authority to create SSL/TLS certificates).
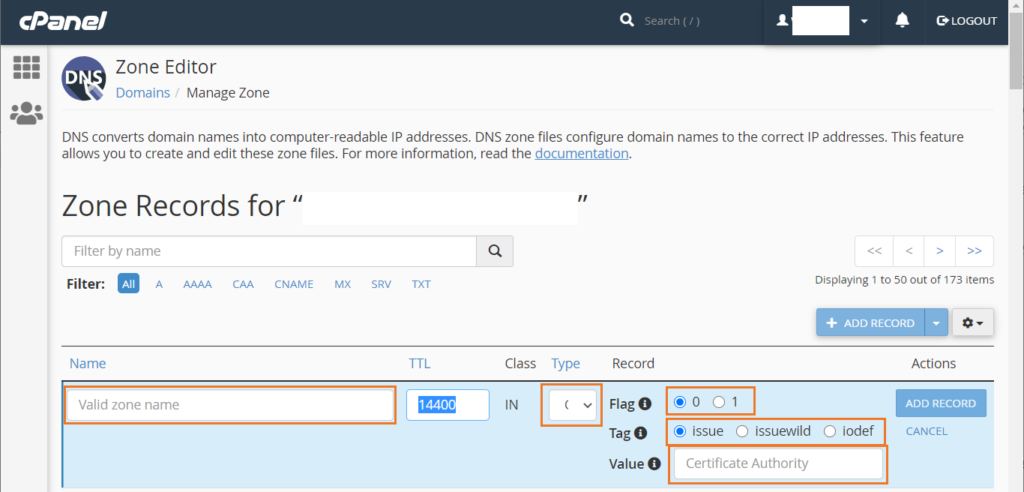
Once you’ve completed these steps, simply select Add Record next to the entry on the right-hand side to save your work.
That’s it!
How CAA Works & the Role Certificate Authority Authorization Plays in Cert Issuance
Whenever a certificate authority receives a request to issue a new certificate, they first check to see whether any CAA records exist for that domain. This is because of the CA/B Forum ruling that dictates that all commercial CAs must check for CA records before issuing any certificate.
Here’s what happens when a publicly trusted CA runs a CAA DNS records check:
- If there is a CAA record: The CA must check to see whether they are authorized to issue a cert and verify that the certificate request matches the CAA record specifications.
- If yes to both, then the CA can move to the next phase of the certificate issuance process.
- If no to one or both, then the CA should reject the request outright.
- If no CAA DNS record exists: If the CA can’t find a CAA record for the domain in question, it will proceed with next phase of the certificate issuance process.
It’s important to note, though, that CAA records work hierarchically. This means that if someone requests a certificate for one of your subdomains and there’s no CAA record available for that subdomain, the CA will automatically look at the next level up in the DNS name tree to search for a CAA record there. If they find one on the root domain, that will be used for the subdomain in question as well.
But where exactly does the CAA records check fit into the certificate issuance process for publicly trusted CAs?
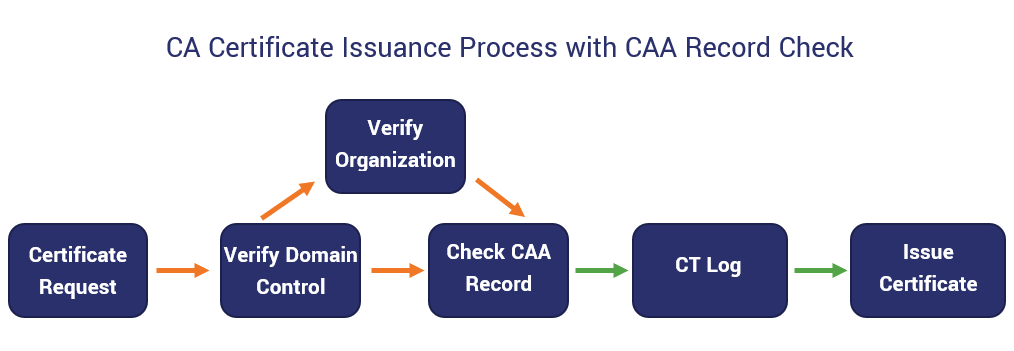
A Look at Certificate Authority Authorization in Action…
Let’s consider the following example to better understand how certificate authority authorization applies to a real-world situation.
Say you want to authorize Sectigo and DigiCert to issue certificates on your behalf but no one else. What you’ll do is create a CAA DNS record. This CAA record makes it so that any time a request for a new certificate goes to a publicly trusted CA, they’ll see the record that says only those two specific CAs can issue certificates for your domain. So, when the CA checks for the domain’s CAA DNS record, they’ll see that they basically have either a red light or a green light in terms of whether they halt or continue with the certificate issuance process.
This means that if someone tries to request a certificate for your domain through another publicly trusted CA — GoDaddy, Let’s Encrypt, or anyone else — their certificate signing requests will receive the big, fat stamp of rejection.
One last quick but also important note: Although all CAs are required to perform a CAA DNS records check, it doesn’t mean that you as the domain name owner have to create a CAA record. If you don’t have any CA-related requirements that you need to specify, then you don’t have to create a CAA record. There’s no obligation one way or the other for domain owners.
But what are the advantages of using CAA for your domain (and subdomains)?
Why You May Want to Consider Creating a CAA DNS Record for Your Domain
Despite the issues that have come up previously, using a CAA helps you to prevent certificate mis-issuance. Some of the biggest advantages of implementing certificate authority authorization include:
- Preventing fraud or misrepresentation of your brand. Specifying which CA (or CAs) can issue certs for your domain helps you to prevent cybercriminals from requesting unauthorized certificates through unauthorized CAs. This helps to protect the identity of the certificate holder.
- Limiting shadow certificates. By making it so that only the CAs that you have company accounts with can issue certs for your domain may help you to limit shadow certificates.
- Adding an additional layer of security prior to certificate issuance. Requiring this CAA records check through the DNS is a more technical way of ensuring that a CA verifies whether they have the authority to fulfill a certificate request.
- Showing your preference and support for specific CAs. If, for one reason or another, you only want your organization’s name or reputation associated with a particular publicly trusted CA, you can make that possible with CAA.
- Enhanced certificate management. With CAA, you can better manage your certificates under one umbrella rather than trying to track certificates from multiple CAs.
Need to Generate a CAA DNS Record? Look No Further
Did you know that we have a CAA record generator tool here at The SSL Store? Not to toot our horn (at least not too much), but it’s actually a really great way to automatically generate a DNS record for your domain. And if you have a DNS through your domain registrar, we have directions there for how to create a CAA DNS record for multiple providers, too.
Whether you choose to set up a CAA DNS record or not is entirely up to you. As an SSL/TLS certificate provider that works with many of the world’s leading CAs, we have no dog in this race. We just want to ensure you have as much information as possible to make an informed decision about what’s best for your brand identity and domain security.
Final Thoughts on Certificate Authority Authorization and DNS CAA Records
As you can see, using CAA has its advantages. Not only does it give you greater control of managing your domain’s SSL/TLS certificates, but it also gives you greater control of your brand identity as a result. While it’s not perfect, and you certainly can see the progression of this standard over time in the IETF’s requests for comments, certificate authority authorization does hold promise and is a great way to add another layer of identity and security to your domain.
We hope this article has provided you with greater clarity about what CAA is and why creating a CAA DNS record may be valuable for your organization. There are a lot of important little pieces that make up each CAA record, and understanding the role of each component is crucial to making the use of CAA most valuable for your organization or business.
Have questions or additional insights? Feel free to share in the comments below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown