Cloudflare Debuts Improvements During “Encryption Week”
TLS 1.3, Opportunistic Encryption, and Automatic HTTPS Rewrites.
Cloudflare has deemed this to be “Encryption Week” and will be rolling out three major improvements to their network’s SSL/TLS capabilities.
The improvements are designed to improve performance, ease deployment of SSL, and make encrypted connections available to a wider audience.
All of these new features are now available to all Cloudflare customers, including their free plan users.
TLS 1.3
The newest version of our favorite protocol – TLS 1.3 – is still being drafted by the IETF. But that is not stopping Cloudflare from deploying the in-progress protocol.
With new authenticated encryption suites that improve security, and major improvements in performance – TLS 1.3 handshakes can be up to 40% faster – it’s no wonder why they are eager to start as soon as possible.
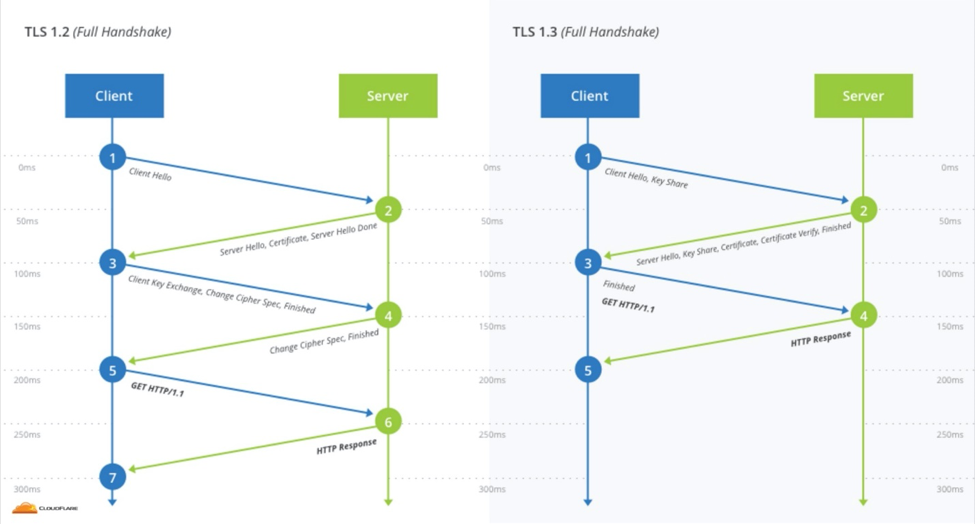
The TLS 1.3 Handshake can be completed with fewer “roundtrip” connections, which can significantly reduce connection time. Image courtesy of Cloudflare.
If you are a Cloudflare user, you need to opt in to TLS 1.3. On the client side, you won’t see any changes unless you are using developer releases of Chrome or Firefox; since TLS 1.3 is still being drafted the standard versions of browsers don’t yet support it.
Automatic HTTPS Rewrites
One of the biggest problems websites face when adopting HTTPS is mixed content.
Mixed content is when a given page has both HTTP and HTTPS resources. When this happens browsers treat the page as insecure because all the resources can’t be loaded safely. That means no green padlock or EV address bar – and that your users aren’t entirely protected.
Fixing mixed content isn’t always easy – even major sites struggle with it – because there are a variety of reasons why it exists in the first place. When HTTPS simply isn’t supported by a site, there is not going to be an easy solution.
But one of the most common sources of mixed content does have an easy fix. Many sites that do have HTTPS capabilities simply aren’t taking full advantage – usually because their source code has explicitly written HTTP links, causing browsers to load the content insecurely. In this case “manually changing “http” to “https” in the page’s source is often enough to fix mixed content.”
But administrators may not know that this needs to be done, and “many sites can’t do that because their sites are created dynamically by content management systems or they include third party resources that they have no control over.”
That’s why Cloudflare is introducing Automatic HTTPS Rewrites. They will simply spot mixed content and upgrade URLs from “HTTP” to “HTTPS.”
Cloudflare will detect when this can be done by looking at “EFF’s HTTPS Everywhere list, Chrome’s HSTS preload list” to know what sites can support HTTPS without introducing any breakage. Over time, Cloudflare hopes to build their own list to expand compatibility.
Opportunistic Encryption
Opportunistic Encryption (OE) is an alternative to traditional HTTPS. Instead of real “HTTPS” that we know and love, it’s “HTTP requests with Opportunistic Encryption over TLS.”
The difference is subtle, but important. Opportunistic Encryption allows HTTP requests to be made over an encrypted TLS connection. OE can even be used with a valid and trusted certificate.
It may help to think of Opportunistic Encryption as Optional Encryption. It tells the browser to use encryption if it can. If it can’t, that’s okay. This means there are no security guarantees.
Therefore, browsers treat OE differently. Sites using OE are still accessed over HTTP. “Users will not see a security indicator… in the address bar when visiting a site using Opportunistic Encryption, but the connection from the browser to the server is encrypted.”
Nick Sullivan, Cloudflare’s Cryptography lead, wrote “to be clear, Opportunistic Encryption is not a replacement for HTTPS.”
Despite the drawbacks, OE is helpful for sites that can’t adopt HTTPS yet – primarily websites that have unfixable mixed content issues.
Because OE connections are encrypted, it will allow those sites to use HTTP/2. Though, only with browsers that support OE. Currently, that would only be Firefox (after all, the technology was designed by Mozilla engineers).
For now, Opportunistic Encryption is essentially some clever engineering to spread transport encryption to a small section of the internet. If you want to learn more about OE, Cloudflare has an entire blog post on the topic.
Encryption for All!
Cloudflare has been doing a lot to make it easier for websites to deploy HTTPS and HTTP/2. As one of the world’s largest CDNs, these latest improvements are giving new technologies a huge jump start in adoption.
TLS 1.3 isn’t even finalized yet and already more than 4 million sites support it thanks to Cloudflare! We can’t wait to see what they rollout next.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown