TLS Interception Warnings Coming in Google Chrome 63
Google’s browser will warn users about Man-in-the-Middle attacks starting in Chrome 63.
Google Chrome will add an interstitial warning notifying users of HTTPS interception starting in Chrome 63. The warning can currently be viewed in Chrome’s dev browser, Canary, with a quick tweak. The stable version of Chrome 63 is set to go live December 5, 2017.
Now let’s hash out what this means, and why it’s relevant.
As you’re aware, the internet is moving rapidly towards universal encryption. The “http” protocol you see at the front of URLs is being replaced by “https,” which allows all data being transmitted to be secured with encryption. To aid in the proliferation of HTTPS, Google and the other browsers have incentivized it. Websites that add SSL and migrate to HTTPS have been given perks like small SEO boosts, access to advanced browser features and the promise of HTTP/2.
Google’s decision to add this warning is a different approach that aims to accomplish the same thing: complete encryption.
And one thing that interrupts complete encryption is HTTPS interception, sometimes called TLS interception.
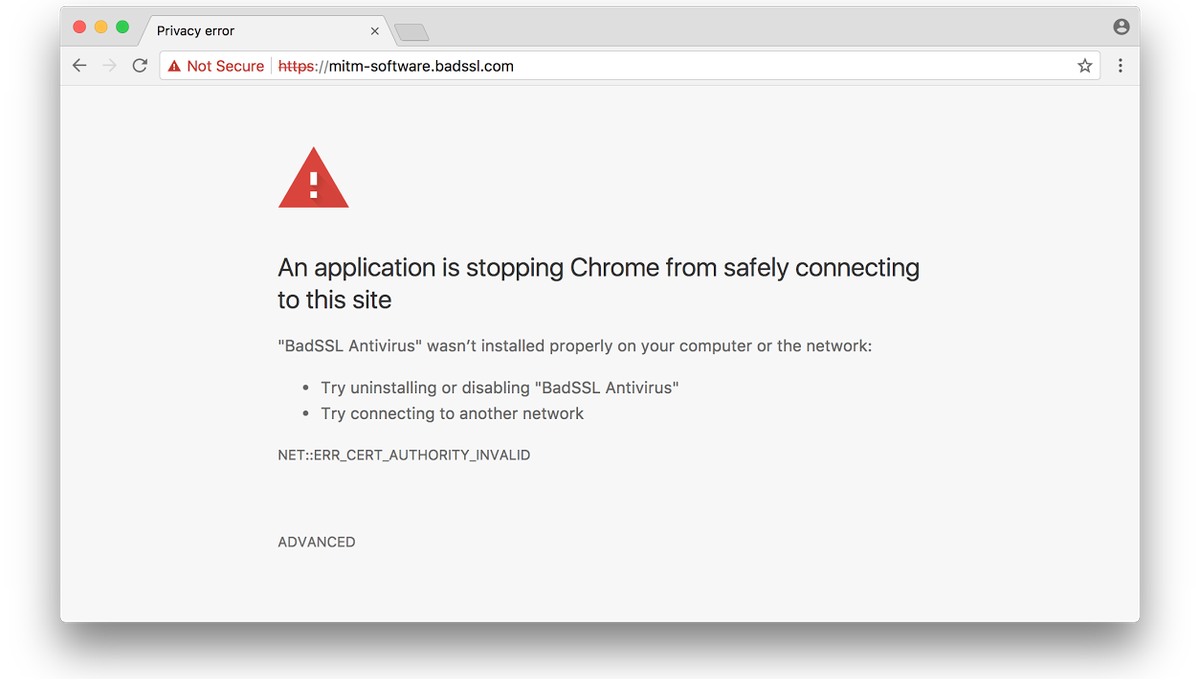
Two Kinds of TLS Interception
For the sake of this discussion, we’re going to divide TLS Interception into two main categories: Man-in-the-Middle attacks, which this alert will actively warn users about, and HTTPS Interception.
A Man-in-the-Middle attack is where an attacker is able to position him or herself between a user and the server that user is communicating with. As the name suggests, the man-in-the-middle can intercept and inspect all data transmitted between the two parties it’s spying on. It can even manipulate that information if it wants to.
SSL prevents a great number of MITM attacks just by virtue of adding encryption in the first place. But it is possible for an attacker to intercept the encryption and perform a MITM attack even when SSL is in place. Often times this sort of vulnerability occurs because of misconfiguration on the part of the site administrator, but it’s a threat nonetheless. In many cases, an affected user may not even know that an attack has taken place beyond getting a few TLS errors during their browsing experience.
Google’s decision to add a TLS interception warning will help alleviate that by presenting users with an unpassable interstitial warning anytime interception is detected. It will flag whenever it notices an AV CA that is not in its trust store (h/t to Patrick Figel for this correction).
The Other Kind of HTTPS Interception
Now let’s talk about the other reason to intercept HTTPS traffic. Technically, this category still constitutes MITM, but its aim is a little different. In this instance, you’re intercepting HTTPS traffic to inspect it for security purposes.
Now, this type of HTTPS interception is controversial. While many of the security companies that sell it claim that it is harmless, there have been studies that show HTTPS Interception weakens the overall security of users’ data.
When HTTPS interception is being done for security reasons, an intercepting device is placed between the client and the server. In this arrangement, two connections are needed, one between the client and the interceptor, and one between the interceptor and the server. The reason for intercepting is to inspect traffic for malware and malicious requests.
Frankly, the topic of HTTPS Interception as a security practice is a completely different debate for another time. There are valid points on both sides, but the evidence tends to point towards the practice being harmful. I’m just mentioning it to help complete this discussion.
Either way, this type of HTTPS interception is unlikely to trigger Google’s new TLS Interception warning.
How to Enable TLS Interception Warnings on Canary
While you’ll have to wait for Chrome 63 in December for these changes to show up on their own, you can enable Google’s TLS Interception warning on Chrome’s dev browser, Canary. Here’s how to do it:
- Find the Google Chrome Canary icon/shortcut and double click on it.
- Choose “Properties” from the drop-down menu.
- In the “Target” field, add the following text “–enable-features=MITMSoftwareInterstitial” and hit “Save.”
What We Hashed Out (For Skimmers)
Here are the key points we covered in today’s discussion:
- Google will add a TLS Interception warning to its browser starting in Chrome 63
- TLS Interception, sometimes called HTTPS Interception, involves placing a “man-in-the-middle” between a client and a server to inspect traffic or inject content
- The TLS Interception warning will be available in December 2017, but can be added to Canary today





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown