Protection Guideline to Protect Yourself from “Heart Bleed” OpenSSL Bug
What is Heartbleed?
 Heartbleed is a security concern for users of OpenSSL, a widely-used opensource cryptographic software library. The error allows anyone to read the memory of servers supposedly protected by SSL, and reveals the cryptographic keys that allow messages to be decoded, the credentials of users, and the content. Once the keys are compromised, attackers can look at any communications with impunity, completely undetected. However, it is important to note that this is a vulnerability of OpenSSL software, NOT a flaw with SSL or the certificates themselves.
Heartbleed is a security concern for users of OpenSSL, a widely-used opensource cryptographic software library. The error allows anyone to read the memory of servers supposedly protected by SSL, and reveals the cryptographic keys that allow messages to be decoded, the credentials of users, and the content. Once the keys are compromised, attackers can look at any communications with impunity, completely undetected. However, it is important to note that this is a vulnerability of OpenSSL software, NOT a flaw with SSL or the certificates themselves.A serious filled vulnerability in the OpenSSL cryptographic library affects around 17.5% of SSL web servers which use certificates issued by trusted certificate authorities, as per a recent Netcraft survey. This accounts for around a half a million certificates. Already commonly known as the Heartbleed bug, a missing bounds check in the handling of the TLS heartbeat extension can allow remote attackers to view up to 64 kilobytes of memory on an affected server.
This could allow attackers to retrieve private keys and ultimately decrypt the server’s encrypted traffic or even impersonate the server. These certificates are consequently vulnerable to being spoofed (through private key disclosure), allowing an attacker to impersonate the affected websites without raising any browser warnings.
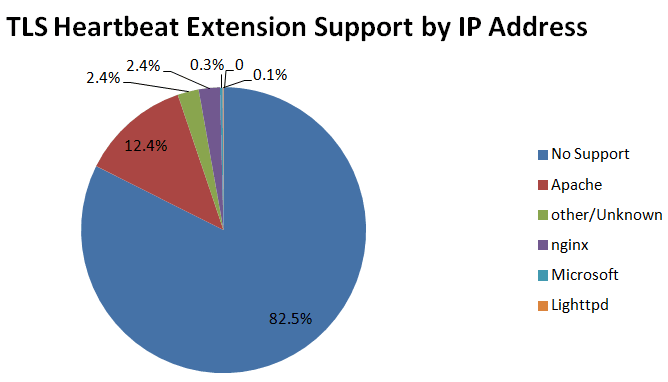
Please note that a small percentage of Microsoft web servers also appear to support the TLS heartbeat extension; these are actually likely to be vulnerable Linux machines acting as reverse proxy frontends to Windows servers.
Support for heartbeats was added to OpenSSL 1.0.1 (released in 2012) by Robin Seggelmann, who also coauthored the Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) Heartbeat Extension RFC. The new code was committed to OpenSSL’s git repository just before midnight on New Year’s Eve 2011.
OpenSSL’s security advisory states that only versions 1.0.1 and 1.0.2-beta are affected, including 1.0.1f and 1.0.2-beta1. The vulnerability has been fixed in OpenSSL 1.0.1g, and users who are unable to upgrade immediately can disable heartbeat support by recompiling OpenSSL with the -DOPENSSL_NO_HEARTBEATS flag.
How to Protect Yourself from the Heartbleed Bug
First, check which sites are affected and identify the ones that you use. If you don’t want to read through the long list of websites with the security flaw, the password security firm LastPass has set up a
Heartbleed Checker, which lets you enter the URL of any website to check its vulnerability to the bug and if the site has issued a patch.
Here are some websites that we recommend changing passwords for immediately:
| Website | Was it affected? | Is there a patch? | Do you need to change your password? |
| Unclear | Yes | Yes | |
| What Facebook Officials Said: “We added protections for Facebook’s implementation of OpenSSL before this issue was publicly disclosed. We haven’t detected any signs of suspicious account activity, but we encourage people to … set up a unique password.” | |||
| Tumblr | Yes | Yes | Yes |
| What Tumblr Officials Said: “We have no evidence of any breach and, like most networks, our team took immediate action to fix the issue.” | |||
| Unclear | Unclear | Yes | |
| What Twitter Officials Said: Twitter has not yet responded to a request for comment. | |||
| Yes | Yes | Yes | |
| What Google Officials Said: “We have assessed the SSL vulnerability and applied patches to key Google services.” Search, Gmail, YouTube, Wallet, Play, Apps and App Engine were affected; Google Chrome and Chrome OS were not. Google said users do not need to change their passwords, but because of the previous vulnerability, better safe than sorry. | |||
| Yahoo | Yes | Yes | Yes |
| What Yahoo Officials Said: “As soon as we became aware of the issue, we began working to fix it… and we are working to implement the fix across the rest of our sites right now.” Yahoo Homepage, Yahoo Search, Yahoo Mail, Yahoo Finance, Yahoo Sports, Yahoo Food, Yahoo Tech, Flickr and Tumblr were patched. More patches to come, Yahoo says. | |||
| Gmail | Yes | Yes | Yes |
| What Gmail Officials Said: “We have assessed the SSL vulnerability and applied patches to key Google services.” Google said users do not need to change their passwords, but because of the previous vulnerability, better safe than sorry. | |||
| Yahoo Mail | Yes | Yes | Yes |
| What Yahoo Mail Officials Said: “As soon as we became aware of the issue, we began working to fix it… and we are working to implement the fix across the rest of our sites right now.” | |||
| Amazon Web Services (for website operators) | Yes | Yes | Yes |
| What Amazon Officials Said: Most services were unaffected or Amazon was already able to apply mitigations. Elastic Load Balancing, Amazon EC2, Amazon Linux AMI, Red Hat Enterprise Linux, Ubuntu, AWS OpsWorks, AWS Elastic Beanstalk and Amazon CloudFront were patched. | |||
| Dropbox | Yes | Yes | Yes |
| What Dropbox Officials Said: On Twitter: “We’ve patched all of our user-facing services & will continue to work to make sure your stuff is always safe.” | |||
| LastPass | Yes | Yes | Yes |
| What LastPass Officials Said: “Though LastPass employs OpenSSL, we have multiple layers of encryption to protect our users and never have access to those encryption keys.” | |||
| Wunderlist | Yes | Yes | Yes |
| What Wunderlist Officials Said: “You’ll have to simply log back into Wunderlist. We also strongly recommend that you reset your password for Wunderlist.” | |||
Lastly – as always – make sure to keep an eye on your sensitive online accounts, especially banking and email, for suspicious activity, especially for the next week or so.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)











5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown