Majority of US Federal Websites Using HTTPS
This time, the government is ahead of the security curve.
Everyone is adopting HTTPS, even the federal US government, which is frequently criticized for being far behind the technological curve.
But thanks to 18F, an agency of the government building modern software, and some federal policy changes, .gov sites are getting secure access at a break-neck pace. In fact, 18F says “the government now outpaces the private sector on HTTPS.”
In 2015, the White House released a mandate requiring federal websites adopt HTTPS – which they call the “HTTPS-Only Standard.” It requires all newly developed federal government sites and services use HTTPS, and existing sites had until the end of 2016 to support HTTPS.
Unfortunately, we are not here to say that 100% of .gov site are HTTPS, that goal has not been fully realized yet. But in the past year and a half, HTTPS use went from “a clear minority to a clear majority.”
18F’s Eric Mill (one of the sharpest guys working on HTTPS) recently wrote about .gov’s progress so far.
They looked at HTTPS support of .gov domains from June 2015 to this month, January 2017. In that time, the number of .gov sites using HTTPS more than doubled – around 60% are now using HTTPS. When weighted by popularity (number of page views), that number ticks up a bit higher.
HTTPS adoption varies by agency. Some, like the EPA (Environmental Protection Agency) and Social Security Administration, are already at 100% HTTPS use across their sites. Others are still at 0% – come on Advisory Council on Historic Preservation!
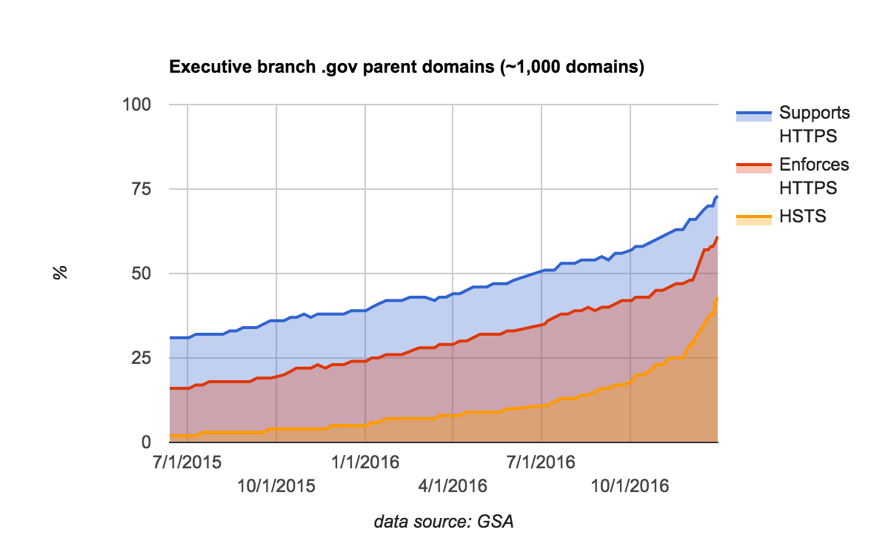
You may find this interesting: there is no complete list of .gov sites. That made collecting this data a bit more difficult. But by using a combination of official government lists and tools, and academic resources like Censys.io, 18F was able to put together a list of 1,000 .gov parent domains and 26,000 subdomains.
Not only are federal websites using HTTPS, they are also using advanced security mechanisms. The mandate requires the use of HSTS (HTTP Strict Transport Security), a technical mechanism that prevents clients from browsing the site over HTTP, so that you cannot accidentally browse insecurely. HSTS also blocks a class of attacks against HTTPS that rely on “down-grading” you to HTTP, and prevent users from ignoring certificate errors.
For those who are curious, you can explore HTTPS use on .gov sites in depth at pulse.cio.gov.
Mr. Mill concludes the post with some thoughts on the effectiveness of the formal HTTPS mandate:
“The sharp uptick in December (especially for HSTS) shows that the government, like many things made of humans, needs a deadline to get things done. The HTTPS policy provided that deadline, along with enthusiastic assistance from GSA and DHS during the implementation process. That assistance will remain as agencies continue to close gaps over 2017, and work to eliminate remaining insecure connections their services make to federal staff, citizens, and the rest of the US government’s many users.”
A firm deadline is something that the commercial SSL industry has a lot of experience with. Over the last few years we have hit various deadlines dealing with phasing out the now-insecure SHA-1 hashing algorithm. As each deadline approached, a huge proportion of websites and services migrated away in the final days.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown