No, It’s Not Okay To Ignore Certificate Warnings
UK Government website tells users to ignore security warning.
I came across some troubling security advice today, and I wanted to set the record straight: No, you should not ignore certificate warnings in your browser, and no, it is not “safe to continue” past these warnings.
This troubling advice came from Maidstone.gov.uk, the website for the Borough of Maidstone, a district in Kent, England.
Their SSL certificate expired earlier this week, and instead of acquiring and installing a new certificate (which is a basic, routine part of maintaining a website), they published a notice across the top of their page, reading “If you get a message saying our security certificate has expired when using our forms, it’s still safe to continue.”
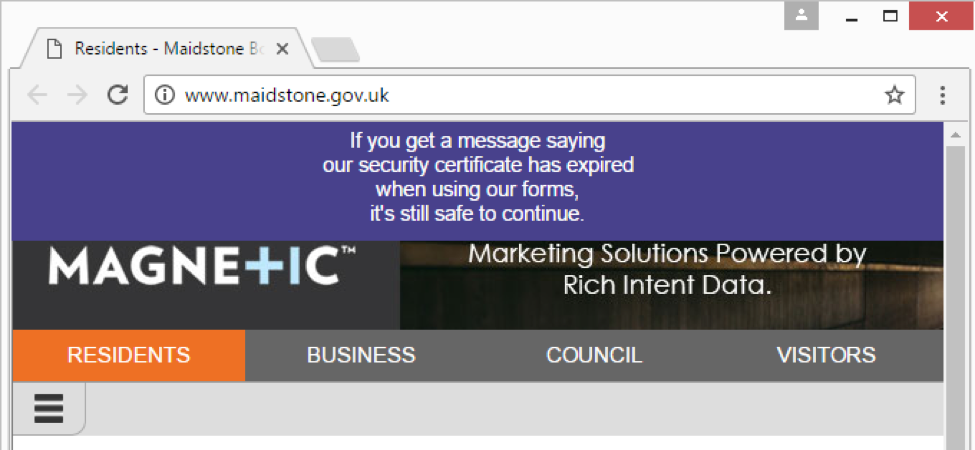
When an SSL certificate expires, they are no longer safe to use, and web browsers display a full-page interstitial warning when they encounter expired certificates.
Now, certificate expiration happens all the time, and we don’t fault people for that. But encouraging users to ignore warnings? That is downright irresponsible.
First, SSL certificates have an expiration date for a reason. When a Certificate Authority (CA) issues a certificate to a website, it required that the website proved its identity, so to prevent people from getting a certificate for a website they don’t own. The expiration period exists to make sure a website regularly provides this proof, for the same reasons that any important form of ID expires.
Once a certificate expires, a CA is saying that they can no longer attest to the website’s identity. They also stop supporting it, so important factors like revocation status are no longer published. We previously gave an in-depth explanation why SSL certificates expire.
But the bigger problem is that MaidStone is teaching users that warnings don’t matter. Someone who reads this advice from Maidstone and clicks through their browser’s warning is going to internalize that advice.
The average user is not going to be able to distinguish between, or make an educated decision about, the various SSL errors they come across. Is it an expired cert that poses relatively little risk? Is it a revoked certificate that has been compromised? Is it a phishing site?
We don’t need to just focus on website security. Many ransomware strains and other malware will use social engineering to trick users into turning security measures off. Some malware distributes itself via macros embedded in Word documents. As Microsoft has tried to counter this problem, malware authors have learned clever tricks, like inserting an image that mimics the Word UI, instructing the user to enable macros to enable “special formatting” or “proper display” of the file.
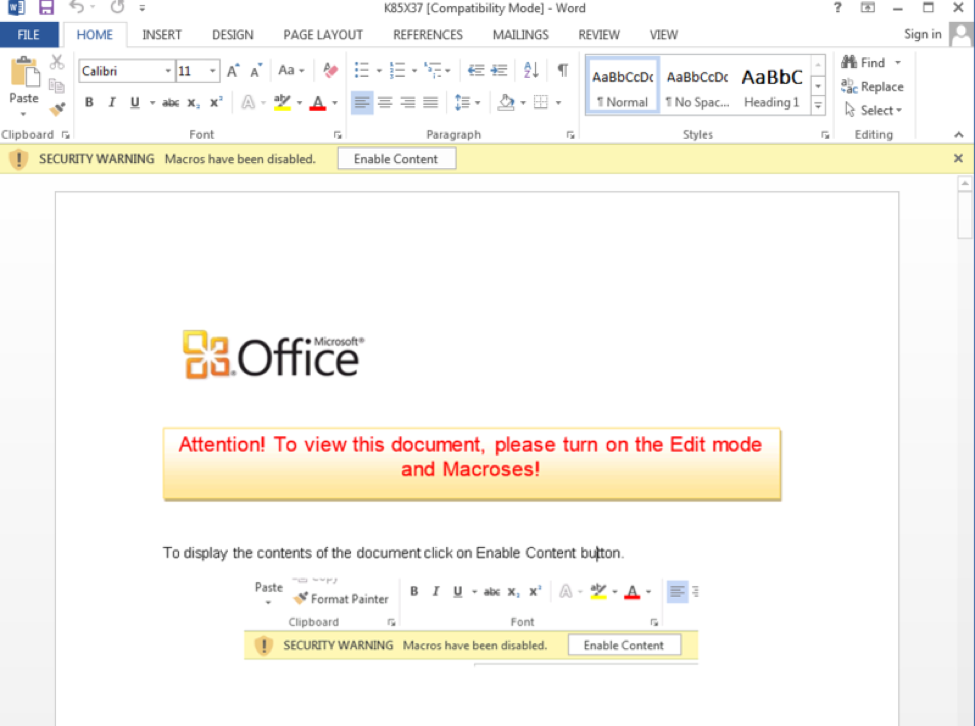
Individual websites cannot act in their own interest at the cost of security as a whole. Everyone needs to be encouraging good security hygiene by abiding by standard procedures, and not encouraging their users to circumvent legitimate security measures.
Every time a legitimate website tells a user to ignore security precautions, it aides malicious actors trying to trick them.
Someone from Maidstone’s team was clearly around to publish that notice on their site, but they could not be bothered to get a new certificate? An experienced server administrator should be able to get a new certificate installed in under an hour – and SSL providers like us offer 24/7 support because we know everyone isn’t an SSL expert.
So consider how much care Maidstone.gov.uk has for their users when they can’t take an hour to acquire a new SSL certificate, and think about who might get phished, scammed, or otherwise harmed by applying Maidstone’s bad security advice elsewhere.




































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown