Report: 32% of Top US Companies Receive an F in SSL/TLS
The report by High-Tech Bridge also turned up an alarming number of expired SSL/TLS certificates
A new report by High-Tech Bridge, released Wednesday, makes some troubling findings about the state of SSL/TLS and encryption across 1,000 of the world’s top companies. Among the key findings:
- 32% of US companies and 16% of European companies received failing grades for their SSL/TLS implementations.
- Only around 15% of the companies had an SSL/TLS configuration that was compliant with current PCI DSS requirements.
- 45% of US companies and 30% of European companies have at least one invalid SSL/TLS certificate.
- Only around 84% of companies are compliant with Article 32 of the GDPR.
There’s a lot to unpack from this report, some of it is quality information while other parts may be a little less reliable because of some questionable methodology. We’ll have to parse it to see what’s what.
Let’s hash it out…
A Quick Word About Methodology
Let’s start at the top. Applicable though the quote may be, I’m not sure starting any kind of report by paying homage to the “wisdom” of Donald Rumsfeld – the former US Secretary of Defense who gained infamy for overseeing America’s use of “enhanced interrogation techniques,” (a less charitable term would be torture, which is a war crime) following the invasions of Afghanistan and Iraq – is really appropriate.
 But hey, you do you, High-Tech Bridge.
But hey, you do you, High-Tech Bridge.
As far as the methodology behind the report, there are a couple of things that we need to consider up front because they do bear an influence over some of the findings. High-Tech Bridge used the Financial Times top 500 lists for the United States and Europe, scanning those 1,000 companies. Now come the declarations:
- High-Tech Bridge sells a suite of scanner software called ImmuniWeb.
- High-Tech Bridge uses its own grading system as opposed to a more neutral third-party one like SSL Labs.
Now, neither of these things is disqualifying, but it does represent a conflict of interest that is worth keeping in the back of your mind. The report also makes use of several terms that are worth defining as they can help inform some of the data we’re going to look at in a moment:
- Shadow IT – This refers to assets that are created organizationally and serve a legitimate purpose, but were built or implemented without proper coordination with other parties. This is a term that we’re very familiar with at The SSL Store given the fact that SSL certificates are among the most common Shadow IT assets. A company is building a new website, the dev team slaps an SSL certificate on it without coordinating with IT and the Security team, then when it expires in a year or two, things break and they call us. Happens all the time.
- Legacy IT – This refers to assets that were either built or procured a long time ago and can no longer be properly maintained. This is another area we deal with a lot, a lot of organizations, particularly in healthcare, use older devices – some of which have even had their vendor support deprecated – that can’t use modern encryption protocols or SHA-2.
- Abandoned IT – This one is the most self-explanatory. These are legitimate websites and applications that have just been abandoned or forgotten. A great example of this would be brendanfraser.com, the website for actor Brendan Fraser that clearly hasn’t been updated since at least 2005 and requires Flash 7 (we’re in the 30s now) to run properly. (And don’t act like you didn’t just click and slurp up some of that old Geocities-flavored early-internet nostalgia.)
Now let’s delve into the study a little bit.
What Is an External Web Application?
Let’s start out by defining what a web application is. I realize the vast majority of you are already well-versed on this, but not everyone is. And Web application is one of those terms that kind of has a hazy definition. It’s defined different ways by different companies and organizations, so my definition may be a little bit different than other companies’. Generally though, a website is a set of documents or pages that are hyperlinked together. A web application is more like a program, it typically serves a particular function or action.
That can seem a little abstract so let’s use some examples. Let’s look at our website. The website itself is a collection of pages that are hyperlinked together. But on those pages are web applications that allow you to search for content, put items in your shopping cart or interact with the user control panel.
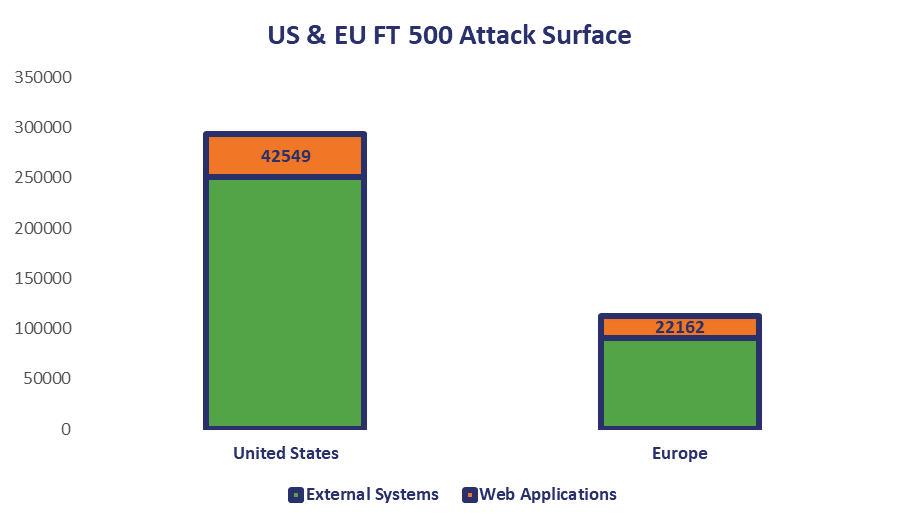
So how prevalent are web applications? When High-Tech Bridge scanned the US and European FT 500, it found 293,512 external systems that were accessible from the internet, 42,549 of which were live web applications. Europe has less than half that, with an attack surface of 112,750 external systems, of which 22,162 are web applications.
High-Tech Bridge found that each US company had an average of 85.1 web applications that are accessible by the internet and that aren’t protected by:
2FA, strong authentication or other security controls aimed to reduce application accessibility to untrusted parties…
That number was 44.3 for European companies.
Now, that’s a staggering figure and it probably needs to be laid out with a little bit more context. Without the raw data it’s hard to really piece together an accurate picture. Kind of like trying to discern the real value of an NFL contract.
While HTB only counted unique, live web applications – disregarding redirects, default installation pages and HTTP errors – it doesn’t seem as though it did anything else to categorize those web apps. Not every single web app needs to be secured the same way and it’s unclear how the study adjusted for a lot of these different variables.
Let’s move on to the areas that are a little more germane to our area of focus…
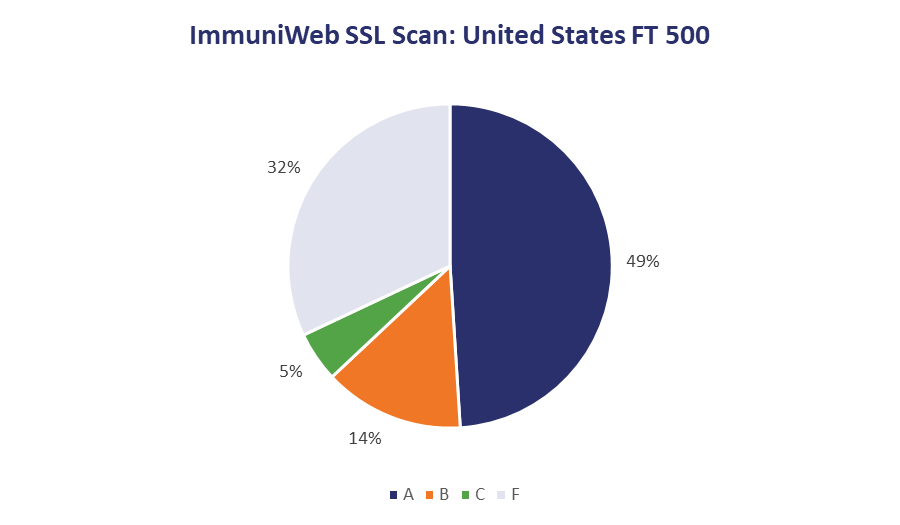
32% of US Companies Receive a Failing Grade For Their SSL/TLS Implementations
This is a very eye-catching statistic, and it certainly points to the need for more companies to understand SSL/TLS and PKI so that they can make better decisions about their configurations and implementations, but as we discussed earlier, High-Tech Bridge is operating on its own grading rubric.
Again, there’s nothing wrong with this. This is the grading system that its ImmuniWeb SSLScan uses, and for what it’s worth it can be used to check for PCI DSS and HIPAA compliance and a whole range of other good things, but, it comes with a few caveats. The obvious comparison is Qualys’ SSL Labs. That has a grading scale with clearly defined meanings:![]()
A+ – exceptional configuration
A – strong commercial security
B – adequate security with modern clients, with older and potentially obsolete crypto used with older clients; potentially smaller configuration problems
C – obsolete configuration, uses obsolete crypto with modern clients; potentially bigger configuration problems
D – configuration with security issues that are typically difficult or unlikely to be exploited, but can and should be addressed
E – unused
F – exploitable and/or patchable problems, misconfigured server, insecure protocols, etc
That same information isn’t provided by HTB. There is also no D on the grading scale. As a proud former straight-D student this offends my sensibilities.
Jokes aside, there are also a couple of questionable bonuses, specifically. The first is for Extended Validation. EV is absolutely the best way to assert identity on a website, but in terms of the improvement to security it provides—that’s contingent upon the additional trust asserting identity can provide. EV SSL doesn’t provide encryption that’s any stronger than OV or DV SSL. So you be the judge of whether or not that’s worth ten points. Also, TLS_Fallback_SCSV was designed to prevent Man-in-the-Middle attacks when negotiating what TLS version to use, but now that best practice is to deprecate support for SSL 3.0 and TLS 1.0, SSL Labs is thinking about removing it from its criteria entirely, so a 10 point bonus for supporting it seems a little bit questionable, too.
Basically, if a company had an up-to-date configuration its server received an A while companies with bad configurations got hit with multiple penalties (many of them redundant) and ended up with a big F.
Let’s compare that with the figures produced by Qualys’ SSL pulse, using data from its SSL Labs scans of the Alexa most popular lists.
Granted, this isn’t a 1:1 comparison, but it still gives you a rough idea of how the two vary.
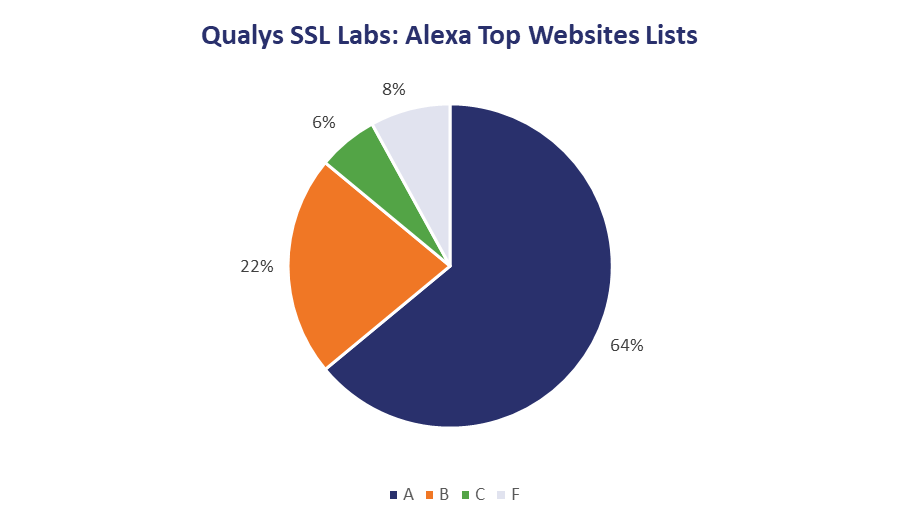
SSL Labs really does have a D grade, it’s just apparently really difficult to achieve—to the point where the percentage of websites that received it is negligible and I haven’t included it in the graph (this also offended my D-student sensibilities).
The real takeaway from these scans is the fact that 7.82% of the US companies scanned and 5.15% of the European ones still have support for SSL 3.0 enabled. That’s pretty inexcusable and should have been handled four years ago.
Also of note, 35.2% of US companies and 24% of European companies have at least two servers with an exploitable SSL/TLS vulnerability.
The Last PCI DSS Deadline Maybe Didn’t Go So Well…
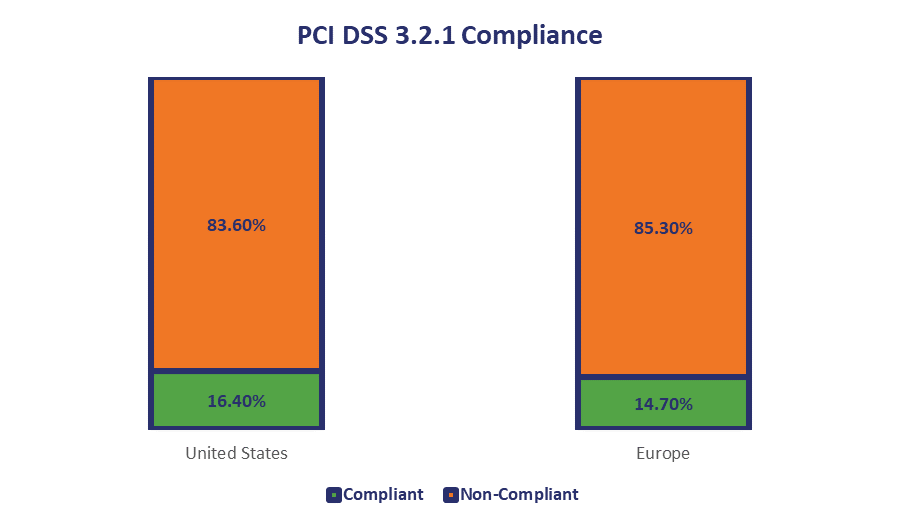
One of the other interesting findings from High-Tech Bridge’s report was the number of companies that still haven’t fully complied with the latest PCI DSS deadline to remove support for TLS 1.0. It was also advised that TLS 1.1 be deprecated as well, though that wasn’t mandatory.
The scans found that just 16.4% of US companies and just 14.7% of European companies had server configurations that were compliant with requirements 2.3 and 4.1 of the most recent PCI DSS regulations.
2.3 requires companies to secure their administrative access points and 4.1 requires them to encrypt Payment Card Information as it’s being transmitted. Pretty much all of this was a result of companies not deprecating TLS 1.0 support yet.
GDPR Compliance – Another Thing That Doesn’t Seem to be Going Well…
The GDPR headaches have only just begun. We’ve written about it ad nauseum, everything from best practices to how to train your support staff—we’ve covered it. Recently we reported that the European Privacy chief, who helps oversee and coordinate the various Data Protection Agencies in the EU, said penalties will be incoming by the end of the year.
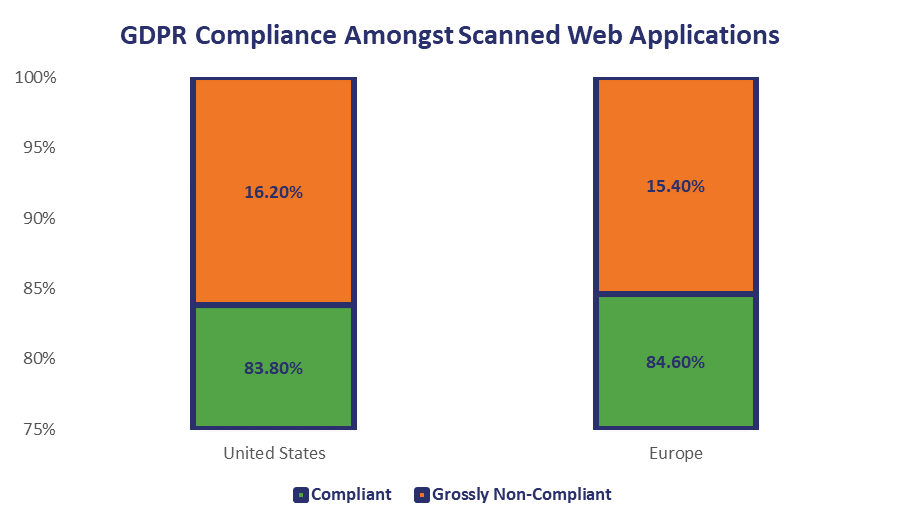
They DPAs are going to be busy, too. At least if the HTB report is any indication. 16.2% of US companies have at least two active web applications that process personal data and are either running outdated SSL/TLS implementations or have an unpatched vulnerability in their CMS. 15.4% of European companies can say the same.
This is a violation of Article 32 of the GDPR, which outlines the appropriate technical safeguards.
The report also added:
Numbers of non-compliant web applications may likely be much higher, but it is impossible to say how many of the outdated and vulnerable websites actually process or store PII without conducting intrusive tests.
Trusted SSL Certificate Usage
This is the part of the study where I have some legitimate questions about methodology and part of the problem is the way that the information is being presented.
The US companies have 45.1% invalid SSL certificates because of untrusted Certificate Authority (CA), expiration or issuance for a different domain name. Untrusted CAs include the distrusted Symantec KPI [sic] legacy certificates. The European companies come out with much better results of “just” 28.9% invalid certificates.
A few things, first off this is not attributable to the Symantec distrust. DigiCert has pretty much gotten that handled, when Mozilla pushed back its deadline earlier this month the number of websites in the Alexa Top 10,000 with an ill-fated Symantec certificate installed was less than 1%.
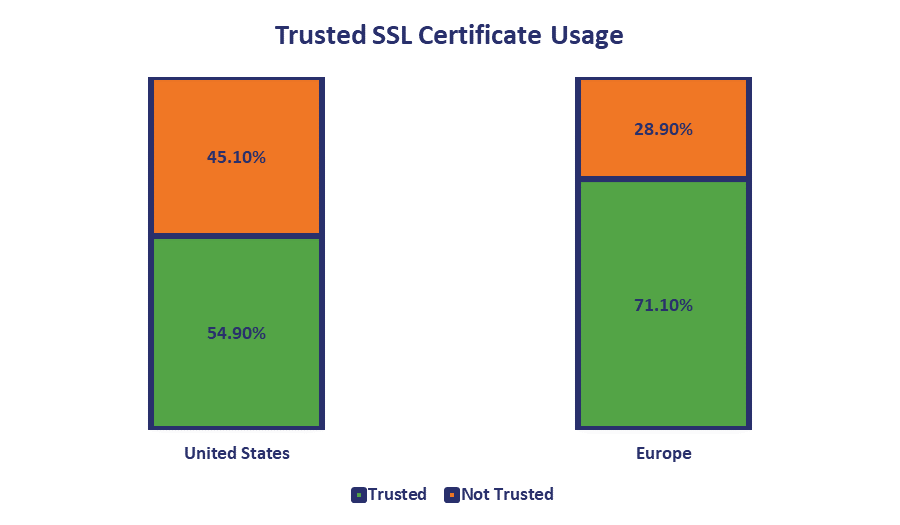
Personally, I think what was meant – though poorly communicated – is that this refers to the number of companies that have at least one expired, distrusted or improperly installed SSL certificate. That would go back to the three categories of unknown IT assets – Shadow IT, Legacy IT and Abandoned IT – that we discussed at the outset of the article.
RELATED: What is a Rogue Certificate?
As I mentioned then, that’s actually a very regular issue we deal with here. SSL certificates are one of the most frequent Shadow IT purchases, and on abandoned or forgotten websites and IPs, it only makes sense that there would be expired certificates or distrusted certificates. Frankly, the existence of those sites and the obvious fact that they would likely have outdated configurations and expired certificate is something that would have influenced the astronomical figures the study produced.
Again, without the raw data there’s no way to know how much, but Ilia Kolochenko, High-Tech Bridge’s CEO and Founder contends that’s partly the point.
“The research has clearly demonstrated that abandoned and unmaintained applications are a plague of today. Large organizations have so many intertwined websites, web services and mobile apps that they often forget about a considerable part of them. Legacy applications, personnel turnover, lack of resources, outsourcing and offshoring exacerbate the situation.”
What Conclusions Can We Draw From This?
If it seems like I’ve been overly critical at points, that was never my intention. I’ve only attempted to provide an objective analysis of the report that was released. There’s a lot of very good information in this study, including a few major takeaways:
- Lack of visibility is a major problem, especially for Enterprises. We talk about that all time time from a certificate management standpoint, but it applies to almost every cybersecurity context. It’s not the parts of your digital infrastructure that are frequently used and well-maintained that are the biggest threats, a lot of times it’s the older stuff that you may have discontinued but didn’t properly shut down. And all it takes is a tiny opening for a cybercriminal to exploit it and cause you major problems.
- You need to have a strategy for assimilating Shadow IT assets into your larger organizational security apparatus when they are discovered. It’s almost impossible to completely stamp out Shadow IT issues, as your company grows it gets harder and harder to coordinate, so instead treat it like an inevitability and figure out what needs to be done to gain visibility over Shadow IT assets and inform stakeholders to take appropriate action.
- Finally, keep a critical eye when you’re reading research like this. While a lot of this information is very good and extremely useful, don’t get too hung up on the figures and statistics. Let them give you a rough idea, but remember that numbers can be manipulated and teased to create the intended effect. And without raw data you can never know how much.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown