SAN Exchange 2010 SSL Certificates & Key Elements of SAN SSL
Subject Alternative Name (SAN) lets you secure multiple host names under just one certificate. Subject Alternative Name extension has been part of X509 certificate standard since before the year 1999. But it became popular only recently after its application in Microsoft Exchange 2007 which use these certificates to simplify server configuration.
Key Elements of SAN SSL Certificate:
Certificates that use Subject Alternative Name SSL Certificates are strong ssl certificates to secure multiple domain names inexpensively and efficiently. They are capable of securing up to 25 fully qualified domain names with a single SAN certificate. They are also known as Unified Communication Certificates (UCC) and are commonly used with Microsoft Exchange Server 2007 & 2010 & Microsoft Communications Server.
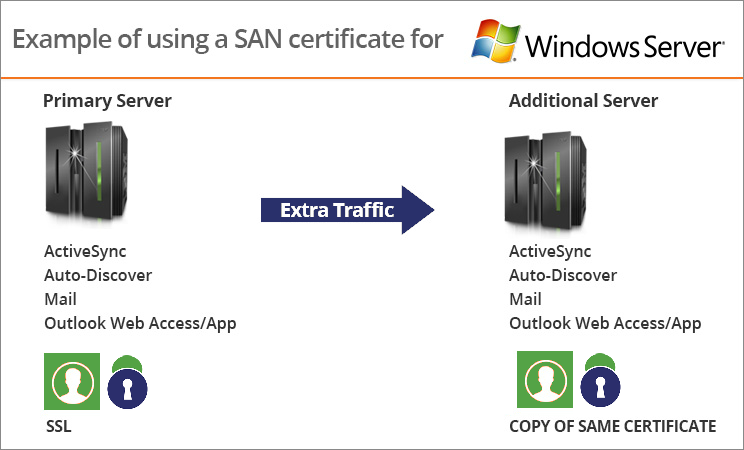
Their purpose is similar to that of any other SSL certificate. It helps establish server’s identity and sets up secure communication. SAN certificates also provide a subject alternative name field that allows additional domain names to be protected with just one certificate.
Understanding SAN Exchange 2010 SSL Certificate:
Usually one SSL certificate secures just one domain name or URL, but this is limiting because once an SSL is bound to an IP address, that IP address can’t accept connections addressed to various names over SSL. At least not without the name mismatch which generates a warning message to the connecting client.
This became a problematic issue for Exchange Server 2007 & 2010 because depending upon the server roles installed, the server may require accepting SSL connections to other names, like:
- Server’s Fully Qualified Domain Name (Eg. Exchangeeserverprone.net
- Webmail etc (Eg. Webmail.exchangeserverpro.net, mail.exchangeserverpro.net etc)
- Multiple DNS (Domain Name Systems) namespaces.
Now, configuring all the multiple IP addresses, DNS Records and SSL certificates for all of the possible names in an Exchange organization becomes very costly and tedious. X.509 has provided a simple solution to this situation in form of Subject Alternative Names. This is the most convenient option to secure multiple domain names on a web server with a single SSL certificate.
Unlike Wildcard SSL certificates, SAN certificates provide secured communications on multiple fully qualified domain names (FQDNs), IP addresses, private host names etc. They save a lot on time and money and instantly reduce the complexity in server security administration. They are highly recommended by Microsoft since 1999 especially for Microsoft Exchange Server 2007, 2010 & 2013, Office Communications Server 2007 & 2010. SAN certificates also support Microsoft Exchange Autodiscover service.
SAN SSL Exchange 2010 is much simpler, as MS Exchange 2010 server automatically encrypts the communication with SSL for MS Office Outlook Web App, Exchange ActiveSync & Outlook Anywhere. Out of all the SSL certificates, SAN SSL certificate is a perfect choice to secure multiple domains and sub-domains in this Exchange server.
Why Microsoft Exchange Server needs a SAN SSL?
The basic reason is to encrypt the private and confidential information being transferred within MS Exchange Server with a least complex and economical approach. Let’s take a look at a few services and applications by MS Office that are highly in require data security:
- ActiveSync: This is a Mobile Data Synchronizing technology designed by Microsoft. Safeguarding this is very important as there is a lot of important information that gets relayed to wireless devices such as iPads, Mobile Phone Devices etc.
- Outlook Web Access: If security is compromised here, a lot of sensitive information in the e-mails, contacts etc can get stolen.
- Auto Discover: A security breach here can cost many critical usernames and passwords.
- Mailboxes: E-mails need to be encrypted on its way to and from server so that they are not read by the attacker.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)











5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown