SAN/UCC SSL Certificates Will Not Work for Internal Domain Names after November 1, 2015
Are you shocked after reading the headline? Yes, it is true that ALL (SAN/UCC) SSL Certificates will not work for internal server domain names from 1st November, 2015.

As per the CA/Browser Forum (CA/B), the regulatory body that governs the SSL industry, one of the new changes is the elimination of certificates for internal names. This change makes it impossible to obtain a publicly trusted certificate for any host name that cannot be externally verified as owned by the organization that is requesting the certificate after 2015.
This does not mean you can no longer use SSL certificates for internal use. Internal websites and networks simply need to transition to using delegated domain names or registered IP addresses. For instance, “mynetwork.internal” cannot be reliable verified to be owned by only one company or party. Therefore it is a security risk to have multiple certificates issued out to that same domain. If your internal network is on a similar internal name, it just needs to be transitioned to a registered domain name, such as “mynetwork.com”. That domain does not need to resolve in the public DNS, or go to a publically available page.
The CA/B forums new requirements also disallow internal domain names in the Subject Alternative Name (SAN) extension. If Certificate applications do include a disallowed domain, often times the CA can automatically reject the order or notify the applicant that the use of internal name has been depreciated.
So to summarize, Certificate Authorities shall not issue a certificate with an expiry date later than 1 November 2015. Certificates with validity periods past that date may also be forced to lose their internal names they next time they reissue.
Here is some quick FAQ Answers for Your Basic Questions:
What is SAN/UCC SSL Certificate?
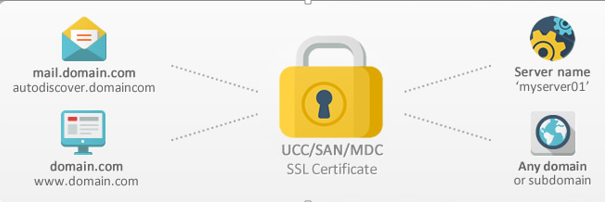
SSL Certificates that you can and can’t use to secure your internal domain names or Internal Server Names likes:
No longer allowed:
- mycompany.internal
- mycompany.priv
- mail.mynetwork.server
- 192.168.1.1
Use these instead:
- www.mycompany.com
- mycompany.com
- www.mycompany.net
- mail.mycompany.com
What Is Internal Server Name?
An internal name is a domain or IP address that not actually registered. Common examples of internal names are:
- Any server name with a non-public domain name suffix. For example, www.company.local or server1.company.internal.
- NetBIOS names or short hostnames, anything without a public domain. For example, Web1, ExchCAS1, or Frodo.
- Any IPv4 address in the RFC 1918 range.
- Any IPv6 address in the RFC 4193 range.
What You Need to Do?
If you have multi server names and want to secure them with trusted SSL Certificates then you need to reconfigure all those servers to use a public name. Some exceptions can be made if you need more time to transition, for these cases please contact us directly. All internal connections that require a publicly-trusted certificate must be done through names that are publically delegated and verifiable (it does not matter if those services are publicly accessible).
How to Redirect Internal Names to use a Registered Domain Names?
If you are using a single SSL Certificate to secure your internal domain names for your Exchanges Server for your internal communication then you will need to make all the internal domain names to public domain names to use SSL Certificates.
To reconfigure your domain to use only the external domain name you have a couple of options. If you are using Active Directory you can migrate an internal Active Directory domain to a registered External name. This will change the internal FQDN of your Exchange Servers so they will reroute to a valid subdomain of your registered external domain(e.g. change from Server01.yourcompany.internal to Server01.yourcompany.com) allowing you to use a SAN certificate or UCC Certificate to secure these names.
Alternatively, you can redirect the internal names to use the external mail URL, but this method will not allow access to mail using the Outlook Anywhere service so users connecting over a VPN would have connection problems.
Redirecting your Exchange Server to use the External DNS Name
To update your Exchange 2007 or Exchange 2010 server you will need to run the following commands from the Exchange Management Shell and replace the Server running the Client Access Role with your external domain name. These commands update the URL for the Auto discover service, Exchange Web Services (EWS) and the OWA Web-based Offline Address book respectively.
Before running these commands you will just need to check make sure a DNS record exists mapping the IP Address to the Exchange Client Access (CAS) server.
Note: Each of these commands below should be run on a single line in the Exchange Management Shell (EMS):
- Set-ClientAccessServer -Identity HostName -AutodiscoverServiceInternalUri
- Set-ClientAccessServer -Identity HostName -AutodiscoverServiceInternalUri https://mail.yourdomain.com/autodiscover/autodiscover.xml
- Set-WebServicesVirtualDirectory -Identity “HostNameEWS (Default Web Site)” -InternalUrl https://mail.yourdomain.com/ews/exchange.asmx
- Set-OABVirtualDirectory -Identity “HostNameoab (Default Web Site)” -InternalUrl https://mail.yourdomain.com/oab
Recycle the IIS Application Pools
Next to make these commands take effect you have to tell IIS to push these changes by recycling the application pools.
- Open IIS Manager by clicking Start, then enter inetmgr.
- Expand the server and expand Application Pools, then right-click on MSExchangeAutodiscoverAppPool, and select Recycle
The Last Word:
Please Contact Our SSL Experts to “Resolve” your SAN/ UCC SSL Certificate issue





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)











5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown