Everyone Has Server Name Indication (SNI)
New Figures Show Wide Support for Feature Allowing HTTPS On Virtual Hosts.
New data from Akamai confirms that Server Name Indication (SNI) is widely deployed and can be used in an HTTPS deployment without excluding devices.
SNI is a feature of the SSL Handshake that was added as an extension in 2003. Server Name Indication allows the connecting client to specify the hostname to the server. This means a server can use virtual hosting to serve multiple HTTPS sites from one shared IP addresses, and know which certificate to provide.
This makes deployment of HTTPS easier and cheaper, and is especially important for IPv4 services who don’t have addresses to spare.
However there was always a concern that relying on Server Name Indication meant losing some of your audience. While all modern clients have supported SNI for quite a while, its late addition to the protocol meant that some older operating system Any clients who didn’t support SNI would be given the wrong certificate by the server, which effectively breaks HTTPS.
Akamai is finally putting that fear to rest by sharing that, on average, 98% of client HTTPS requests over their network support SNI. This is for global traffic and is essentially universal support. They note that China is the exception, and has significantly lower SNI usage but did not specify how far behind the country was.
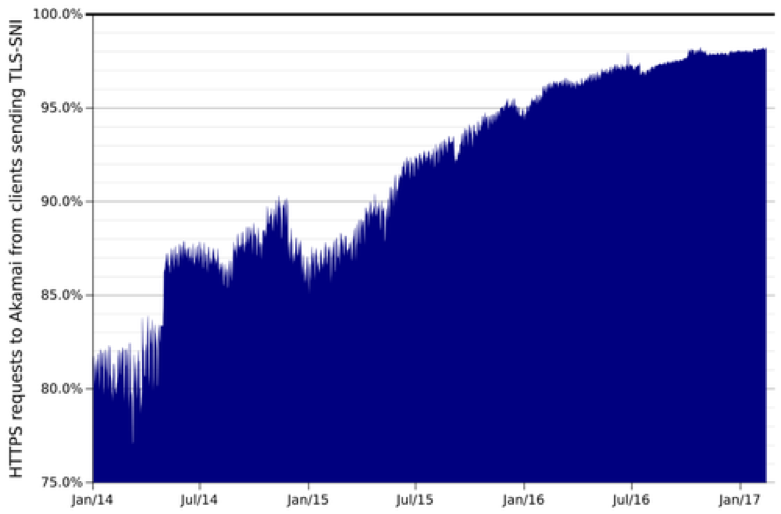
In the last three years, the gap for SNI support has closed. Image courtesy of Akamai.
So, what’s the missing 2%?
Overall, the most notable clients that lack Server Name Indication support are Internet Explorer 8 (and earlier) on Windows XP, and Android 2.3.
The Android developer page reports that only 1% of devices connecting to the Google Play Store are on Android 2.3.
Windows XP has a reputation for refusing to die. But according to analytics.usa.gov, which aggregates data from a few thousand US government sites, less than 1% of visitors are still using Windows XP. This is probably an accurate measure for American internet users.
But the rest of the world probably isn’t visiting these sites, so we need a metric that more accurately reflects them. We like Wikimedia’s user agent dashboard. According to them, just 1.7% of visitors are hanging onto XP.
Now that the internet has moved to SHA-2 signatures for SSL certificates, that also eliminates users who are using Internet Explorer on XP SP2 or earlier. You also have to consider the likelihood that someone on a decade-old OS is part of the potential audience for your site.
Akami notes that TLS proxies performing traffic interception, and bots and search engine crawlers are also a notable portion of the non-SNI clients.
Akamai’s blog post provides more background for those interested in the history of SNI.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown