33% of top WordPress sites are at least two versions behind
We crawled the Quantcast top 10,000, a lot of websites need critical updates
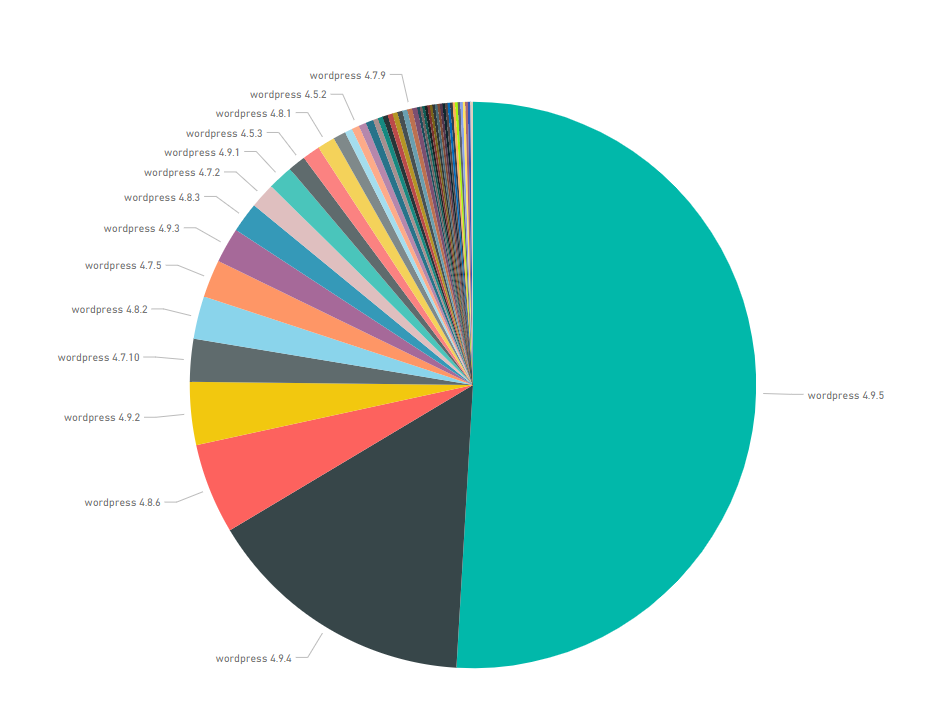
Following WordPress’ recent update to version 4.9.5, we decided to do a little bit of research to see just how quickly WordPress websites were updating—and how many were multiple updates behind. What we found was disconcerting to say the least. 49% of WordPress sites in the Quantcast Top 10,000 are not running the latest, most secure version of WordPress. And 33% are multiple updates behind.
“WordPress is the number one platform globally used to build websites,” says Adam Cohen, a web developer and security expert with over 15 years of experience. “With the count of the number of websites being run off WordPress in the millions, it’s also the most common platform for hackers to attack against. Because if they find any exploits, it can be replicated on hundreds of thousands of sites.”
That makes the fact that many websites are not keeping up to date with new releases a huge concern. These sites are playing fast and loose with known vulnerabilities. This is how you get hacked.
Methodology and Key Findings
To perform our survey, we created a tool to crawl the homepages of every website in the Quantcast Top 10,000. The crawl was performed on April 5th, 2018—two days after the release of WordPress 4.9.5. With 48 hours since the official release, any site configured to update automatically would have already done so.
Of the Quantcast top 10,000, 17% of website homepages were running on WordPress. The total number of sites that may use WordPress for their blogs or on other portions of their sites it obviously much higher, but owing to the complexity and time-consuming nature of such a scan, we opted to stay with just the homepages.
Here are our key findings:
- 17% of websites in the Quantcast Top 10,000 run primarily on WordPress
- 50.93% of those WordPress websites are running the latest, most secure version
- 49.07% of WordPress websites are not running the latest version
- 33.58% of WordPress websites are at least two updates behind
Not Updating WordPress is a great way to get hacked
Let’s talk about why this is so crucial. And before we go any further, understand that this a universal problem. Organizations are constantly weighing the need to patch, update and harden their systems with the costs associated, both in terms of price, and downtime/interruptions to business. That’s not just limited to WordPress sites, either.
“Many people forego WordPress updates because they are worried that they will impact the stability of the site,” says Paul Bischoff, a security expert and privacy advocate for Comparitech.com. “WordPress plugins can stop working, for example. If you made changes to a theme but didn’t put those changes into a child theme, those changes might get wiped in the next update. If you’re running an online business of some sort, the prospect of downtime can seem more costly than the risk of malware or attack.”
Senior web developer and WordPress expert Ken Dawes is quick to warn site owners that WordPress needs constant attention.
“The biggest problem in WordPress security (or any other kind of site) is getting people to realize that having a WP website is like having a puppy,” says Dawes. “If you don’t take care of it – feeding, grooming, vaccinations and the like – You’re going to have problems.”
Taking care of it means regularly updating to the latest version and keeping your plugins up to date, too.
WordPress is making these updates for a reason
Just like pretty much any other software, WordPress releases updates on a regular basis. While these updates also provide new features, it’s the security improvements that are critical. And cybercriminals are paying attention to what gets fixed.
“People don’t realize that hackers often don’t find vulnerabilities in software all on their own,” says Bischoff. “When a software publisher like WordPress puts out a patch that includes a security update, it tips off hackers to the fact that a vulnerability will exist on any WordPress installation that didn’t perform said update. If you don’t update, you’re a target. The longer you wait, the more vulnerable you are.”
That nearly half of the WordPress sites in the Quantcast Top 10,000 aren’t on the most recent update is alarming. The fact that over one-third, 33.58% are multiple versions behind is outright dangerous.
“Once your website is hacked it’s very difficult to repair. Essentially, hackers who get in to your website will create new hidden entry points and unless you close them all, it’s easy for them find a way back in. The results are horrible for the business,” says Mazdak Mohammadi, head of Canadian WordPress Design Studio, BlueBerryCloud.
“The good news is that WordPress makes it very easy to update the installation along with plugins through the WordPress Admin dashboard. Your web developer should be able to do this for you, otherwise you can ask for access and figure it out yourself. It’s not rocket science and also, should the update fail, WordPress automatically takes your website to back to the point in time before you started the update.”
WordPress hacks can happen to ANYONE
Small and medium-sized businesses are not immune to being hacked. That’s a common misconception that is not backed up by statistics. In fact, Symantec’s 2017 Threat Report says that 74% of SMBs were targeted last year. And the National Cyber Security Alliance reports that 60% of SMBs go out of business within six months of a data breach.

“Anecdotally, you’ll find website owners who say, “I haven’t updated anything in years and I haven’t gotten hacked! So what’s the big deal?” or… “I’m just a little guy, they won’t bother with my site,” says Dawes. “It’s a game of numbers. All sites get attacked randomly every day by hack-bots. The bots just go through lists of IP addresses and attack using lists of known, exploitable vulnerabilities. All a company needs is for their site to be vulnerable to the right bot at the wrong time.”
“When a vulnerability is found in a version of WordPress, hackers will create an exploit for that vulnerability and then cast a wide net, usually in an automated fashion, looking to see who is not up to date,” adds Greg Kelley, an EnCE and DFCP with Vestige Digital Investigations. “Realize the importance of a “wide net”, they don’t care who you are or what you do, just that you have a site. Once compromised, the hacker will then see what they can get from their site such as account information and then maybe try to use that information to attack other systems that you may have. At the very least, the hacker will trash your site or use it to store data of importance to them (stolen data, illegal pictures, etc.). The result, at the very least, is a bad public image when it is discovered that your site was compromised.”
Or, you could go the way of nearly 60% of the SMBs that get attacked and end up going under.
What you need to do to keep your WordPress site safe
Obviously, the biggest piece of advice you can take away from here is that you need to stay on top of your WordPress updates, both for the CMS itself and for the plugins you’re running with it.
“When plugin and theme vulnerabilities are discovered and remedies released, your dashboard will indicate an update is available,” says Bob Herman, the co-founder and President of IT Tropolis. “Also, always use child themes so that you can update all themes in your installation without affecting your site. Wordfence is a great plugin to notify you of important issues in your installation. And, if you don’t want to update WordPress because a plugin may not be compatible with the latest version, then it’s probably not a plugin worth using. Most widely adopted plugins are updated in sync with WordPress so that vulnerabilities can be patched as fast as possible.”
Cohen has some additional advice, too:
“Make sure you regularly update your passwords and make sure your hosting company is updating Linux/Unix, Php, and MySQL libraries annually (and installing patches as needed). Delete old plugins or themes when not in use or when they’re outdated. Install a service like Sucuri or Wordfence for monitoring files and access of your site.”
But above all else, if you only take one thing from this article, don’t fall into the trap of thinking that you don’t need to stay on top of updates.
“It’s a false economy to *not* keep everything up to date,” says Dawes. “If a company doesn’t want to make updates because they are afraid that their site will break, then they need to be cognizant of the increased risk of their site becoming compromised and be willing to accept those risks that their site will be hacked. And if the company’s site contains personal information about website visitors – names, email addresses, credit card info, etc. – They better be very accepting of their legal liabilities!”
As always, leave any comments or questions below!





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown