5 Actionable Takeaways from Ponemon and Keyfactor’s 2020 PKI Study
Looking for the latest stats and info about public key infrastructure? Look no further
74%. That’s how many organizations report not knowing how many keys and certificates they have. This unsettling statistic was reported in the latest data from “The Impact of Unsecured Digital Identities,” a new public key infrastructure (PKI)-focused research study by the Ponemon Institute and Keyfactor
Last year, Keyfactor and the Ponemon Institute joined forces to publish a study on public key infrastructure. This year’s publication is chock full of goodies and valuable insights on PKI as a whole. In early March, Chris Hickman, chief security officer at Keyfactor, and Larry Ponemon, chairman and founder of the Ponemon Institute, shared key insights from the study during a webinar. And in this year’s report, they included something new — the Critical Trust Index™. This 16-question core competency measurement aims to help businesses measure their certificate management capabilities, the effectiveness of their PKI efforts, and their agility and growth.
It’s a great study — one we’ll definitely quote cybersecurity statistics from throughout the year. But what makes it so good? The items highlighted in the study are the ones we see every day from our clients across multiple industries… both good and bad.
So, what can the results of this study tell you and how can it help you make informed decisions for your own PKI? And who was involved with the study?
Let’s hash it out.
Who and What the Study Evaluated This Year
The study, sponsored by our friends at Keyfactor, was independently conducted by the Ponemon Institute, both of which are well-known names within the industry.
The data in the study comes from the survey responses of 603 IT and infosec professionals from across North America. The majority of the respondents (61%) reported their positions as “supervisor or above” and another 30% indicated that they are at the staff/technician level. The majority are from large Enterprises, with 64% of the respondents indicating that they work for organizations with at least 5,001 employees.
The participants were asked to respond to a series of questions relating to cyber security threats, strategies, budgets, certificate management, compliance, and financial impacts relating to several of these areas.
5 Key Insights from Ponemon and Keyfactor’s 2020 PKI Study
From a 30,000-foot perspective, the current mechanisms for securing and managing digital certificates and cryptographic keys are lacking. Many companies lack the personnel and technical resources, budgets, procedures, or policies to effectively support public key infrastructure. As such, this leaves organizations open to significant risks from a variety of cybersecurity threats the world over.
But no matter how challenging it can be, IT security and information security practitioners alike know that public key infrastructure is critical to organizations. After all, PKI helps organizations to increase trust with end users and clients (their web browsers) alike through authentication and encryption. As certificate lifespans shrink and threats continue to evolve, the risk that your organization will be impacted increases with them.
But how important is PKI in the eyes of the C-suite executives above them? Let’s find out as we glean insights about this topic and others relating to the PKI ecosystem.
Takeaway 1: Executives Tend to Over-Estimate How Secure Their Organization Is
Perception and reality are frequently two different things — this is particularly the case regarding how PKI tasks and IT security challenges are handled. Probably the biggest takeaway that the study highlights the tremendous gap in perceptions in terms of confidence in the responses to questions between the technical guardians within an organization and those who are among the executive leadership above them.
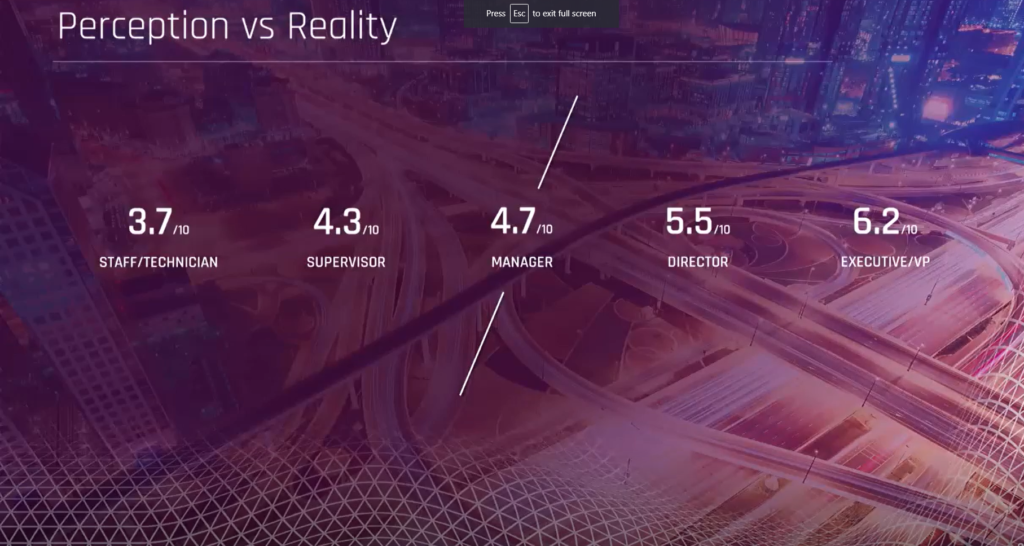
“In that data alone, it showed us very significantly how the problems of managing these types of critical assets in the organization, from the practitioners to the executives, differ when asked the same questions,” Hickman said in the webinar on the study.
Their observation made them question why there’s such a difference in the landscape between these different ranks within an organization. Executives tend to be significantly more optimistic in their responses than their staff/technician counterparts — averaging 6.2 on a 1-10 scale, versus staff/technicians, who have an average confidence rating of 3.7. This is particularly true concerning issues relating to managing critical assets.
These responses demonstrate why challenges might exist within organizations — leaders think issues are being handled or resolved, and practitioners are struggling to keep up with the never-ending demands.
Actionable Recommendations for How to Resolve This Issue
As with any organization and tasks, communication is key. There needs to be clear communication and transparency about the situation. If there are deficiencies, insufficient resources, or other challenges, everyone needs to be on the same page.
Practitioners
Don’t sugar coat things. Be open and honest about PKI and IT security-related issues that exist within your organization. Make your leadership aware of any challenges and offer recommendations and solutions to address the issues. Most importantly: Learn to speak their language.
One suggestion from Hickman and Ponemon shared during the webinar comes from Gartner:
Security leaders that successfully reposition X.509 certificate management to a compelling business story, such as digital business and trust enablement, will increase program success by 60%, up from less than 10% today.”
Essentially, executives want to know the bottom line — costs involved and how circumstances will affect the operation and organization as a whole. Don’t speak technical mumbo-jumbo. Give them what they want while still pushing for the resources you need by changing how you frame the situation.
C-Suite
Listen to your experts. Listen to understand and not to reply. Recognize that they’re humans and that the industry and cyber threats are continually changing. The threats we face today aren’t necessarily the same as those we’ll face in the future. Be flexible and open to change. If you want to protect your organization, don’t put off investing in your cybersecurity infrastructure and resources until tomorrow. Commit to making those changes today.
Takeaway 2: Organizations Use Lots of Certificates (They Think) But Lack PKI Visibility
According to the report, “60% of respondents believe they have more than 10,000 certificates in use across their organization.” That’s a lot of cats to herd. Interestingly, though, the respondents aren’t all that confident in their estimates — 74% indicate that they have no clue how many certificates and keys they actually are using for certain.
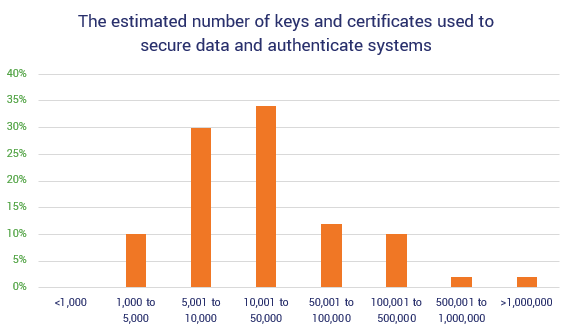
So, what do all of these statistics have in common? A lack of certainty (and clarity), for one. That’s because these organizations lack visibility into their PKI certificate management. Essentially, they don’t know:
- what certificates they have,
- where to find them, or
- when they expire.
This lackadaisical approach is kind of like trying to run a restaurant without any clue about who’s responsible for what and how it’s all getting done. For a restaurant to work, you need to know who’s ordering the supply deliveries, who’s making the food, whether the food that’s available to serve to customers meets certain quality and hygienic standards (it hasn’t expired), and who’s serving it.
If you don’t know these things because you lack visibility within your operation, then, frankly, you’re not going to be in business for very long.
Honestly, this finding that organizations have a lack of visibility into their PKI doesn’t strike me as surprising. After all, a lack of visibility is an ongoing issue for many organizations within the industry as a whole and was also an issue in their previous study from 2018. But it does surprise me a little is that the organizations are willing to admit that they lack this visibility and that it continues to be an ongoing issue.
According to their data, 55% of surveyed organizations said they had four or more certificate outages over the last 2 years! And 73% said that their organizations still experience unplanned downtime and outages due to mismanaged digital certificates.
So, what can done to help you address this lack of visibility and poor certificate management within your organization?
Actionable Recommendations for How to Resolve This Issue
Here at Hashed Out, we’re all about helping our readers avoid common PKI certificate management mistakes. One of the things we always emphasize is the importance of having visibility over your PKI. An issue that many admins have is that they’re trying to manage their keys and certificates using manual methods such as Excel spreadsheets. This is not only clunky and cumbersome, but it leads to a variety of issues.
One such example is shadow IT certificates. If you’re not the only person in charge of installing, renewing, and managing X.509 digital certificates, then some certificates can get installed that you don’t know about. And certificates that you may have installed yourself may fall through the cracks and expire without your knowledge. And you can’t effectively manage what you don’t know you have.
Using a reliable and reputable certificate management solution can help you to avoid this issue. The best certificate management tools enable you to
- discover certificates and keys on your network,
- manage certificate lifecycles with renewals and reissuance,
- avoid unplanned expirations (and the costs associated with them), and
- get back time that you can use to handle other important tasks.
This provides you with full visibility of your public key infrastructure. Considering that many organizations believe they have at least 10,000 certificates, you can see how trying to manually manage these assets is virtually impossible.
Takeaway 3: PKI Budget Ownership and Staffing Are Serious Issues
We get it. Everyone’s busy and, frankly, there just aren’t enough hours in the day to handle every task that comes our way. But that doesn’t change the importance of having a specific team or department that’s responsible for handling essential tasks.
Despite this need, study respondents indicate that digital certificate budgets and responsibility ownership are lacking. The tasks, responsibilities, and budgetary requirements associated with certificate management are often times spread among various departments within different organizations. Essentially, there’s no clear “center of excellence” for cryptography.
Their findings also report that nearly just a third (38%) of organizations claim that their organizations have the human resources dedicated to their PKI deployment. Part of this might be because of the stagnant cybersecurity budgets in comparison to the industry’s growing costs, or it could be related to the challenges companies report facing in terms of hiring and retaining talent.
Organizations represented in the Keyfactor/Ponemon Institute study reported spending only 16% of their budgets on PKI. That’s approximately $3 million from the reported average IT security annual budget of $19.4 million! And they also discovered that the responsibilities and ownership is frequently spread among other departments:
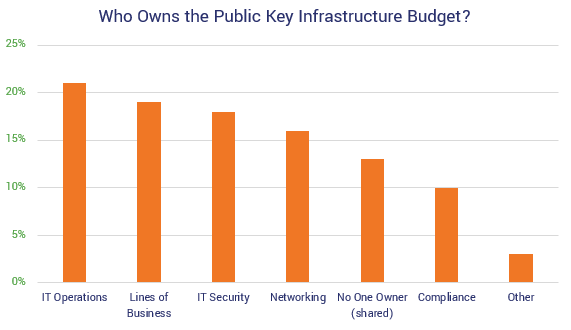
Actionable Recommendations
In the U.S., we’re experiencing some of the lowest unemployment levels in more than two decades. The U.S. Bureau of Labor Statistics (BLS) reports that for college grads, the unemployment rate is at 2.0% and 3.8% for high school graduates as of January 2020. We’re experiencing the lowest unemployment rates in IT security and technology, which is literally at 0%, according to Cybersecurity Ventures.
While this is great for jobseekers, it’s not as great for organizations looking to hire them. Why? Because it would imply that there’s a greater demand for skilled workers than there are people looking for jobs. This means that businesses and organizations are competing for talent. So, what can you do to combat growing workloads when you have static resources?
Some organizations are turning to automation and the use of artificial intelligence (AI). Automation can help reduce the load on your staff and augment their capabilities by eliminating the menial tasks from their workloads. Predictive analytics, language processes, authentication, and log analysis to identify anything unusual. Using AI helps to free up your employees so they can focus some of their attention on higher-level priorities and tasks.
One example of automation in PKI is a certificate management solution. You can use this tool to gain visibility into your PKI and discover shadow certificates. It’s also invaluable in terms of helping your team effectively manage all aspects of the certificate lifecycle and avoid certificate expirations, which Gartner estimates can cost an average of $300,000 per hour.
SSL/TLS certificates are a must for any ecommerce business (or any website, really, that wants to rank on Google and other search engines). And as more organizations readily adopt PKI solutions, it means there are more keys and digital certificates to manage. Using certificate management tools and other automation solutions can help you to not only streamline your operations and make them more effective, but it also helps you to control rising operational costs.
Takeaway 4: Certificate Outages Are a Big Risk, But They’re Not the Only Ones
While certificate outages are a major cause of concern, the responses received during the study indicate that failed audits due to insufficient key management practices, rogue or compromised certificate authorities (CA), and misuse of code signing certificates and keys are even bigger areas of concerns. This is true both in terms of financial costs as well as compliance.
The seriousness of failed audits and compliance headed up the rankings (4.1 on a 1-10 scale where 1 is considered a least serious problem and 10 is most serious problem). In particular, survey respondents are worried about insufficient or unenforced key management policies and practices. The next most serious issue related to man-in-the-middle (MitM) and phishing attack vulnerabilities that stem from CA comprormise.
We mentioned earlier that nearly three-quarters (73%) of respondents indicate that they experience unplanned outages and downtime due to mis-managed digital certificates. These occurences are more frequent than unplanned outages that result from certificate expiration. What makes these numbers even more dire is that disruptive outages are expected to keep increasing rather than decreasing. According to the report:
59 percent of respondents say the misuse of keys and certificates by cybercriminals is increasing the need to better secure these critical assets. Yet, more than half (54 percent) of respondents are concerned about their ability to secure keys and certificates throughout all stages of their lifecycle – from generation to revocation”
Actionable Recommendations
If you’re using a private CA, it’s not really surprising when things go sour. One of the best things you can do to avoid issues relating to rogue or compromised certificate authorities is to work with established, reputable commercial CAs who provide managed PKI services. It would be best to stay away from free PKI certificate providers because they lack the support and resources that commercial digital certificate providers have at their disposal.
Takeaway 5: Post-Quantum Is Not a Big Issue… Yet
The final insight we’ll share from the survey is that respondents’ concerns stemming from post-quantum cryptography are decreasing — for now. The Keyfactor and Ponemon report says:
Only 47 percent of respondents are concerned about the impact that quantum computing will have on their key and certificate management practices, but we expect this number will rise as recent advances in quantum technology bring us closer to the potential breaking point of the keys and algorithms we rely upon today.”
Essentially, there is and has been hype surrounding the topic for several years. But until quantum computing is available at the commercial level, we’ll overestimate the potential negative impacts rather than highlight its positive impacts on security, Ponemon said.
Hickman says that quantum computing is our future reality — it’s just a matter of “when,” not “if” it will become a thing. That’s why the industry’s work on post-quantum algorithms is critical (see our previous blog post highlighting DigiCert’s work on post-quantum cryptography) and why organizations need to:
- take inventory of their assets,
- know where their technology and encryption are deployed, and
- have a plan for managing crypto as algorithms become deprecated.
“Rarely have we seen something in this industry with the potential cataclysmic effect of quantum, and the disruptive nature that it will bring from a security standpoint,” says Hickman, who emphasizes the importance of planning, which seems to be taking a back seat in terms of being considered a priority.
Hickman continues:
Having a plan, understanding where your digital assets live, where your cryptography is deployed, having ways to manage that crypto is absolutely important. Things are going to happen along the way — such as the deprecation of algorithms… But you’ll be able to reuse that same plan and actually validate it top make sure that you’re ready for a post-quantum world.”
Final Thoughts
From these survey responses, it’s obvious that there’s no one clear owner of PKI budgets and efforts with multi-discipline and multi-functional teams. And there’s also no one agreed upon method that these surveyed organizations rely on to deal with these increasing crypto responsibilities. But it’s obvious that having a governance process in place and clear visibility of your public key infrastructure are essential to improving a business’s certificate management capabilities. Part of this entails establishing a cryptographic center of excellence if one doesn’t already exist.
The increasing use of encryption technologies, digital certificates, etc. for compliance with regulations and policies dictates the need for better certificate management practices. And as operational costs continue to increase without a parallel increase in operating budgets to cover those costs, automation will become important the closer we get to a PQC world.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown