Post-Quantum Cryptography: 10 Things You Need to Know
DigiCert’s newly released survey shows that 71% of IT professionals consider quantum computing a looming threat to encryption and security—here’s how you can protect your company and customers
Quantum computing is coming, and it has current encryption algorithms in its crosshairs.
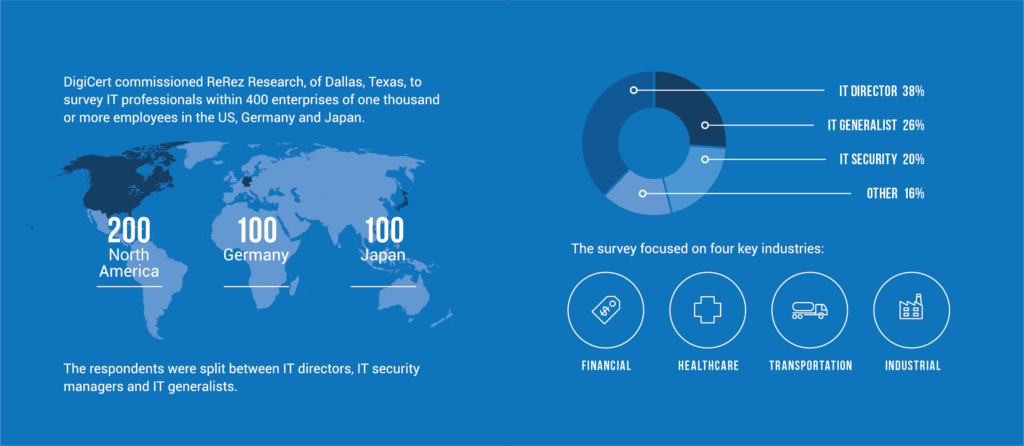
The good news is that IT professionals across the globe are aware of the threat and are already taking action to get ready. That’s according to a newly-released survey from DigiCert and ReRez Research that gathered data from IT staff at 400 enterprises in the US, Japan, and Germany.
Here are 10 things you need to know about quantum computing, quantum proof encryption, and how you can prepare.
Let’s hash it out.
#1: Google & IBM Made Huge Strides in Quantum Computing in 2019
Just this year, the tech giants have made two advancements that are moving quantum computing from theory to reality:
- IBM introduced IBM Q System One in January – the first ever circuit-based commercial quantum computer.
- Google announced in September that they achieved quantum supremacy – their quantum computer solved a problem that was practically impossible for standard computers to do.
#2: Quantum Computing Will Make Current Encryption Obsolete
Current encryption algorithms are considered secure because it would take current computers too long to break the encryption. For example, DigiCert calculated that it would take a standard computer quadrillions of years to break a 2048-bit key.
Diving into all the technical details is outside the scope of this post, but the main point is that quantum computers will be able to do things that are impossible with current computers…including breaking current encryption standards such as RSA, ECC, etc. That’s what post quantum cryptography (PQC) is all about – replacing current cryptographic algorithms with quantum resistant cryptography.
#3: 71% of IT Professionals Say Quantum Computing Will Be a Large Threat
The majority of respondents to DigiCert’s survey agree that quantum computing is and/or will be a significant threat to cryptography:
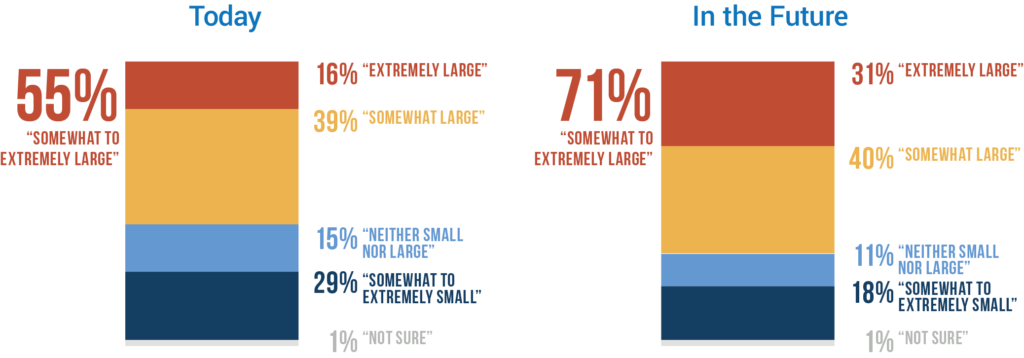
#4: Encryption Is Everywhere – And It Will All Need to Be Replaced
SSL certificates are perhaps the most prominent use of public key encryption in our modern lives, but they’re pretty easy to update—most of us update our certificates every 1-2 years anyway.
But public key encryption is also found countless other places in our lives, and many of them won’t be so easy to update:
- Most programming languages and operating systems have built-in cryptographic libraries used by all types of software from CRMs to medical billing.
- Encryption is used across all types of databases for everything from web apps to the IRS.
- Modern cars, airplanes and other vehicles relay heavily built-in computers, certificates, and encryption. (And, a car that’s sold today could still be on the road in 20 years.)
- IoT devices, including everything from smart electricity grids to thermostats (and everything in between) often use encryption in multiple ways. These can be extra tricky, as an IoT device may be installed and in service for decades before it’s replaced or updated.
In short, encryption is used by nearly every piece of hardware and software on the planet (not to mention those not even on the planet…satellites and the International Space Station).
Most of these encryption implementations will need to be updated before quantum computers become generally available.
#5: 83% Say Learning About Quantum-Safe Security Is Important
The good news is that IT professionals want to keep up with the threats quantum computing is bringing. DigiCert’s survey found that an overwhelming majority consider learning about post quantum encryption an important priority.
Knowledge is power: forewarned is forearmed!
If you want to learn more about post quantum cryptography, here are a few resources we recommend:
- DigiCert’s documentation on PQC
- Sectigo’s 6-part podcast series on Quantum-Resistant Cryptography
- Trail of Bits blog post on PQC
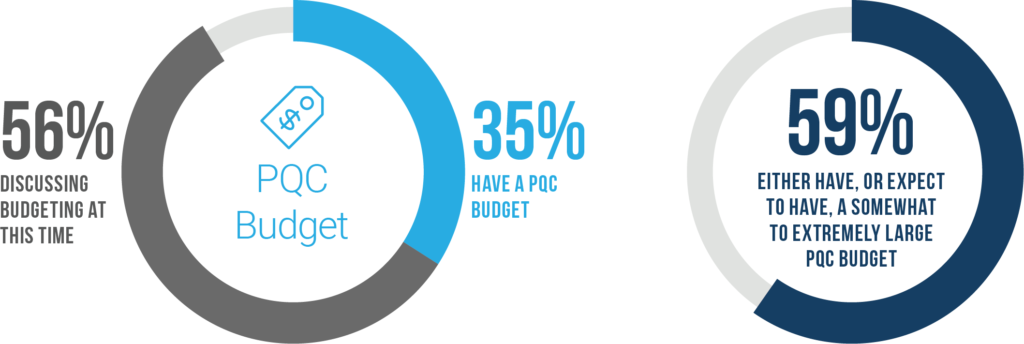
#6: 91% Say They Have or Are Discussing a Budget for PCQ
Now only are enterprise IT pros aware of the threat of quantum computing, and interested in learning about it, they’re taking action. A strong majority say they already have, or will have a substantial budget for updating their encryption to protect against quantum computing threats.
#7: We’ve (Probably) Got a Few Years Until Quantum Computing Is a Real-World Threat
You don’t need to go out today and start replacing your SSL certificates and database encryption solutions – in fact, in most cases you can’t. Post Quantum Cryptography (PQC) is still “in progress.” (For example, PQC isn’t yet supported by popular web browsers.) And that’s OK, because quantum computers aren’t a real-world threat yet – they’re still locked up in the labs of companies like IBM and Google.
There’s no accurate way to know when quantum computing will be available, but it probably won’t be in the next year or two, at least. Scientific American estimated it’s “more than a decade away,” some experts say “about a decade, give or take,” while most respondents to DigiCert’s survey think it will be by 2025.
#8: Cryptography We Do In 2019 Echoes in Eternity
I’m borrowing a little wisdom from Maximus Decimus Meridius (Gladiator) on this one. Although he was giving a pep talk to Roman Legionaries, the same basic principle applies to technology: things we do now tend to stick around longer than we think they will.
This is part of the reason that companies need to start preparing for quantum computing now – once a device or software is released “into the wild” it might be months or years before it would typically be updated or replaced. Consider these examples:
- The average car in the United States is 12 years old, and there are approximately 75 million vehicles still on the road that are over 16 years old. Even if all cars are built with PQC starting in 2020, in 10 years there will still be a lot of smart cars on the road that were built before PCQ was available.
- Many IoT devices are being built to last for 10-20 years without even needing a battery replacement.
- Outdated operating systems (which, comparatively speaking, are pretty easy to update) stubbornly stick around for years. So far this year, we’ve had 9,100 people visit our blog using Windows XP (an 18 year-old operating system that’s been outdated for 13 years). Believe it or not, we still get visits from people using Windows 2000, Windows NT, and Windows 98!
If your company works with technology that’s designed for an extended lifespan (i.e. IoT), you’ll need to accelerate your schedule for PQC to ensure your devices are ahead of the curve, even after they’ve been in the field for years.
#9: Now Is the Time to Prepare – Here’s What You Can Do
As we mentioned above, companies need to get ahead of the curve with PQC to ensure that they and their customers are protected. (Few things are more frustrating than frantically scrambling to update technology at the last minute to defend against a threat that’s already arrived.)
What you can start doing now to prepare? Timothy Hollebeek, Industry and Standards Technical Strategist at DigiCert, recommends companies take these three steps:
- Make a list of your encryption implementations. Build and maintain an inventory of everywhere cryptography is used in your organization – this includes everything from digital certificates to databases and everything in-between. (This is a great example of why it’s important to use a certificate management tool with a discovery feature – see our Certificate Management Best Practices Checklist for more info.)
- Lean on your vendors to build a plan. PQC is still a work in progress, but you’ll want to be sure that your vendors (for everything from SSL certificates to databases to online backup) have a plan to ensure they stay ahead of the curve for quantum computing threats.
- Begin proof-of-concept testing. This step is critical, as it will allow you to identify the areas where you’re most likely to experience significant challenges when the time comes to make the switch.
Note: If you’re looking for PQC digital certificates, stay tuned. We’ll soon be offering DigiCert certificates with hybrid PQC encryption options! You’ll be able to start testing PQC while remaining fully compatible with current algorithms.
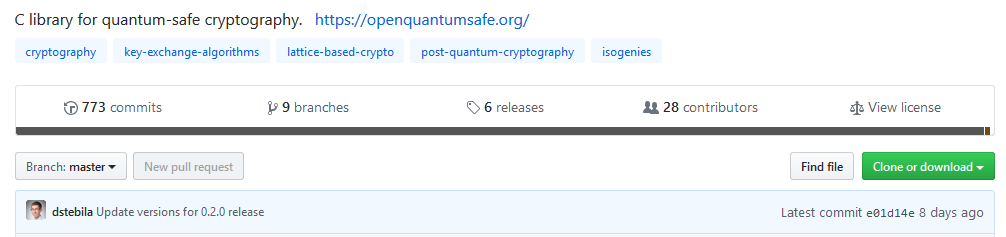
#10: There’s Already an Open Source Library For PQC
If you’re looking to jump in and get hands on with post-quantum cryptography, check out the Open Quantum Safe project, an initiative “to support the development and prototyping of quantum-resistant cryptography.” Their open source C library for quantum-resistant cryptographic algorithms, Liboqs, is available on GitHub.
Summary (The Sky Isn’t Falling)
In short, quantum computing will necessitate a major change in how we do cryptography and will mandate a lot of technical updates over the coming decade. But don’t panic – we’ve probably got a few years to take care of this. The sky isn’t falling (yet)!






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown