71% of Organizations Don’t Know How Many Certificates & Keys They Have
A new study begs the question: are we having the right conversation?
A new study from KeyFactor and the Ponemon Institute has shed some interesting light on the pain points most organizations go through when they’re managing their digital certificates and encryption keys.
There were some key takeaways from the study, one of which was simply the scope of the problem. Certificate management has become a major burden as our digital infrastructure and the role of PKI has continued to grow. The larger an organization gets, the more acute the problem becomes.
But one of the other major takeaways is the fact that for many organizations, the biggest risk they perceive stemming from bad certificate management isn’t compromise, misuse or expiration.
It’s failing audits or being non-compliant.
And that begs the question, are we, as an industry, having the wrong conversation?
Let’s hash it out.
The Impact of Unsecured Digital Identities
Published just last month, KeyFactor and the Ponemon Institute created an exhaustive survey and spoke with a range of professionals from myriad organizations to put together this information. Let’s just start a little bit with the methodology before we get into the findings.
First of all, this study was conducted in the United States and consisted of 30 questions about five potential certificate management disaster scenarios (the five fingers of death). Here’s the breakdown of what positions those surveyed hold in their organizations.
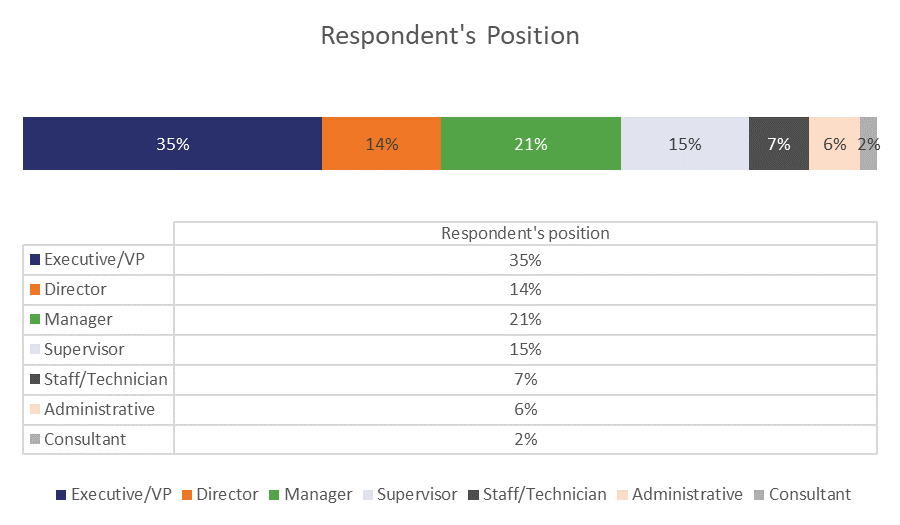
This survey was originally sent to over 17,000 organizations and was returned by just over 600. 58 of those were tossed out for various reasons, which means the final sample comes from 596 American organizations. Here’s the breakdown of their size.
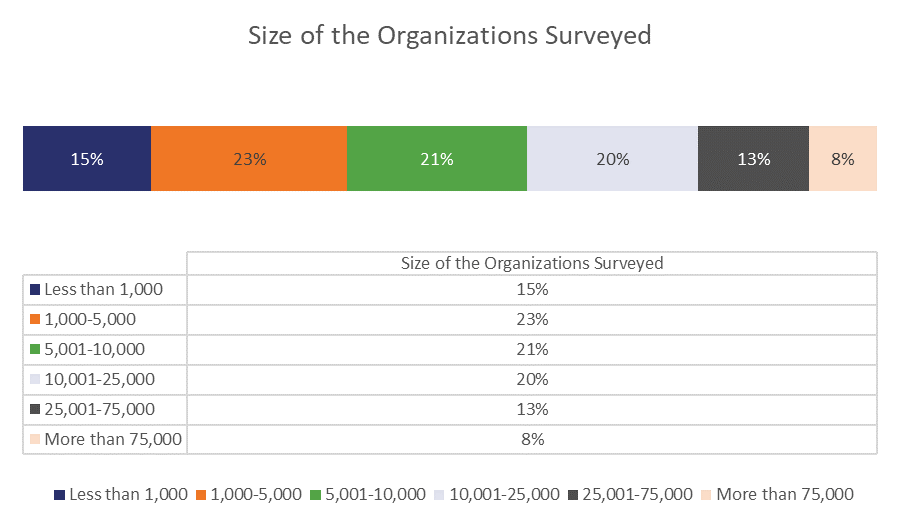
Ok, so with that in mind, let’s look at the key takeaways from the study.
61% of Organizations Are Concerned They Can’t Secure Keys Through All Stages of the Lifecycle

Three out of five organizations have serious concerns about their ability to secure encryption keys during all stages of their lifecycle, from issuance to rotation, renewal and revocation. As we’ve discussed before, at its heart SSL/TLS is really just an elaborate digital mechanism for exchanging the encryption keys we’ll use to communicate with the websites or end points we visit. Strip away all of the other terminology and what you are doing every time a handshake takes place is authenticating the other party so you can use their public key to encrypt a session key (or the secret that will lead to its generation) so you can communicate securely.
Obviously, that’s just in the context of SSL/TLS, but encryption keys are also used for a number of other purposes like signing email, documents, software, etc.
We cover the risks of key compromise all the time because it’s a fairly common threat. This underscores the fact that many organizations view it the same way. But there do seem to be some things holding many organizations back from improving their certificate and key management practices: cost.
Per the study:
Most organizations do not have adequate IT security staff to maintain and secure keys and certificates, especially in the deployment of PKI. Further, most organizations do not know how many keys and certificates that IT security needs to manage.
So, it’s partly a lack of qualified personnel. But that costs money. Additionally:
Pricing models can prevent organizations from investing in solutions that cover every identity across the enterprise.
That’s why it’s generally better to work with an SSL service instead of trying to go direct from a CA, but what would we know…
Anyway, the financial concerns don’t end there. This is taken from a part of the survey that dealt with organization’s perceptions of PKI and certificate management in general, it asked respondents to respond with their level of agreement about a given statement from Strongly Agree to Strongly Disagree. Clearly, cost is a major concern:
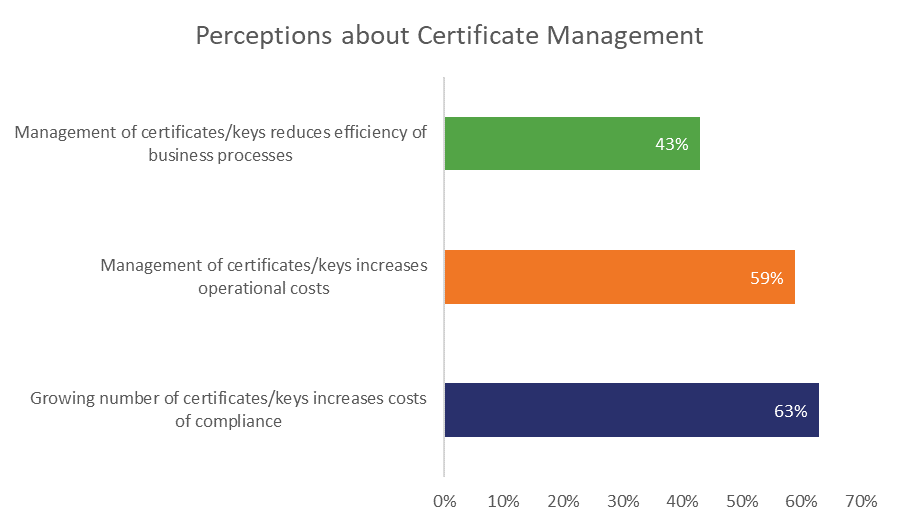
We actually deal with quite a few Enterprise clients, not every PKI and certificate management solution is cost-prohibitive. In fact, some are quite budget-friendly. And we’ve actually got a white paper coming out on Certificate Management best practices next month (so keep an eye out).
Here’s a look at the percentage of organizations that are outsourcing all or part of their Public Key Infrastructure deployment.
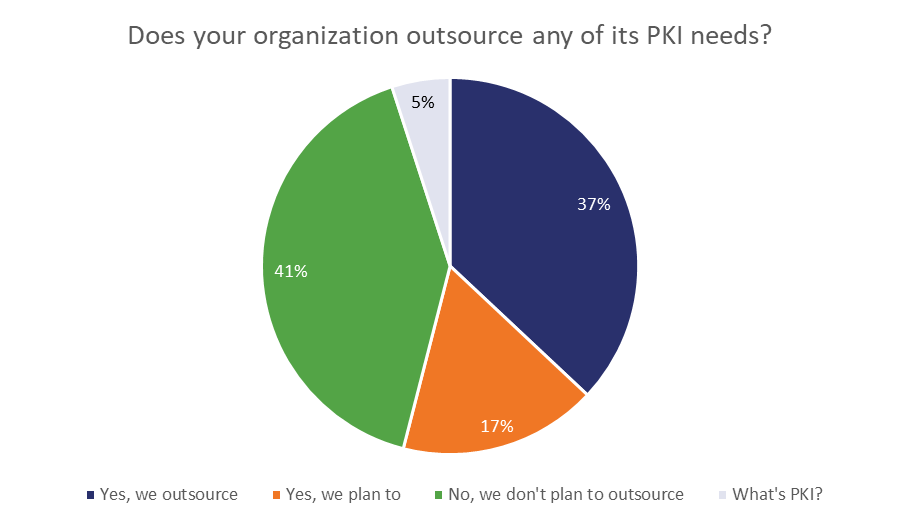
This is one of the ways we’re probably missing the target as an industry, because the perception of certificate management is that it’s expensive and complicated. It doesn’t have to be. And in the long run, it’s not a sunken cost – it’s an investment. Because as we’re about to unravel, the costs associated with mismanaging certificates is staggering.
But, before we go any further, let’s take one more chance to identify the scope of the problem we’re talking about. Of the nearly 600 respondents, this was the average number of certificates and keys owned by each one (per the survey’s extrapolation).
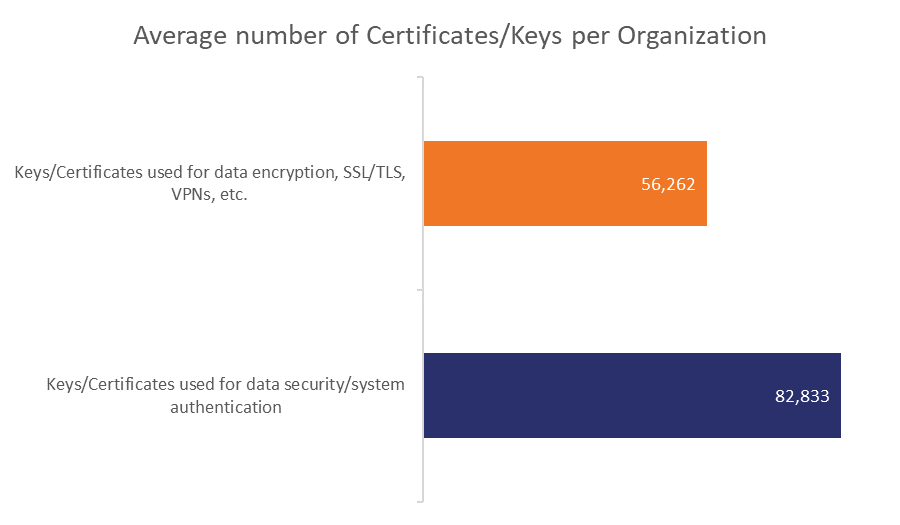
As organizations grow larger, certificate and key management become exceedingly difficult. There comes a point where you either need to hire dedicated staff to handle it or you need to outsource it to a third-party security company that knows how to handle it for you.
Doing anything else is just inviting trouble.
And, as we touched on at the start of this section: 61% of these organizations don’t have confidence they can secure these keys and certificates for the entire duration of their lifecycle. Organizations need to be proactive about this before it comes back to bite them.
Let’s talk about what kind of trouble you may be inviting by not being proactive with your certificate management policies.
The Five Fingers of Death
Indulge me the Kung Fu header while we talk about the five nightmare scenarios that this survey presented:
- Unplanned outages due to certificate expiration
- Failed audits or compliance due to bad certificate/key management
- Server certificate and key compromise/misuse
- Code Signing certificate and key compromise/misuse
- CA compromise; rogue CA for MITM or phishing (rogue certificates)
This is where things take an interesting turn, and it goes back to whether we’re having the right conversations as an industry – this is how the organizations surveyed view these threats.
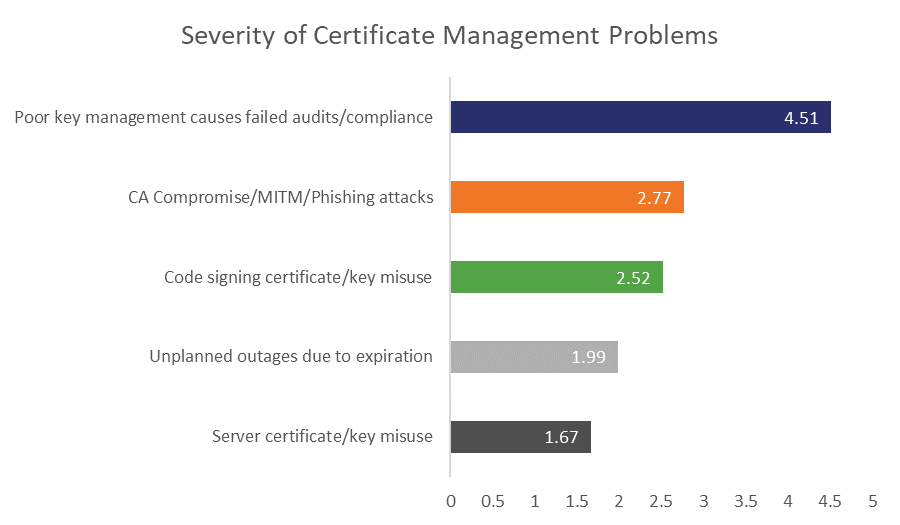
On a scale of one to five, with five being the most sever, Failed audits/non-compliance is number one by a wide margin. That shows that for most organizations, data security and secure connections are nice ideals, but where rubber meets the road is in terms of maintaining compliance with industry standards and legal regulations.
There’s a good chance a lot of this stems from the GDPR, which went into effect last year and threatens massive penalties for organization’s that fail to comply.
In that sense, the security is a means to an end. The end being compliance. Organizations are less interested in the actual security benefits than they are in maintaining compliance and avoiding the fines and penalties that come with running afoul of that.
There’s an old anecdote about a salesman who sells drill bits and over time realizes that his customers could really care less about the details of the drill bits themselves – what they want is a quarter-inch hole. That’s their interaction with the product. What we might be missing is that for many organizations, their quarter-inch hole isn’t cybersecurity at all, that’s a secondary concern to compliance.
But despite the decided advantage failed audits/non-compliance have in terms of the severity they’re perceived with, they cost organizations about the same as any of the other four certificate/key management disasters.
| Scenario | Extrapolated Cost |
| Cost of unplanned outages due to certificate expiry | $11,122,100 |
| Cost of failed audits/compliance due to undocumented or poor key management | $14,411,500 |
| Cost of server certificate and key misuse | $13,423,250 |
| Cost of Code Signing certificate and key misuse | $15,025,150 |
| Cost of CA compromise or rogue CA for MITM and/or phishing attacks | $13,219,850 |
| Total Cost | $67,201,850 |
Truth be told, it’s often the other four disasters – expiration, compromise or rogue certificates – that lead to failed audits and non-compliance. So, mitigating them is ultimately going to strengthen compliance. These things are all interconnected.
RELATED: This is what happens when your certificate expires…
It All Starts With Visibility
The biggest pain point for most organizations dealing with large-scale certificate management is visibility. They don’t know how many certificates and keys they have, they don’t know who ordered them all, they don’t know when they expire. That goes for 71% of all organizations surveyed.
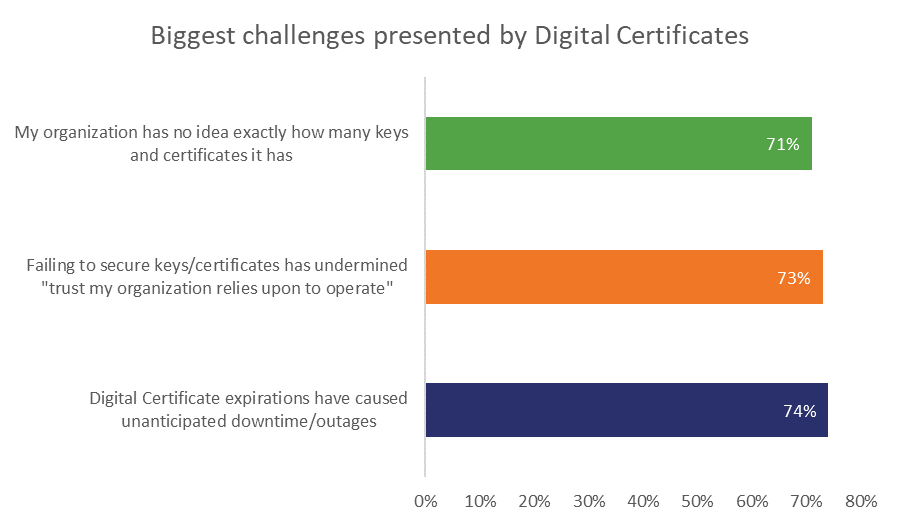
This is exactly where a good certificate management platform can pay for itself: by scanning your network and the various CT logs for all relevant certificates and giving you a single interface with which to manage them all. Just by doing that you’ll be minimizing the risk of unforeseen expiry or rogue certificates.
Here’s a look at what departments control the PKI budgets and certificate/key management. As you can see it’s a total scattershot. And if you’ve got multiple departments in the same organization making PKI decisions things are only going to grow more complicated.
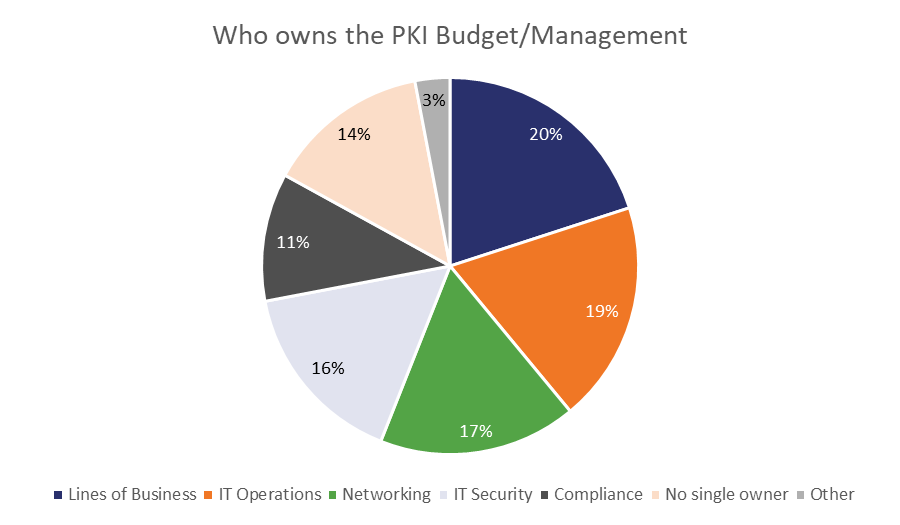
Again, this is where investing in an actual certificate management platform pays dividends. You can add multiple users with varying permissions so you can better control who touches what and more importantly, who can’t touch it.
Let’s look at some more pain points for organizations in the certificate/key management department. Or, more specifically, the frequency with which they occur and the likelihood they will continue to be a problem.
| Event | Occurrences (per 24 months) | Future Likelihood |
| Expired Certificates | 4 | 30% |
| Failed Audits/Non-compliance | 5.5 | 42% |
| Server certificate compromise | 4.6 | 39% |
| Code Signing certificate compromise | 3.9 | 29% |
| Rogue Certificates | 2.3 | 38% |
A quick word on the rogue certificates, it’s easy to dismiss this scenario as unlikely. Don’t. In just the last 30 days the US Department of Homeland Security issued an emergency directive warning of rogue certificates. That’s just the most recent example, but make no mistake about it: rogue certificates are a threat and an extremely costly one at that. Notice it costs organizations about the same over two years as any of the other four scenarios – despite occurring less frequently.
Again, a lot of these things can be avoided simply by investing in a quality certificate management platform. There are good ones from Sectigo, DigiCert, Venafi and a range of other vendors. They help you to scan your networks, provide visibility, an interface to manage all stages of the certificate lifecycle and if you would prefer to just outsource everything, you can even have someone manage it for you.
This is something that more organizations need to act on, but it’s also a conversation that we, as an industry, aren’t approaching correctly.
Organizations care deeply about complying with the various laws and industry standards that govern them. There are very real, very tangible ramifications for non-compliance. A certificate expiration that causes a website to go down doesn’t invoke the same level of panic in the C-suite that a failed audit does.
Certificate management won’t solve all of that, it’s not a turn-key solution for compliance across the board. But it does mitigate any risks that digital certificates and encryption keys may pose to your organizational compliance. And in the long run, that could save everyone a lot of money.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown