US DHS issues Emergency Directive warning about Rogue Certificates
“Because the attacker can set DNS record values, they can also obtain valid encryption certificates for an organization’s domain names…”
The US Department of Homeland Security (DHS) issued an emergency directive on Tuesday ordering all federal agencies to “audit public DNS records on all authoritative and secondary DNS servers to verify they resolve to the intended location.”
That’s because attackers have been launching DNS hijacking attacks that could help them get SSL/TLS certificates issued for government domains.
Obviously, that would be disastrous.
So today we’re going to talk about Iranian hackers, DNS hijacking and rogue certificates.
Let’s hash it out…

An Emergency Directive from the DHS
The US Department of Homeland Security is authorized to issue emergency directives “in response to a known or reasonably suspected information security threat, vulnerability, or incident that represents a substantial threat to the information security of an agency.”
It rarely does so, but yesterday it deemed it necessary and issued Emergency Directive 19-01.
In coordination with government and industry partners, the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) is tracking a series of incidents1 involving Domain Name System (DNS) infrastructure tampering. CISA is aware of multiple executive branch agency domains that were impacted by the tampering campaign and has notified the agencies that maintain them.
Attackers are rewriting DNS records to point them towards address under their own control, which gives them the ability to MITM connections and even get SSL/TLS certificates issued for compromised domains. When this happens, and an attacker gets their hands on a legitimate certificate, it’s called a rogue certificate and it can spell disaster. That gives the attacker the ability to impersonate the site, decrypt its traffic, whatever they want.
Add in the fact that these are federal websites and the risk increases exponentially. Researchers at FireEye have determined with a moderate degree of certainty that the hijacking attacks are emanating from Iran. They’ve been occurring in clusters since 2017.
In order to stave off any rogue certificates and protect DNS records, the DHS is mandating four actions be taken over the next ten days:
- Audit DNS Records – “Audit public DNS records on all authoritative and secondary DNS servers to verify they resolve to the intended location.”
- Change DNS Account Passwords – “Update the passwords for all accounts on systems that can make changes to your agency’s DNS records.”
- Add Multi-Factor Authentication to DNS accounts – “Implement multi-factor authentication (MFA) for all accounts on systems that can make changes to your agency’s DNS records.”
- Monitor Certificate Transparency Logs – “Agencies shall immediately begin monitoring CT log data for certificates issued that they did not request.”
If the agencies run into any problems they’re supposed to contact the DHS’s Cybersecurity and Infrastructure Security Agency (CISA).
Per the release, CISA will:
- Provide technical assistance to agencies that report anomalous DNS records.
- Review submissions from agencies that cannot implement MFA on DNS accounts within the timeline and contact agencies, as needed.
- Provide regular delivery of newly added certificates to CT logs for agency domains via the Cyber Hygiene service.
- Provide additional guidance to agencies through an Emergency Directive coordination call following the issuance of this directive, as well as through individual engagements upon request (through CyberLiaison).

Wait, isn’t CISA Furloughed because of the Shutdown?
Yes, as of last week CISA had about 45% of its workforce furloughed, with only “essential” functions covered. Additionally, 45% of the DHS’ operations team, which includes the Office of Intelligence and the Office of Operations Coordination, is furloughed as well.
RELATED: Apparently certificate management isn’t an “essential function.”
It’s possible that more of CISA’s personnel has been called back to work (unpaid), but I haven’t seen anything official. If I do I’ll update this post. Otherwise, assume that DHS and CISA are both currently a little understaffed.

Do these attackers feel emboldened because of the shutdown?
Maybe a little bit, but these attacks would still be occurring even if the US government was not currently shut down. These kinds of attacks between nation states are beginning to occur with startling frequency. Russia, China and the US are all engaged in varying degrees of cyber espionage and reconnaissance. And more and more countries are beginning to adopt a more aggressive, offensive-minded approach – as France announced yesterday.
But, make no mistake about it, if ever there were a time to try to hit the US government with a cyber-attack – it’s right now. And if FireEye is right, and it is Iran, there is no lack of potential enmity there as a result of the US’ withdrawal from the nuclear treaty and its subsequent economic sanctions. This is not a commentary on the wisdom of either of those decisions, just a simple statement of fact.
What is DNS hijacking and why is it dangerous?
DNS hijacking is what occurs when you manipulate a server’s DNS records to resolve to an address of your choosing. In order to execute this attack, you need to have credentials for, or some other means of accessing a user account with permissions to edit DNS records. So there’s likely another component of this campaign that hasn’t been ferreted out yet, and it likely involves some form of phishing.
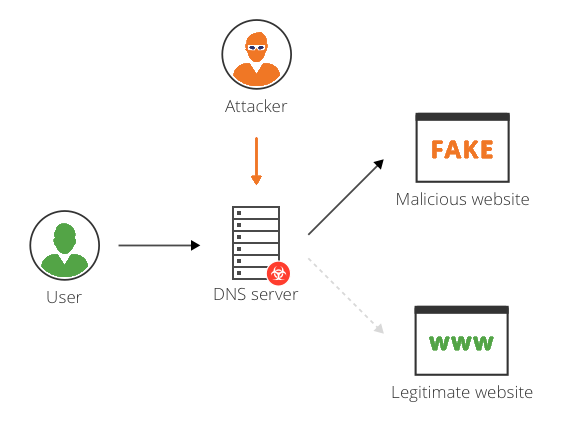
Once the attacker has access to an account that can change DNS records, they begin to alter address records, mail exchanger records or name server records and replace the original addresses with addresses under the attacker’s control.
This enables [the attacker] to direct user traffic to their own infrastructure for manipulation or inspection before passing it on to the legitimate service, should they choose. This creates a risk that persists beyond the period of traffic redirection.
Finally – and this is the part that’s most germane to our area of focus – being able to control DNS records on a given server gives the attacker the ability to request, and have issued, legitimate SSL/TLS certificates for any website residing on said server.
This allows the redirected traffic to be decrypted, exposing any user-submitted data. Since the certificate is valid for the domain, end users receive no error warnings.
This is the same thing we saw last year when a DNS cache poisoning technique was discovered that allowed attackers to obtain legitimate certificates for sites they didn’t control. When this happens it’s called a rogue certificate
How dangerous are rogue certificates?
If there is a nuclear-level emergency in the SSL/TLS world, it would be rogue certificates. We’ve actually gone in-depth on Rogue Certificates in the past, but here’s the gyst of it:
Rogue certificates allow attackers to create illegitimate sites that are indistinguishable from real sites like eBay, Google or PNC because their certificate hierarchy can be validated. Users then will be redirected to such sites through phishing or ”man in the middle” attacks where a compromised host in-between the user and a legitimate site sends traffic to an illegitimate site instead.
Eric Vandenburg, VP of TCDI (Technology Concepts & Design, Inc.)
Rogue certificates are rare, but still more common than they should be. In the past, rogue certificates have gotten CAs shut down, perhaps unironically it was actually Iran that helped to put an end to the Dutch CA DigiNotar in 2011 after it managed to compromise DigiNotar’s private key with an SQL injection.
The best ways to defend against rogue certificates are:
- Monitoring CT logs, which is exactly what the DHS is instructing other federal agencies to do.
- Add a CAA Record. That prevents unauthorized CAs from issuing for your domain.
- Run regular scans on certificate revocation lists and OCSP logs.
Hopefully this shutdown ends soon and the US National Cyber Security apparatus can return to full strength. In the meantime other countries are going to keep probing.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown