HTTPS Phishing: 49% of Phishing Websites now sport the green padlock
We need to have a clearer discussion about HTTPS and the green padlock.
Every month it seems like we hit a new milestone in the internet’s mass migration from HTTP to HTTPS with more and more websites adopting SSL/TLS and securing their connections. Unfortunately, today we’re reporting a far more dubious milestone: nearly half of all phishing websites are now using HTTPS, too.
And while this was always inevitable, given the fact that HTTPS has become the new standard, it still casts a light on an issue that is going to plague this industry until we start to have a more frank discussion about HTTPS:
Secure ≠ Safe.
If you’re a regular reader of Hashed Out you know this is a point we’ve belabored, but one that still bears repeating. So, today we’re going to do that. We’ll talk about HTTPS, people’s misperceptions about it and what we need to do better as an industry to correct those misperceptions moving forward.
Let’s hash it out.
Nearly half of all phishing websites now use HTTPS
HTTPS phishing has been increasing exponentially for the past couple of years. As of last Fall, over 1.4 million new phishing websites were being created each month. That number only figures to have grown since then. But while last year the number of HTTPS phishing sites was only about 25% – one in four – that’s nearly doubled to 49% as of Q3 2018, per Phish Labs.
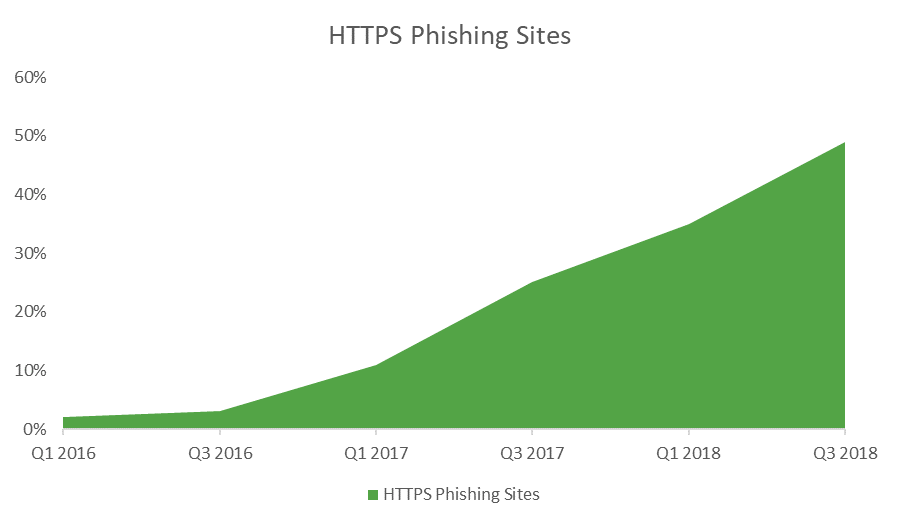
That’s a significant increase. Almost two years ago, in early 2017, we ran a research article that showed the prevalence of free Let’s Encrypt SSL certificate on fake PayPal phishing websites. And while many Let’s Encrypt supporters were skeptical of our intentions, the point that we were making – about the approaching spike in HTTPS phishing websites – is kind of borne out by these figures.
HTTPS is no longer GOING to be a problem. It officially is. And that shows no signs of abating given the ubiquity of free Domain Validated SSL/TLS certificates and the industry-wide push towards HTTPS.
And we want to be on the record here: there’s absolutely nothing wrong with free SSL certificates. There should not be an economic gatekeeper to HTTPS when that’s now the standard. The issue is how we’re framing HTTPS.
 Most people have no idea what HTTPS actually does or what that green padlock means
Most people have no idea what HTTPS actually does or what that green padlock means
It’s easy to take for granted just how little people know about what they’re doing online. Historically, internet users have had to be at least semi-computer literate owing to the fact you could only access the internet from a computer. But now that almost everyone in the developed world owns an internet-connected smart phone, that barrier for entry has effectively been removed.
And whereas with traditional desktop browsers we have made some effort to educate people on how to use them – in my experience this was usually done by an aging librarian/media specialist (depending on when you went to school) upon your first visit to the library/media center each school year – and meager though that was—it was something.
Again, with the age of the smart phone, that’s all gone out the window. People are oftentimes left to their own devices (literally) to figure it out. And given the lack of space these devices have to display things like URLs, the symbols and visual indicators used by those devices must serve as a sort of shorthand that can help inform users about what they’re viewing.
Unfortunately, those symbols, specifically that little green padlock that is synonymous with HTTPS, have fallen short on accomplishing what they were intended to do. Let’s start with this: all that green padlock means is that the connection your device is making with the server hosting the website or application you’re visiting will be encrypted and secure. So, any data you and the party at the other end of that connection exchange will be safe from any attackers or third parties that may be attempting to eavesdrop on said connection.
But, without some form of organization authentication, you have no guarantees about who the party on the other end of that connection is. Bad guys can use HTTPS, too. So while the green padlock means that your connection will be secure, it makes no guarantees about your safety on that website or what the party on the other end of the connection may do with the data you send.
Most people don’t know that. Here are the results from a survey that Phish Labs did last year.
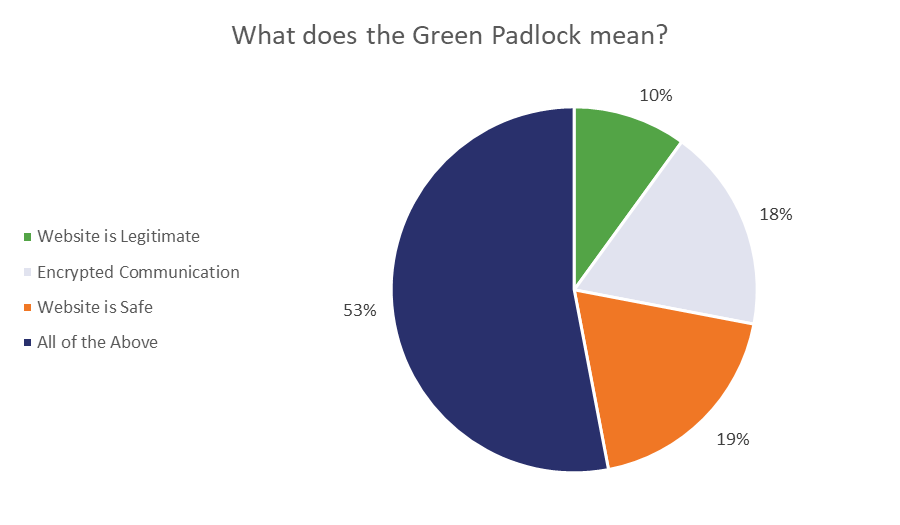
We can re-categorize that a little bit so that it makes our point a bit more explicitly.
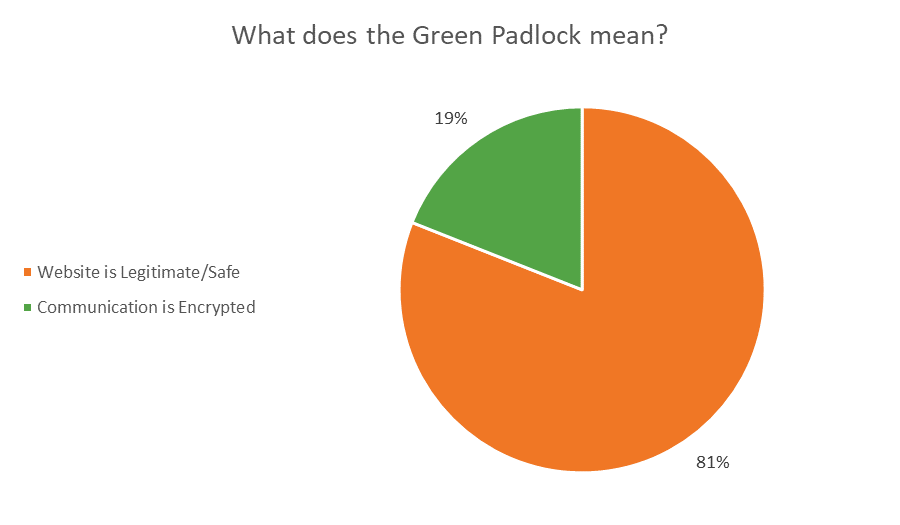
That means that a staggering number of people – again, a good many of them on mobile – can be easily duped by that little green padlock icon. And cybercriminals are acutely aware of this fact. Cybercrime will be a 1.5 trillion dollar industry in 2018, and that did not happen by accident. These criminals know how dupe people out of their money. They know how to socially engineer emails that will get you to these websites with your guard already lowered.
And the presence of that little green padlock certainly isn’t going to raise any antennas. Sure, having an SSL certificate, and thus HTTPS, on a phishing website is by itself probably not going to snare anyone. But when it’s layered on to the site alongside other convincing elements – a few fake testimonials, maybe a spoofed site seal or a Unicode URL – it can help to achieve the intended effect.
It only needs to pass the glance test, after all. Most people aren’t going to do much more than that.
Google, you may not be helping…
Like it or not, Google is the de facto industry leader when it comes to browser indicators. Given its market share, largely owing to its Android OS and Chrome desktop browser, Google needs to take the lead on educating people about HTTPS, specifically what it is and isn’t.
And it’s been Google that’s been pushing websites to migrate to HTTPS for years, practically mandating it this past July.
Unfortunately, Google hasn’t done a very good job with the messaging that has accompanied this initiative. And it may have done some real damage in its attempts to expedite the internet’s migration to HTTPS.
While it’s reversed course now and removed the positive indicator, for about a year Chrome was showing a badge that said, “Secure” on websites that had an SSL/TLS certificate installed and were properly configured for HTTPS. That was a horrible idea – one that we criticized extensively.
Google has now completely reversed course, phasing out the protocol (https://) at the start of the URL, with intentions to eliminate the green padlock icon that has traditionally accompanied it, too.

All that will remain is a negative indicator for websites still being served via HTTP.
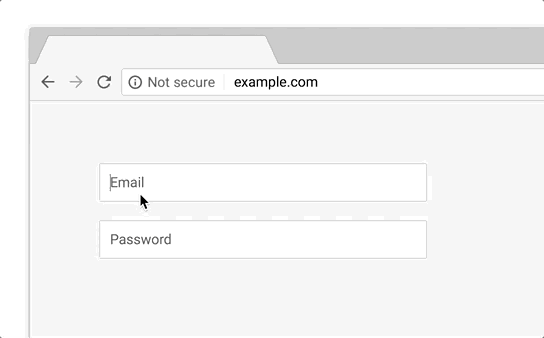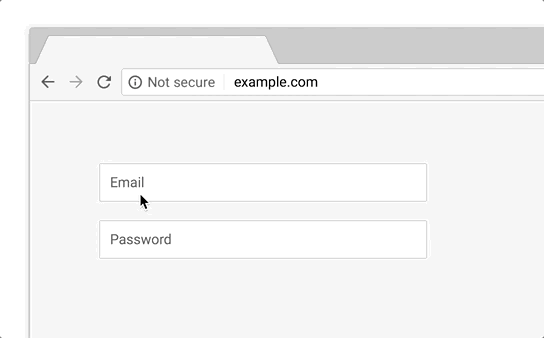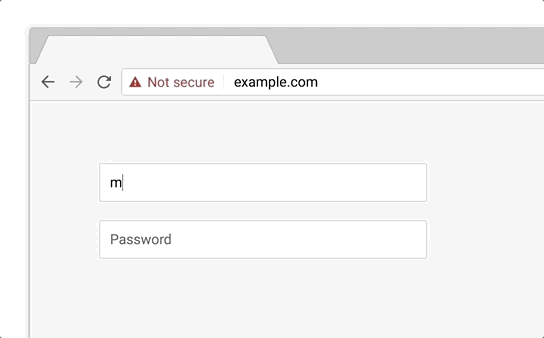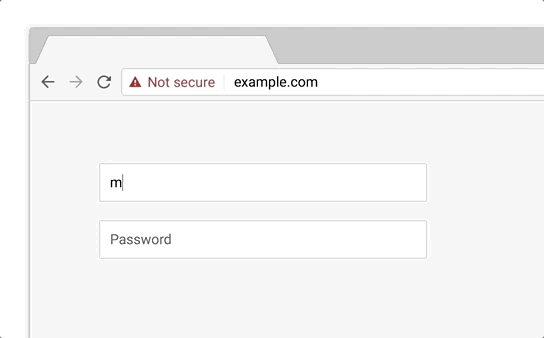
That’s definitely a step in the right direction, but it fails to actually address the problem at the heart of this issue: people don’t understand what HTTPS actually is or what the green padlock actually means.
Google spent a ton of time researching how to handle these visual indicators for connection security. It’s not as if these design choices were made without forethought. Personally, I just think Google didn’t aim quite high enough. I’m painfully aware that humans are dumb. We can’t expect the average internet user to perform feats of mental dexterity to make security judgments and it would be foolish to ask. But we also don’t have to treat internet users as if they’re brain-dead and incapable of any critical thought, either.
In Google’s case, it researched how people reacted to a bunch of different indicators and then opted for the least imperfect ones. I’m neither a psychologist, nor a software engineer but I think that choice does beg the question: could we have taken a tact that tried to educate people about HTTPS and connection security a little more, rather than just relying on what they misunderstand the least?
We need to have a different conversation about HTTPS
The point’s not to wax philosophical about browser design choices, it’s to point out that we – as an industry – need to do more to educate people about what HTTPS is and what HTTPS ISN’T.
It’s too late to put the toothpaste back in the tube. With SSL/TLS certificates available at no cost from a number of vendors, we’re unlikely to see a decline in HTTPS phishing. What needs to happen is we need to have a discussion about that green padlock. Specifically with average internet users about what it actually means.
And then we need to work on a way to better assert website identity. Whether that’s accomplished by improving existing validation processes that are already integrated into our current digital certificate ecosystem, or uncoupling the two and coming up with something entirely new – the status quo isn’t working anymore.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown