Negative Security Indicators: Sign(s) of the Things to Come
Brace yourself. Negative SSL indicators are coming!
We’re now less than 60 days away from witnessing something remarkable. You know what we’re talking about, don’t you? On July 24, Google Chrome, the most popular browser on the planet, will flag every website that doesn’t have SSL/TLS encryption. Some view this move as Google’s last throw of the dice in its crusade against HTTP. However, contrary to this belief, a whole new game is about to kick off. This game will eradicate all the positive security indicators (such as the “secure” text & padlock icon) and will introduce penalizing negative security indicators instead.
So, Why Is Google Doing This?
To understand this, we’d have to time-travel a bit. If you remember, at 2014 Google I/O, Google announced its campaign to encrypt the entire web—HTTPS Everywhere. Since then, Google has repeatedly cracked down on the use of HTTP. As a result of such efforts (and other factors), the usage of HTTPS has reached unprecedented heights. So much so that Google believes that web users should expect HTTPS by default and the sites that are not HTTPS-secured should be reprimanded.
This is what Emily Schechter posted on Chrome’s official blog:
“Users should expect that the web is safe by default, and they’ll be warned when there’s an issue. Since we’ll soon start marking all HTTP pages as “not secure,” we’ll step towards removing Chrome’s positive security indicators so that the default unmarked state is secure.”
To put this all in simple words, websites needed some incentivization from browsers so that the usage of HTTPS could proliferate. But now that HTTPS is close to becoming a standard, Google feels no need for such incentives in the form of positive indicators and will now be turning to negative security indicators instead.
To be fair, Google is doing the right thing with this move. More often than not, the positive indicators are misleading to ordinary users. On seeing the “Secure” text and padlock, most internet users would believe the site to be secure, but it’s only encrypted in reality. This is especially true in case of DV SSL certificate and its visual indicators. DV SSL indicators are too strong and often the main ingredient in a successful phishing scam.
Now that SSL certificates have become free and installing them is pretty straightforward, more and more sites have started using HTTPS-enabled sites to dupe users into phishing scams. Due to the lack of awareness, many fall for it.
Now there are two ways in which this could be curbed: by spreading awareness or by eliminating misleading positive indicators and replacing them with even more obvious negative security indicators. As good as the first option is, it’s mightily difficult to teach everyone about URLs, SSL, encryption, and phishing. Google was always going to go with the second option.
So, No More Padlock?
No (eventually).
Ultimately, Google aims to establish HTTPS as a norm, and the way it’s going to do is not attaching any positive signs pertaining to HTTPS or encryption and penalizing the exceptions (HTTP sites). So, the “Secure” text and the padlock sign will soon be a thing of the past. With the launch of Chrome 69 in September 2018, the “Secure” text will be gone. The next step would be removing the padlock sign that will mark a milestone in establishing HTTPS as a norm.
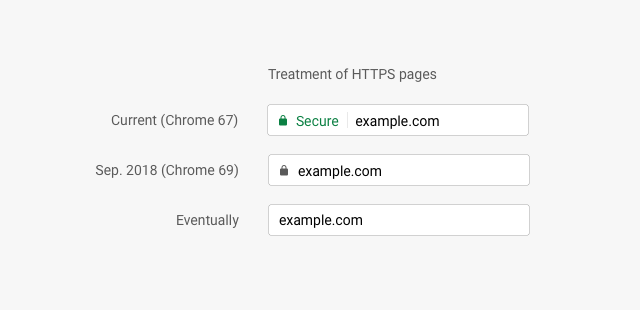
Negative Security Indicators to Get Even More Negative
Chrome 62, released in October 2017, introduced a new negative security indicator that warned users when they typed anything in a non-HTTPS website. Here’s how it looks:
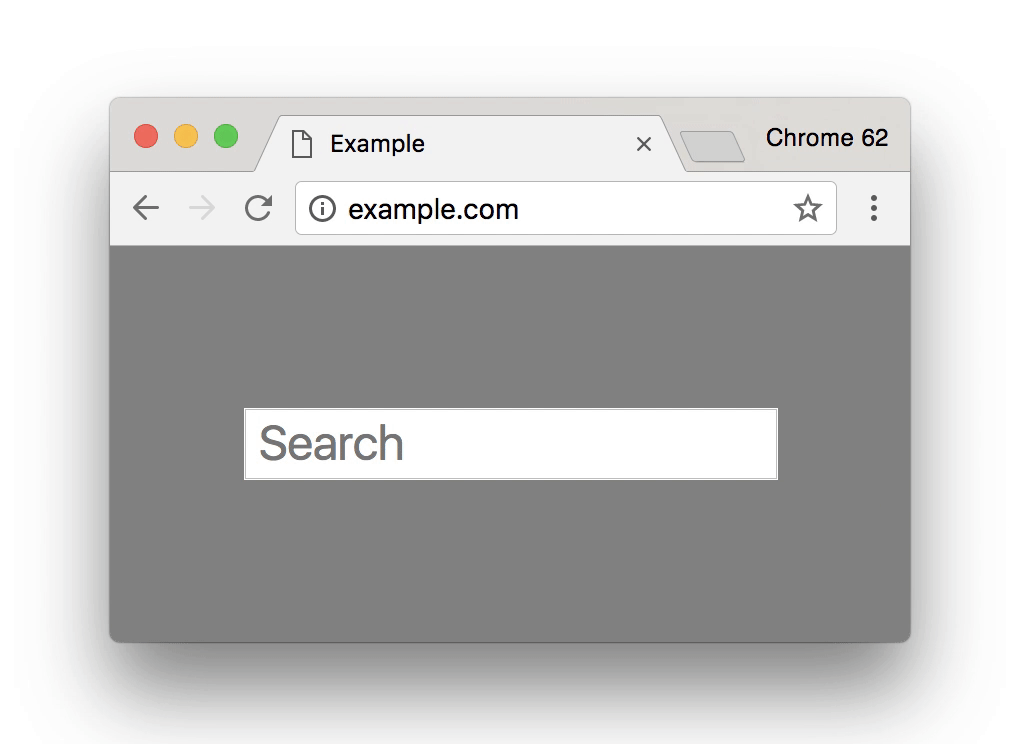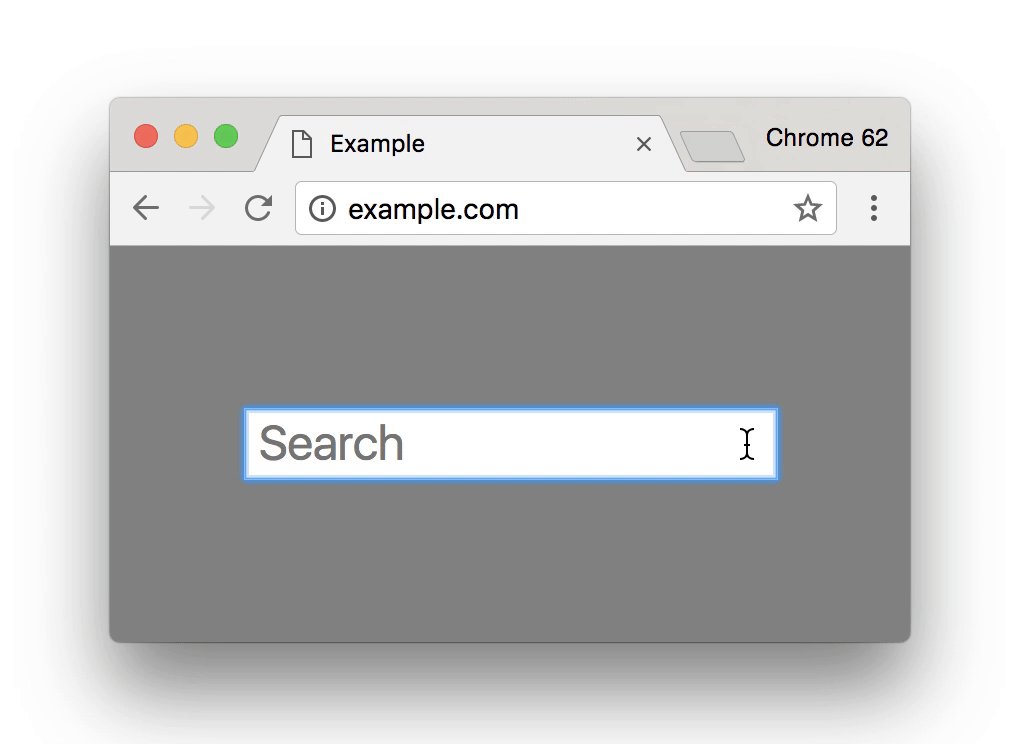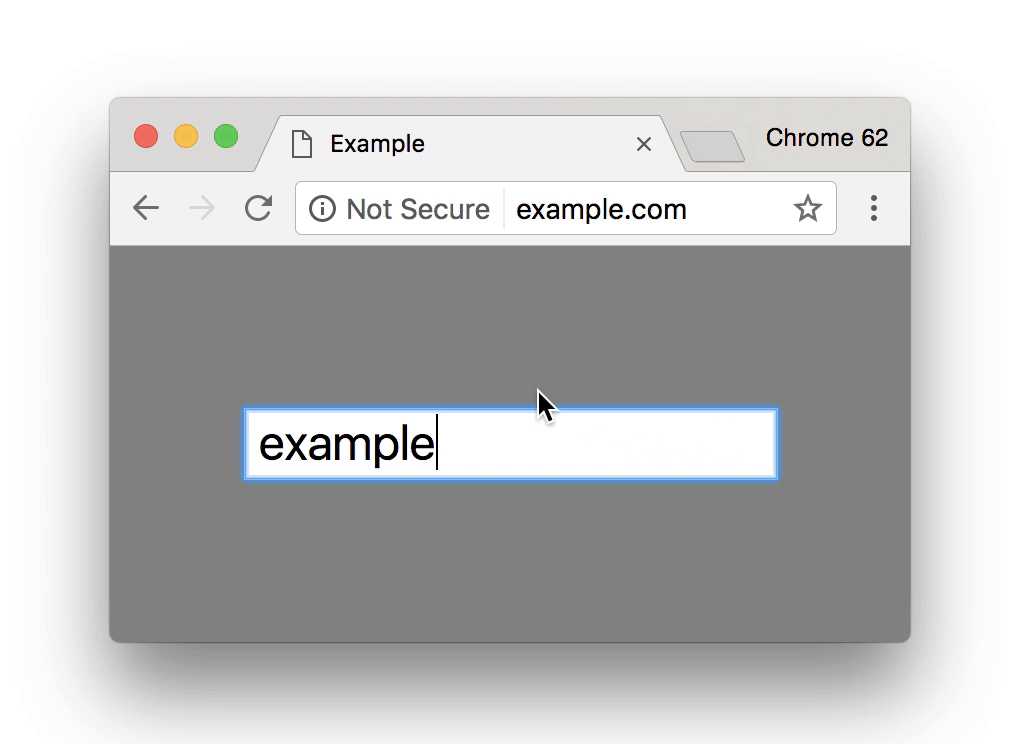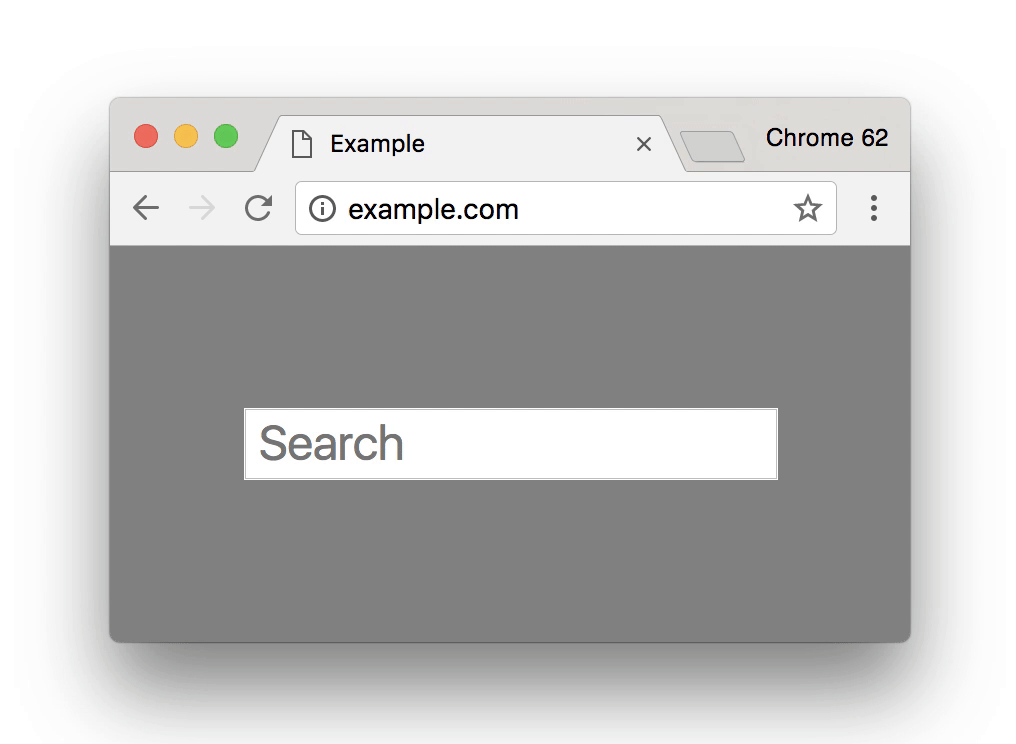
This warning was intended to discourage users from typing anything or giving away their details when the connection isn’t secure. Chrome 70, to be released in October 2018, is set to make this warning even more negative—more noticeable in other terms. After the introduction of Chrome 68, when every HTTP site will be marked as “Not Secure,” Google will need some other negative security indicator when one types in something on an HTTP page as the “Not Secure” sign is there as a default. This will be done with the cunning use of the color red. Here’s how it looks:
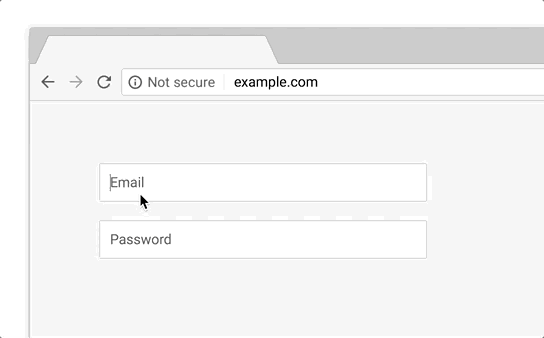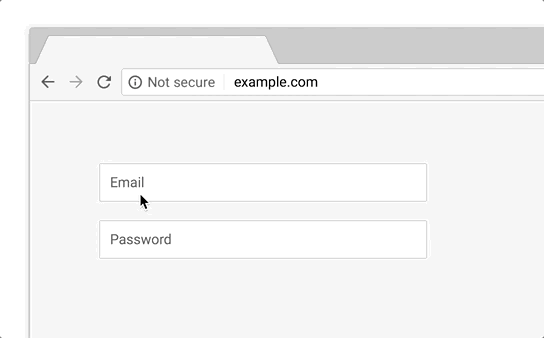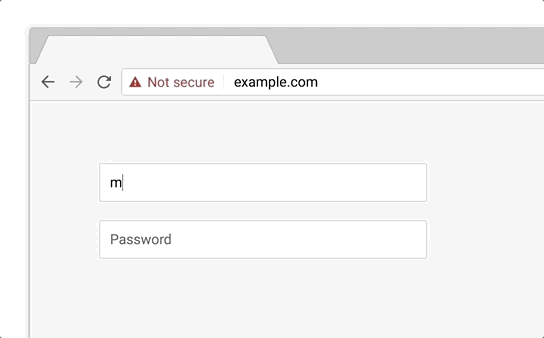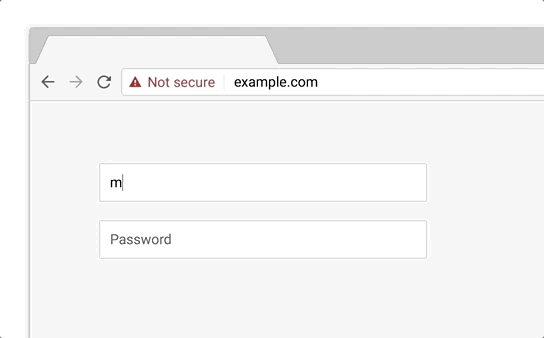
As you can see, the red warning is much angrier than the current one—behold, the power of red.
What Happens to EV Certificates and Green Address Bar?
Let’s just say that the omens don’t look good right now for the EV fans—including me.
First, Google doesn’t see EV SSL certificate as a viable solution to phishing attacks. Emily Schechter, Product Manager, Chrome Security even said at the Loco Moco Sec conference that “EV isn’t a good defense against phishing attacks.” This may seem to be just another statement, but it’s not. Many experts view EV SSL certificates as a good counter-measure against phishing and social engineering attacks. To be fair, the authentication is the only thing that separates an EV cert from the rest. However, Google seems to have other ideas. This perspective of Google—whether right or not—will inevitably get reflected in the upcoming versions of Chrome and you know what? It’s already started.
Google Chrome now incorporates a flag (chrome://flags/#simplify-https-indicator) that allows users to disable the EV indicator—the green address bar. This tells us that the Chrome team is working (or at least thinking) on removing the EV indicator.
I realize that’s a really depressing note to end this section on, so he’s a picture of a hamster in a sweater.

Final Thoughts
Flagging all HTTP sites, removing the secure sign, tinkering with the EV UI…all of this tells us that Google thinks the usage of HTTPS is close to becoming a norm. In other words, Google, in its eyes, has succeeded in its “Encryption Everywhere” campaign. That’s why it no longer feels the need to incentivize sites to propagate HTTPS. Instead, it wants to treat HTTP sites as exceptions and reprimand them with negative security indicators.
Another thing that Google wants to focus upon is the user experience. As most internet users feel safe seeing the “Secure” sign in Chrome, many fall prey to scams and frauds as many phishers now hide behind the curtain of free and DV SSL/TLS certs.
To counter such attempts, many see high assurance certs (OV and EV) as a solution because of the validation process that they require. However, Google—as it seems right now—doesn’t seem to be agreeing with it. Even the EV certs, the ones that require a rigorous validation process, are not good enough for Google against phishing scams. So, if EV certs are not good enough, no SSL cert is. Therefore, I’m assuming that Google sees SSL certs only as means to provide encrypted connections, nothing else. On the grounds of this, in the future, Google *could* treat all encrypted sites equally—whether secured through DV, OV or EV.
Needless to say, such radical changes will have some serious impact in the SSL industry. However, we can only sit on the sidelines and play the guessing game. The real game is in the hands of the mighty Google, and it can change its rules anytime it wants!





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown