Thousands of Android Devices Shipped with their Debug Port Exposed
The issue dates back to February, but appeared again last week
An old Android bug, ADB.Miner, which was originally spotted by Qihoo360 Netlab back in February is finding new life thanks to a vendor oversight.
The bug, or more specifically, the worm is a cryptocurrency miner that takes advantage of the Android Debug Bridge (ADB), a baked-in feature that allows the vendor to troubleshoot faulty devices.
Typically, on Android devices the ADB feature is disabled by default, meaning that a user would have to manually connect it during a USB connection. The problem is that some vendors are shipping Android devices with the feature still turned on.
What complicates this even more is that the ADB also supports WiFi connections, which means that many device owners may not even realize it but their phone is completely accessible to remote connections made via the ADB interface, which is typically accessible via TCP port 5555.
It gets better, because ADB is a troubleshooting mechanism it grants access to some pretty powerful tools, including a Unix shell.
This is how the original worm, ADB.Miner, originally spread back in February. It would gain access to a device via ADB, use the Unix shell to install the miner and then scan for new devices to infect.
Last week, in a post on Medium, researcher Kevin Beaumont reminded everyone about the original issue while warning that thousands of devices are currently exposed online, with the highest concentration in China.
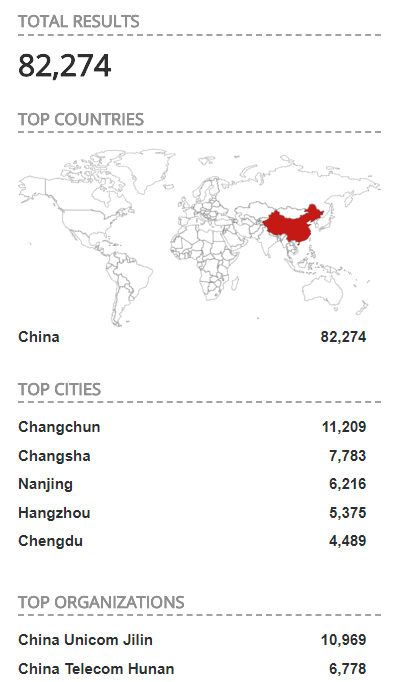
In terms of raw numbers I can see nearly ten thousand unique IP addresses scanning in any 24 hour window, and over a hundred thousand IP addresses scanning each 30 days. It is worth keeping in mind that because of Network Address Translation and dynamic IP reservations it is difficult to know the exact number of devices. But it is safe to say: “a lot”.
That’s not good, and the average internet user isn’t going to know how to check whether their Debug port is exposed. Fortunately, we can help with that.
How to turn off Android Debug Bridge
You’re going to need to go into the developer tools and make sure that you’ve got ADB toggled off. Here’s how you do it. For Android 4.2 and beyond, the Developer Tools are hidden, here’s how to make them viewable.
- Go to Settings
- Select About phone
- Tap the Build Number seven times
- Return to the previous screen, Developer Tools should display at the bottom.
I realize that sounds like some crazy cheat code video game stuff, but read the source material if you don’t believe me.
Ok, now that you can view Developer Tools, here’s what you need to do:
- Select Developer Options
- Make sure that USB debugging is disabled
Boom. Done. Much like your fly, it is unbecoming to leave your Debug port open. Now you can make sure you haven’t.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (1 votes, average: 4.00 out of 5)
(1 votes, average: 4.00 out of 5)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown