Automotive Cyber Security: A Crash Course on Protecting Cars Against Hackers
Modern vehicles have up to 50 different automotive IoT devices (computers) hackers can attack. That’s why vehicle cybersecurity is critical for automobile safety…
Modern cars have dozens of computers on board, and they’re not just for running GPS or playing music. Computers monitor and control nearly every system on your vehicle, including steering, brakes, and the engine itself. This is why automotive cyber security is essential.
If a vehicle’s computer systems aren’t properly protected, hackers can steal data or even take control of the vehicle. As you can imagine, that makes automotive cyber security a major concern for consumers, auto companies, and OEMs alike.
But what is there to know about automotive cyber security? We’ll explore what cybersecurity in the automotive industry entails and what the biggest threats are to automotive IoT and connected vehicles. We’ll also share some insights from a recent webinar by Sectigo and Mentor Graphics on how to protect connected vehicles from emerging cybersecurity threats.
Let’s hash it out.
Why Automotive Cyber Security Is Such A Big Deal
As we already mentioned, modern vehicles rely heavily on computer systems to monitor and control the vehicles different systems. If an auto’s technology isn’t secure, hackers can steal data, such as tracking your location information via GPS.
But, it gets a lot scarier: hackers can even run commands, forcing a vehicle to obey the hacker instead of the driver. While getting your data stolen is a disconcerting thought, the idea that a hacker could take control of your car is outright terrifying. Hackers can use commands to activate or deactivate different features like your A/C and windshield wipers, or to control your steering, brakes, or engine.
Want to see a demonstration showing how hackers could control a vehicle? Check out this video of cybersecurity researchers remotely hacking a Jeep Cherokee while someone was driving it on the highway:
Once you’ve seen that demonstration, it’s easy to see why this is such a big area of concern. Especially considering that these vulnerabilities don’t extend to only one brand — they also affect BMW, Tesla, Volkswagen… Basically, if you drive it and it has Internet of Things (IoT) devices (which virtually all modern vehicles do) it’s potentially at risk to cybersecurity threats.
Attacks Against Cars Nearly Doubled in One Year
Upstream Security’s 2020 Automotive Cybersecurity Report shows that the past decade has demonstrated a marked increase in automotive cyber incidents. From 2018 to 2019, there was a 99% increase in automotive cyber security incidents. Now, keep in mind that their AutoThreat Intelligence data covers both physical and remote attacks, although 82% of the attacks in 2019 involved short- and long-range remote attacks.
OK, great, so what’s the solution? I’m glad you asked…
An Overview of Automotive Cyber Security
When we talk about automotive cyber security or vehicle cybersecurity, what exactly are we referring to? The National Highway Traffic Safety Administration (NHTSA) defines it as the following:
Cybersecurity, within the context of road vehicles, is the protection of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation.”
That’s a lot to digest. Let’s break it down into plain English!
Basically, when we say automotive cyber security, we’re talking about protecting the in-vehicle computer systems on automobiles from cybercriminals and other unauthorized individuals who might be up to no good.
Vehicle cybersecurity means implementing proven defenses to:
- Keep anyone from stealing your data (like your GPS location info or data that’s one your smartphone you connected to the Bluetooth speaker),
- Stop hackers from being able to control or manipulate your vehicle (for example, disabling the burglar alarm or tricking the collision avoidance system), and
- Ensure nobody can damage your vehicle (for example, resetting your oil change counter so you don’t get your oil changed on time).
According to the Alliance of Automobile Manufacturers, there are seven critical areas in cybersecurity for connected vehicles:
- Security by design
- Risk assessment and management
- Threat detection and protection
- Incident response
- Collaboration and engagement with third parties
- Governance
- Awareness and training
So, how do you address some of these concerns within your own environment?
A 3-Part Plan for Automotive Cybersecurity
We mentioned earlier that one of our certificate authority (CA) partners, Sectigo, teamed up with Mentor Graphics, a Siemens Business, to host a webinar on how to protect connected vehicles from emerging cybersecurity threats. The webinar, which was presented by Dr. Ahmed Majeed Khan (Mentor) and Alan Grau (Sectigo) focused on methods auto manufacturers could use to protect connected vehicles from modern cybersecurity threats.
We’re borrowing this from Khan and Grau’s presentation, because we think it’s a super-simple way to think about vehicle cybersecurity. Khan, senior development engineering manager at Mentor, says that automotive cyber security boils down to three areas:
- Authentication and Access Control — Who is allowed to do things, and what do they have access to do.
- Protection from External Attacks — Preventing unauthorized controls and malware, protecting data, protecting communications, etc.
- Detection & Incident Response — Identifying, reporting, and responding to attacks and threats.
This is where having a multi-layer security approach comes in handy. This should include mechanisms that secure internal and external communications, use embedded intrusion detection and prevention systems, facilitate authentication, secure system updates, and secure the operating system.
Automotive Cyber Attack Methods
So, if an actor wants to take control of a vehicle or its systems, what do they need to do? First, they must find a way to break into the car’s systems. Doing this gives them an opportunity to compromise an electronic control unit (ECU) (that’s the automotive industry term for an automotive IoT device or computer) and to find a feature that they can compromise.
Khan called out several areas that we should be concerned with regarding cyber attack methods:
- Direct physical attacks. These types of attacks occur when someone has direct physical access to a vehicle, such as when it’s at a shop for repair or someone breaks into it. These attacks frequently involve use of onboard vehicle networks, ports, and various connectors. An attacker could install hardware or software that easily gives them control of your vehicle later (when you’re using it).
- Indirect physical vulnerabilities. Unlike the first, this type of attack requires some type of medium to carry out the attack. These mediums can include firmware updates, the use of SD cards and USB devices, etc. For example, an attacker could get a vehicle owner to plug in an MP3 player that’s infected with malware.
- Wireless vulnerabilities. This can include everything from short-range methods like Wi-Fi and Bluetooth attacks to long-range mechanisms that involve the use of GPS or cellular technologies. With these attacks, the hacker doesn’t need any type of physical access to your car.
- Sensor fooling vulnerabilities. While there aren’t any documented threats of this type as of this time, that doesn’t mean that sensors aren’t exploitable, says Khan.
After a hacker has access to the virtual insides of your vehicle, without any internal defensive measures in place, they’re essentially off to the races and can wreak havoc however they choose.
This is where strong automotive cyber security comes into play — both keeping hackers out of vehicle systems, and blocking them from causing problems if they do get in
How to Build Security into Connected Vehicles
There are many different security solutions that need to be built into connected vehicles to increase security, and to cover all three areas of automotive cyber security that Khan spoke to earlier. Grau, vice president of IoT and embedded solutions at Sectigo, says:
Security is all about defense in depth, multiple layers of protection. If one aspect of the security solution breaks down, you need to have other aspects coming into play.”
Effective automotive security is about:
- Integrating the right solutions. Integrating an embedded firewall can help to identify and report threats.
- Protecting communications. This includes external communications to a vehicle, as well communications within the vehicle itself and communication between it and other vehicles
- Authenticating communications. This entails knowing who is communicating with a vehicle and blocking communication from unauthorized devices.
- Encrypting data. Encrypting data helps to protect privacy.
Improve Your Intrusion Detection & Response: Implement an Embedded Firewall
Among the most important solutions for connected car security is an embedded firewall to block unauthorized communication and commands from reaching the onboard computers (ECUs). An effective firewall is one that can integrate with real time operating systems (RTOS) and deploy via gateway ECUs (to limit and filter external communications to the vehicle, communications within the vehicle, and vehicle-to-vehicle communications) and/or via endpoint ECUs that manage critical functions.
A firewall has a pretty simple job: let through authorized communication, while blocking unauthorized communication. But don’t mistake a firewall for automotive cyber security with one that’s used on your laptop or enterprise network. A connected vehicle’s embedded firewall is a highly configurable and specialized solution that’s designed to:
- Integrate with the existing communication capabilities,
- Integrate with any type of ECUs via portable source code,
- Offer filtering and configurability options, and
- Support real time operating systems (RTOS) and run in AUTOSAR environments.
But why is such a comprehensive tool necessary?
Grau says that many attacks start by an actor sending malicious packets to the target vehicle:
If we can control that and ensure that certain types of packets are not allowed to be received or forwarded into the connected car, we can block many attacks before they even really get that first initial toehold in the vehicle. We can control what ports and protocols the vehicle receives messages on. We can control what IP addresses are sending data to the vehicle. And we can also then report any suspicious activity. If we start to get a flood of packets from a specific IP address, or other activity that looks suspicious, we can report that.”
Attackers start their attacks by poking and prodding a vehicle’s defenses to see what messages or packets they can send, what gets through, and monitoring the results. It often boils down to simple trial and error. So, if there’s a firewall in place that’s not only identifying but also reporting on such activity to a vehicle operations center, Grau says, then you can act accordingly to block the attack.
Integrate Certificate-Based Safeguards to Authenticate and Secure Communications
The next important part here is to secure and authenticate communication sessions to, between, and within vehicle systems. This is done through the use of public key infrastructure (PKI) — though it’s different in this case. We’ll explain why momentarily.
In general, authentication is an integral component to cybersecurity. This is true regardless of whether you’re talking about automotive cyber security or just cybersecurity for other industries. When you can verify that the individual or system that’s communicating with you is legitimate, it means that you’re less likely to fall for scams and your defense mechanisms can weed out fraudulent communications.
Using Digital Certificates for Authentication and Encryption
As you likely know, SSL/TLS certificates are used to facilitate secure, encrypted connections between parties (traditionally clients and browsers). In automotive cyber security, securing communications via the use of secure protocols offers several security benefits:
- Encrypts communication between devices on the vehicle
- Encrypts communication between the vehicle and “home” (for example, the manufacturer)
- Authenticates devices so computers on the vehicle only accept commands from authorized devices
- Authenticates software updates using code signing certificates so that the manufacturer is the only one who can push updates to the vehicle
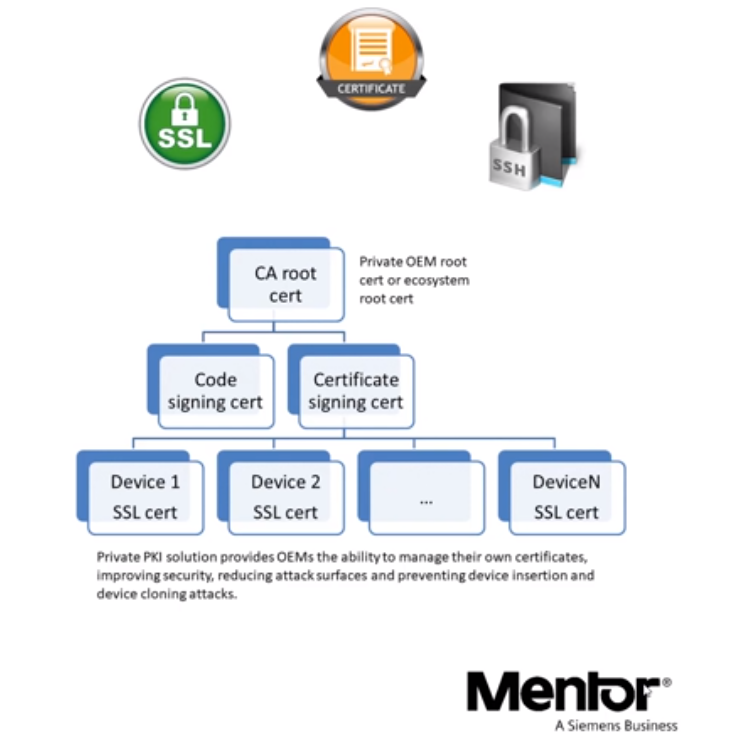
Why Private PKI is Needed for Vehicle Cybersecurity
So, when we’re talking about TLS, for example, we’re typically talking about PKI in the traditional sense. This means the use of public/private key pairs via SSL/TLS certificates, which play a role at each endpoint. It also encompasses another type of PKI certificate, known as a code signing certificate, can help you validate software for secure boots and updates.
But in automotive cybersecurity, we’re usually not using the public ecosystem that’s used for TLS certificates for websites. In this case, we’re talking about purpose-built PKI for IoT vendors for private ecosystems and shared ecosystems across multiple vendors. Specifically, this is talking about those ecosystems for vehicle manufacturers and OEMs.
Simply put, publicly trusted PKI systems aren’t built to meet the needs of automotive cyber security. That’s why automotive vendors use private PKI solutions.
To use public key encryption effectively within a private IoT ecosystem (which is what cars are), you need to be able to manage your certificates effectively. This entails:
- Generating SSL/TLS certificates and keys using appropriate entropy (random bit generation).
- Managing those certificates and keys so that you know what you have, when they expire, and implementing automation for high-speed issuance. Managing your device certificates and keys is simplified with an embedded PKI client on each device.
- Safely storing those private keys to keep them out of the reach of hackers and cybercriminals. This can be done through the use of hardware storage management (HMS) tools.
Facilitate Secure Boot and Firmware Updates
Recalls and software issues are something no manufacturer wants to deal with. This sentiment extends to connected vehicles as well. This is where over-the-air (OTA) firmware updates and the use of secure boot can come in handy.
OTA updates are the modern way of delivering operational and security software and firmware updates — you can deliver them without ever physically needing to connect a device to the vehicle. These digital updates are not only more convenient, but they also look good for your bottom line. According to data from a study by IHS Automotive, OTA software update events are expected to help auto manufacturers globally realize $35 billion in cost savings by 2022.
The purpose of secure boot is to verify software integrity by analyzing every device’s bootloader, microkernel, and code to ensure that it:
- Came from an authorized entity,
- Hasn’t been tampered with, and
- Doesn’t contain any malicious code.
For example, it can help to ensure that no one has tampered with the firmware on a vehicle’s ECU.
As OTA gains a stronger foothold within the automotive industry, if firmware updates serve as an avenue that’s left unprotected, it essentially serves as a playground for hackers. Automotive security needs to be airtight — a corrupt OTA update can result in your customers getting killed should a hacker take control of their vehicles. This is why your connected vehicles need strong automotive cybersecurity solutions that facilitate these secure updates and secure boot.
Compliance: Where Automotive Cyber Security and Privacy Regulations Come Together
Compliance is a pretty big deal. We can talk about it from an ethical sense, but, really, we know that compliance as a priority often boils down to the bottom line for a lot of businesses — it’s about avoiding fines, penalties, and potential lawsuits.
National government and regulatory bodies across the globe have called for standards and regulations in terms of both safety and privacy. For example, in the U.S., the federal government proposed cybersecurity standards for automobiles — think of the SPY Car Act of 2017 (S.2182) and the SELF DRIVE Act (H.R. 3388).
The SPY Car Act aims to “protect consumers from security and privacy threats to their motor vehicles, and for other purposes.” Basically, any OEM or auto manufacturer would need to get express consent of the vehicle owner or lessee to use any personal driving information that’s collected. Furthermore, they’d need to abide by the National Institute of Standards and Technology’s (NIST) cybersecurity framework to ensure that critical cybersecurity infrastructure is in place.
The SELF DRIVE Act aims to ensure the safety of “highly automated vehicles as it relates to design, construction, and performance, by encouraging the testing and deployment of such vehicles.” It also prohibits OEMs from selling or exhibiting vehicles with any automation functionalities if they don’t have cybersecurity plans that meet specific requirements.
As outlined under Section 5 “§ 30130. Cybersecurity of automated driving systems,” there must be:
- A written cybersecurity plan in place that outlines detection and mitigation processes for cyber attacks and other unauthorized intrusions (including “false and spurious messages and malicious vehicle control commands”).
- Someone who is identified as managing cybersecurity within the manufacturer or OEM to limit access to automated driving systems. This individual must also manage the implementation of employee training and processes relating to any related policies.
But this still leaves the question of not only who owns the data, but also who’s responsible for protecting it? The European Union’s Parliament called for the development of regulations relating to access to car data, and Canada’s Digital Privacy Law also speaks to data privacy concerns as well. The European Data Protection Board also has guidelines relating to the processing of personal data of connected vehicles and mobility related applications that’s open to feedback until May 2020.
Final Thoughts
I think Dr. Khan said it best at the end of his presentation: “The automotive industry must prove itself trustworthy for humans to trust connected cars.” Automotive cyber security needs to be a priority for every OEM — it’s a multi-layered approach that can’t be cobbled together at the last minute. Any solutions that are used to authenticate and secure communications needs to be flexible and capable of working via both private and shared ecosystems. And it needs to not only identify but also report fraudulent communications and attacks.
Releasing connected vehicles to the market without effective security mechanisms in place is like firing a gun without taking the time to aim. It’s dangerous, it’s foolish, and someone’s bound to get hurt. Furthermore, it’s going to wind up costing your company a lot at the end of the day.




































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown