Browser Watch: Tracking SSL Changes in Chrome 54
Chrome 54 Features Better Messaging For Server Admins.
Google Chrome 54 released last week, and like every new version of Chrome, there have been some changes to Chrome’s SSL/TLS and networking capabilities and features.
The most notable changes in Chrome 54 are expanded information in the Security panel in Developer Tools, along with fixes for two problematic bugs in macOS Sierra.
Improved Messaging In Developer Tools
Lots of useful information about a site’s SSL configuration lives in the Security panel in Chrome’s Developer Tools. This is where you must now go for any serious information after Chrome removed the Connection panel (which was accessible by clicking the lock icon in the address bar) a few versions ago.
With the release of Chrome 54, the Security panel now provides additional information about bad SSL configurations, giving server admins a helping hand to improve their site’s SSL security.
The Security panel will specifically call out weak ciphers and blocked mixed content in grey info bullets, as seen in the screenshot below.
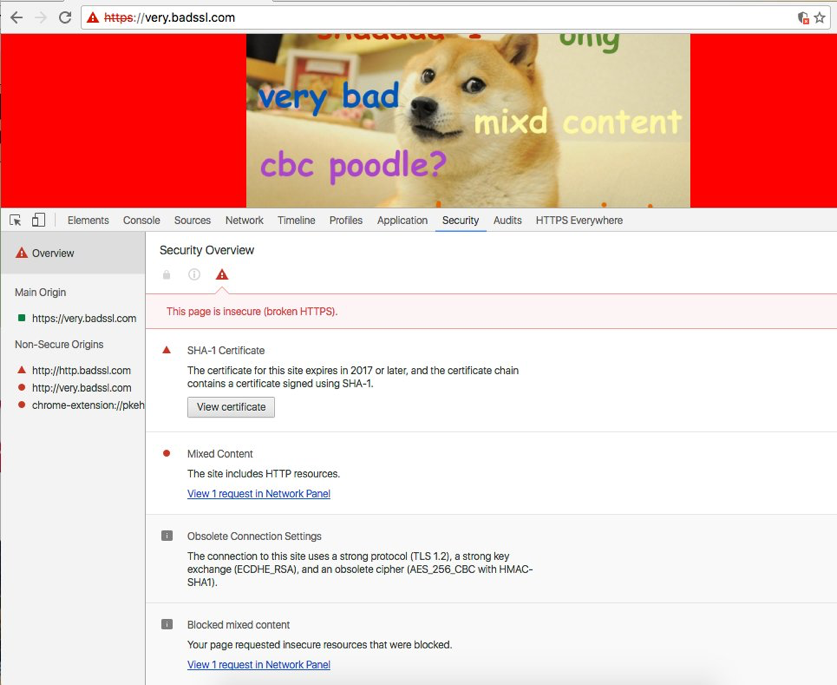
Another small, but helpful improvement has been made to the full-page interstitial errors that appear for major problems with a site’s SSL configuration (expired certificate, obsolete protocol, etc). A “Learn More” link to a support page about how to “Fix connection errors” has been added to these Interstitial error pages to provide a bit more context to people who encounter them.
Certificate Chain Fetching Bug Fixed In Sierra
Google Chrome has a functionality known as AIA fetching to retrieve the needed intermediate certificates when a server has not been properly configured to provide them. This allows Chrome to successfully make an HTTPS connection to a site and avoids a “Your connection is not private” interstitial error.
Changes to OS functions in macOS X Sierra broke this functionality, causing a four-fold increase in errors related to missing/incorrect certificate chains.
Chrome 54 for Mac ships with a fix for this bug that restores AIA fetching. Chrome’s team refers to this as a “hack” because it will introduce some performance penalties and they are still looking for a proper solution.
New Certificate Transparency Logs
Certificate Transparency allows Certificate Authorities (CAs) to publically log certificates, providing proof of their issuance and allowing third-parties to audit their activity. In just a few short years Certificate Transparency has become one of the most important tools for strengthening the CA model and closing the gap on CA malfeasance.
As a technical mechanism, Certificate Transparency is quite complex. It is important to have a variety of “logs” where certificates can be publicly recorded in order to insure the accuracy, reliability, and diversity of the system.
In Chrome 54 two new logs have been approved, and are now accepted as valid sources for CT information. These logs are operated by WoSign and StartCom, and both are public logs that will provide free logging of any certificates issued from roots in Mozilla’s CA Program. These two join a short list of internationally hosted logs.
These logs are also now indexed by crt.sh, a Certificate Transparency search engine operated by Comodo.
Post-Quantum Cipher Support
CECPQ1 is Google’s first attempt at designing a cipher suite that is resistant to quantum computing. Google originally launched this cipher a few months ago in Canary, and has now enabled it in a select number of clients in the stable release of Chrome 54.
This is primarily a research experiment that is collecting real world data for future cipher designs. Unless you are looking out for it, you will likely never notice its existence.
Only a few websites are configured to use this cipher. If you want to see if your client has support enabled, visit play.google.com and look for “CECPQ1” listed as the Key Exchange method.
Certificate Viewer Bug Fixed in Sierra
Sierra has another bug, this one affecting the OS’ Certificate Viewer Window where you can view the certificate’s details. It currently has a bug where the Window’s height is set higher than the screen height and it cannot be used.
Chrome has another “hack” fix for this one that should restore functionality while a more permanent solution is sought.
HTTP/0.9 Disabled Over Non-Default Ports
At this point, HTTP/0.9 is absolutely ancient. While the internet is busy migrating to HTTP/2, there are still some legacy and consumer networking devices holding onto the past.
In order to encourage a timely move away from HTTP/0.9, and also reduce compatibility issues some users are experiencing, HTTP/0.9 will only work over default ports (80 and 443) in Chrome 54.
Chrome plans on removing support for HTTP/0.9 altogether within a few versions.
Wrap Up
That’s is for Chrome 54! Lots of small changes this release.
If Chrome Canary is an accurate indicator, we will see some bigger changes coming in Chrome 55/56 – including the addition of a “Secure” indicator next to HTTPS sites, which Google designed based on new user research conducted earlier this year.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown