Mozilla expanding its DNS-over-HTTPS test to Firefox release channel
Encrypted DNS requests can now be made from Firefox, here’s how to do it.
In the ongoing debate between DNS-over-HTTPS and DNS-over-TLS, Mozilla has just given a huge win to the DoH camp. Following its decision to test DNS-over-HTTPS in a Limited Shield study on its advance Firefox Nightly browser in June, Mozilla is now pushing that test on to its release channel in the United States.
We covered the difference between DNS-over-TLS and DNS-over-HTTPS about a month ago, but today we’ll cover that again, we’ll talk a little bit about how DNS-over-HTTPS works and then I’ll show you how to activate DNS-over-HTTPS on Firefox so you can start encrypting your own DNS requests.
Let’s hash it out.
 What is DNS-over-HTTPS?
What is DNS-over-HTTPS?
As we mentioned in the previous article, you don’t get the full benefit of HTTPS if you’re not encrypting your DNS requests. Sure, no one can see specifically what it is you’re viewing on a given website, but thanks to the DNS requests your browser made – unencrypted requests – it is possible to at least discern what site it is you’re on.
As privacy becomes more and more of a priority, it’s understandable why encrypting DNS requests would be desirable.
There are two ways to do this, DNS-over-TLS and DNS-over-HTTPS. These are not interchangeable terms. While they are both extremely similar, there exists a very large distinction that has proven to be quite controversial: the port used.
DNS-over-HTTPS sends the DNS requests via port 443, the standard port for HTTPS connections. DNS-over-TLS has its own dedicated port, Port 853. There are other differences, DNS-over-HTTPS uses HTTPS and HTTP/2 to connect while DNS-over-TLS layers TLS over a TCP connection.
But the important distinction is the port. Because as attractive as a dedicated port sounds, it’s a double-edged sword – it also means the requests are easier to block.
Activists support DNS-over-HTTPS because it gives greater privacy to internet users in countries without a free internet. Others in the tech industry prioritize the best possible design over social concerns.
It seems as if Mozilla is in the first camp.
How does DNS-over-HTTPS work?
Mozilla’s study is using Cloudflare’s DNS service to encrypt requests and responses for any DNS queries made. It’s relatively simple, the application, browser, OS, IoT device or router making the query connects to a Cloudflare DNS-over-HTTPS endpoint and the call is encrypted.
But there are some concerns about this, and it has to do with the Content Delivery Networks that many sites use to improve performance for users in various geographical regions.
Content Delivery Networks (CDNs) provide localized DNS responses depending on where you are in the network, with the goal being to send you to a host which is near you on the network and therefore will give you the best performance. However, because of the way that Cloudflare resolves names [technical note: it’s a centralized resolver without EDNS Client Subnet], this process works less well when you are using [DNS-over-HTTPS] with Firefox.
What that means is that DNS-over-HTTPS could add latency to a connection, which is definitely not desirable. Early on, SSL/TLS could add latency to connections at scale, and frankly you still hear some people bring that up even though it hasn’t really been an issue for years. But noting that, Mozilla is being cautious rolling this feature out for fear of poisoning the well.
This is something we can test. We are going to study the total time it takes to get a response from the resolver and fetch a web page. To do that, we’re working with Akamai to help us understand more about the performance impact. Firefox users enrolled in the study will automatically fetch data once a day from four test web pages hosted by Akamai, collect information about how long it took to look up DNS and then send that performance information to Firefox engineers for analysis. These test pages aren’t ones that the user would automatically retrieve and just contain dummy content.
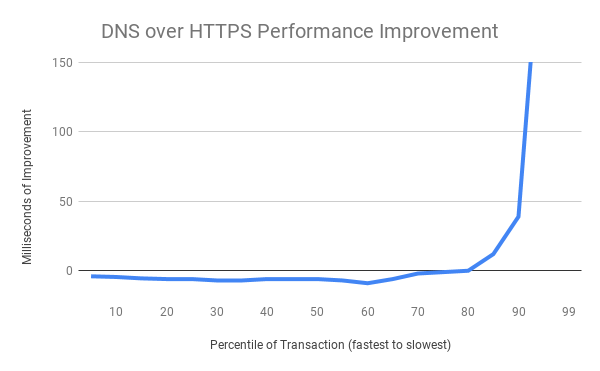
So far, Mozilla has been happy with the early returns, calling them “very positive.” During July of 2018 about 25,000 users opted into the test, which generated over 1,000,000,000 DNS-over-HTTPS transactions.
![]()
The slowest 20% of DNS exchanges are radically improved (improvements of several seconds are truncated for chart formatting reasons at the extreme), while the majority of exchanges exhibit a small tolerable amount of overhead when using a cloud service. This is a good result.
Now the feature is headed to the Firefox release channel, where Mozilla will continue the test. A soft rollout will begin this week and continue into next. The test will continue to provide in-browser notifications to keep participants informed.
While Mozilla has only been working with Cloudflare so far, it hopes to expand its test to other DNS providers in the near future.
How to enable DNS-over-HTTPS on Mozilla Firefox
While the DNS-over-HTTPS test is currently limited to a select group of users, it is possible to activate the feature by tinkering with your settings. Here’s how to do it.
Step One: Type About:Config into the address bar.

Note: If this is your first time, you’ll need to click through the disclaimer. Don’t worry, we’re not going to break your browser or void your warranty.
Step Two: You’ll need to pull up Firefox’s Trusted Recursive Resolver, this is the DNS-over-HTTPS endpoint. To do this, type network.trr into the search field.
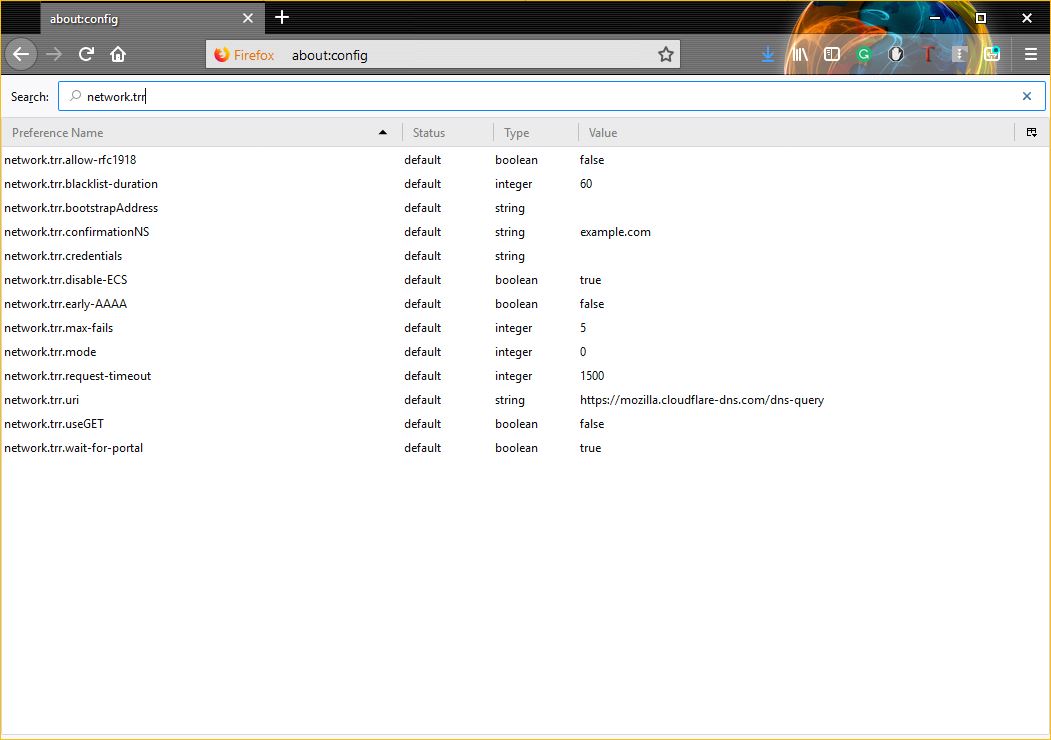
Step Three: Double-click on network.trr.mode, then enter 2 in the field and click OK.
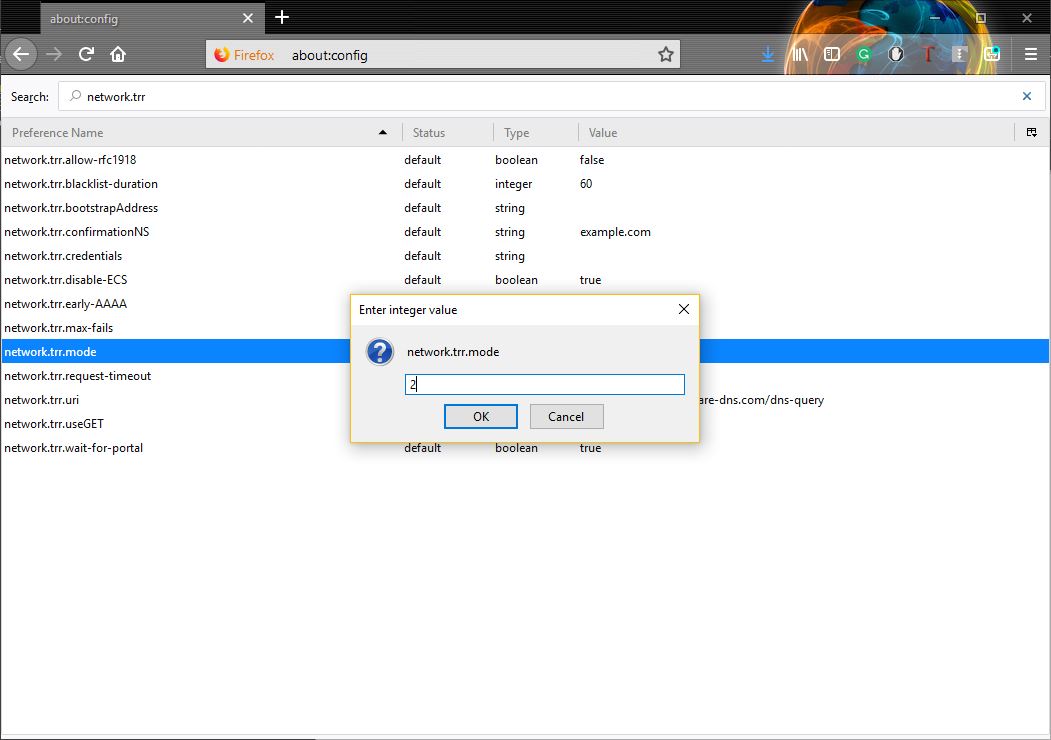
Ok, now DNS-over-HTTPS is activated, but you’re still going to need to configure one more thing: the end-point.
Step Four: Back on the network.trr results page, select network.trr.uri and set it to: https://mozilla.cloudflare-dns.com/dns-query
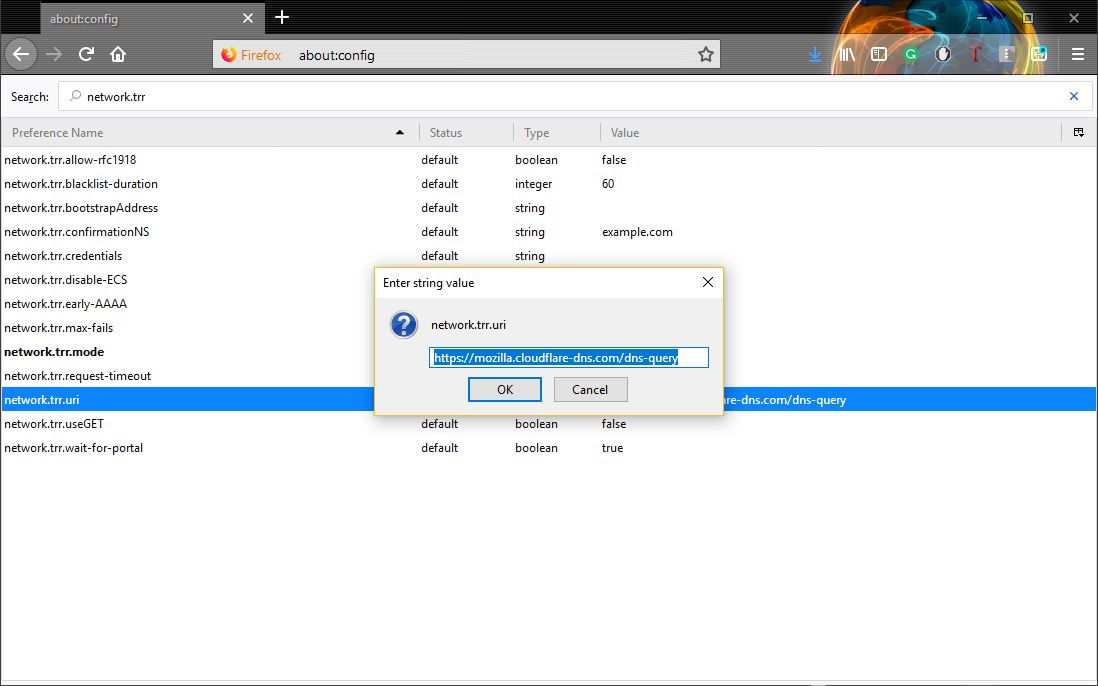
If you would like to test and make sure that everything is working properly, head over to Cloudflare’s Browsing Experience Security Check page and click the Check my Browser button. You should see a beautiful green check mark indicating that you’re using Secure DNS and TLS 1.3.
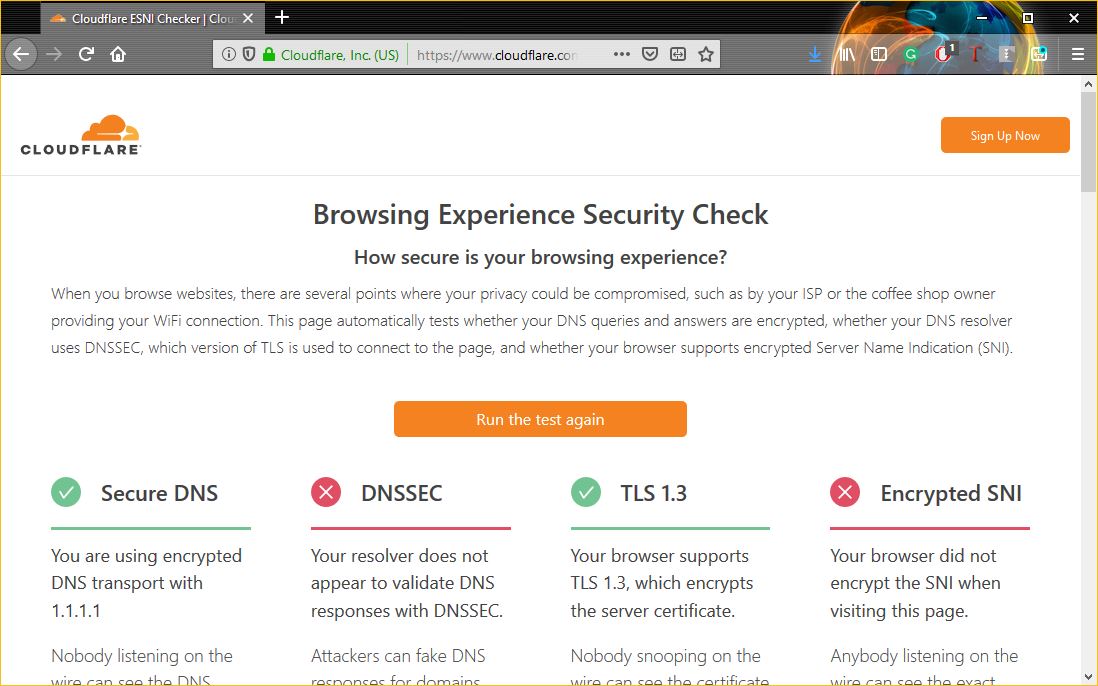
Congratulations, you’re getting the most out of HTTPS now.
As always, leave any comments or questions below…





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown