What is the difference between DNS over TLS & DNS over HTTPS?
While they sound like the same thing, there’s one major difference and it’s causing a heated debate.
DNS over TLS (DoT) and DNS over HTTPS (DoH) sound like they would be interchangeable terms for the same thing. And they do actually accomplish the same thing – encrypting DNS requests – but there’s one big difference: the port they use.
And while it may seem silly for something that sounds so simple to have created two totally divided camps with deeply entrenched beliefs about which is better–the stakes are high. One side is more socially conscious, more user-oriented, their primary interest is privacy and human rights. On the other side is a more pragmatic group that even includes one of the architects of DNS, who make the case that network admins need to be able to see and analyze DNS activity.
There’s a lot to unpack here, but it’s worth delving into the details to give you a better idea about the difference between DNS over TLS & DNS over HTTPS—and why this is an important discussion.
So without first ado, let’s hash it out…
What is DNS? Why does it need TLS or HTTPS?

DNS stands for Domain Name System. The best comparison, and also the most cliché, is that of a phone book. When most people surf the web, they don’t type in the actual IP address—they input the Uniform Resource Locator (URL). The DNS server takes that URL and finds the IP address it resolves to.
For instance, when you want to visit The SSL Store, you type in thesslstore.com, the DNS server will take that URL and find the IP address associated with it, in our case it’s 107.23.230.173. But asking people to remember that would be pointless, hence the ubiquity of the URL (which Google is trying to kill).
If you ever want to find the IP address of a website you’re visiting, it’s easy on both Windows and Mac. Windows users simply need to type “cmd” into the search bar and open the Command Prompt, then type:
tracert anydomain.com
It’s a little easier for Apple users, and a bit more elegant, too. In your Mac’s search bar, type “Network Utility” and click to open it. Then navigate to the Traceroute tab and enter the domain name in the trace field. Easy.
Historically, DNS requests have been made using the UDP or TCP protocols—meaning that they’re sent in plaintext.
And as we’ll discuss, that can be a problem.
Why do we need to encrypt DNS requests?
If you’re living in the US, the UK or Australia, as the majority of our readers are, it’s easy to take for granted the rights and freedoms that we enjoy. In the greater scheme of things, our privacy concerns are pretty trivial. I found out last week that I was one of the lucky 50-million or so people that had their Facebook data compromised.
And while that’s supremely annoying, it’s what we would mockingly refer to as a first-world problem. Though there are a few terrifying outliers, the worst that’s going to happen to most of us is identity theft. And that’s no laughing matter, but it’s also not a threat to your life or liberty. Outside of kiddie porn and snuff, there’s nothing you can’t access in the US, the UK and much of the western world.
That couldn’t be less true for other parts of the world. China has a notoriously restricted internet (one that Google is currently developing a clandestine censored search engine for).
Russia, North Korea, Iran, Saudi Arabia – just to name a few of the larger countries – are among dozens of nations that restrict their citizens’ use of the internet.
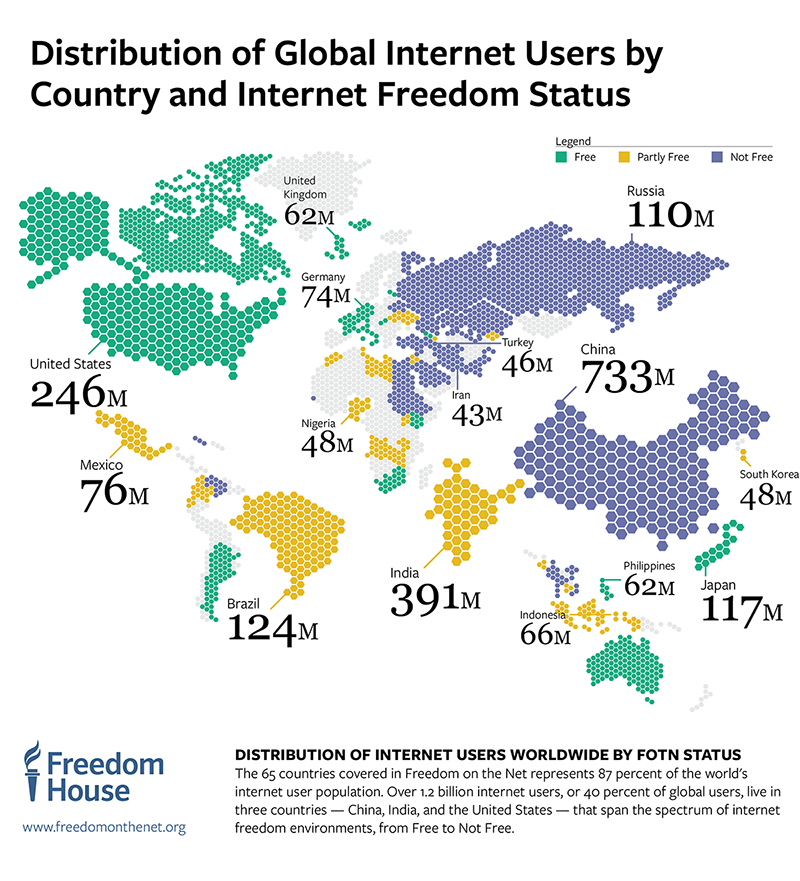
According to Freedom House, less than one quarter of the world’s internet users live in a country where the internet is designated as Free. That’s free in terms of rights and liberties–not price. 36% percent of internet users live in a country where the internet is fully restricted and another 28% live in a country where the internet is partially restricted.
Heck, a couple weeks ago the entire country of Ethiopia had its internet access turned off to try to quell what looked like, at the time, a potential military coup.

And when your internet history can result in you being extra-judicially detained, or harmed or even killed—being able to obfuscate those DNS requests can be a matter of life or death. That may seem hyperbolic, but it doesn’t take a whole lot of research to turn up what can befall regular people who get labeled dissidents based on their internet usage.
That’s why, to some parties involved in this debate, this is a human rights issue—one that can stir up considerable emotion.
Nobody is arguing that DNS requests shouldn’t be encrypted, the argument is over how best to do it.
Ok, so what’s the difference between DNS over TLS & DNS over HTTPS?
While both of these standards encrypt DNS requests, there are some important differences between DNS over TLS vs DNS over HTTPS. The IETF has defined DNS over HTTPS as RFC 8484 and it’s defined DNS over TLS as RFC 7858 and RFC 8310.

DNS over TLS uses TCP as the basic connection protocol and layers over TLS encryption and authentication. DNS over HTTPS uses HTTPS and HTTP/2 to make the connection.
This is an important distinction because it affects what port is used. DNS over TLS has its own port, Port 853. DNS over HTTPS uses Port 443, which is the standard port for HTTPS traffic.
While having a dedicated port sounds like it would be an advantage, in certain contexts it’s actually quite the opposite. While DNS over HTTPS requests can hide in the rest of the encrypted traffic, DNS over TLS requests all use a distinct port where anyone at the network level can easily see them and even block them.
Granted, the request itself – its content or response – is encrypted. So you wouldn’t know what was being requested, but they’d know you were using DNS over TLS. And at the very least that’s going to raise suspicions. It’s kind of like taking the fifth in the US. It just lends itself to the perception you have something to hide and in a lot of countries that’s not a good perception to have about you.
The case for DNS over TLS
Paul Vixie is one of the architects of DNS. And given the subject, his opinion bears considerable weight. Over the weekend he responded to Nick Sullivan, the head of crypto at Cloudflare’s Twitter announcement about RFC 8484 (DNS over HTTPS) by voicing his opposition:
RFC 8484 is a cluster duck for internet security. Sorry to rain on your parade. The inmates have taken over the asylum.
Personally, in the duck department I’m partial toward the Mallard, but, at any rate, Vixie’s opposition is made less from the perspective of a conscientious human rights activist and more from the standpoint of a seasoned security veteran. Those same human rights drawbacks, the ability to identify DoT requests – are also a boon to security.
It’s not unlike HTTPS inspection. On its face, the idea of interrupting an HTTPS connection sounds like a bad idea, and there’s certainly a segment of the infosec community that has a singular focus on security and argues that the practice weakens encryption. But there are also enterprise network admins and security officers that would be loathe to give up the ability to inspect their traffic. Losing that visibility is part of what led to the Equifax breach. Attackers love to hide in encrypted traffic, a point reiterated by the recent Magecart attacks.
DNS over TLS has more nuance, which is useful from a network health standpoint. DNS over HTTPS on the other hand…
DoH is an over the top bypass of enterprise and other private networks. But DNS is part of the control plane, and network operators must be able to monitor and filter it. Use DoT, never DoH,” tweeted Vixie.
Vixie argues that DNS over HTTPS removes a key distinguisher that assists in traffic inspection. It also makes blocking other websites more difficult because instead of just shutting off the DNS requests coming through a specific port you have to block all of the HTTPS traffic which can lead to all kinds of headaches.
That’s a good thing from a human right’s standpoint and bad thing from a network security one.
What’s the better standard, DNS over HTTPS or DNS over TLS?
That’s what all of this debate is trying to decide! There are legitimately valid arguments on both sides. What’s not helpful are ad-hominem attacks that distract from an otherwise worthy conversation.

Given the fact this is a human rights issue emotions are bound to flare, but it’s important to remember the side advocating for DNS over TLS, which favors a network security approach but potentially opens up some privacy concerns don’t hold that position because they’re cold or lack empathy, they’re just viewing this from a different perspective.
Sometimes what’s best from a qualitative standpoint, and what’s best from a human rights or even a morality standpoint don’t align. To many in the DNS over TLS camp, this has nothing to do with real-world privacy issues and everything to do with the fact they see DNS over HTTPS as an inferior standard to DNS over TLS.
This isn’t about working in deference to a social conscience to them, it’s about designing a standard that is the most efficient.
Nobody is fighting against privacy, even if not everyone is fighting for the same thing.
We’ll keep updating you on this as more develops.
As always, leave any comments or questions below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown