What is SSL Inspection? How does it work?
Everything you need to know about SSL Inspection, sometimes known as HTTPS Interception
SSL Inspection or TLS/HTTPS Interception is a fascinating concept that divides opinion. Some regard SSL Inspection as an absurd idea, while some are rooting for it with conviction. There seems to be very little middle ground. It’s kind of like the never-ending “Pineapple on the Pizza” debate. Personally, I cannot stand the sight of Pineapple staring at me while lying comfortably on a slice of Pizza. But let’s not go there as we all know how it ends—err, doesn’t end.
Instead, let’s untangle the technique that is SSL inspection and see how it works.
What is SSL Inspection?
SSL/TLS Inspection or HTTPS Interception is the process of intercepting SSL/TLS encrypted internet communication between the client and server. Interception can be executed between the sender and the receiver and vice versa (receiver to sender)—it’s the same technique used in man-in-the-middle (MiTM) attacks, without the consent of both entities.
 Now at first blush, it may seem that SSL Inspection undermines the purpose that HTTPS/SSL was created for. However, it’s not as simple as that.
Now at first blush, it may seem that SSL Inspection undermines the purpose that HTTPS/SSL was created for. However, it’s not as simple as that.
We all know that SSL/TLS encryption helps us protect our sensitive information (such as passwords and credit card details). Every single bit of data is turned into an indecipherable format and thus it protects us from eavesdropping and data tampering.
However, it’s not all sunshine and rainbows.
Along with your legitimate information, malicious content could also be hidden in the encrypted traffic. And because it’s encrypted, it goes unnoticed by common security mechanisms meaning it could do the damage that it was intended to do. SSL-based malware attacks have become a common thing these days with HTTPS being utilized in around 37% of malware.
SSL Inspection is *intended to inspect* and filter out potentially dangerous content such as malware. This kind of inspection or interception is called Full SSL Inspection or Deep SSL Inspection. It allows you to do antivirus scanning, web filtering, email filtering, etc. Interception and inspection are done by an interception device sitting in the middle, often referred to as a ‘middlebox.’
How does SSL Inspection work?
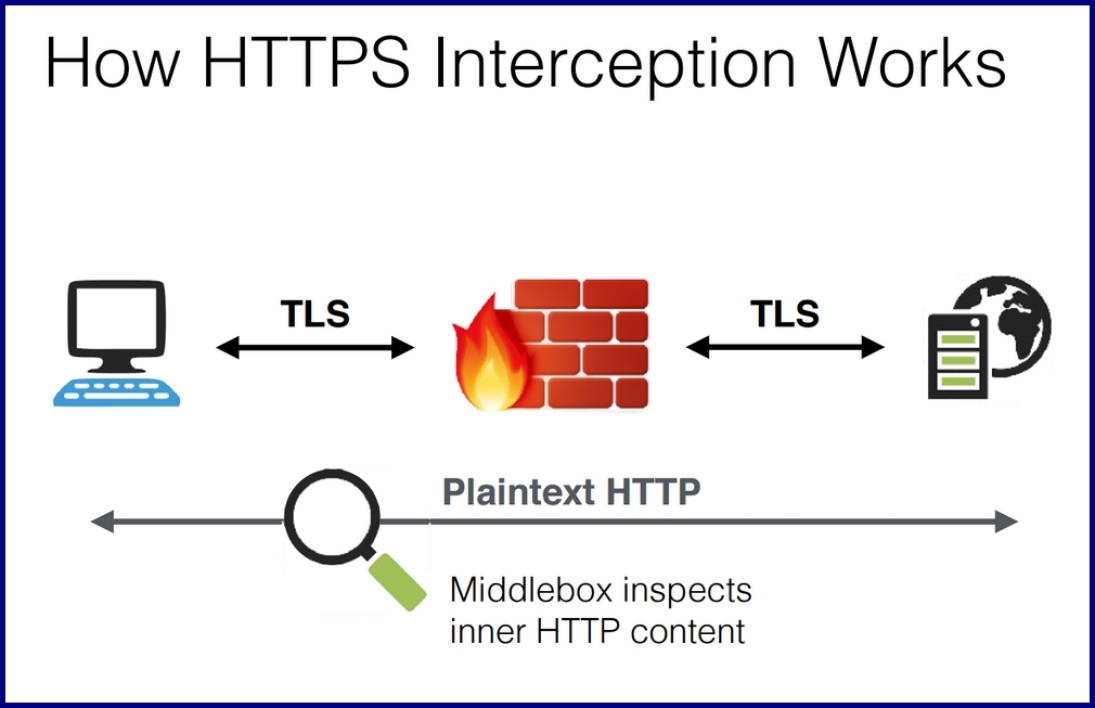
To put it in simple terms, SSL Inspection or HTTPS Interception is a man-in-the-middle attack executed to filter out malicious content. SSL Inspection or TLS Interception, as we saw, is done by means of an interception device. This interceptor sits in between the client and server, with all the traffic passing through it.
When the connection is made over HTTPS, the inspector intercepts all traffic, decrypts it and scans it. First, the interceptor establishes an SSL connection with the web server. Here, it decrypts and examines the data. Once the scanning is done, it creates another SSL connection—this time with the client (browser). This way, the data gets to the client in an encrypted format—the way it was intended originally.
Here’s an overview of the SSL Inspection process of inbound traffic:
- First, the middlebox intercepts the traffic coming and decrypts HTTPS sessions between clients and servers.
- Once the traffic has been decrypted, the middlebox inspects the content through antivirus scanning, web filtering, etc.
- Then the interceptor encrypts the traffic and forwards it to the destination, in this case the web server.
SSL Inspection works almost the same way for outbound traffic as well. Here’s a visualization courtesy of 01Net:
Poorly Executed SSL Inspection is Harming Security
In 2017, a study conducted by a large team of academics and professionals showed that SSL Inspection is doing more harm than good. This team included academics and professionals such as Zakir Durumeric, Zane Ma, Drew Springall, Elie Bursztein, Nick Sullivan (Head of Cryptography at Cloudflare), and Richard Barnes (Internet Security Research Group).
 The team analyzed nearly 8 billion SSL/TLS handshakes, comparing data of the observed connections to determine when an interceptor was bridging the connection between the server and the client. They found that up to 10.9% of observed connections were intercepted.
The team analyzed nearly 8 billion SSL/TLS handshakes, comparing data of the observed connections to determine when an interceptor was bridging the connection between the server and the client. They found that up to 10.9% of observed connections were intercepted.
This has enormous implications on the true privacy provided by those HTTPS connections. But the more significant problem is that some interception products are severely weakening HTTPS by using outdated cryptography and failure to implement essential features.
The study shows that 62% of traffic that traverses a network middlebox has reduced security and 58% of middlebox connections have severe vulnerabilities. They also investigated popular antivirus and corporate proxies, finding that nearly all of them reduce connection security and that many introduce vulnerabilities.
While there is a way to perform HTTPS inspection securely, and without much latency, poorly performed SSL interception is a problem.
Final Word
From the organizational security point of view, SSL Inspection looks good on the paper. And if implemented correctly, it could prevent a lot of damage. But as we saw, that doesn’t always happen.
A good part of the blame must go to the middlebox manufacturers for using outmoded or insecure SSL/TLS configurations. And then, of course, there’s always a risk in the form of the human element.
Right now, SSL inspection could potentially be doing more harm than good, that’s why over the coming months we’re going to delve into the practice and explore the best methods and practices for securely inspecting HTTPS traffic without sacrificing security or performance.
As always, feel free to leave any comments or questions below.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown