HTTPS Phishing: The rise of URL-based attacks
A new FireEye report shows a recent spike in URL-based HTTPS phishing attacks
If you’re a regular reader of Hashed Out, you know that we have been sounding the alarm on HTTPS phishing for a couple of years now. Recently, the Anti-Phishing Working Group published a study that found 58% of all phishing websites are now served via HTTPS. Some reports put that number as high as 90%.
On Tuesday, FireEye released its Q1 2019 Phishing Trends report and one of its key findings is that HTTPS phishing is continuing to evolve.
In 2018, FireEye reported that URL-based attacks had overtaken attachment-based attacks as a means of delivery. This trend continued in Q1 2019. URL-based attacks are harder to identify because they require a more dynamic means of detection.
So, today, we’re going to talk about what URL-based HTTPS phishing is, the rate at which it’s increasing and we’ll wax philosophic about how get here.
Let’s hash it out.
Free SSL and the rise of HTTPS Phishing
The original SSL certificate was actually Organization Validation. And at least part of the thinking was that since we’re trying to teach users that HTTPS is synonymous with security, it would be kind of counterproductive if malicious actors could easily slap a certificate on their website and make it say “https://.”

That was a somewhat noble, if deeply flawed approach. Obviously, there shouldn’t be an economic barrier to HTTPS. All websites should be encrypting their connections, it’s basically a standard at this point thanks to the browsers. The downside of that is when something is universally available – when there is zero barrier – bad guys can get it, too.
Now we’re kind of at a crossroads where the old talking points, about looking for the protocol and the padlock, are being taken advantage of by phishing websites and criminals. There’s already so much that can be done to make a website look convincing, that extra little flourish just really brings it home sometimes.
Now, we are not blaming free SSL – we have to make this disclaimer every single time – public CAs are a good thing. But like all good things people find ways to take advantage.
HTTPS phishing is one of the most pernicious ways of all of them.
What is URL-based HTTPS phishing?
Generally, when we refer to HTTPS phishing we’re discussing the landing page or watering hole site that a user arrives at. It’s easy to get confused because phishing is often considered to be “just an email thing,” but really, the email is usually just the opening salvo. Sometimes it asks you to open an attachment. Other times it takes you to a malicious website.
The problem is that phishing can be combated with education. Studies show that with phishing simulations run over time, and with enough frequency, employees can show marked improvement when it comes to identifying phishing emails. And a couple of the tenants of those educational simulations are not to trust attachments and to avoid following suspicious links.
So, as the proverbial game of cat and mouse continues now the criminals are evolving.
FireEye identifies two different variants of URL-based attacks – well, really one is a variation of the other – but the premise is basically the same in each: send an email with no content; only a believable link in the body.
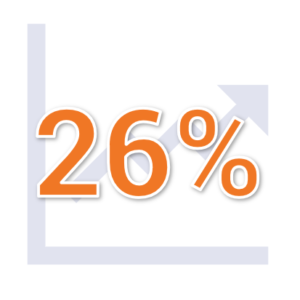
Now, I realize that sounds incredibly dumb. And it wouldn’t work on its own if it’s emanating from a random email address that the target wouldn’t recognize. But when coupled with other tactics, it’s clearly working well enough that FireEye has noticed a 26% increase over the first three months of 2019.
[Overall,] FireEye saw a 17% increase in phishing attacks in Q1 2019 compared to Q4 2018. In a typical attack, the email appeared to come from a well-known contact and/or trusted company.
In fact, URL-based attacks are now the most prevalent method for delivering a malicious payload.
Quick example, with a little social engineering, you can change the “from:” field in an email to someone in the company. Here’s an email purporting to be from our owner:
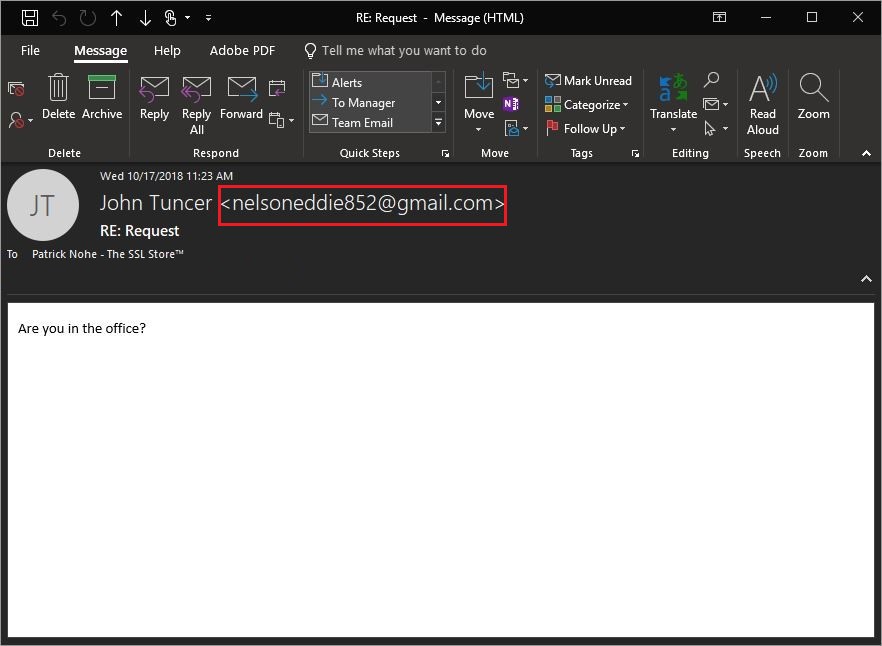
Now, if you’re diligent you could verify the actual address it came from or check the email header, but a lot of people aren’t going to do that.
You can see how someone could fall for it. This looks like it came from Dan in sales and he’s always sending you funny stuff and you click on it.
So, that’s the first variant, the content-less email. It’s literally just a link.
This has the added benefit of making it harder for spam filters to detect. The lack of content in the email itself doesn’t give the filter enough to know whether or not it’s malicious. And obviously, as we just touched on it plays on the curiosity and impetuousness of the target.
Then there’s a variant of the no content email, which is to make the link non-clickable. That way it makes it even harder for the filter to detect because there’s no active link in the email. The link isn’t active until the target pastes it into their browser’s address bar.
It almost seems like the sender just forgot to hit return on the line before sending the email.
Now, these emails occur without the HTTPS component, too. You don’t HAVE to have an SSL certificate to do it. But, being able to affix HTTPS to the beginning of that URL adds another layer of believability and, as we’ve discussed, sometimes it’s that last little brush stroke that pushes it over the threshold.
Again, the only defense with any level of efficacy is education.
What do we do about HTTPS phishing?
At this point, it’s probably too late to put the toothpaste back into the tube. And some in the industry are taking action. Google, which has really led the way on the entire HTTPS initiative, is in the process of scaling back its visual indicators.

Ideally, it wants to remove the protocol (https://) and the padlock from the address bar entirely and just give HTTPS sites neutral treatment. HTTP sites are already receiving a negative indicator. The idea would be that HTTPS is now the status quo.
The bigger question the industry is wrestling with is how do you treat the higher-validation certificates. Historically, OV has received the same treatment as DV. It might be worth continuing to allow OV sites to use the padlock. And of course the debate over EV never ends. At this point it’s not even really worth re-hashing as everyone seems to be so entrenched in their beliefs on the topic.
Suffice to say, at the very least we can’t keep giving DV sites positive indicators. In the long run, we would be wise to overhaul our trust indicators entirely.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown