Apple’s iBoot Source Code Allegedly Leaked: Everything an iPhone user needs to know right now
The biggest leak ever?
In what has been a season of leaks, another leak is here, and it could potentially dethrone every other leak once touted as “the biggest leak ever.” A GitHub user named ZioShiba posted a code named “iBoot” – which is said to be Apple iBoot source code for iOS 9.3 – on GitHub. This could open a huge can of worms if this alleged leak is actually what it purports to be.
What is iBoot source code?
iBoot, an integral component of iOS, is responsible for the authenticated boot of iOS devices. In simpler words, iBoot performs security checks and verifies that the kernel (iOS) is genuine, in addition to any other system files, are properly signed by Apple.
So, when you turn your iPhone on, iBoot is the first thing that gets loaded.
Is this really a big deal?
Yes. Emphatically, YES.
From a security point of view, iBoot is a highly critical part of the iOS that makes Apple’s iPhones stand out. That’s why Apple has been keeping the iBoot source code close to its chest. Over the years, Apple has opened up certain parts of iOS and MacOS, but never the iBoot source code. You can understand its significance from the fact that Apple rewards up to $200,000, one of the highest payments under Apple’s bounty program. If this is truly code for iOS 9.3, it could aid attackers in finding zero days, as well as will developing persistent malware and iPhone jailbreaks.
Okay, what are the potential dangers?
As iBoot authenticates iOS, the first risk comes in the form of jailbreaking. If the perpetrators can find a way to do this, it could make their job much more manageable.
Moreover, there’s also a huge risk of programmers imitating iOS on non-Apple devices.
Many are even suggesting that this could allow an attacker to unlock and decrypt iPhones. This seems highly unlikely as far as the devices with biometric sensors (Touch ID and Face ID) are concerned. That’s because they come with Secure Enclave – a physical, dedicated encryption processor with its own kernel (OS).
One thing is for sure, we will be talking about security researchers finding its flaws for some time.
Am I affected?
Although the leak is said to be for iOS 9, it’s highly likely that the recent versions of iOS still contain some of the same code. That’s why even if your device doesn’t use iOS 9, you’re not out of the woods.
How likely is it that this is a “genuine” leak?
Pretty likely, if we go by the opinions of some researchers. Motherboard, which is a very trustworthy source, has confirmed it with several developers. However, others still aren’t completely convinced. There are still plenty of questions floating around the code, beyond just its authenticity. Questions like, who is behind this? And how did they get a hold of this?
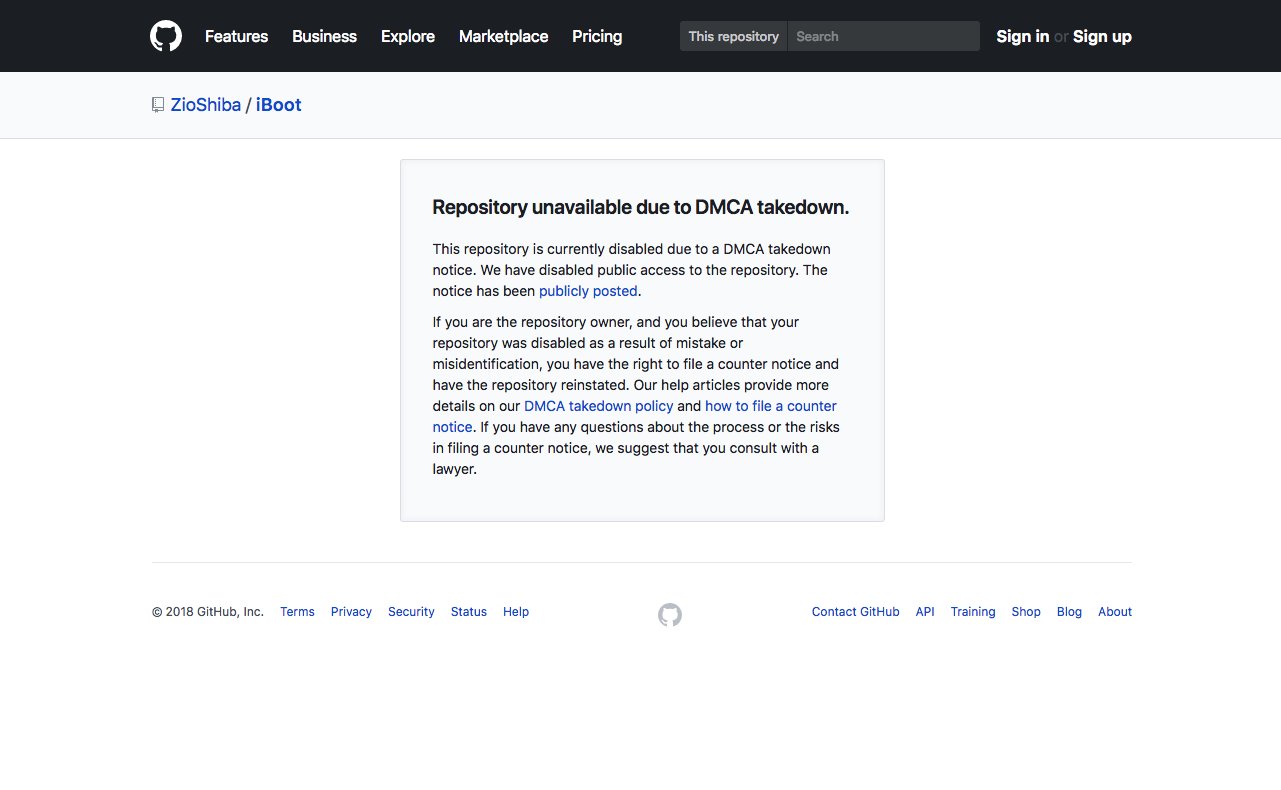
As of now, GitHub has already shut down the repository that hosted the iBoot source code.
Wrapping Up
As I’m writing this post right now, we haven’t heard anything from Apple yet. It will be interesting to see what the company thinks (and tries to make us think) of this leak. I expect Apple to release a security patch in the upcoming days.
If any of your Apple devices are running on iOS, update them as soon as Apple releases one.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown