Microsoft Wants You To Ditch TLS 1.0 and 1.1 Support
Windows Server 2008 Will Receive TLS 1.2 Capability Later This Year
TLS 1.3, the upcoming update to our favorite security protocol, is still just around the corner. But for most of the internet-connected world, supporting the latest version is more of a pipe dream than a reality. That’s because we work with legacy systems, software dependencies, and all sorts of other support requirements that mean we are lucky if we get to use software from this decade.
That’s why TLS 1.2 – the current best version of TLS – which came out in 2008, is still not being used by many systems and programs.
Microsoft is concerned that protocol vulnerabilities – such as POODLE, which affected SSL 3.0 and TLS 1.0 – pose an unacceptable risk to businesses and software still relying on these aging versions of TLS.
That’s why Microsoft has announced a new effort to improve TLS 1.2 support for Windows and are encouraging their enterprise customers to ditch the problematic versions that came before.
The goal? Remove support (or preference) for TLS 1.0 and TLS 1.1 in favor of TLS 1.2. If your operating system does not support TLS 1.2, it needs to be upgraded or replaced.
While TLS 1.0 and 1.1 have not been put to pasture like older versions of the protocol, the smart money is on the fact that there are deficiencies and vulnerabilities in them.
The problem versions of Windows are Vista, Windows 7, and Server 2008. In Vista and Server 2008, TLS 1.2 is not supported at all. In 7 and Server 2008 R2, TLS 1.2 is supported by disabled by default.
To solve this Microsoft has announced that they will provide support for TLS 1.2 in Windows Server 2008 “later this summer” with a new patch.
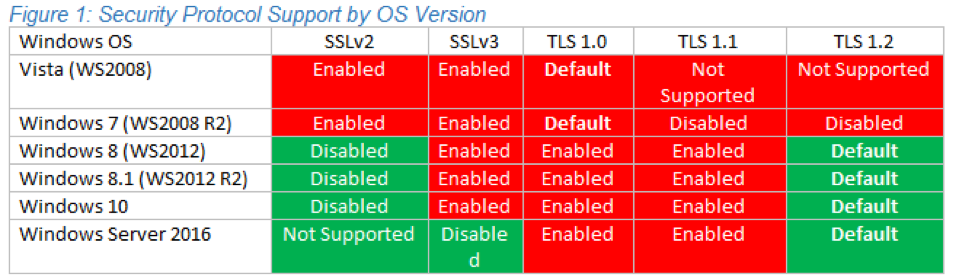
In recent versions of Windows operating systems – Windows Server 2012 and newer – TLS 1.2 is the system’s preferred protocol version by default. But you still need to make sure your software isn’t specifically asking to use inferior versions.
For those working with Windows crypto libraries, Microsoft has published a new whitepaper, Solving the TLS 1.0 Problem, which contains some specific guidance on how to find out if your software has hardcoded preferences for TLS 1.0/1.1, including specific functions that are indicative of older protocol support.
“If not already complete, it is highly recommended to conduct an inventory of operating systems used by your enterprise, customers and partners (the latter two via outreach/communication or at least HTTP User-Agent string collection). This inventory can be further supplemented by traffic analysis at your enterprise network edge. In such a situation, traffic analysis will yield the TLS versions successfully negotiated by customers/partners connecting to your services, but the traffic itself will remain encrypted.”
If you aren’t sure what versions of TLS your server is offering that is a great place to get started. You can test the configuration of any internet-facing server for free using SSL Labs.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown