Only Certificate Authorities need to worry about Certificate Transparency
End users, resellers and enterprise clients don’t need to take any action for CT
One of the most common questions we’re getting about all of these Certificate Transparency announcements is: “what do I need to do comply with CT?”
If you’re not a Certificate Authority, the answer is: nothing.
The party responsible for logging the certificates is the issuing Certificate Authority. And when you think about it, that also makes the most sense. The CA has to handle validation and issue the certificate off its own PKI, it has the biggest vested interest in making sure that the certificate is trusted by browsers. After all, it doesn’t take too many mis-issuances to attract the attention of Google and Mozilla.
How does Certificate Transparency work?
To help you better understand why you don’t need to worry about Certificate Transparency unless you’re a Certificate Authority, let’s look at how it all works:
- The process begins when the CA creates a “pre-certificate.” This pre-certificate contains all the same information that will be included in the SSL certificate. It gets sent to the CA’s preferred CT log server at the outset of the process.
- The CT log server responds to the pre-certificate by returning a Signed Certificate Timestamp or SCT. You might have see SCT thrown around in relation to Certificate Transparency before. An SCT is essentially a tokenized promise to log the certificate within 24 hours of receipt. This is known as the Maximum Merge Delay (MMD).
- The CA takes the SCT and adds it to the body of the SSL certificate when it’s issued. That SCT serves a signal to the browsers that the certificate its attached to is published on a CT log. The SCT can be delivered three ways: via X509v3 extension, TLS extension or OCSP Stapling (see image below).
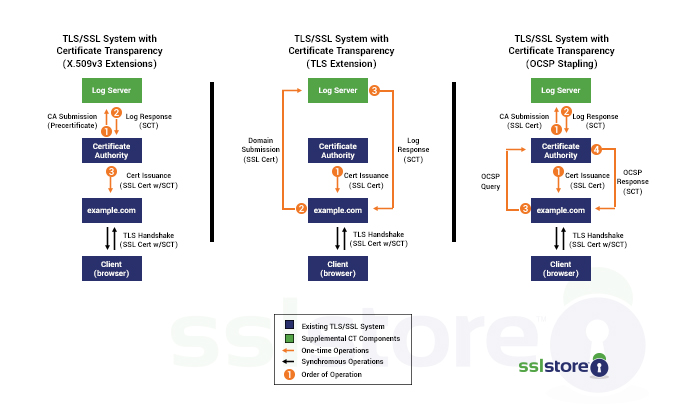
For the sake of better security, some browsers (like Apple’s Safari, for instance) will require SCTs from multiple CT logs in order to be trusted. This just means that the CA issuing the certificate has to send pre-certificates to multiple CT logs. So for instance, DigiCert may log a certificate it’s issuing on its own CT server, and then it may also send pre-certificates to Apple and Google for inclusion on their logs as well.
The CAs are the only ones required to do the logging?
Yes. There are, for all intents and purposes, two ways to log a certificate if we’re being honest. The alternative way is using web crawlers, which can see certificates and report them back to logs, too. The problem is crawlers can’t see everything on the web so you would never get a complete picture.
Certificate Transparency has long been a Google initiative, and with the entire internet moving towards HTTPS it makes sense to push for a system that requires greater accountability from issuing CAs—especially in light of some of the issues that have occurred over the past few years with CAs like WoSign and StartCom making egregious mistakes. Certificate Transparency provides a greater level of oversight, making it easier to detect mis-issuances and revoke them.
One of the biggest issues facing the SSL industry right now is the lack of a reliable revocation mechanism. Certificate Transparency doesn’t fix that entirely, but it’s certainly a step in the right direction.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown