The WhatsApp Security Setting You Should Turn On Now
It only takes 15 seconds to turn on WhatsApp Security Settings.
Last week, The Guardian sparked controversy with a story about a “backdoor” in the popular messenger WhatsApp. The reality was more complicated than that – WhatsApp did not have a backdoor. But there was a legitimate security risk as a result of a default setting in WhatsApp, which was an active choice by the developers to make the app more usable for its largely mainstream audience.
The Info Sec community reacted loudly – denouncing their claim and stressing the dangers of mislabeling the problem as a “backdoor.” To those outside of the community, this may sound like a debate over semantics, but the claims play into a bigger discussion around user security and reporting. If you are interested in learning about the controversy over the “backdoor” claim, we wrote about it in-depth last week.
[su_pullquote]”…there is a legitimate concern over WhatsApp’s default settings, which do not notify users if their contact’s key changes.”[/su_pullquote]
But, underlying the outrage, there is a legitimate concern over WhatsApp’s default settings, which do not notify users if their contact’s key changes. WhatsApp uses public key cryptography, like SSL/TLS and PGP, which protects messages by encrypting them a unique pair of keys that belongs to each user. When a user’s key changes, it could be for legitimate reasons (they got a new cell phone) or dangerous ones (an attack is impersonating them).
However, with a simple change in the settings, you can partially protect yourself. By turning on “Security Notifications,” you can at least be notified when one of your contact’s key changes. Messages that you sent, but have not yet been delivered (these are messages which only have a single checkmark next to them) will still be automatically resent to the new key, and there is no way to stop WhatsApp from doing this. So at best, this is a notification, not a prevention.
That being said, anyone using the messenger service should turn on WhatsApp security settings. There is no downside and it literally takes 4 taps of your finger. Here is how you do it…
Turn on WhatsApp Security Settings: Notifications
Before we get to the instructions, which are incredibly simple as promised, I want to take a moment to talk to the high-risk user: If you think you may be at risk of physical harm or imprisonment, your best option is to switch to Signal. That is not to say WhatsApp is insecure, but if there is a real risk to your freedom or safety, it is better to use Signal which was designed primarily for secure communication. For example, Signal has additional measures to block messages after a key change, while WhatsApp only notifies you.
It’s incredibly simple to turn on WhatsAppSecurity Settings and enable Notifications. It is a three step process on iOS and Android:
- Go to Settings
On iOS, the Settings button is at the bottom right of the screen when you are on the main menu of the app
On Android, click the ⋮ menu from the main menu of the app. Settings is the last option on the pop-up list.
- Tap Account and then Security
- Turn on Show Security Notifications
Done! Next time any of your contacts’ key changes, you will see a notification in the chat. The notification looks like this:
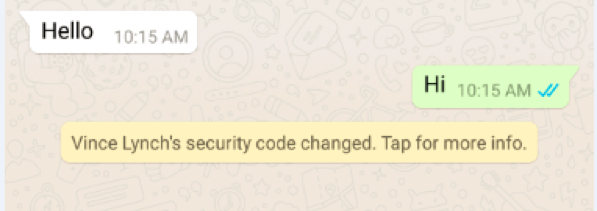
If your key changes, you contacts will only get a notification provided they have also turned this setting on. So share these instructions so there will be an alert if either side has a key change.
If you do see this notification, you should check with your contact about the change. If you are a high-risk user, make sure you check with them in-person (if possible) or through another medium you trust (phone call, Signal, Facebook Messenger) and verify that the key change was legitimate before exchanging any more sensitive information with them via WhatsApp.
If you want to go even further, you can verify keys with your contact. Verifying keys allows you to make sure that the public key you are encrypting your messages with really belongs to your contact. This protects you from man-in-the-middle or impersonation attacks where you may be delivered a key that is impersonating your contact.
Verifying keys (or fingerprints) has traditionally been seen as an essential step in public key systems. However in mass market applications like WhatsApp, it is seen as an optional security measure. If you are a high-risk user, you should do this with all your contacts that you consider sensitive.
Verifying keys is done on a contact-by-contact basis and is done the same way for iOS and Android. First select the chat you have with the contact (or start a chat, if you do not already have one) and then select their name from the top pane. Select the Encryption option to see their “Security Code,” which is a unique fingerprint that identifies their key.
If you can physically meet up with your contact, WhatsApp can automatically verify each other’s code using your phone’s camera. If you cannot meet up in person, you can share the number listed on the page through another medium you trust (phone call, Signal, Facebook Messenger).
What’s The Threat?
So, you may be wondering what exactly is the threat from WhatsApp’s behavior? The threat can be broken up into two main components
Component One
Because WhatsApp’s default behavior is not to notify you of a key change, your contact’s key could be maliciously changed and you could start talking to someone impersonating them without knowing it. This can be fixed when you turn on WhatsApp security settings and enable notifications (how-to explained above).Depending on how long this goes unnoticed, this could prove extremely dangerous. In a worst case scenario, a hostile key change is made and you continue talking to the wrong person for days/weeks/months without knowing it.
On the other end, immediate detection would allow you to know you are under attack and immediately start defending yourself.
Component Two
Because WhatsApp resends in-transit messages to new keys automatically, there is no way to prevent an attacker who can initiate a key change from receiving these messages. There is no option to prevent this. If you turn WhatsApp security settings and enable notifications, you will at least know when this happens, though that won’t fix the fact that your messages have just been sent to an attacker.
If you assume that the WhatsApp server can be hostile, it’s possible that the server could intentionally “hold” multiple messages in transit and then initiate a key change. This is a fairly serious problem as it could allow targeted attacks. While this is less likely – because it relies on the server being hostile – it should concern high-risk users. Think about the risk of any given message you send being received by an attacker. If you believe WhatsApp (or its parent company Facebook) to be unreliable or able to be influenced by your government, you should consider switching to Signal.
What Does it Mean?
If you are an everyday person using WhatsApp because that is where your friends are, or because you want more security than SMS, these threats probably do not apply to you. But if you are a political activist, reporter, hold dissenting opinions, or live in a country with a hostile government or a government known for human rights abuse, you may want to consider switching to Signal.
The Info Sec community maintains that the bigger threat is in The Guardian’s reporting. Their “backdoor” claim has continued to spread, and the Info Sec community fears that as a result many users will abandon WhatsApp for less secure options.
To combat this, Zeynep Tufekci, a professor and civil rights advocate, wrote a letter to The Guardian’s editors to encourage them to correct their story. The letter has been signed by more than 60 members from the cryptography and Info Sec fields, including Matthew Green, Jon Callas, and Yan Zhu. There has been consensus from the Info Sec community that The Guardian’s claims are wrong and dangerous.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown