Understanding the Encryption Technology Behind SSL
Gary Stevens stops by to give us an expert’s take on SSL/TLS
There’s a good chance you’ve heard of SSL before, even if you don’t have a background in IT.
You probably have a vague idea of what it is, why it’s important, and how to go about getting a certificate. Beyond that, do you understand how it works and what the benefits are to you and to others?
Here’s what you need to understand about SSL, the encryption technology behind it, and how it protects you today and will still be protecting you in the years to come.
The Basic Concept of SSL and SSL Certificates
Let’s start with a basic definition of SSL. A secure sockets layer is a networking process that’s designed to allow web clients and web servers to communicate over some type of public network. In most cases, that public network is the Internet. Basically, the point is to create connections that other parties cannot break into, change to their liking, or intercept and collect data without proper authorization.
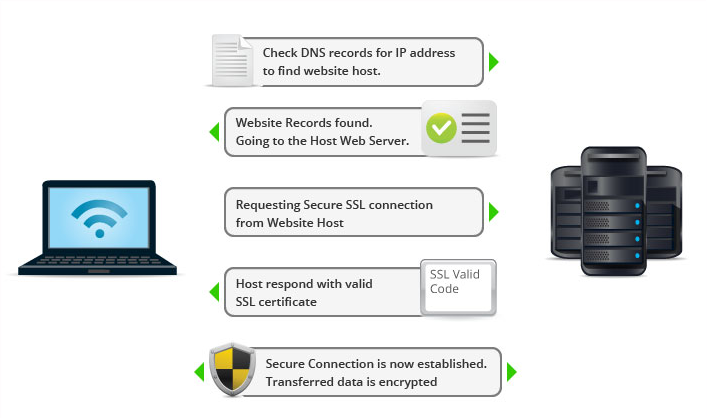
SSL has been around for over two decades. The development and the accompanying certification process made it possible for businesses to begin offering goods and services online in a secure setting. That included remitting payments for purchases.
What’s commonly called SSL today by many people is actually a secure protocol that has superseded the original. Officially known as Transport Layer Security, the first versions were made interoperable with what’s known as SSL 3.0. As of 2018, the two protocols are no longer interoperable, although both continue to be used.
Asymmetric Encryption
So what is it about SSL that makes it so important to online security? One aspect that should be explored is known as asymmetric encryption. When you visit a website, the browser makes the connection with the site. The goal is to determine if the SSL certificate is valid before any data flows between the site and the browser. All this happens so quickly that you don’t detect a delay.
In other words, the connection’s encryption is determined before you see anything. If there is a problem, the browser stops you in your tracks and gives you the chance to migrate away from the site.
What makes asymmetric encryption important? It employs both a private and a public key. The public key encrypts data while the private one decrypts the data. It’s only after both keys are determined to function that you get to continue.
Symmetric Encryption
What about symmetric encryption? It’s also important to the process of verifying the SSL certificate. It’s what keeps the connection going once the browser and site are talking to one another after the secure session is established.
Thanks to the use of this type of encryption, the sessions keys are capable of encrypting and decrypting data. What you see is a smooth flow of data back and forth that’s still safe.
How They Work Together to Form SSL
Think of asymmetric encryption as the means of checking, confirming, and verifying that the browser and the website can communicate. In a sense, it checks the SSL certificate and makes sure it’s safe to communicate. From there, symmetric encryption takes over and allows the communication to flow unabated until one party or the other ends the conversation.
Consider this: you use your browser to get to your favorite online store. Asymmetric encryption makes sure the SSL certificate is up to date and communication can be established securely. Once you are on the site and in the store, symmetric encryption allows you to conduct searches, read descriptions, and conduct a transaction.
Digging Deeper: RSA and ECC
As you learn more about SSL and encryption in general, there are two terms that you are likely to hear. One of them is known as RSA encryption.
The name is based on the three individuals who came up with the idea for this kind of encryption: Rivest, Shamir and Adelman. It focuses on public key encryption and uses specific mathematical equations to produce two large prime numbers whenever a browser is used to connect with a website. The prime numbers are kept confidential at all times and ultimately lead to the development of public and private keys. Once the process is completed, the two prime numbers are no longer needed.
This is one more layer of protection for the “handshake” between the browser and the site. As with encryption in general, it happens so quickly that you don’t have time to see it happening. What it does do is keep the connection safe.
You’ll also hear about ECC encryption. This stands for Elliptic Curve Cryptography. It’s been in use for more than a decade and is typically considered to be more complex than other aspects of SSL. What it does it participate in the verification process that establishes the connection.
Like RSA, ECC is about evaluating and determining the connection between the site and the browser is secure and safe. Once that’s verified, there’s a foundation for communication back and forth. See it as one more way to prevent third parties from breaking into what is meant to be a conversation between you the user and the website you are visiting.
SSL Encryption is Not the Same as VPN – Except When it Is
While much of the focus on the use of SSL has to do with public access on the Internet, it can also be important to creating and preserving privacy on a virtual private network (VPN). That includes granting access from a public network (the Internet) to your private network, something that happens when you or your employees attempt to remotely access your company network using a public Internet connection at an airport or restaurant, for example.
Without peering too deeply into Pandora’s cryptography box, we should note that some VPNs (known as SSL VPNs) actually use the SSL and TLS protocol by essentially hitching a ride on the function already built into a web browser as a “clientless” or IpSec VPN. This differs from traditional VPNs that require software installation in order to work.
Better? Worse? Flip a coin and pick your protection. An SSL VPN, such as OpenVPN, is more versatile but comes with additional risk in the form of trust issues from self-signed certificates.
SSL Certificates and the ‘Value’ of Free
You don’t have to browse online long to realize that the price to buy an SSL certificate is all over the place, often included for free in web hosting plans, but ranging up to hundreds or thousands of dollars for premium certificates. While there’s no one right answer for which to choose, keep in mind that any free SSL protection is likely domain validated only (the least secure option) and may have a shorter time limit that others – essentially a free trial.
Check this comparison of the top SSL certificate brokers to get an idea of the price, features and level of security offered. The bottom line is that, thanks to the ever-frantic efforts of hackers and Google’s decision to reward sites with the ‘HTTPS’ offered by SSL protection with better search engine ranking, it’s no longer a choice of should you or shouldn’t. In 2019, you absolutely must.
As always, leave any comments or questions below…





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown