2018 was a busy year for SSL/TLS
Here’s why you shouldn’t expect it to slow down in the new year.
The SSL industry has seen a lot of changes, especially this past year. As the door on 2018 gets ready to close, we wanted to take this opportunity to recap where we’ve been, the current state of the market and what we expect to come down the pike in 2019.
SSL was anything but boring in 2018
Browser UIs evolved. Again. Not secure warnings hit the net. GDPR went into effect. Comodo CA re-branded as Sectigo. 2018 saw plenty of SSL-related action and we had a front row seat.
HTTPS is gaining traction
No doubt about it, the web is becoming more and more encrypted by the day. Articles abound that confirm that the browser’s push for total encryption is becoming a reality. In his November Trend Briefing, DigiCert’s Threat Strategist Jeff Barto shared that more than 80% of page loads in Chrome and 70% in Android are now over HTTPS. While that’s impressive, there’s still plenty that need to make the move, according to our recent blog post, roughly 21% of the world’s top 100K sites still aren’t using encrypted connections.
The SSL market continues to grow
Netcraft’s June 2018 report confirms significant growth in SSL certificates. Specifically, total certificates increased more than 13.2 million or 68% year-over-year from June 2017. And, while 80% of this growth was Domain Validation (DV) certs, Extended Validation (EV) grew 21.1%.
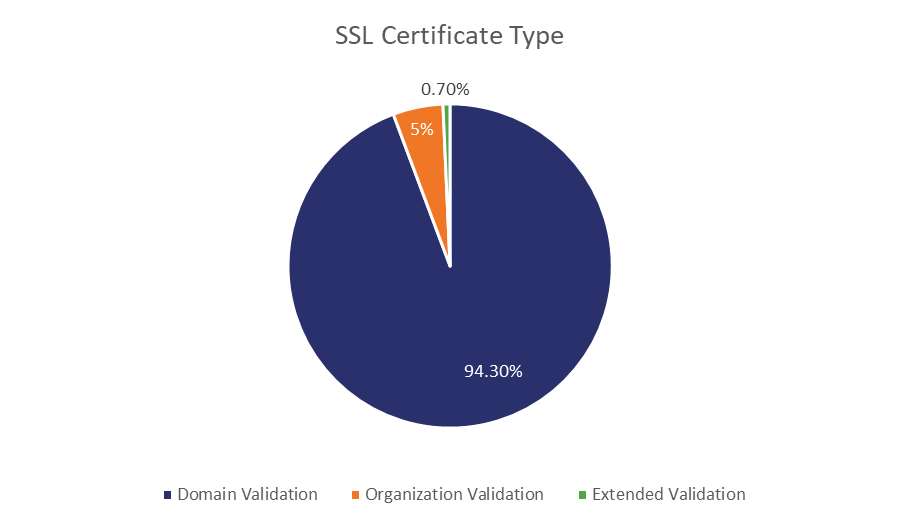
Source: Netcraft June 2018 Report
So, while DV still dominates the market share, there’s also a definite place for premium certificates. Especially when you look at the share of traffic by certificate type.
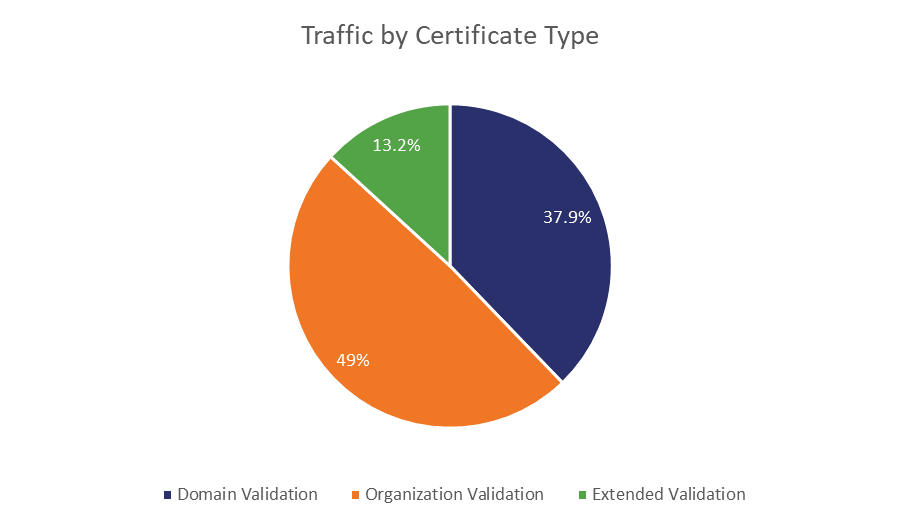
Source: Comscore and Netcraft
The percentages even out even more when you look at ecommerce transactions.
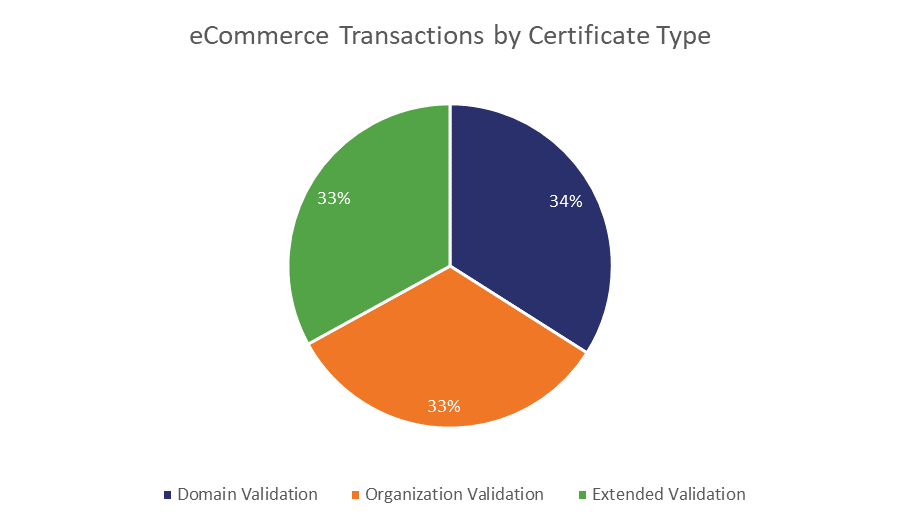
Source: Comscore and Netcraft
A peek at 2019
Forecasts are mostly positive for SSL as we look ahead to 2019. Let’s look at what a few industry experts are predicting.
According to the CA Security Council’s 2019 Predictions:
- More than 90% of the world’s traffic will be secured over SSL/TLS by the end of 2019
- TLS 1.3 will grow by more than 30% by the end of 2019
- Phishing (especially encrypted phishing) will continue to skyrocket

And, here’s what DigiCert’s Threat Strategist Jeff Barto sees on the horizon:
- 2019 will be the year we’re going to wake up and demand to know that who we’re connecting to is a legit company
- Inconsistent trust indicators present both challenges and an opportunity to re-define what they can do and mean, and create new ones
- This will be the year people get sick and tired of breaches, driving them to take control and take steps to protect their identity
Here’s what we see at The SSL Store™.
SSL isn’t going anywhere but up
Industry reports support our position that SSL will continue to be an increasingly important staple of every organization’s security budget. The 2018 IDG Security Priorities Study supports the notion that companies are moving toward a more proactive stance, with 74% of respondents reporting that best practices and compliance are key factors that drive their security spending. And, the SSL market overall is predicted to grow at nearly twice the rate of web hosting or domain registration.
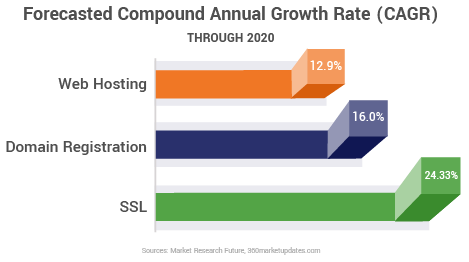
So, how does an IT manager or advisor help the powers that be understand that SSL needs to be an essential part of their security strategy?
The SSL conversation needs to be about way more than encryption
The browser UI changes have certainly had a huge impact on SSL market growth. But that’s not the only thing driving the increasing need for SSL certificates. Here are a few other factors companies need to equally consider when contemplating if they should protect their data, customers and reputation with SSL and which type of certificate to choose.
Phishing—According to PhishLabs Q3 2018 report, nearly half (49%) of phishing sites are duping visitors into believing they’re safe by enabling HTTPS with DV certificates. And, secure and safe are definitely not the same thing as we pointed out in our November 27 blog post. This might explain the steady bump in premium certs as organizations increasingly choose to separate themselves from the phish pond.
PCI Compliance—PCI compliance is a necessary evil of running a business that accepts credit cards and SSL certificates play an important role in meeting these requirements. Here are a few SSL-related issues that can cause a “fail” on a PCI compliance scan if they’re not resolved:
- Using expired SSL certificates
- Using non-publicly trusted SSL certificates in the wrong areas
- Using lower than 256-bit encryption
- Using outdated TLS protocol
Failing a PCI compliance audit could result in hefty monthly fines in the tens, to hundreds of thousands, possible suspension of a company’s ability to handle card payments, plus leaves them more vulnerable to cyberattacks.
GDPR—These new regulations took effect May 25 of this year and Gartner predicts more than 50% of companies affected still won’t be in full compliance by the end of 2018. Breach penalties are steep at €20 million or 4% of annual turnover, whichever is higher. Just to put this into perspective, this would equate to $7 billion for Amazon, more than two years of profit. Plus, there may be additional fines based on the type of breach, data exposed, notification, remediation and response. And, this doesn’t include irreparable damage to reputation or costs associated with insurance, legal fees and settlements. Beyond the regulation itself and possible fines, there are other considerations, including companies with partners that want to be GDPR compliant and require them to follow suit. Last, but not least, there’s plain old customer trust and expectations for companies to treat their information with kid gloves. And, some of the requirements in the 99-article GDPR can only be accomplished with SSL certificates.
One last note about compliance. Companies are, in fact, taking it seriously and backing it with budgets according to the 2018 IDG Security Priorities Study that reports 69% of companies see compliance mandates driving spending.
RELATED: The Hashed Out GDPR Compliance Series
Data Breaches—Almost a day doesn’t go by without reports of a massive data breach. Adidas (two million records compromised), Facebook (up to two billion accounts scraped)—the list goes on. And, it’s not just the mega brands. According to the 2018 Global Threat Report, 71% of companies report suffering at least one data breach.
Gemalto’s Breach Level Index tracks activity and reported the first six months of 2018 saw 945 reported data breaches involving 4.5 billion records. That’s 291 records stolen or exposed every second. And, a mere 1% were encrypted. In fact, Verizon’s Data Breach Investigation Report cites lack of encryption and security when handling confidential information among the top most common causes of breaches. If you suffered a breach, wouldn’t you at least want to make sure your company and customer data couldn’t be decrypted by evil doers?
Companies need to ensure that they have implemented best practice encryption to protect data at rest (when it’s on the server) and in transit (while it’s on the way to/from the user). SSL certificates have been the de facto encryption and authentication standard for protecting data in-transit for more than 30 years. Simply put, not having an SSL certificate increases your risk of a data breach.
Man-in-the-Middle Attacks—In case you missed it, our Hashed Out Editor-in-Chief Patrick Nohe recently took a deeper dive into MITM attacks and there’s a lot more to it than meets the simple internet connection. Detecting MITM attacks is difficult, so prevention is the key. And, once again, the only real way to prevent a MITM attack is with SSL/TLS encryption and HTTPS. Let me rephrase that—it won’t necessarily stop the attack, but it renders the intercepted data useless and, therefore, secure.
The SSL future looks bright
There’s certainly no lack of talking points around why every organization needs SSL/TLS certificates. Hopefully we’ve given you some insights to help you make 2019 the year you put SSL in the spotlight.




































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)















5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown