7 Security Factors to Consider When Choosing A Web Host
Choosing a web host is an important decision – are you looking at the right things.
Let’s be honest – when shopping for website hosting space most people will usually look out for points such as features and price. Security, for the most part, comes down to an ignoble last place in the list. Thanks to increasing concerns on cybersecurity, priorities have changed a bit of late but is it enough?
When it comes to security in the field of technology, there is truly no way to guarantee 100% assurance. Even isolating a computer in a locked room with no network connection can leave it open to a chance of physical intrusion.
For web hosting that’s even scarier as many security aspects are completely out of your control and in the hands of the web hosting provider and data centre. Now imagine that your website is your primary source of income. How safe do you feel leaving that in the hands of just anybody?
There are things you can look out for in a web host which can help assure you of better security safeguards.
In this article, we’ll dive into 7 different security factors you should look at when choosing a web host, to ensure your website is protected.
Let’s hash it out.
1. Software Security
Web hosting is managed by software that sits on servers that need operating systems (OS) to function properly. The type of OS affects what measures you can take to increase the security of your website. Mostly, your choice of web hosting runs between Windows-based servers and Linux-based servers.
An interesting point raised by Windows Server Administrator Lukáš Kučera is that the question of the OS itself being inherently secure is less relevant than the actual usage of the server deployed. The usage model will more directly affect server configuration, which is what Kučera feels would be a more accurate gauge of security.
Irregardless of the type of server you opt for, some of the questions you can ask a web hosting company would be;
- How are software updates handled?
- Does the hosting company provide auto updates?
- How many senior server admins are there?
- What is their level of experience?
Windows OS is a more highly commercialized system that is unique to Microsoft. It is also known to be more vulnerable than Linux simply because it is in greater commercial use.
Aside from the primary security involved in your hosting account’s operating system type, keep in mind that all software has various levels of vulnerability. Anything you install on your web hosting account, such as web applications potentially increases your vulnerability level.
Take for example if you use a Content Management System like WordPress. This powerful CMS is highly modular and powerful because other applications known as plugins can easily be installed to extend functionality. Aside from WordPress itself, each additional plugin you install could alter your security profile.
Always keep your applications updated and if possible, use the latest versions of scripts such as PHP. Newer versions of applications usually have been patched to address known vulnerabilities in previous versions.
In that regard, it might also be wise to check with your host;
- What is the minimum acceptable version of PHP to run on their servers
- How often do they update core software
- How user software updates are handled (e.g. WordPress core and plugin updates)
2. SSL Availability and Support
Secure Sockets Layer (SSL) is a protocol that governs the encrypted connection between server and web browser (e.g. your website to the visitor). Thanks to recent initiatives to increase consumer security and awareness today by search engines such as Google, web browsers today are helping to clearly identify what websites do or don’t use SSL.
If your website uses SSL, most browsers now will display an icon of a green padlock somewhere near or on the address bar for users to see. This provides a strong visual assurance of safety to the visitors on your website. This affects all websites on the internet, not just eCommerce or other high-profile websites.
When looking for a web hosting service provider, try to identify SSL support and see how easily you will be able to deploy an SSL certificate for your website.
Take for example hosts that offer AutoInstall SSL. This is one of the best SSL installation tools in the market because it not just covers DV SSL like Let’s Encrypt does but allows you to choose from the entire gamut – DV, OV or EV.
It is tools like this that can give you a pain free end-to-end experience. Let’s say you start off with a DV SSL but as your site develops you find your requirements leaning more towards an EV or OV. Something like AutoInstall SSL can give you an extremely seamless experience.
The key takeaways to note here are (a) that an SSL is practically a requirement for any website nowadays and (b) look out for an easy to use yet advanced SSL installer like AutoInstall SSL.
Some questions to ask your host about SSLs would be;
- Do you allow private SSL?
- Do you configure SSL for each domain added?
3. Backup & Restore
Most people see backups as a nice side benefit of some web hosting plans but may not be aware of how closely this feature relates to their website security. There are so many scenarios that may require you having a reliable backup and restore system in place.
At the very simplest level, some files on your website get corrupted and you need to restore previous versions from a backup to resume service. Incidences of data centre disaster are not as rare as you may think.
In 2012, half of Yahoo’s Santa Clara data centre was wiped out by a squirrel with a hunger for power lines. In 2014, Cloud provider Joyent suffered the embarrassment of an administrator rebooting every single virtual server at their data centre in one go.
The list goes on, but suffice it to say that it is a very good idea to look out for a web host which has a comprehensive backup and restore system. Try to also keep an eye out for those which have specific disaster mitigation policies spelled out in their service level agreements (SLA) as well.
Remember that these backups should be at the server level – you can implement other rudimentary backup and restoration services at the user level on your own.
To learn more about the host’s backup offerings, ask;
- How are your backup and restores carried out?
- How long is your data retention period?
- How long are your archive cycles?
4. DDoS Attack Mitigation
Distributed Denial of Service (DDoS) is an attack type that tries to bring down a web host by overwhelming it with requests. When the server faces a load too big for it to manage, service is interrupted and the attacker … um … wins?
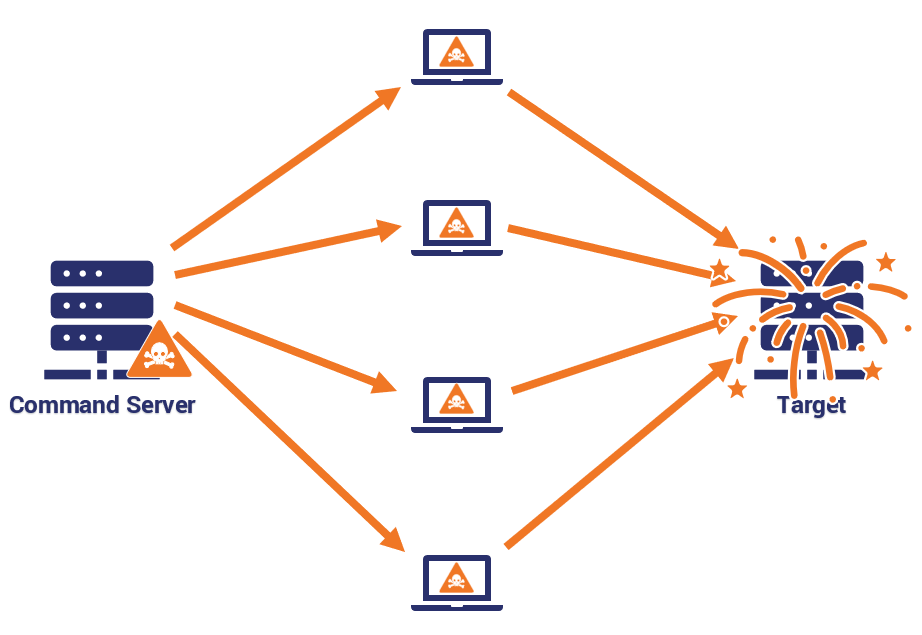
If you’re thinking of this in terms of something that you can overcome or mitigate on your own – here’s the thing; DDoS attacks have been known to be so large that even websites with massive resources such as GitHub have been brought down by them.
To prevent attacks such as this from affecting their networks, some web hosting service providers such as SiteGround and Bluehost often work with Content Delivery Networks (CDN) such as Cloudflare.
CDNs operate massive global networks of servers, which they offer to users to help them serve data faster and absorb resource-heavy attacks such as DDoS. This helps web hosting providers reduce their own server load without having to invest heavily in additional infrastructure.
Again, this use of CDNs is different at the data centre level as compared to the user level. When looking out for a secure web host, see if they have signs of working with CDNs such as Cloudflare.
To learn more about DDoS mitigation, ask your host;
- If they have a CDN partnership
- What their mitigation protocols are
- What level of support they offer in case of a DDoS attack
5. Malware Scanning
Malware is malicious software that affects computers sometimes. The results of an infection can range from mild – some rudimentary data might get stolen – to horrific – all your data gets wiped out. Servers can also be affected by Malware and when that happens, it usually isn’t a pretty sight.
Knowing how your web host defends against Malware can serve to reassure you that your site won’t suddenly crash and burn for no reason. For example, some web hosts might run daily Malware scan on their servers. Some might even go as far as to make use of account isolation so that any infections will be contained, even on the same server.
Some questions to ask your host would be;
- How often do your systems scan for Malware?
- Do you offer remote Malware scanning?
- Do you carry out file integrity monitoring?
6. Availability and Uptime
The CIA Triad (Confidentiality, Integrity and Availability, not Central Intelligence Agency) refers to an information security model that some companies use. These three elements are seen as the pillars of security and helps them form effective security policies.
In web hosting, the main concern to the web host will be availability, or uptime. (If you’re not sure what uptime is, see: What is Website Uptime?) There are many ways for web hosting service providers to assure availability. Some of these include the employment of RAID technology, hardware redundancies, network redundancies and even alternate mirror locations.
The depth in the amount of equipment and effort that a web host puts into their service affects how available your site is. Therefore, most web hosts will be able to offer you an uptime guarantee in their SLA.
Take for example the case of SiteGround; They guarantee a network uptime of 99.9% on an annual basis. If your uptime falls below that percentage, then they are committed to reimbursing you at a specific rate.
Why is this important? The fine print in the SLA often contains many caveats to the uptime guarantee a web host offers. For example, SiteGround’s SLA doesn’t cover outages in the event of Distributed denial of service (DDOS) attacks, hacker attacks, and other similar events.
Personally, I feel that the SLA is a very good indicator of how much a web host has invested into the availability of their business.
Some questions to ask your host about uptime would be;
- What are your uptime assurances?
- What happens if you breach your allowable uptime guarantee?
- What is the procedure to follow in case of excessive downtime?
7. Firewall Protection

Caption: A firewall blocks unauthorized traffic into or out of a network (courtesy of IBM)
Another thing that a web host can do to increase your security is to make prudent use of firewalls. At a data centre level, these are often physical devices dedicated to protecting whole networks from hostile or harmful traffic.
Even without taking into consideration the needs of web hosting companies, almost all organizations that deploy large numbers of devices in a network will make use of Firewalls to control, monitor and safeguard data traffic.
These are complemented by web application firewalls, just keep in mind these are not designed to protect against all types of attacks – they work at a more specific level. Web application firewalls are dedicated to monitoring and controlling web traffic that is being directed towards specific web applications
Unfortunately, firewall breaches are most commonly caused by configuration errors. Mistakes made in the configuration of a firewall can increase the risk not just of network performance impact but also represent a potential risk to the network as a whole.
Some of the questions to ask you host about would be;
- Do you implement firewalls? (If not, you may need to factor in the cost of using a third-party firewall)
- How are your firewall rules documented?
- How often are your firewall settings updated and reviewed?
Conclusion
In the never-ending quest for the perfect web host, most people will tend to prioritize one thing over another. This is natural, since all of us have different means and areas of focus. I’m under no illusion that what I’ve discussed here will influence everyone to prioritize security in a web host but at the very least I hope the points I have raised will help increase awareness.
Having dealt with technology in some form or other intimately for over 30 years, I have seen trends come and go. Security isn’t a trend, it’s a real necessity and as a website owner, your responsibility is not just to your own site, but the security of your website visitors as well.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown