Click2Gov Servers Infected with Malware that steals PCI
Local governments across the US have been reporting breaches—this is why.
A couple of weeks ago we talked about Magecart and a newly resurgent exploit called formjacking. Essentially it works like this: find a way to make a javacript injection on to a payment page that exfiltrates the information provided to an external third-party server. Magecart, specifically, has attacked Ticketmaster, British Airways and Newegg in the past month, each time refining its script to be simpler and more elegant.
But Magecart is far from the only group attacking payment pages: this week the city of St. Petersburg, the beautiful coastal city that The SSL Store calls home, announced it had been hit by formjacking after it discovered a malicious script installed on the Click2Gov server it uses to collect payments.
Click2Gov was used to take payments for:
- Utility Bills
- Parking Tickets
- Business Licenses
- Building Permits
- Civil Citations
The city of St. Petersburg was informed of the issue on September 27th and had rectified the situation by 1:30 PM on the next day, September 28.
The breach only affected users of the online Click2Gov system who made payments for utility bills, parking tickets, business licenses, building permits, or civil citations by credit card between Aug 11, 2018 and Sept 25, 2018. Any payments made in person, via the phone system, via E-Check or to any other city systems were not impacted.
So, what is formjacking? Was the St. Pete breach formjacking? And if not, how did it happen?
Let’s hash it out…
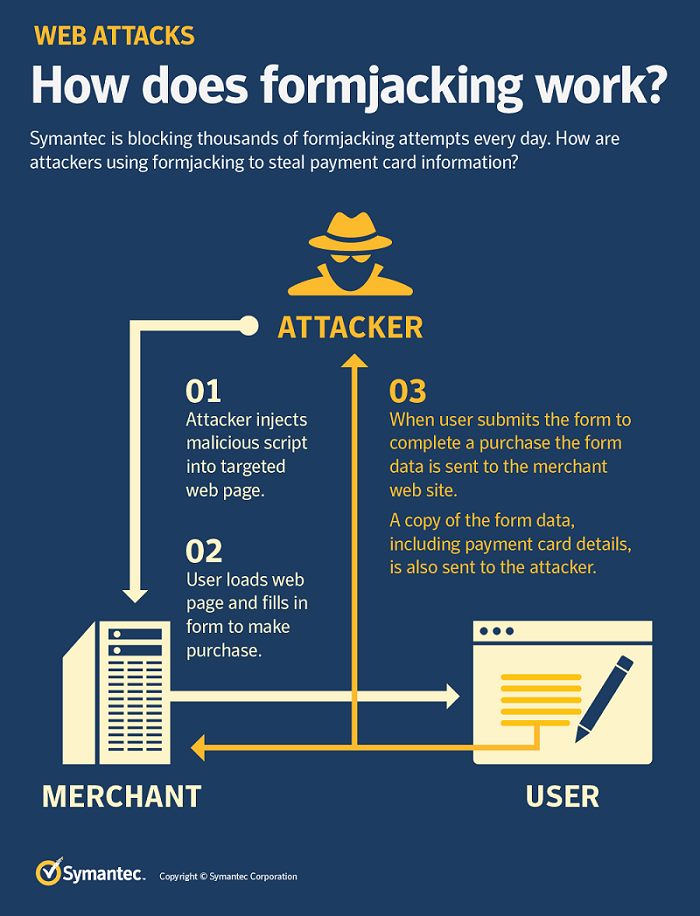
What is Formjacking?
Formjacking has seen a bit of a renaissance lately. It’s an exploit where attackers make a malicious javascript injection into a web page’s forms, like on a sign-up page or a checkout page, with fields where you enter information.
Formjacking is a term we use to describe the use of malicious JavaScript code to steal credit card details and other information from payment forms on the checkout web pages of e-commerce sites. Formjacking is not a new technique, but recent campaigns are interesting as they are large, sophisticated, and have increased dramatically since mid-August 2018.
Once the malicious script has been injected, it works like this:
- A victim enters information into a form
- The victim clicks “Submit” (or its equivalent)
- The script gathers that information and sends it to the attacker’s server
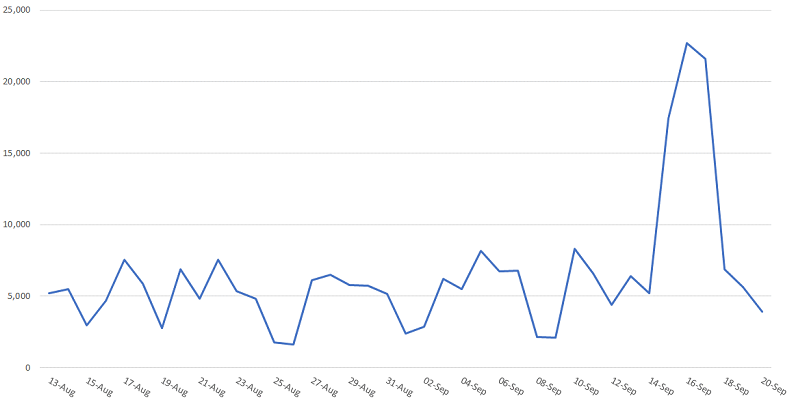
Formjacking isn’t new, but recently there’s been a major uptick in it. A lot of that can be attributed to Magecart. Since August 13, Symantec’s telemetry reports that 248,000 attempts at formjacking have been blocked (an average of 6,368 per day), with the bulk of that activity (36%) occurring between September 13-20, which coincides with the British Airways and Newegg incidents.
Formjacking is a technique that is best used to target checkout pages, places where customers are going to input payment card information. When Symantec took a sample of 1,000 attacks committed between September 18-20, it found that 57 different websites had been impacted, mostly online retailers. And all over the world, too.
Australia. Italy. France.
We’ve been paying more attention to the high profile Magecart attacks like British Airways, Ticketmaster and Newegg, but any websites that process PCI is potentially a target. We say this a lot: SMBs are targeted with an alarming frequency.
Case in point, the Click2Gov attacks.
Infecting Click2Gov servers was brilliant, but it wasn’t formjacking
One of the things I have been most impressed with regarding these payment page exploits is just how clever they are. In Magecart’s case the script was likely added by infecting one of the site seals that was being displayed on checkout pages. In the case of the Click2Gov breaches, while the same ends were accomplished the means were dramatically different. Whereas Magecart uses a Javascript injection, the Click2Gov servers were hit with a malicious webshell variant and a couple of tools. However, both methods allowed a single infection to potentially hit dozens of websites. The ratio of work to reward is staggering.
Also, my coworkers think I’m turning into a black hat.
Click2Gov is a web-based personal payment portal that local governments can use to accept payments for things like utility bills and parking tickets.
As FireEye mentions in its report:
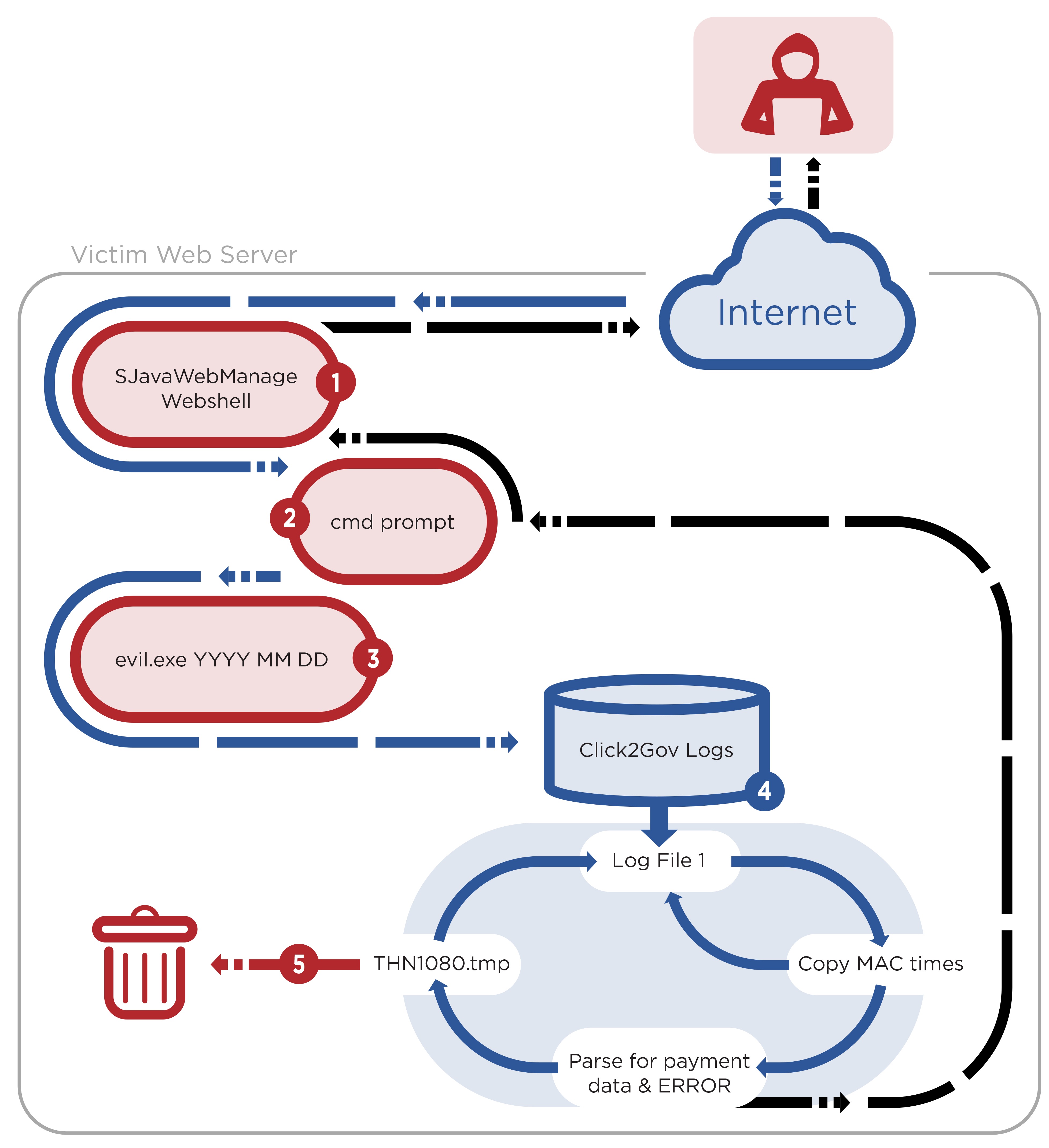
The first stage of the campaign typically started with the attacker uploading a SJavaWebManage webshell to facilitate interaction with the compromised Click2Gov webserver. Through interaction with the webshell, the attacker enabled debug mode in a Click2Gov configuration file causing the application to write payment card information to plaintext log files. The attacker then uploaded a tool, which FireEye refers to as FIREALARM, to the webserver to parse these log files, retrieve the payment card information, and remove all log entries not containing error messages. Additionally, the attacker used another tool, SPOTLIGHT, to intercept payment card information from HTTP network traffic.
Now, as we mentioned, the methods employed by Magecart and the Click2Gov attackers differ pretty substantially, but the premise is the same, by infecting a specific page the attacker can easily steal loads of information with minimal effort.
While the exact method used to initially compromise the Click2Gov servers is unknown, it was likely done with an Oracle Web Logic exploit. The attackers then uploaded a malicious variant of a webshell that had been crafted to avoid detection. Without getting too granular, the webshell gave the attackers persistence, which could then be used to restart the targeted payment module (like the one in St. Petersburg) into a debug mode where it would log payment card information (PCI) in plaintext.
The attackers used two tools Firealarm and Spotlight, to assist in the exfiltration of PCI. The first, Firealarm, is a datamining utility. While the payment module is in debug mode and logging PCI in plaintext, that doesn’t mean that all of the information being logged is useful to the attackers. So, Firealarm’s job is to sort through all the plaintext data, grab the PCI and format it so that it can be printed to the console.
Here’s the data that Firealarm parses:
- medium.accountNumber
- medium.cvv2
- medium.expirationDate.year
- medium.expirationDate.month
- medium.firstName
- medium.lastName
- medium.middleInitial
- medium.contact.address1
- medium.contact.address2
- medium.contact.city
- medium.contact.state
- medium.contact.zip.code
And here’s a visualization of how it works.
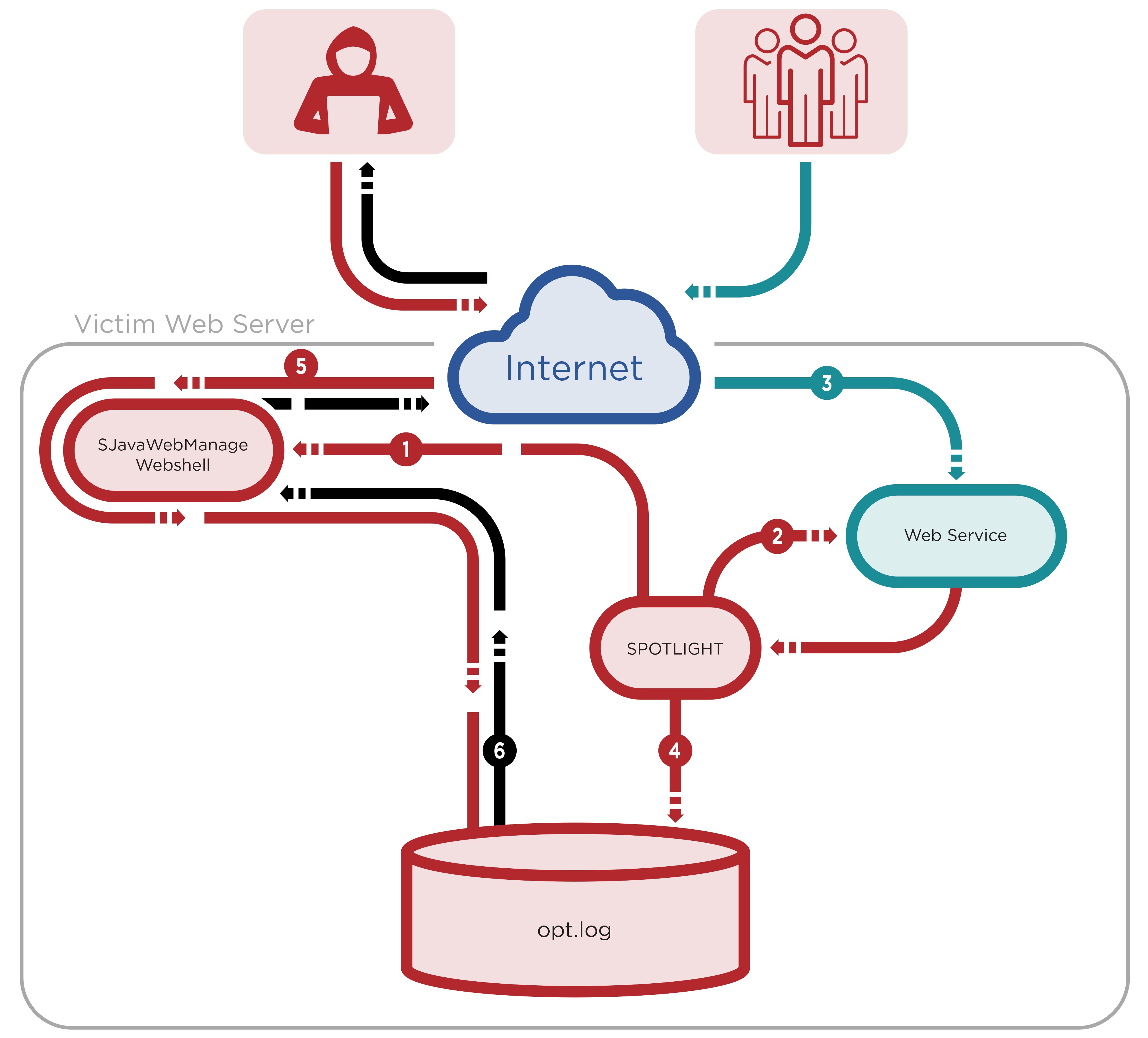
The other tool being used by the Click2Gov attackers is called Spotlight. Spotlight is a network sniffer that was uploaded after the initial infection.
This tool offered the attacker better persistence to the host and continuous collection of payment card data, ensuring the mined data would not be lost if Click2GovCX log files were deleted by an administrator.
Once again, focusing on just the concepts at play, in addition to providing redundancy in the event of detection, Spotlight also works as a socket listener. Basically it works like this, Spotlight saves a buffer of received packets from TCP port 7101, which is used for application resolution from the internal network to the Click2Gov server. Once one of two conditions is met, either the file reaches a certain size or begins with a certain string, the internal buffer data is searched for:
- <op:AccountNum>
- <op:CSC>
- <op:ExpDate>
- <op:FirstName>
- <op:LastName>
- <op:MInitial>
- <op:Street1>
- <op:Street2>
- <op:City>
- <op:State>
- <op:PostalCode>
The data is then extracted, formatted and Base64 encoded so that the attackers can easily extract it using their variant of the webshell.
Here’s a visualization:
Was this Magecart?
No. While the crux of what Magecart is doing is very similar to this, Magecart seems to possess a level of nuance and sophistication that is missing in these exploits. Magecart has been refining the script it uses with each successive attack. The scripts are customized for their targets and become shorter and more efficient every time. In the Newegg breach the script was just 8 lines (15 beautified) and managed to collect, format and exfiltrate data the moment a mouse button or touch screen press is released.
Beyond that, Magecart actually managed to hide in its targets HTTPS traffic as it exfiltrated the information which made it even more difficult to detect. By comparison the Click2Gov attackers went the other way, using a packet sniffer to sort through HTTP traffic and collect even more information.
So, who are the Click2Gov attackers? FireEye assesses, with moderate confidence, that it was likely a group as opposed to a single actor.
Either way, it’s highly advisable that organization implement some form of file integrity monitoring to help you maintain visibility over any static content or code that generates dynamic content on your web servers for evidence of unexpected modifications.
Additionally, it’s considered best practice to only run web services accounts with the least possible privileges/permissions.
This is likely not the last we’ve seen from this group of attackers.
As always leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown