Browser Fingerprinting: The Good, Bad & Ugly
Browser fingerprinting is a controversial user data tracking technique. On the one hand, companies like it for security. On the other, it can be a data privacy issue for users and compliance concern for organizations. Let’s see how device fingerprinting works and why it’s such a divisive topic
Editor’s Note: This is a guest blog contribution from Tamas Kadar, CEO at SEON, who shares his expert perspective on browser fingerprinting.
Did you know that someone could identify who you are without cookies and without you entering any information about yourself? Yes, it’s entirely possible to get an idea of who you are simply by using a technique called browser fingerprinting.
But what is browser fingerprinting and how does it work? Why do companies like using it? And what data privacy-related issues and compliance concerns does this method pose for users and businesses?
Let’s hash it out.
What Is Browser Fingerprinting?
Browser fingerprinting, or what’s also known as device fingerprinting, is a set of data collection techniques that uniquely identifies users by their devices’ specific attributes. The combination of these attributes allows companies to identify unique users based on seemingly innocuous data such as their device settings or operating systems.
Much like the name implies, browser fingerprinting is reminiscent of how your physical fingerprints uniquely identify you from other people. That’s because everyone has unique physical fingerprints — the unique ridges, lines and swirls that make your fingerprints your own. Even identical twins, whose genes are identical, have unique fingerprints. Similarly, companies can use this data to track unique users’ browsing habits and create individual profiles that they can use for various purposes (such as advertising or cybersecurity functions).
Unlike traditional web cookies, which place one or more files within users’ browsers, browser fingerprinting is done by website or app owners by adding specific JavaScript to their websites.
Essentially, browser fingerprinting doesn’t look at what you do online or what kind of information you provide. It only looks at how you connect to a website by looking at the configuration of software and hardware you use, such as:
- Operating system,
- Browser version,
- Active plugins,
- Time zone and language settings,
- Screen resolution, and
- HTML5 canvas properties.
This list is just a handful of examples. There are hundreds of other data points that browser fingerprinting techniques can detect to help create a unique ID that can be linked to you and you only.
4 Common Browser Fingerprinting Methods
Not sure what sorts of browser fingerprint detection methods exist? A few of the common browser fingerprinting techniques include:
- Canvas fingerprinting: Websites written in HTML5 contain a code element called the canvas, which draws graphics on a web page. It also generates data such as the font size or active background colour setting, which come into play when creating a unique user ID for tracking.
- iOS or Android fingerprinting: A piece of JavaScript code in a web app can also return useful data such as the device’s local language, screen brightness setting, MAC address, etc.
- Audio fingerprinting: The complexity of the Web Audio API allows fingerprinting tools to look at values such as the AudioBuffer, Oscillator or Compressor to help identify users.
- WebGL fingerprinting: WebGL is a JavaScript API that also renders on-screen images and graphics. How it does this can point to information about a device’s graphic system.
And browser fingerprinting works. According to Panopticlick, a website that helps audit online protection, only 1 in 286,777 connections will share the same browser fingerprint as another user.
In short: it’s a lot easier for websites to track you and your online activities than you may think. But is it always bad? And what happens when the technology falls into the wrong hands? Let’s explore those questions in the sections below.
The Good: Browser Fingerprinting Is a Useful Cyber Security & Fraud Protection Method
There is one area where the technology is undeniably useful: browser fingerprinting in the context of fraud detection.
Browser fingerprinting becomes a security tool. Companies can use your device information to get an idea of who you are without necessarily tying it to real-life personal data. They only look at your software and hardware, so you’re not actually identified as an individual person.
Identifying a browser fingerprint is useful when looking at suspicious activity on your account, for example, to flag an attempt to hack your account or to purchase something without your authorization.
Here’s a quick example of how it would work from a fraud prevention perspective:
- You connect to a website.
- A JavaScript code captures all your hardware and software data.
- The unique configuration is assigned an ID.
- The ID is tracked, in combination with an IP address, to check for suspicious activity
It’s worth noting that there are limitations to how precise browser fingerprinting can be. For instance, the default Android web browser identifies itself as Safari to make compatibility easier. So, only focusing on the browser version, in that case, could lead to false assumptions about a user’s device.
While fingerprinting works with incognito or private browsing, fraud protection and cybersecurity vendors do have to combine it with other analysis techniques to get a clearer picture of who the visitors truly are.
The Bad: Concerns Regarding Loss of Privacy
Browser fingerprinting for security is completely legal (so long as companies abide by data privacy and security regulations). In fact, the European Union’s General Data Protection Regulation (GDPR) Recital 47 specifically states:
“The processing of personal data strictly necessary for the purposes of preventing fraud also constitutes a legitimate interest of the data controller concerned. The processing of personal data for direct marketing purposes may be regarded as carried out for a legitimate interest.”
Just like web cookies, tracking is allowed as long as businesses are transparent about their policies (i.e., how they collect and use the information). This responsibility falls on the shoulders of businesses who have to ensure their tracking remains compliant and that users give their informed consent. Using the GDPR as an example once more, this is how GDPR Article 4(11) defines user consent:
“Any freely given, specific, informed and unambiguous indication of the data subject’s wishes by which he or she, by a statement or by clear affirmative action, signifies agreement to the processing of personal data relating to him or her[.]”
This isn’t to say that users will be happy about being tracked. There is definitely a trade-off between security and privacy online. Users concerned with how their devices are tracked may wish to opt out of browser fingerprinting manually.
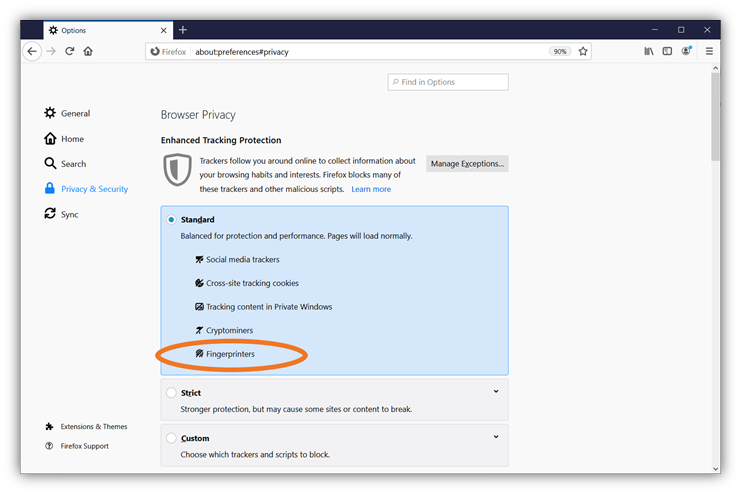
But a growing number of anti-fingerprinting browsers are also gaining popularity worldwide. There is no shortage of extensions designed to block fingerprinting JavaScripts. Tor browser usage is booming, and companies like Mozilla Firefox, who have always put privacy front and centre, now offer built-in fingerprinting blockers within their browser:
Developers who need to test multiple browser configurations can also use tools like a Chrome User-Agent (UA) spoofing extension that lets you change your user agent manually. A user agent is an HTTP header that provides information about a user’s web browser to the site or web app they connect to.
(One quick note about Chrome and data collection: Google is currently implementing changes to how it tracks user data with its new Federated Learning of Cohorts (FLoC) technology and attempting to reduce reliance on User Agents. You can read more about it on Google’s Developer blog).
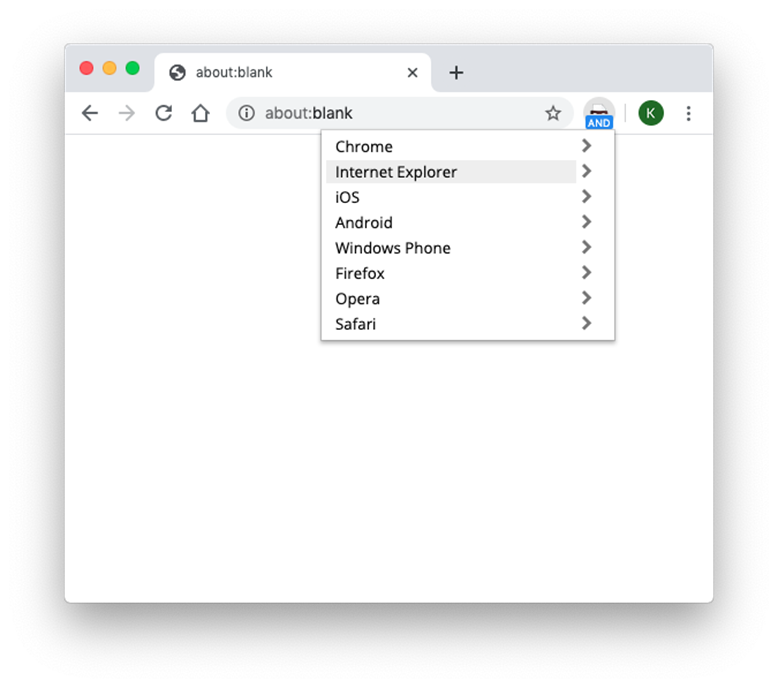
For a browser to connect with the website, that HTTP header (i.e., the UA or UAS browser agent string) must be present for each request header. And not all UA strings look the same — the specific format varies from one browser to the next. So, being able to change it is a useful tool for users and web developers alike. For the former group, it may improve user privacy; for the latter, it has very tangible uses and applications in web development.
Even more advanced: you can use browser extensions such as Trace to protect you against multiple advanced tracking techniques. Otherwise, you can use the Tails browser, which is designed to access Tor from an external hard drive to:
- Protect yourself from canvas fingerprinting,
- Remove Google headers,
- Hide JavaScript plugins,
- Disable the battery status API, and
- Spoof a MAC address.
These are more sophisticated solutions, often favoured both by privacy enthusiasts and, sadly, cybercriminals as we’ll see in the next section.
The Ugly: Device Fingerprint-Spoofing Tools Cybercriminals Love to Use
Another trend we’ve witnessed is the rise in advanced anti-device fingerprinting software tools. These programs take browsers spoofing to the next level, allowing users to inject JavaScript code snippets into visited websites to modify the behaviour of a page. They tend to be sold as browser extensions, but can also be shipped into modified browsers where the extensions come pre-installed. They can still be detected with a string comparison.
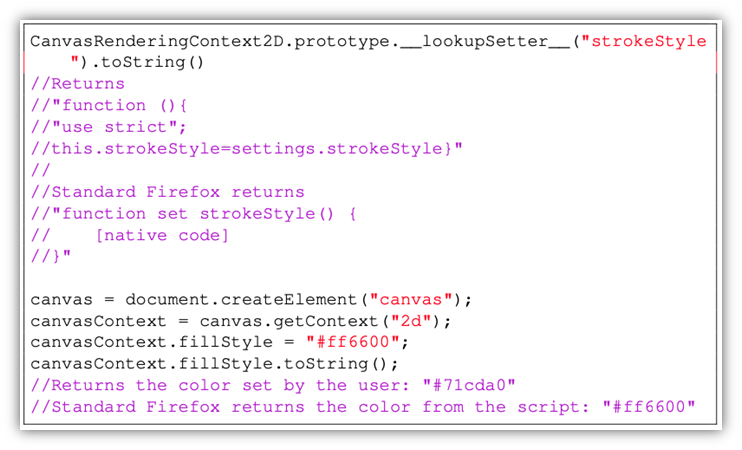
Then there are native tools, which let you modify the JavaScript functions to such a deep level that even string comparison won’t work. Browsers like Mimic will even add noise creation. This is a feature that modifies values at run-time to confuse the tracking. In the Mimic browser, this is allied canvas poisoning, which can fool canvas fingerprinting.
Need even more advanced features? Then you’ll have to simulate a fake user environment. This is possible with a research tool called Blink, which recreates a whole virtual machine stack every time it launches. This allows you to change fonts, plugins, browsers, user agent strings, time zones, or even operating systems.
The question is: why would anyone purchase these tools, which aren’t cheap or easy to set up? They are clearly targeted and marketed to a specific clientele that needs to spoof various environments quickly and at scale. It’s no secret that the only real use case is for online fraud or cybercrime such as money laundering.
Fingerprinting, Spoofing & Privacy: It’s an Arms Race
Regardless of which side of the fence you’re on when it comes to browser fingerprinting, the fact of the matter is that the tool sophistication on both sides increases by the day. Every new method for fingerprinting is soon thwarted by a new technology that’s designed to protect identity. But companies have very little incentive to stop knowing who their users are, whether it’s for advertising or for cybersecurity reasons.
There is simply no way of knowing where the technology is headed, but it’s important to understand where we are at now and how browser fingerprinting is used today. We hope this article was a good primer on the topic and will make you think about how your information is shared online.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown