Browser Updates Round-Up: Continuing the Push for HTTPS Everywhere
Google Chrome and Mozilla Firefox are updating how SSL/HTTPS sites are displayed to users, continuing their initiative to move all internet traffic to HTTPS
Google and Mozilla have recently announced several changes to how they will display HTTPS websites in Chrome and Firefox, respectively. Most of these changes are part of the push the browsers have been talking about for a few years – encouraging all websites to move from HTTP to HTTPS.
Here’s a quick overview of six noteworthy changes the browsers are making, and what webmasters and internet users need to know.
Let’s hash it out.
1) Chrome to Force HTTPS or Block “Mixed Content”
For years, “mixed content” has been the bane of web developers all over the world – after switching your site to use HTTPS, there were often images, scripts, or other files still loading via HTTP that would trigger “mixed content” security errors in the user’s browser like this:
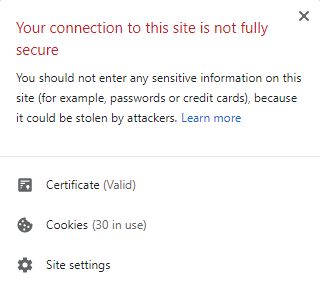
As Google explains:
“HTTPS pages commonly suffer from a problem called mixed content, where subresources on the page are loaded insecurely over http://. Browsers block many types of mixed content by default, like scripts and iframes, but images, audio, and video are still allowed to load, which threatens users’ privacy and security. For example, an attacker could tamper with a mixed image of a stock chart to mislead investors, or inject a tracking cookie into a mixed resource load. Loading mixed content also leads to a confusing browser security UX, where the page is presented as neither secure nor insecure but somewhere in between.”
Starting with Chrome version 79 (scheduled for release in December 2019), Google will gradually implement a plan to change how mixed content is handled:
- Version 79: Users will be able to manually block or unblock mixed content.
- Version 80: Mixed audio and video will be auto-upgraded to HTTPS – if they are unreachable via HTTPS they’ll be blocked. Mixed images will load but will show a “Not Secure” warning in the address bar.
- Version 81: Mixed images will be auto-upgraded to HTTPS – or blocked if they can’t be loaded via HTTPS.
Ultimately, this doesn’t change what webmasters need to be doing – ensure that all resources (including images, video, and audio) load over HTTPS 100% of the time.
2) Firefox Marks All HTTP URLs as Not Secure
Following in Chrome’s footsteps, Firefox is now marking all HTTP webpages as “Not Secure”. Over the past couple of years, Firefox has started warning users if an HTTP page contained a login or other form, but now Firefox will show the warning on all HTTP pages.
Starting with Firefox version 70 (scheduled for release in October), users will see a warning like this on all HTTP pages:
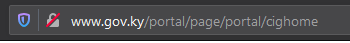
If you click the padlock, you’ll see a message like this:
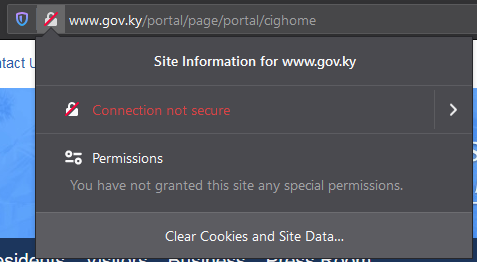
From there, you can click for more details to see this:
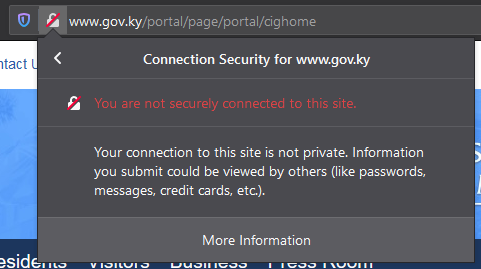
3) Firefox Begins Transition to DNS-over-HTTPS
Starting in September, Firefox began a gradual rollout switching users to use DNS-over-HTTPS (DoH) by default. If their plan goes as hoped, they’ll have all US users switched over by 2020.
Last year, Firefox explained why they were starting efforts to switch to DoH:
“Because there is no encryption, other devices along the way might collect (or even block or change) [DNS] data too. DNS lookups are sent to servers that can spy on your website browsing history without either informing you or publishing a policy about what they do with that information…Our first effort to upgrade the privacy of DNS is to implement the DNS over HTTPS (DoH) protocol, which encrypts DNS requests and responses.”
This decision hasn’t been without controversy, though, as some cybersecurity experts believe that DoH is going to cause more problems than it solves.
Firefox’s DoH uses CloudFlare’s DNS service by default, but users can switch to an alternate service if they prefer.
4) Google Tests DNS-over-HTTPS
Starting with Chrome version 78 (scheduled for release in October) Google will begin testing DoH for certain DNS servers:
“This experiment will be done in collaboration with DNS providers who already support DoH, with the goal of improving our mutual users’ security and privacy by upgrading them to the DoH version of their current DNS service. With our approach, the DNS service used will not change, only the protocol will…The goals of this experiment are to validate our implementation and to evaluate the performance impact.”
While Google’s a bit behind Firefox in rolling out DoH, it seems likely that Chrome will roll this out to most/all users in 2020.
5) Chrome Hides Protocol (http:// or https://) From URL
Google recently made a change to how URLs are displayed in the address bar – hiding the http:// or https:// from the beginning of the URL. At first glance, this change might sound like Chrome is reducing the importance of HTTPS, but it’s actually the opposite. This change is part of Google’s push to make HTTPS the default protocol for the entire web.
Research has shown that when it comes to internet security, positive indicators are valuable, but users pay more attention to negative indicators. That’s why Google has implemented a plan to make HTTPS the default and to show warnings for HTTP URLs. This change is simply the next step in that plan: HTTPS is normal (so normal it’s not shown) but HTTP triggers an error.
HTTPS webpages now display like this:
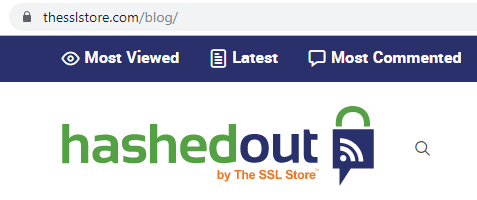
While HTTP pages look like this:

6) Chrome & Firefox EV Display Changes
Unlike the first five changes, this one isn’t about getting more sites to switch to HTTPS – it’s a change to how sites with EV SSL certificates are displayed. Chrome and Firefox are moving the EV display (verified company name) from the address bar to the certificate details display. Users will now be able to view the EV company details by clicking on the padlock to get a display like this:
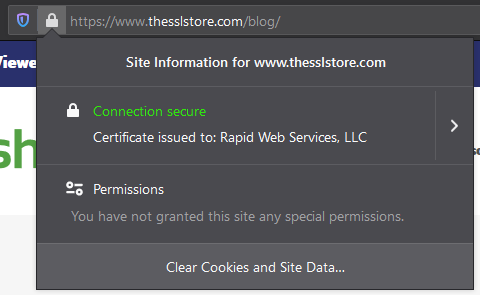
They can also click to view additional certificate details like this:
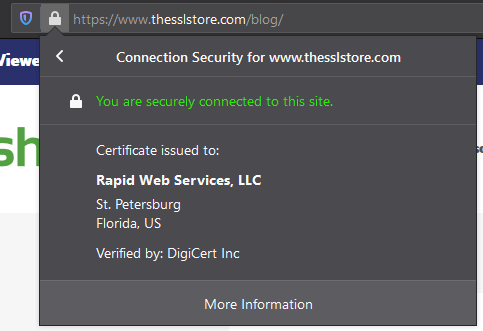
You can think of this EV display a bit like a passport: you don’t wear it on your sleeve, but it’s there anytime identity verification is needed. If a user is unsure about a website, they can quickly check the EV details to see what legal entity owns and operates the website.
In addition to being available for customers to check anytime they’re unsure about a website, EV certificate details are used by other entities for identity verification:
- Anti-virus software uses EV certificate details to distinguish reputable websites from phishing websites.
- Governments (especially in Europe) are increasingly requiring companies who transact online to provide verified identity information via an EV SSL certificate and/or an LEI.
For the record, we believe that browsers should make verified identity information such as EV details more prominent, not less. Unless/until a better solution is implemented, EV SSL is still the best solution out there for users to verify the legal entity that operates a website.
That being said, these changes don’t change the fundamental purpose an EV SSL certificate fills: a way for internet users, security software, and governments to verify the legal entity that operates a website.
With the explosion of online crime, regulators are increasingly expecting companies to present verified identities online – we believe that EV SSL (and similar tools) will be an important part of the internet for years to come.
The Bottom Line
None of these SSL UI changes are game changers for users or for website owners. Most of these changes are incremental changes gradually moving more users and websites to HTTPS – on balance, that’s a good thing for users, for website owners, and for the internet.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)






 (3 votes, average: 4.00 out of 5, rated)
(3 votes, average: 4.00 out of 5, rated)






5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown