Browser Watch: Chrome HTTP Warning Spreading to More Pages
The Chrome HTTP Warning is continually raising its expectations for page security.
If you are a regular Chrome user, you have likely noticed the frequent changes to the browser’s SSL UI. The primary padlock icons changed last year, and a few months ago a Chrome HTTP warning was added to pages.
These changes are part of a major project which will re-invent our understanding of connection security as the web’s adoption of HTTPS picks up.
This means that as more of the internet’s traffic becomes encrypted, Chrome will continue to raise their expectations and make the unsecure nature of HTTP connections more prominent.
Late last week, Chrome announced the next step in this project.
The “Not Secure” warning, which currently appears on HTTP pages with login/credit card fields, will be shown in two more scenarios later this year.
When Chrome 62 releases (around October) the “Not Secure” warning will appear on any HTTP page if you start typing data into the page. This includes any HTTP page with text field, such as a search function, contact form, or address box, will trigger the warning.
This warning will be ‘dynamic’ and only appear once the user starts typing data into a field. This behavior is demonstrated in the below gif.
In addition, the “Not Secure” warning will appear on all HTTP pages when you are in “Incognito” mode, which provides a private session.
In the announcement for this latest change, Chrome engineer Emily Schechter wrote “when users browse Chrome with Incognito mode, they likely have increased expectations of privacy.”
This table summarizes the changes:
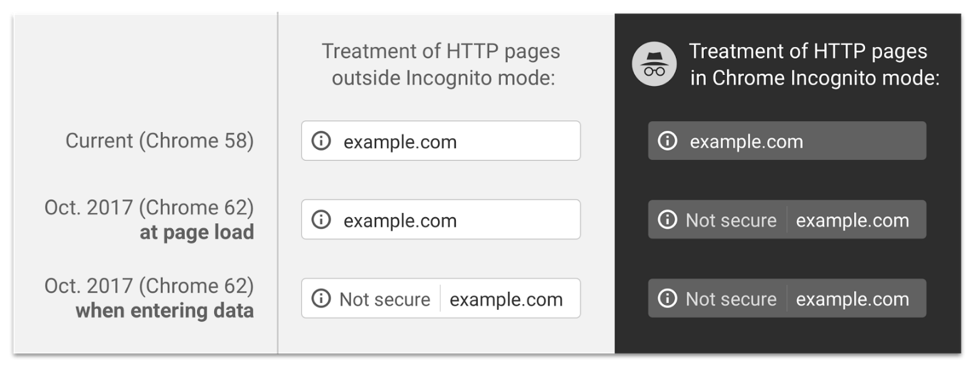
Schechter also reminded us that Chrome’s plan is to “eventually” show the “Not Secure” warning for ALL HTTP pages in all contexts. Chrome’s team has not given specifics on when this will happen, but we know it is tied to HTTPS adoption.
A few versions ago, Chrome added this “Not Secure” warning for HTTP pages with password or credit card forms. This has already led to a 23% reduction in the number of navigations occurring to such pages – evidence that the indicator has been a strong motivator to site administrators to adopt HTTPS.
If you operate a website without HTTPS and don’t yet have a transition plan, you should start developing one as soon as possible.





































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown