Cyber Attacks Hit the City of Johannesburg and South African Banks
Hackers attacked several key South African organizations last week, impacting everything from workers’ paychecks to 112 emergency calls
Note: This article, which was originally published in 2019, has been updated to include related news & media resources.
“Not all treasure’s silver and gold, mate.”
Jack Sparrow
Johannesburg may be nicknamed the City of Gold, but when thieves attacked the City of Joburg and several South African banks last week, they weren’t looking for silver and gold. They weren’t even looking for rand notes. No, these bank robbers were looking for the modern criminal’s currency of choice — Bitcoin.
Here’s what they did, and how you can protect your organization from similar attackers.
Let’s hash it out.
Attack #1: Ransomware Attack Brings Down City of Johannesburg Services
Late in the evening of Thursday, Oct. 24th, the City of Joburg announced that their network had been breached by hackers:
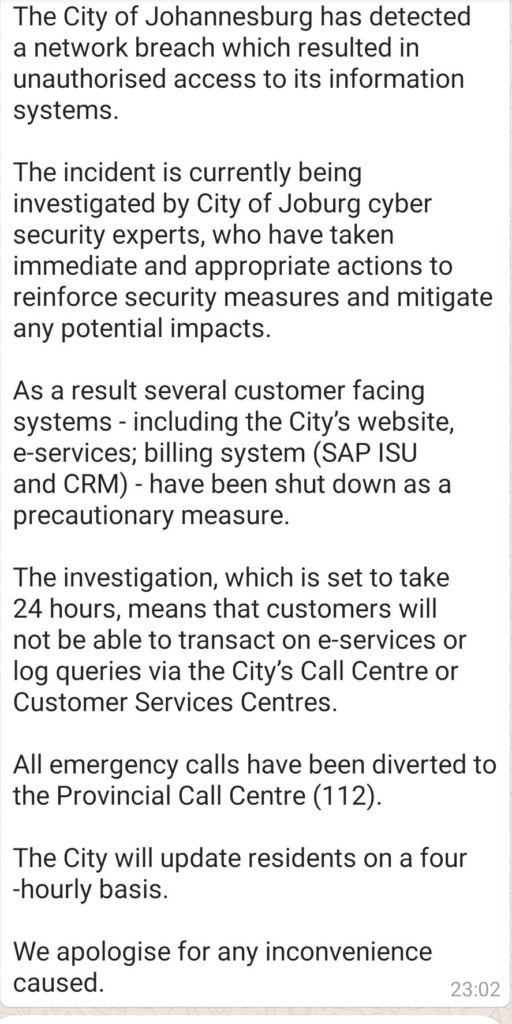
As details slowly trickled out over the next few days, we found out that:
- The attack was a ransomware attack (which typically means key systems and/or data is encrypted and locked down by malware).
- Key city systems were shut down, including online services, bill payments, and more.
- Other services were impacted, including the call center which handles 112 emergency calls (911 for you Americans reading this).
- The hackers were demanding a ransom of four Bitcoins, which equals about R500,000 South African Rand or $37,000 USD.
- The hackers claimed to have backdoors into the city systems and threatened to upload the hacked data online.
- The city has announced they “will not concede to their demands” and are “confident that we will be able to restore systems to full functionality”.
- The city noted that the attack was carefully “timed to coincide with all City month end processes affecting both supplier payments and customer payments.”
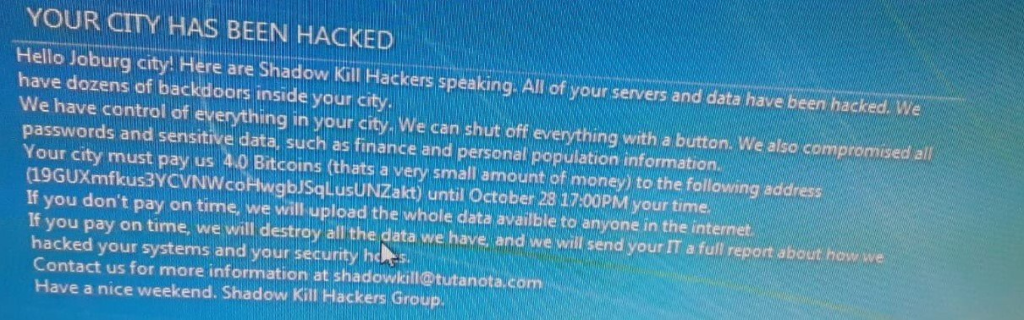
The response and investigation are ongoing, but it’s clear that this was a major attack with huge impacts to many citizens. Fortunately, the response team is making good progress at recovery.
Attack #2: DDoS Attackers Hit Multiple Banks, Demand Bitcoin Ransom Payments
Around the same time the ransomware attack hit Joburg, DDoS attacks were launched against several large South African banks, including Standard Bank and ABSA. This was a different type of attack, but the hacker’s goal was the same — to demand a Bitcoin ransom from the victim.
As the acting CEO of the South African Banking Risk Information Centre (SABRIC), Susan Potgieter, explains:
We must emphasize that DDoS attacks like this one do not involve hacking or a data breach and therefore no customer data is at risk. It does however, involve increased traffic on networks necessary to access public facing services. This may cause minor disruptions.
In ransom-based DDoS attacks, the hackers typically attack the website then demand a ransom payment of Bitcoin before they will cease their attack. In many cases, though, organizations find a way to boost their defenses rather than pay the ransom.
Banks reported that some transactions were delayed and some services experienced intermittent downtime due to the attacks. Like the Joburg attack, these DDoS attacks were carefully timed for maximum damage — the attacks struck on payday, resulting in some delayed paychecks across the country.
Everyone Is a Target (And Not Just Big Silicon Valley Firms)
Hackers don’t discriminate. They don’t care if you’re in Silicon Valley, Johannesburg, or anywhere in between — you’re a target.
This is the Namib Desert — I live right there where the desert meets the ocean. (It’s incredible — you should come visit sometime!)
You might say I live in the middle of nowhere. But hackers don’t care about that — they’ll target anyone they can extort, steal, or blackmail to their benefit.
That’s why cyber security is critical for every business — whether you’re a big bank or a one-man shop, whether you’re in London, Joburg, or even the Namib Desert!
Here’s How You Can Protect Your Organization Against Similar Attacks
We don’t yet know the full technical details of how these attacks were carried out, but we do have a few key clues:
- The City of Joburg attack was a ransomware attack — these are most commonly delivered via phishing emails.
- The SA bank attack was a DDoS attack against the banks’ websites and online services.
These are both very common, typical attacks… ones that every organization should be prepared to defend against.
How to Protect Your Website Against Attackers
Website security is a huge topic, with new attack vectors, vulnerabilities, and tools surfacing every day. Sometimes it might seem that it’s an insurmountable task to keep up with the latest website security needs.
But there’s good news: If you’re a small business (without a dedicated security team), you can defend against the most common attacks by implementing just a few best practices:
- Use HTTPS everywhere. Make sure that every URL on your site (including subdomains for webmail, control panel access, etc.) uses HTTPS… not HTTP.
- Update, update, update. Religiously update your website software (for example: WordPress and associated plugins and themes) to ensure you’ve got the latest security patches to defend against recently discovered vulnerabilities.
- Use a managed web application firewall. A web application firewall, or WAF, uses a set of up-to-date rules to identify and block malicious traffic. It can block DDoS attacks (like the one that hit the banks last week) as well as other common attacks such as SQL injections.
- Backup regularly. Backing up your website regularly (and storing the backups off-site) means you’re prepared if disaster strikes. If you’ve got a recent backup of your website, you can quickly restore service after ransomware or other attacks.
- Scan & monitor. If there’s a security issue with your website, you want to be the first to know. That’s why it’s important to setup daily scans for malware, vulnerabilities, or other issues. As the saying goes, and ounce of prevention is worth a pound of cure.
How to Defend Against Phishing Attacks
With phishing attacks up 269% in just one year, they’re a critical concern for every business. Phishing attacks are a form of social engineering — they’re more about tricking users than they are getting past technical defenses. That means you need a different approach to defend against these attacks – you can’t rely only on technical defenses.
Here are four proven ways you can defend your organization against phishing attacks:
- Turn up your spam filters. Ensure that you’ve got spam filters turned on and optimized for all of your employees’ inboxes. This will catch phishing emails before they’re even seen.
- Use SPF, DKIM, & DMARC. These protocols are used to help your systems detect and flag (or block) emails that are coming from a spoofed domain. They’re especially helpful for catching phishing emails that look like they’re coming from your own company domain.
- Implement email signing certificates. In addition to enabling encryption for sensitive data, email signing certificates make it easy for your staff to verify whether an email really came from the address it shows in the “from” field. Email certificates are especially helpful for combating spearphishing attacks.
- Train all of your employees. Last, but certainly not least, implement a program to train all employees to recognize and correctly handle phishing emails. Be sure that your training includes showing examples of phishing emails so employees know what to look for.
Recent Related News
Updated on April 29, 2021




































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)














5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown