Re-Hashed: Phishing Email Examples — The Best & Worst
Here are the best and worst phishing examples and scams we’ve seen lately — send us some of the best and worst you’ve seen!
Unfortunately phishing has become so prevalent that most of us have grown sort of jaded. Case in point, we pass around phishing email examples at our office. It’s not uncommon to get an email from a coworker with a subject line like “check out teh pheesh” and a screenshot of a questionably worded request to change a password or some such nonsense.
Even referring to a phishing email as phish kind of undermines what a pernicious threat phishing actually is. After all, if you’ve ever read our phishing statistics article, you know that it’s a big issue. Phishing was a factor in 22% of the confirmed data breaches investigated and reported in Verizon’s 2020 Data Breach Investigations Report (DBIR). That means that phishing was involved in nearly one in four data breaches.
Still, call it gallows humor, but sometimes phishing emails can be objectively funny. And sometimes they can be deathly serious — when they’re constructed well enough to be convincing. . For example, when cybercriminals use email spoofing to make their emails appear legitimate. And, nowadays, cybercriminals are even using the COVID-19 pandemic as a way to phish companies and individuals.
So, today, we’re going to look at some phishing email examples — the best and the worst. And then we want to hear from you. At the end, we’ll ask you to send some of your best and/or worst phishing examples and we’ll all learn from and/or have a laugh at them, too.
Let’s hash it out.
Phishing Email Examples: The Best
Now, before we go any further — and for the sake of our comments section — we are by no means saying any of these are the greatest or worst of all-time. I would be skeptical of anyone who claimed they could make that evaluation. And I’m not sure what criteria it would even be based on.
If you removed anything with a trace of subjectivity you would have to quantify it in terms of actual damage caused. For Facebook and Google, the total costs associated with one multi-email phishing email scam surpassed $100 million. And in some cases, like John Podesta and the Democratic National Committee, you really can’t put a number on that kind of damage.
My point is this: don’t overthink it. These phishing email examples are archetypal in nature and are meant to illustrate the kinds of tactics that phishers use. They’re also taken from our own email servers (and were shared by our employees from their personal email accounts, in some cases). This is what phishing looks like in the wild.
With that out of the way, let’s looking at some phishing email examples.
Brand Phishing Email Examples
American Express
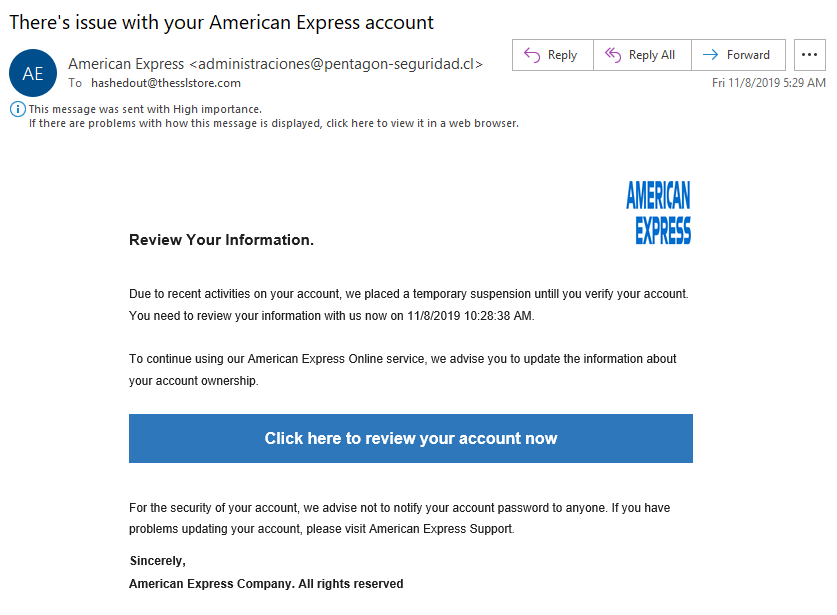
As far as phishing email examples go, this one isn’t too bad (although the American Express logo appears distorted). Sometimes, simple is better when it comes to trying to make a fake email appear legitimate. The attacker changed the sender’s display name to appear as American Express, which means that if the recipient didn’t bother to check the email address itself, they may not realize that it is coming from an email address from pentagon-securidad.cl instead of an americanexpress.com domain registered email address.
The message creates a sense of urgency by warning you that your account is suspended until you take the time to verify your account information. However, in the next sentence, it’s saying to “update the information about your account ownership,” which is different than just verifying something.
GEICO
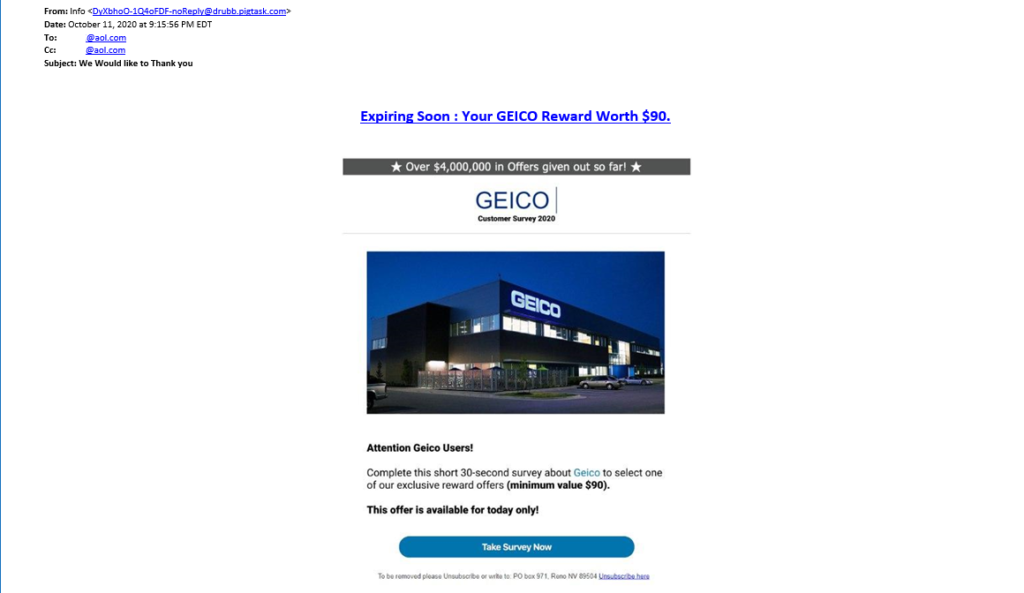
Next up to bat is this message that appears to come from Geico. It looks like they’ve decided to follow the previous phishing example’s lead and take the simpler-is-better approach to design. Considering that Geico is a popular insurance company, it’s likely that it would catch the attention of many potential targets. This phishing email is set up nicely and isn’t as error-ridden as many phishing emails that grace your junk mail folder. However, there are a few things that give away the fact that this is still phish.
First, look at the email “from:” field. The email comes from a pigtask.com domain address instead of geico.com. Second, the sender set both the “to:” and “CC:” fields to send to the same person (those fields have been edited to remove the recipient’s email address).
Second, there are some weird capitalizations going on. And if you were to hover your mouse over the Expiring Soon link near the top or the Take Survey Now button near the bottom, you’d see that they’d take you to a non-Geico website.
Oh, and by the way, never assume an Unsubscribe link is safe in an email. Always hover over it with your mouse to see what the real website URL is. If the unsubscribe link is in a suspected phishing email, don’t click it — ever. Unless, of course, your idea of fun is spending the rest of your day cleaning malware off your machine and changing all of your account passwords… in which case, have at it.
Rackspace
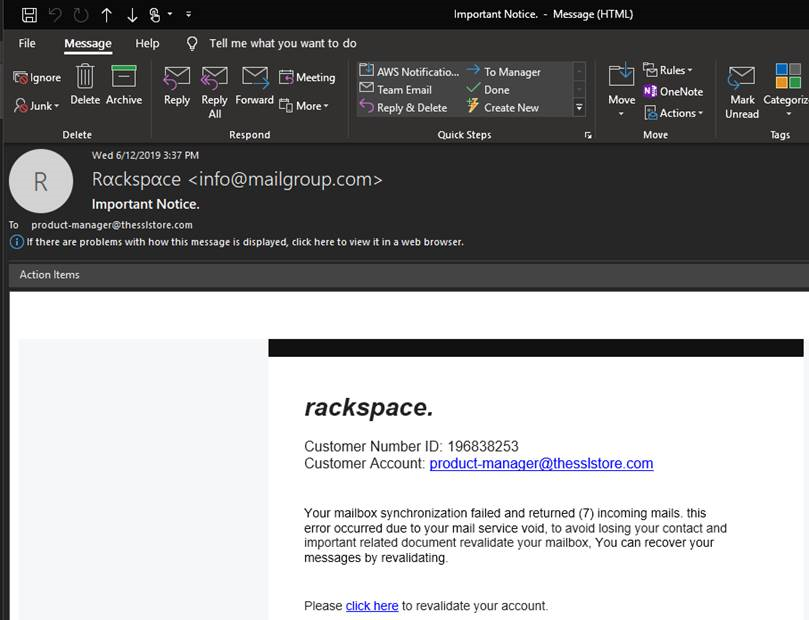
Here’s another example of brand phishing. In this case, the phish is imitating a Rackspace email. We happen to use Rackspace, so this had the potential to pique the right person’s interest. It also requires immediate attention, which tries to force a sense of urgency.
Where it falls apart is in the “from:” field and the link URL. Let’s start with the sender. Rackspace is very clear about the servers it delivers mail from. This isn’t one of them. That was enough to get it flagged by our filters. But beyond that, the from name isn’t quite right (it uses alpha characters instead of “a”) and the URL it links to isn’t rackspace.com.
The URL is pretty sneaky, though. At cursory glance, it almost looks like a valid Rackspace URL:
https://[redacted].com/αpps.rαckspαce.cοm/index.php?email=product-manager@thesslstore.com
All of these well-known brands are being impersonated by cybercriminals through phishing email examples like these. Something that’s poised to be incredibly useful in the future for verifying whether an email is sent from a legitimate organization (i.e., not an imposter) is BIMI, or what stands for brand indicators for message identification.
This BIMI pilot program, which Google’s launched at Google and Verizon Media on July 21, 2020 with DigiCert and Entrust Datacard, involves the use of verified mark certificates (VMCs). The goal is to offer greater security for users and businesses by authenticating businesses and displaying their verified company logos.
Here’s another example of a phishing email pretending to be an unnamed tech company:
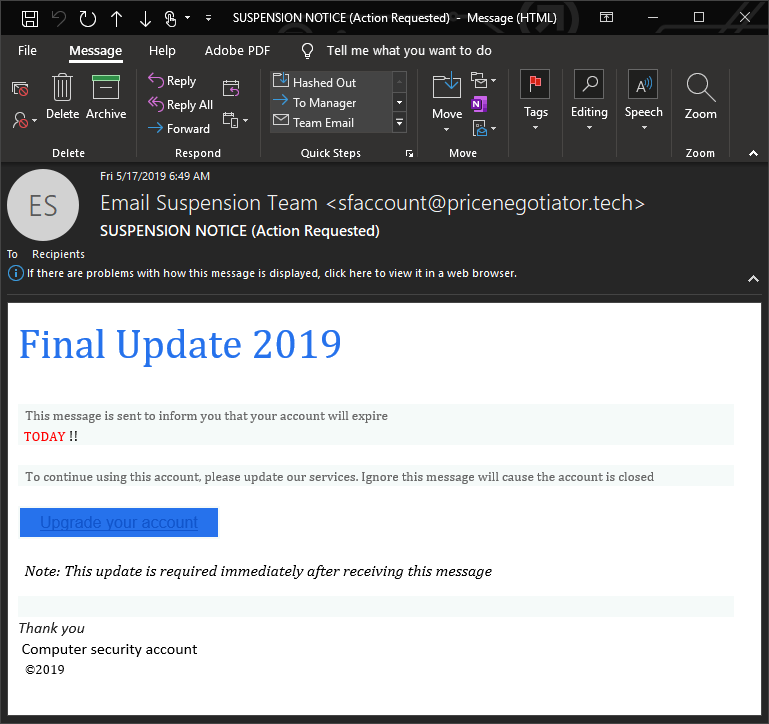
Again, this looks to create urgency about an expiring account. But if you stop for a second, you’ll notice that no where included in this colorful correspondence is any mention of what the expiring account IS. It just says “Computer security account” in the signature. That’s actually helpful in its unhelpfulness. This is clearly a phish.
Posing as a Job Applicant
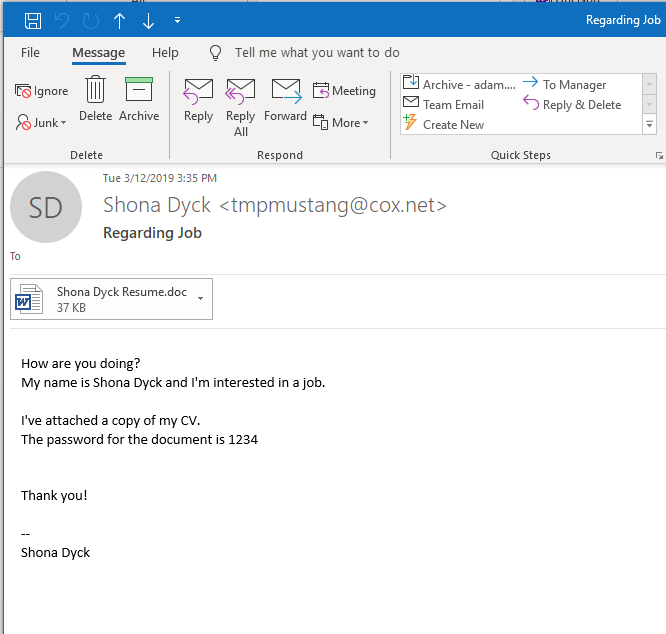
If you ever were — or have just spent time around — a middle school-aged boy, the name of the sender would give this away immediately. But, assuming your purity of mind and heart allowed you to miss that, the premise of this phishing email is actually pretty ingenious. If a company has posted job listings on websites like Indeed or LinkedIn, shoot them an email with a malicious payload masquerading as a resume.
Or in the case of Shona’s resume, maybe just a headshot.
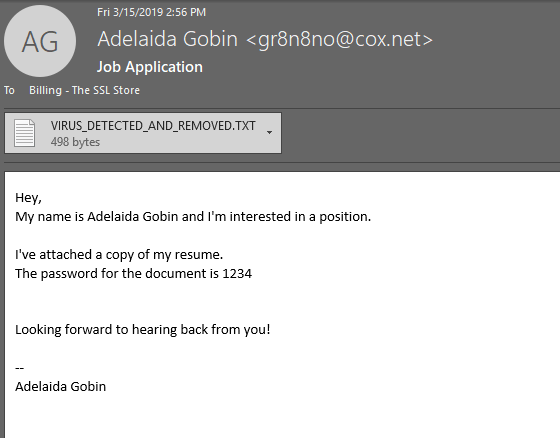
Here’s another phishing email example with a less egregious name, though it’s sent to an email address that a legitimate applicant wouldn’t use, much less even have.
This is just the first of several phishing examples that show that phishing doesn’t always include links. Sometimes, the threat comes in the form of an Office file or .txt doc. Heck, some phishing emails even use doctored images to transmit malicious payloads.
Notice the filters caught the malware and renamed the attachment rather un-suspiciously. I think this is one case where if an employee still opens it, you’re legally sanctioned to load them into a cannon and fire them into the sun.
Posing as an Angry Customer
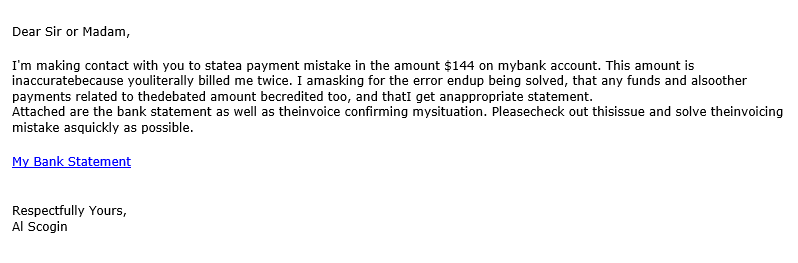
Nobody wants to be accused of billing a customer twice. That’s something that needs to be addressed immediately so this is definitely effective in terms of creating urgency. And when it’s a “customer,” unless the “sender:” and “from:” fields don’t match, it can be tough to rule a whole lot out by domain and TLD.
But there are a couple of things that give this away as a phishing email. For one, every sentence or so you get two words concatenated. That’s a formatting error caused by copy/pasting between differently encoded applications. That’s never a good sign. Also, who sends a link to their bank statement? That’s phishy, too. But the real tell is there’s no contact information given beyond “Al Scogin” and the email address this came from. That speaks to the sender’s intent, which isn’t to recoup a financial loss so much as to get you to click a link. Phish.
Ok, now let’s look at some bad phishing email examples because those are way more fun. We’ll update our best phish section as we see some better phishing examples in the future. As you’re about to see, a lot of these examples of phishing scams are just garbage.
Phishing Email Examples: The Worst
You know how sometimes you CAN judge a book by its cover? The inverse makes for a good movie, but in real life a lot of the time stuff really is as bad as it looks. Sorry, kiddos. Let’s dive into the worst phishing email examples that we have readily available…
Bad Brand Phishing Email Examples
PayPal is one of the most oft-imitated brands in the world of Phishing, so if you want to PayPal phish, you better have your ducks in a row and make it look good.
This… is not that.
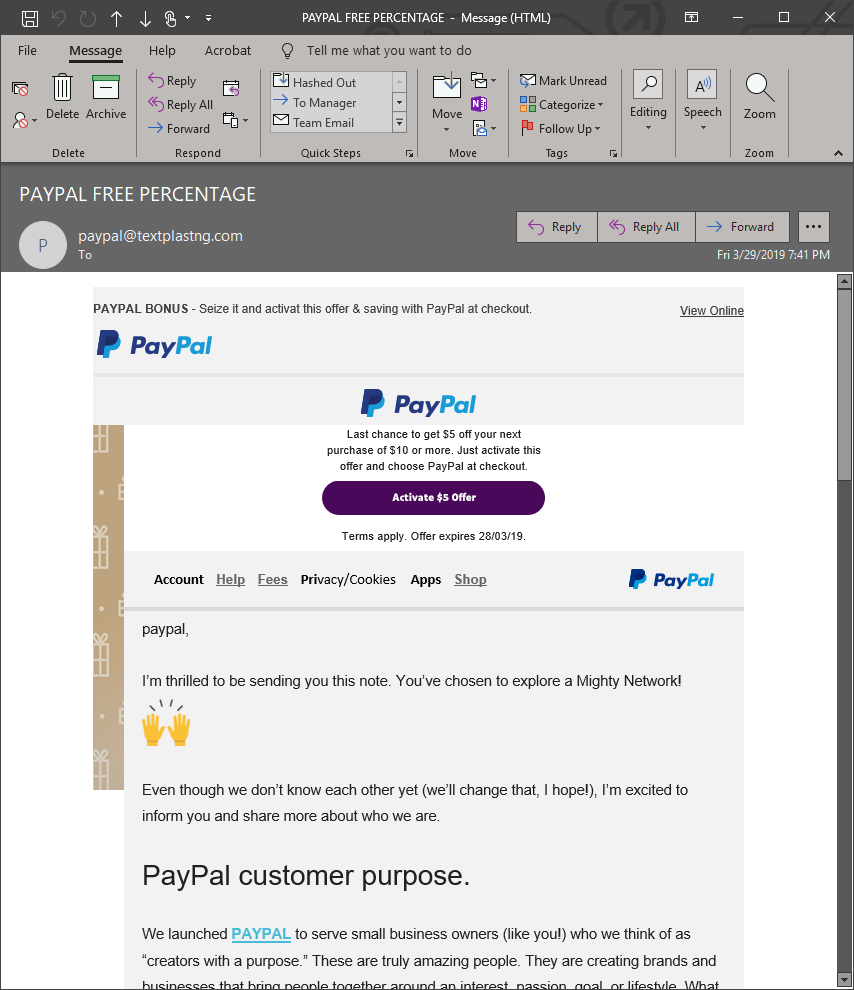
Ignoring for a second that PayPal would never bungle the aesthetics of an email this badly, let’s just admire the details here. The correspondence is addressed TO “paypal” for some reason. Then the second sentence is “you’ve chosen to explore a mighty network!” What the hell does that mean?! If someone says that to you on the street — you clock them and run in the other direction. Then there’s a praise emoji and a stalker-ish “I’ve-been-watching-you”-style sign off. Then a brand statement. What kind of psychopath wrote this email?
Then, of course, there’s also this one…
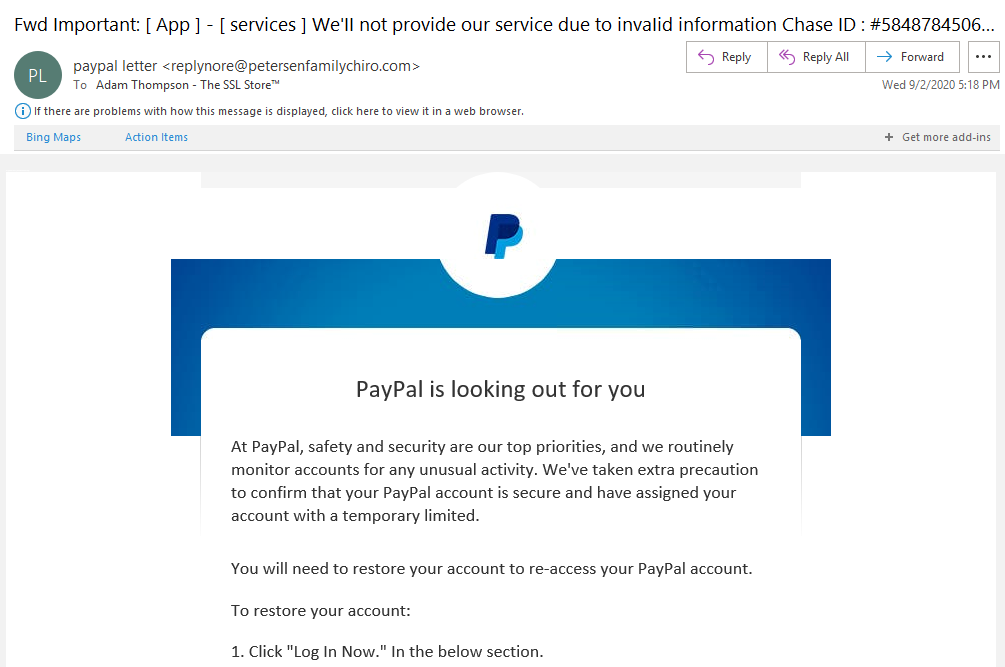
Okay, so this phishing attempt isn’t so bad visually speaking. But seems like a very confused email when you actually bother reading it.
The email subject line talks about a Chase account and the sender’s name is listed as “Paypal Letter.” First, PayPal would never list your account-related information in an email (let alone in the subject line). Second, if the email was legit, it would say that it came from a PayPal domain-related email address. It certainly wouldn’t come from a chiropractic company’s email address.
These two signs alone are great indicators that this email isn’t really from PayPal. But, wait, there’s more!
When you read the content, you’ll quickly realize that it doesn’t make sense even from just a grammatical perspective: “We’ve taken extra precaution to confirm that your PayPal account is secure and have assigned your account with a temporary limited.” A temporary limited what? This message trails off and never completes the train of thought. This never would have made it past PayPal’s real marketing team.
Speaking of confused emails… check out this beauty from Chase. I mean Rackspace. Wait, no, I mean “Online Email Team”…
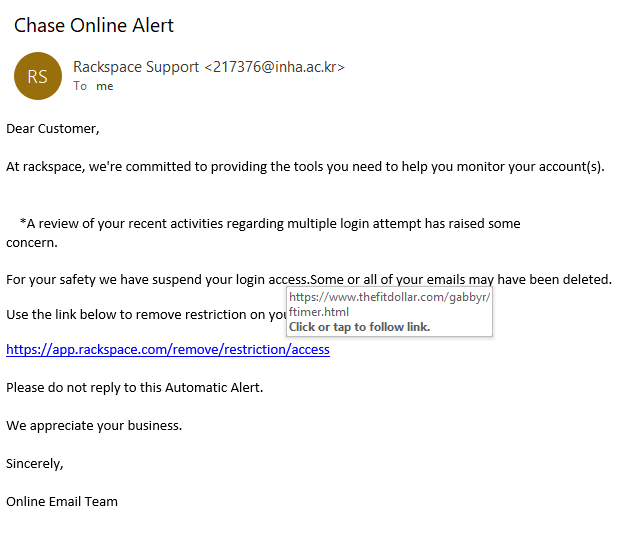
This message is very poorly put together. The subject line says it’s an alert from Chase Online, but the sender’s display name says it’s from Rackspace Support and it’s signed by just “Online Email Team.” Not to mention the email is addressed to “Dear Customer.” I’m pretty sure that Rackspace would know your name if they’re them and you’re one of their customers…
Needless to say, there’s a lot to unpack in this phishing email. The content itself is also poorly written. There are grammatical errors everywhere along with poor capitalizations and spacing issues. Furthermore, the phisher who wrote the email hedged their bet by saying “your accounts” because they don’t know whether you have just one or multiple accounts.
The pièce de résistance comes in the form of the link itself. Sure, the display name appears to be rackspace.com. However, if you hover your cursor over the link, you’ll see that it’s a sham and that the real URL will take you to another unknown website.
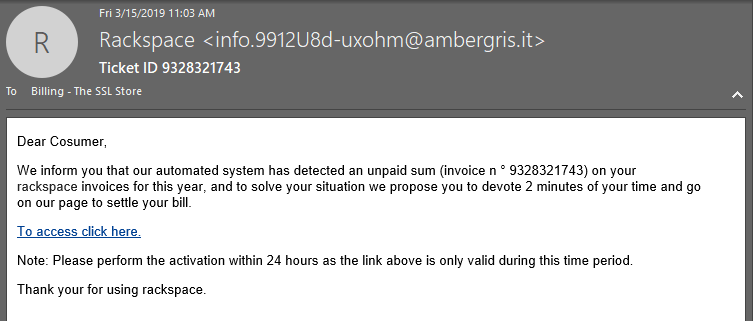
Man, Rackspace just can’t seem to catch a break from being impersonated in phishing scams. This one has a decent subject line and it purports to be from Rackspace. But two words in and we already know it’s BS. Also, it originated from ambergris.it? That’s not a Rackspace server.
My favorite part is the passive-aggressive way Rackspace is allegedly telling the recipient to take care of their bill… “devote 2 minutes of your time and go on our page to settle your bill.” Very on-brand. (So there’s no ambiguity, this is sarcasm. Though we pay our bills on time I’m sure there is no such passive aggression on Rackspace’s part in the event things are past due.)
So, how about one more Rackspace phishing example? Then we’ll leave them alone.
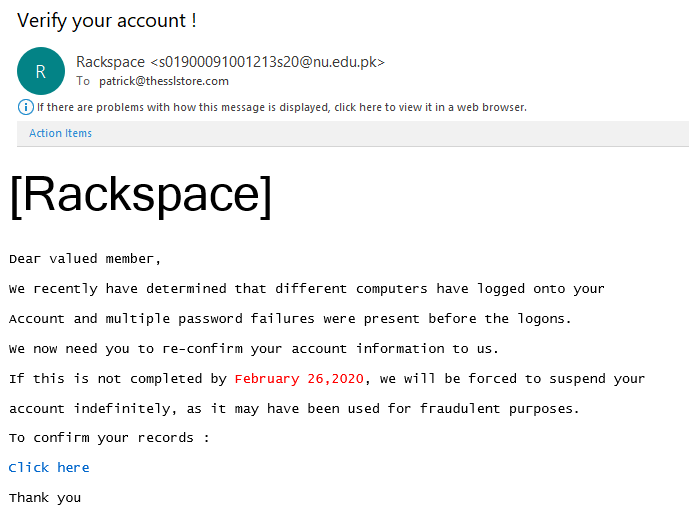
Ah, yes. Another email with all of the hallmark indicators of a phishing scam. It’s addressed with the generic salutations directed to the “valued member.” (Aww, don’t you feel special?) While the email display says Rackspace, the actual email address behind it belies that claim.
When you read the message, there’s no identifying information about the recipient that would indicate that the sender actually knows who they’re talking to. They’re just taking shots in the dark and hoping that one will land a target. And all it takes is for one person to fall for this scam to make their minimal amount of effort worthwhile.
Microsoft
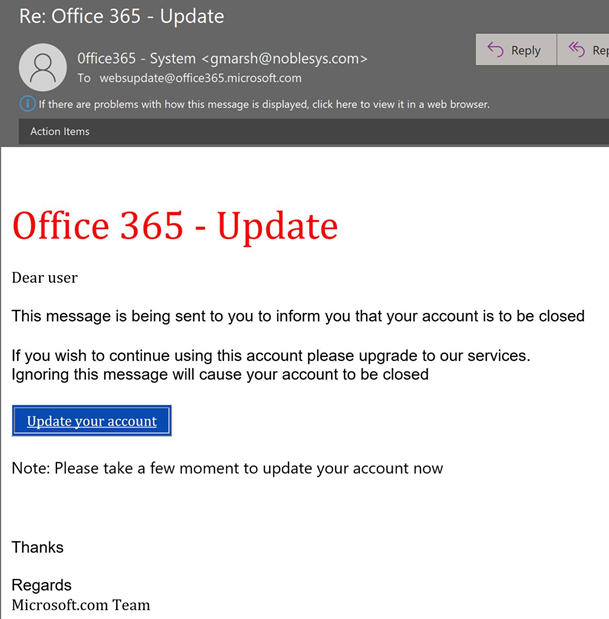
Even this tech giant isn’t safe from the reaches of phishers. That’s why it’s made its way onto our list of bad phishing email examples. This email — again, directed to the generic “user” — seems to confuse the words “update” and “upgrade.” The title of the phish implies that there’s an update coming, whereas the message itself says that you have to upgrade your account to keep it from being terminated.
The message, which says it was sent by Office 365 (and not Microsoft), comes from a sender’s email address that indicates otherwise. After all, I’m pretty sure noblesys.com isn’t the same as Microsoft.com.
Also, as a last quick note, it looks like someone was either in a big rush or they just didn’t give a crap about how the email looks. The message uses text that’s written in both serif and sans serif typefaces, different colors, and different sizes. This is a poor copy-paste job if I’ve ever seen one.
Walmart
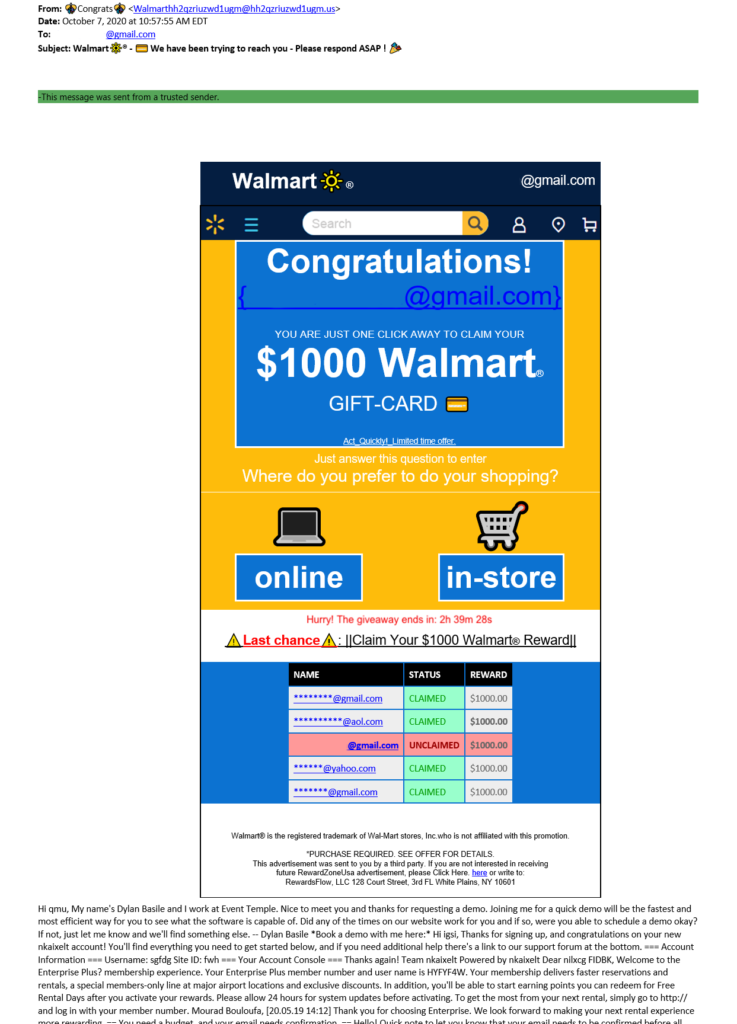
Here’s a colorful example of a bad brand phishing email that one of my colleagues received on her personal account. While the email address does include “Walmart” in the first half of the address, it’s followed by a bunch of gibberish that’s clearly not a Walmart.com-associated account or domain.
In the main body of the email, note how the phisher tries to impersonate Walmart with the sun logo next to the name. However, Walmart’s logo doesn’t look like that. In fact, the icon they’re using is actually the sun icon from Microsoft Office’s icon list. Also, the email’s written to sound suspiciously urgent. And if we’ve learned anything from this article so far, if an unsolicited message pushes immediacy, it’s likely to be a phishing email.
Lastly, notice all of the weird text at the end of the email? Here’s, let’s blow that up a bit so you can see it better:
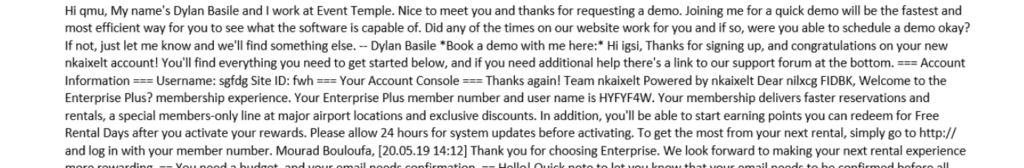
All of that mumbo-jumbo is there to try to help emails get around spam filters. However, it’s important to note that the name of the company is, in fact, a real organization and the person this cybercriminal is impersonating was one of their real employees. Bob Graham, the co-founder of the real Event Temple, posted on Google’s community support forums about the issue:
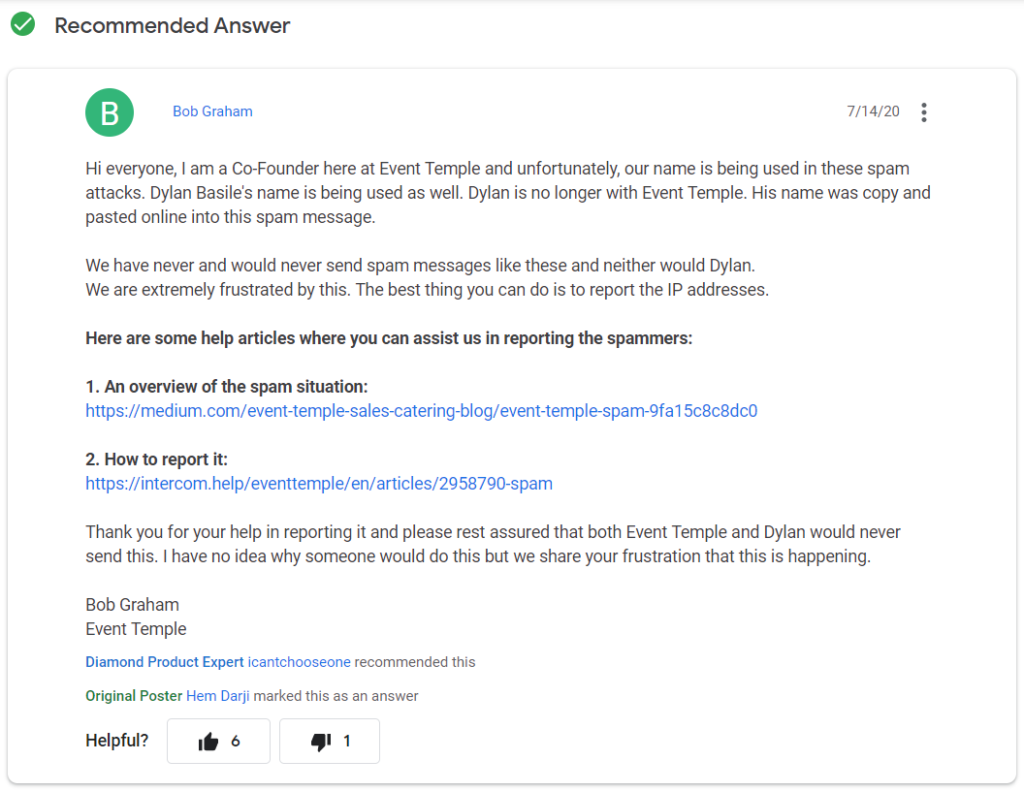
Unfortunately for Dylan — and for his previous employer — phishers are having a field day sending out spam emails using their legitimate info.
Posing As Your Crypto Wallet Company
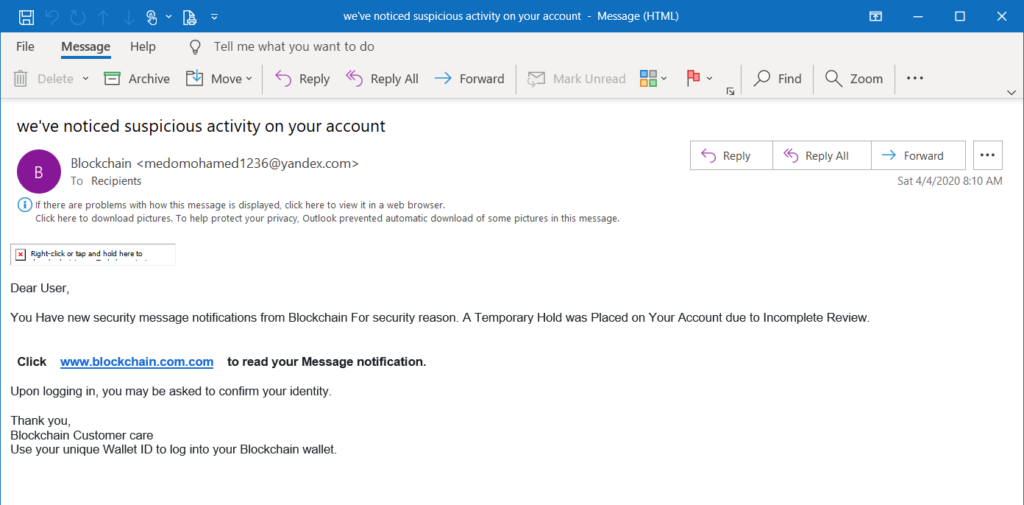
This email is purportedly from blockchain.com, a digital wallet for cryptocurrencies. While it’s got a decent subject line that piques your interest and creates a sense of urgency, the rest of the poorly written email. It’s very vague in nature and is sent to “Recipients” and addresses the recipient as “Dear User.”
Suuuuure, that’s not too suspicious. Not to mention, no legitimate company would send out bulk emails about issues relating to individual accounts.
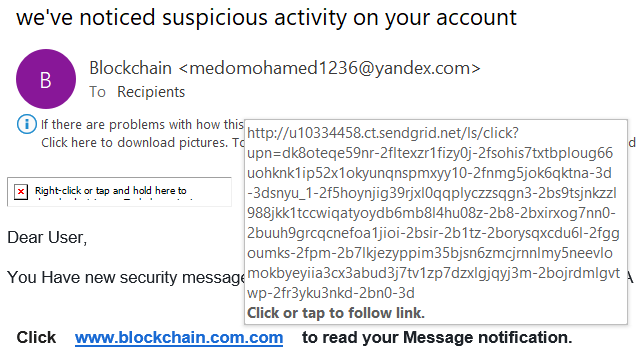
Another dead giveaway? Look at the website — www.blockchain.com.com. When you hover your mouse over the link, it displays the real URL of the site that you’d be directed to if you were to click on it. Needless to say, that’s definitely not a link for blockchain.com.
If someone’s smart enough to have a digital wallet and successfully hold and manage cryptocurrencies, I’m pretty sure they’re also too smart to fall for such a lazy phishing scam attempt. But maybe I should curb my expectations since even experts can fall for phishing scams…
Fake News
The original fake news: sending someone an advertisement that’s really just trying to steal their info or give them malware. Here’s an example:
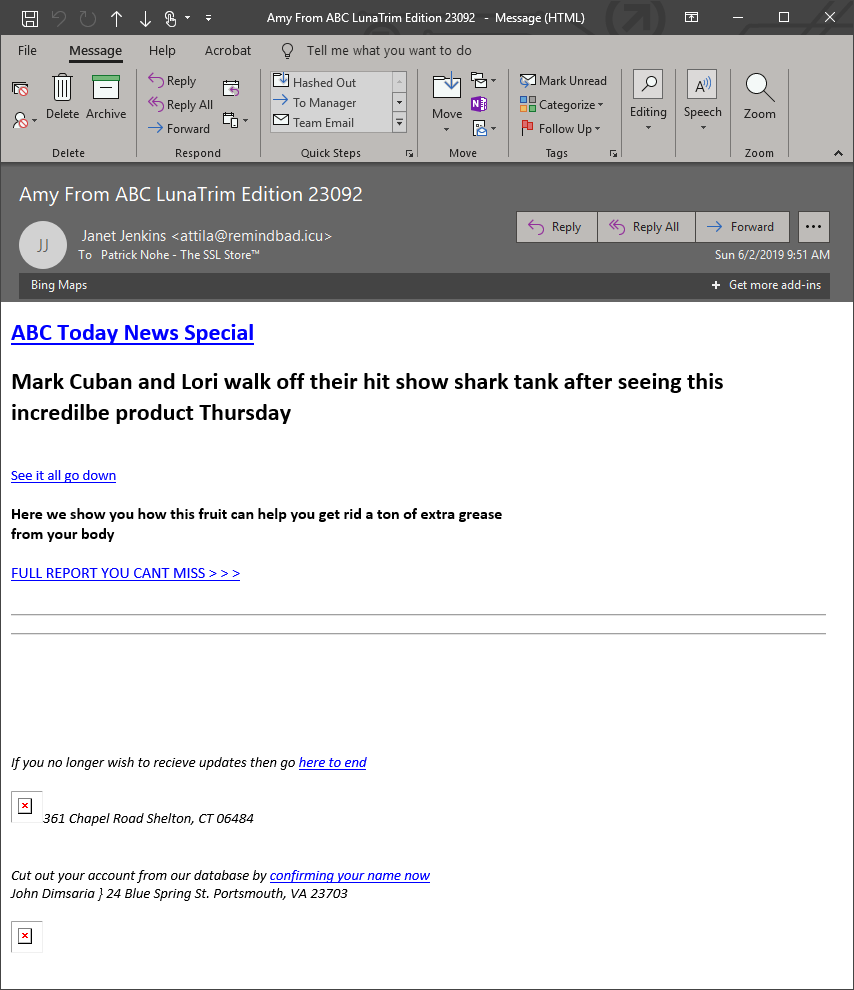
The subject line “Amy from ABC LunaTrim Edition 23092” could pass as a subcription-related message as ABC always sounds like a legitimate enterprise. And it says “ABC Today News Special,” which most people in the U.S. (and Australia) associate with a TV network. But the sender’s name and email address don’t match up. Then things go downhill quickly with one word: “Incredilbe.”
This is such a weird mistake that I actually Googled it just to make sure it wasn’t a cognate, and that’s just how another language spells it and… no. After clicking through Google’s “suggested spelling” all I found was a bunch of travel reviews left by orthographically-challenged (idiot) tourists. Actually, they say spelling isn’t a function of intelligence, but there’s a threshold at which point it’s hard to argue it isn’t at least a little bit indicative of it. Or a lack of it. Also, who uses Bing Maps?
Anyway, the rest of the email does itself no favors, either. Clearly a phish.
Pose as a Hacker
A lot of people don’t know a whole lot about computers and networks and cybersecurity, which paints hackers in a rather fictional light. And to make things worse the media does a really poor job of covering cybersecurity topics, which scares up a whole host of other problems.
Criminals know this, and they are more than happy to prey on those fears with phishing emails and scams.
This next email has some NSFW language. Ohh, I probably should have mentioned that earlier, too (looking at you, Shona), but we’re all adults here, so let’s continue.
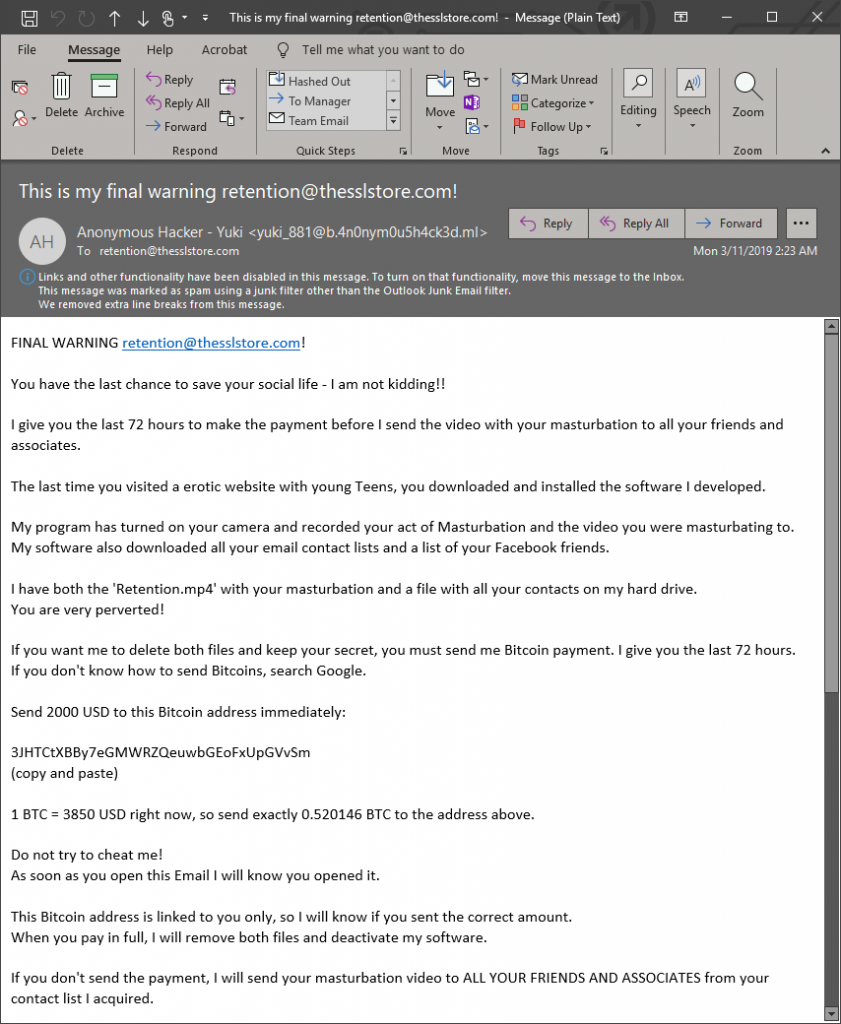
This is actually one in a string of clearly-automated emails that escalated over the course of a few weeks. Regrettably, I emptied my junk folder and deleted the first few before starting this article, but you can probably gather the substance and gravity of the first few from this one.
Right away, you can tell this is a phish. First of all, Mr. Retention doesn’t have a social life. Mr. Retention is not even a person. Mr. Retention is a deprecated mail alias (apparently one with too much time on his hands). You can tell this is automated from the get-go.
And I think there’s a foundational flaw in the logic behind this whole endeavor, which is that the type of person that might be scared into believing this definitely has no idea how to buy Bitcoin.
In fact, asking such a naive, impressionable individual to even try to obtain Bitcoin is like sending a sheep into a lion’s den. They’ll have their money, their home and all their credit sucked out of them way before you ever see your $2,000’s worth.
Here’s the same thing in German Danish. Same disclaimer applies. NSFW language (if you speak Danish).
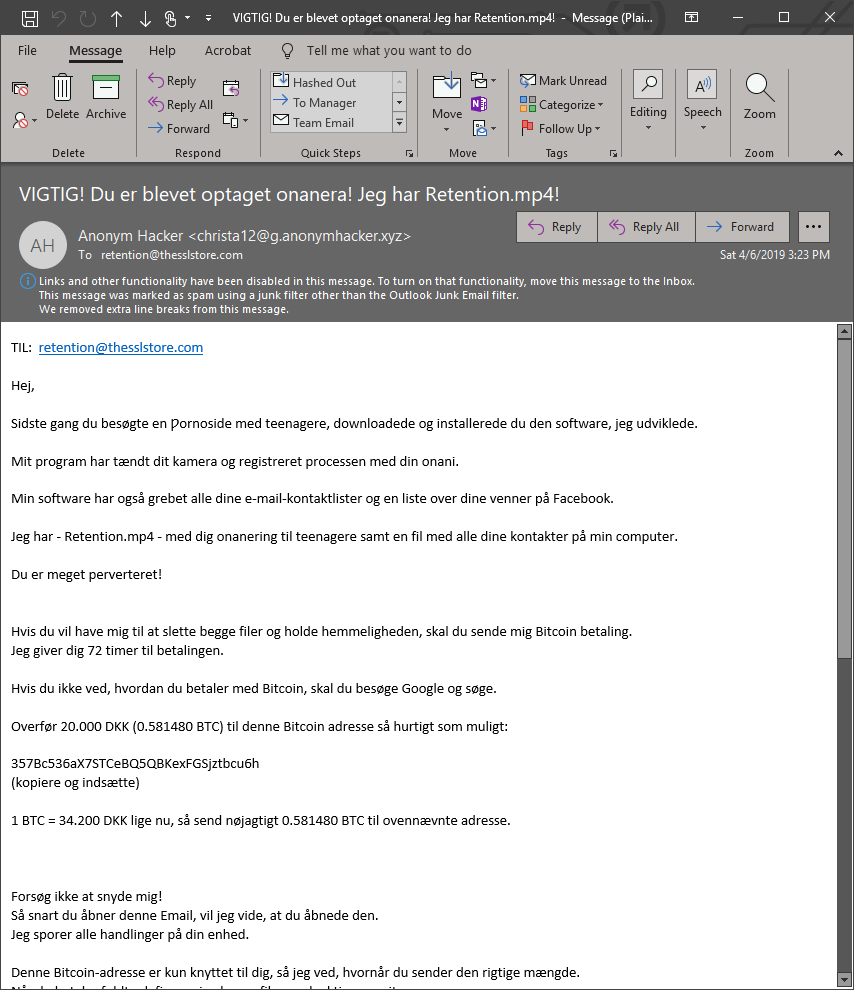
Here’s another phishing example with some slightly different language, but all the same anger and scaremongering we’ve come to love:
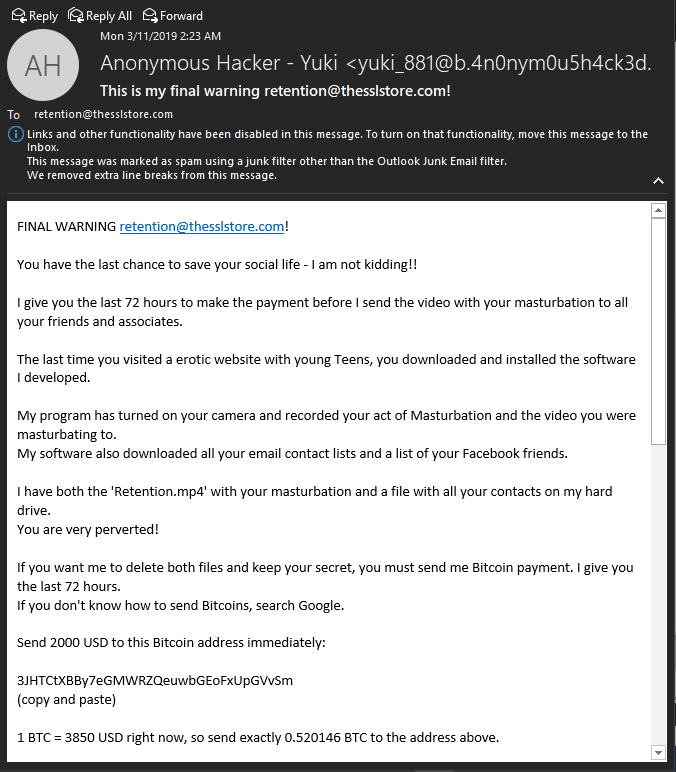
C’mon, Mr. Retention. We’re going to have to take away your internet access, aren’t we?
For an in-depth look at more of these Bitcoin phishing emails, be sure to check out our article on n1ghtm4r3 phishing emails.
Phony Invoices, Payments & Bonus Phishing Email Examples
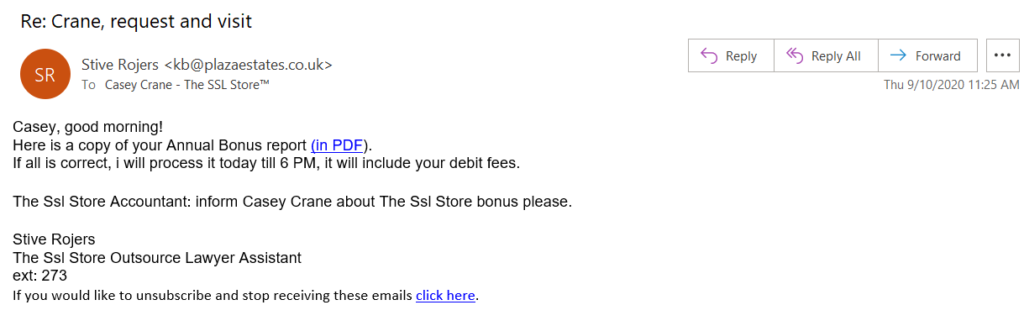
Everyone loves money, and there are few things more attractive to an employee than an email insinuating that they’re getting a bonus. Unfortunately, however, was sent to use from the typo-king version of Captain America, “Stive Rojers.” A quick look at the sender’s email address or name is enough to make you hit the spam button right away. But then when you actually read this sad excuse of a phishing example, you’ll see that it’s written in a way that it tries to be believable without actually doing a good job.
If you’re a legal assistant (not a “lawyer assistant,” by the way), you certainly wouldn’t send a message from your boss while addressing them as “The Ssl Store Accountant.” That’s a bit on the nose, wouldn’t you say? Also, I’m pretty sure that if you worked for a company, you’d know how to properly write their name (The SSL Store), which is named after their core products. Just sayin’.
Furthermore, the contact information contains no phone number (although it does contain an extension), which would imply that the idea here is that you’re not supposed to contact them. Instead, they’ve included a link to a PDF that’s supposedly available on a website. Someone’s annual bonus information isn’t something that you’d want to simply host and send a link out to on a public website.
Needless to say, all of this screams “scam.”
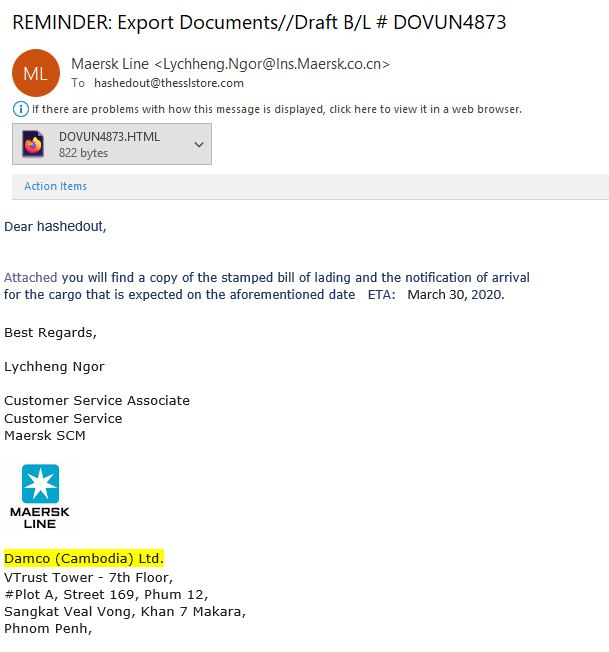
Maersk Line, the largest subsidiary of the well-known international container logistics parent company Maersk Group, is another favorite target of cybercriminals. In 2019, the company released a statement warning that their real employees were being impersonated in phishing scams. Lucky for us, we’ve received one of those phishing email examples here at Hashed Out to share with you.
The email sender info displays Maersk Line and the email spoofing attempt of the email address itself could be considered passable to someone who doesn’t look closely. But the email content itself is a mess — it’s a collage of different colors, typefaces and character sizes.
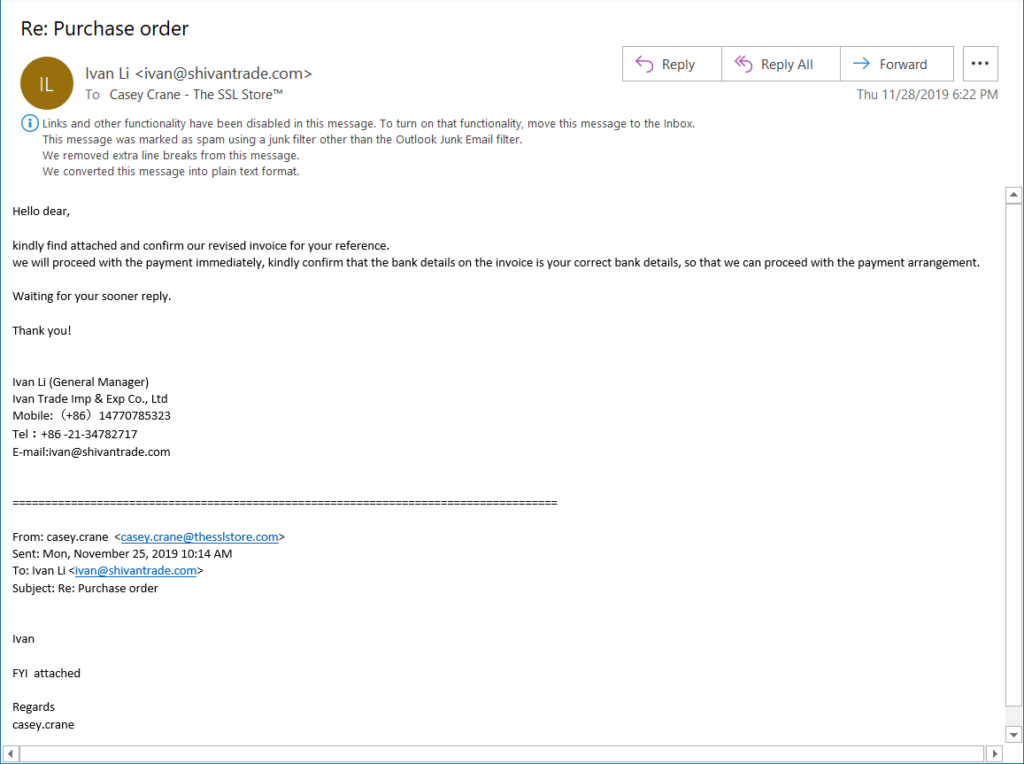
We’ve reached the final item on our list of phishing email examples. This message is written to look like it’s part of an ongoing correspondence. It did contain malicious content, which was removed by Outlook’s email spam filters.
Of course, the writing clearly isn’t from a native English speaker — it’s riddled with poor grammar and a dearth of sentence capitalizations that sets an editor’s teeth on edge. And the email is addressed to “Hello dear.” Definitely not a professional way to address a work-related contact. That would set off red flags immediately.
Let’s consider the sender’s email address itself. If you look up “shivantrade.com,” the search results show a bunch of links relating to Chinese baby wipes exports. Not really sure what that would have to do with The SSL Store or why they’d think we’d order them in bulk. But, hey, who am I to question the decisions of management, right?
A particularly nice touch of this email is making it look like I was the one who reached out to the sender first. Of course, they flubbed it by signing it “casey.crane” — it shows that they either copy-pasted this first half of the email address or used code to auto populate the field. Either way, if you’re going to go to all of that trouble to try to make an email appear legitimate, it would be important to fix those little details.
Send Us Your Best & Worst Phishing Email Examples!
We want to see YOUR best phish. Hang on, let’s reword that. If anyone sends you or your company a particularly good phish — really convincing ones or comically bad ones — take a screenshot and send it to HashedOut@TheSSLStore.com. Just make sure to cover up anything you don’t want the world to see. Probably best to rephrase that, too. If there are any recipients, email addresses or proprietary information included on the screenshot make sure to obscure it before sending it.
And check back on this phishing email examples article periodically. We’ll update this article as more and more phish swim our way.
Note: This article on phishing email examples was originally written by Patrick Nohe on June 11, 2019. The piece, which was updated with lots of new content and screenshots, was re-published by Casey Crane as a “re-hashed” version of the article on Oct. 21, 2020.
As always, leave any comments or questions below…






































![A Look at 30 Key Cyber Crime Statistics [2023 Data Update]](https://www.thesslstore.com/blog/wp-content/uploads/2022/02/cyber-crime-statistics-feature2-75x94.jpg)













5 Ways to Determine if a Website is Fake, Fraudulent, or a Scam – 2018
in Hashing Out Cyber SecurityHow to Fix ‘ERR_SSL_PROTOCOL_ERROR’ on Google Chrome
in Everything EncryptionRe-Hashed: How to Fix SSL Connection Errors on Android Phones
in Everything EncryptionCloud Security: 5 Serious Emerging Cloud Computing Threats to Avoid
in ssl certificatesThis is what happens when your SSL certificate expires
in Everything EncryptionRe-Hashed: Troubleshoot Firefox’s “Performing TLS Handshake” Message
in Hashing Out Cyber SecurityReport it Right: AMCA got hacked – Not Quest and LabCorp
in Hashing Out Cyber SecurityRe-Hashed: How to clear HSTS settings in Chrome and Firefox
in Everything EncryptionRe-Hashed: The Difference Between SHA-1, SHA-2 and SHA-256 Hash Algorithms
in Everything EncryptionThe Difference Between Root Certificates and Intermediate Certificates
in Everything EncryptionThe difference between Encryption, Hashing and Salting
in Everything EncryptionRe-Hashed: How To Disable Firefox Insecure Password Warnings
in Hashing Out Cyber SecurityCipher Suites: Ciphers, Algorithms and Negotiating Security Settings
in Everything EncryptionThe Ultimate Hacker Movies List for December 2020
in Hashing Out Cyber Security Monthly DigestAnatomy of a Scam: Work from home for Amazon
in Hashing Out Cyber SecurityThe Top 9 Cyber Security Threats That Will Ruin Your Day
in Hashing Out Cyber SecurityHow strong is 256-bit Encryption?
in Everything EncryptionRe-Hashed: How to Trust Manually Installed Root Certificates in iOS 10.3
in Everything EncryptionHow to View SSL Certificate Details in Chrome 56
in Industry LowdownPayPal Phishing Certificates Far More Prevalent Than Previously Thought
in Industry Lowdown